802.11 Network Security - Top Threats
Recently, the topic of Wi-Fi on Habré is gaining popularity, which is good news. However, some important aspects, in particular, security, are still rather one-sided, which is very well seen in the comments. A couple of years ago, an abbreviated version of the material below was published in the journal Computer Review . I think the readers of Habr will be interesting and useful to get acquainted with him, especially in the full and updated version. The first article discusses the main threats. In the second we discuss ways to implement protection based on WIPS.
The popularity of wireless local area networks has already passed the stage of explosive growth and has reached the state of "familiar to everyone" technology. Home access points and mini Wi-Fi routers are inexpensive and widely available, hotspots are quite common, a laptop without Wi-Fi is an anachronism. Like many other innovative technologies, the use of wireless networks brings not only new benefits, but also new risks. The Wi-Fi boom has spawned a whole new generation of hackers specializing in inventing more and more new ways of hacking wireless and attacking users and corporate infrastructure. Since 2004, Gartner has warned that WLAN security will be one of the main problems - and the forecast is justified.
The wireless communication and mobility it provides are interesting and beneficial to many. However, as long as the issue of wireless security is not completely clear, opinions differ dramatically: some (for example, warehouse operators) are no longer afraid to tie up their key business processes to Wi-Fi, while others barricade themselves and prohibit the use of wireless elements in their networks. Which of them chose the right strategy? Is Wi-Fi ban a guarantee of protection against wireless threats? And in general - is this Wi-Fi so dangerous and unreliable, as they say about it? The answer is far from obvious!
')
In this article we will consider:
Traditional wired networks use cable to transmit information. The cable is considered to be a “controlled” environment, protected by the buildings and premises in which it is located. External "foreign" traffic, which is included in a protected network segment, is filtered by a firewall and analyzed by IDS / IPS systems. In order to gain access to such a wired network segment, an attacker needs to overcome either the building's physical security system or a firewall.
Wireless networks use radio waves. Ether is an environment with common access and almost no control. Providing the equivalent of physical security of wired networks here is simply impossible. As soon as a user connects an access point to a wired network, its signal can pass through walls, interfloor overlaps, and windows of a building. Thus, the connected network segment becomes available from another floor or even from a neighboring building, parking or other end of the street - the radio signal can extend hundreds of meters outside the building. The only physical boundary of the wireless network is the level of this signal itself.
Therefore, unlike wired networks, where the user’s connection point to the network is well defined and known - this is a wall outlet - in wireless networks you can connect to the network from anywhere, as long as the signal is of sufficient strength.
Also, the air is a shared medium. All wireless devices are included in one giant “hub” (hub) - and any wireless device can “see” all wireless neighbors in the network. In this case, a receiver operating in the passive mode (only listening) cannot be determined at all.
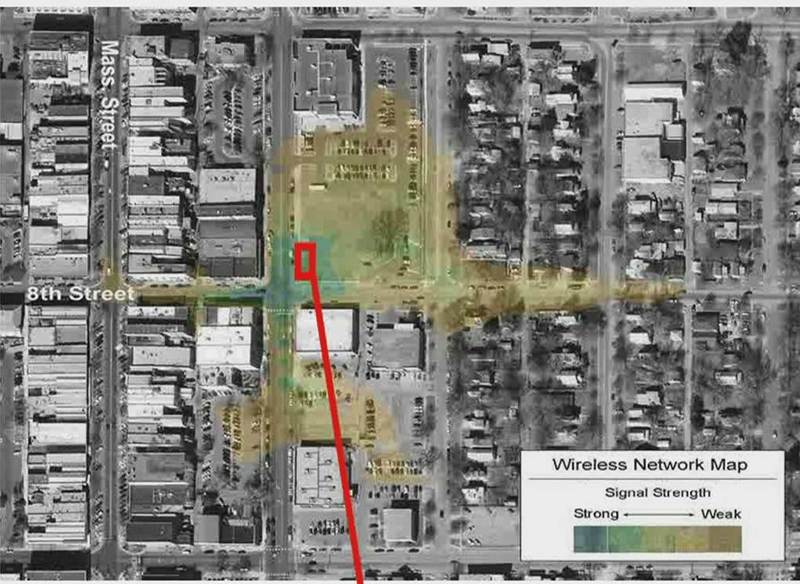
The perimeter of the wireless network is not limited to the perimeter of the building.
Thanks to the efforts of suppliers of consumer Wi-Fi equipment, even the most unprepared user can now deploy a wireless network. A set of inexpensive access point and wireless adapter will cost $ 50-80. At the same time, most devices are supplied already configured by default, which allows you to immediately start working with them - even without looking at the configuration. It is precisely this amount that the intentional or unintentional breaking of your network by its own employees, who have established their own access point without coordination and who have not taken care of ensuring its proper security, can do so.
An even bigger problem is that wireless users are by definition mobile. Users can appear and disappear, change their location, and are not tied to fixed entry points, as is the case with wired networks - they can be anywhere in the coverage area! All this greatly complicates the task of “keeping uninvited guests out of the door” and tracking the sources of wireless attacks.
In addition, such an important component of mobility as roaming is another wireless security problem. This time - users. Unlike wired networks, where the user is “tied” by a cable to a specific outlet and port of an access switch — in wireless networks, the user is not tied to anything. With the help of special software, it is quite simple to “transplant” it from an authorized access point to an unauthorized or even an attacker’s laptop operating in Soft AP mode (software-based access point), opening the possibility for a number of attacks on an unsuspecting user.
Since radio signals have a broadcasting nature, they are not limited to the walls of buildings and are accessible to all receivers whose location is difficult or impossible to fix - it is especially easy and convenient for attackers to attack wireless networks. Therefore, formally, even a teenager with a smartphone in his pocket, now riding on a bicycle in the yard, can do radio intelligence of your network - purely from youthful curiosity. The huge variety of ready-made tools for analyzing protocols and vulnerabilities available on the Internet will also help him find an access point cleanly out of curiosity that some employee recently brought to work and did not bother to reconfigure from the default settings, purely out of curiosity in the instructions there will be a key network access - and voila!
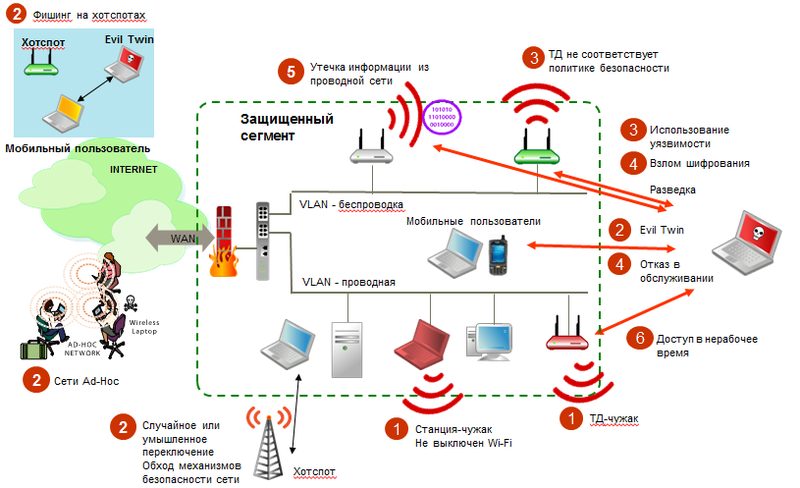
Traditional defenses do not save from new classes of attacks.
So, wireless technologies that work without the physical and logical limitations of their wired counterparts, greatly increasing workflow flexibility and user efficiency, reducing network deployment costs, also expose network infrastructure and users to significant risks. In order to understand how to ensure the safe operation of wireless networks, let's take a closer look at them.
Foreigners are devices that allow unauthorized access to the corporate network, often bypassing the protection mechanisms defined by the corporate security policy. Most often these are the most arbitrarily set access points. Statistics around the world, for example, point to outsiders as the cause of most hacking into networks of organizations. Even if the organization does not use wireless communication and considers itself as a result of such a ban protected from wireless attacks - an implanted (intentionally or not) stranger will easily correct this situation. The availability and low cost of Wi-Fi devices have led to the fact that in the USA, for example, almost every network with more than 50 users has managed to become familiar with this phenomenon.
In addition to access points, a home router with Wi-Fi, a Soft AP software access point, a laptop with a wired and wireless interface simultaneously turned on, a scanner, a projector, etc. can play the role of an alien.
Wireless threats are subject to those who do not use Wi-Fi. For $ 50, you can [not] deliberately create a hole in the security system for $ 50,000.
As mentioned above, wireless devices are not “tied” by cable to the outlet and can change the points of connection to the network during the work. For example, there may be “Random Associations” when a laptop with Windows XP (fairly trustingly related to all wireless networks) or simply an incorrectly configured wireless client automatically associates and connects the user to the nearest wireless network. Such a mechanism allows attackers to "switch to themselves" of nothing knowing the user for subsequent scanning of vulnerabilities, phishing, or Man-in-The-Middle attacks. In addition, if a user is simultaneously connected to a wired network — he has just become a convenient entry point — that is, classic stranger.
Also, many users of laptop devices equipped with Wi-Fi and wired interfaces and not satisfied with the quality of the wired network (slowly, the evil admin has set URL filtering, ICQ does not work), they like to switch to the nearest available hotspot (or the OS does it for them automatically). case, for example, a wired network failure). Needless to say, in this case, all the attempts of the IT department to ensure network security remain literally "overboard."
Ad-Hoc networks — direct peer-to-peer connections between wireless devices without access points — are a convenient way to quickly transfer a file to a colleague or print the desired document on a Wi-Fi printer. However, this way of organizing the network does not support most of the security methods needed, providing attackers with an easy way to hack into the computers of Ad-Hoc users. The recently available VirtualWiFi and Wi-Fi Direct technologies only exacerbate the situation.
Some network devices may be more vulnerable than others — they may be misconfigured, use weak encryption keys, or authentication methods with known vulnerabilities. It is not surprising that first of all the attackers attack them. Analyst reports claim that more than 70 percent of successful hacks of wireless networks occurred precisely as a result of incorrect configuration of access points or client software.
A single incorrectly configured access point (including a stranger) can cause hacking of the corporate network. The default settings of most access points do not include authentication or encryption, or use static keys recorded in the manual and therefore well known. Combined with the low price of access points, this factor significantly complicates the task of monitoring the integrity of a wireless infrastructure configuration and its level of protection. Employees of the organization can voluntarily bring access points and connect them wherever they like. At the same time, it is unlikely that they will pay enough attention to their competent and safe configuration and coordinate their actions with the IT department. Such points also create the greatest threat to wired and wireless networks.
Incorrectly configured user devices present a greater threat than incorrectly configured access points. These devices literally come and go from the enterprise, often they are not specifically configured to minimize wireless risks and are content with the default configuration (which, by default, cannot be considered secure). Such devices provide invaluable assistance to hackers in their penetration into the wired network, providing a convenient entry point for scanning the network and distributing malware in it.
Attackers have long had access to special tools for hacking networks based on the WEP encryption standard (see risk 4). These tools are widely covered on the Internet and do not require special skills to apply. They exploit WEP vulnerabilities by passively collecting traffic statistics on the wireless network until the collected data is sufficient to recover the encryption key. Using the latest generation of WEP hacking tools that use special traffic injection methods, the term “until then” ranges from 15 minutes to 15 seconds. Similarly, there are vulnerabilities of varying degrees of danger and complexity that can break TKIP and even WPA2. The only "impenetrable" method so far remains the use of WPA2-Enterprise (802.1x) with at least server certificates.
Wireless technologies have created new ways of realizing the old threats, as well as some new, hitherto impossible in wired networks. In all cases, it became much harder to fight the attacker, because it is impossible to either track its physical location or isolate it from the network.
Most traditional attacks begin with intelligence, as a result of which the attacker determines the further development of the attack. Wireless intelligence is used as a means of scanning wireless networks (NetStumbler, Wellenreiter, JC client), and means of collecting and analyzing packets, because many WLAN control packets are unencrypted. It is very difficult to distinguish a station collecting information from a regular station attempting to gain authorized access to the network or from attempting a random association.
Many people try to protect their networks by hiding the network name in beacons (Beacon) sent by access points, and by disabling the answer to the ESSID (Broadcast ESSID) broadcast request. These methods, belonging to the class Security through Obscurity, are generally recognized as insufficient, since the attacker still sees the wireless network on a certain radio channel, and all that remains for him is to wait for the first authorized connection to such a network, since during such a connection, the ESSID is transmitted in an unencrypted form on the air. After that, such a security measure simply loses its meaning. Some features of the wireless client of Windows XP SP2 (corrected in SP3) further aggravated the situation, because the client constantly sent the name of such a hidden network on the air, trying to connect. As a result, the attacker not only received the name of the network, but could also “hook” such a client on his access point.
Impersonation of an authorized user is a serious threat to any network, not only wireless. However, in the wireless network to determine the authenticity of the user more difficult. Of course, there are SSIDs and you can try to filter by MAC addresses, but both are transmitted on the air in the open form, and it is easy to fake both, and forging - at least to “bite off” part of the network bandwidth, insert incorrect frames with the aim of Violations of authorized communications, and splitting at least a little encryption algorithms - to organize attacks on the network structure (for example, ARP Poisoning, as is the case with the recently discovered TKIP vulnerability). Not to mention in the WEP hacking, discussed in the paragraph above!
There is a false belief that user impersonation is possible only in the case of MAC authentication or using static keys, that 802.1x-based schemes are completely secure. Unfortunately, this is no longer the case. Some mechanisms (LEAP) are cracked as easily as WEP. Other schemes, such as EAP-FAST or PEAP-MSCHAPv2, are more reliable, but do not guarantee resistance to a complex attack using several factors at the same time.
The task of the Denial of Service attack is either a violation of the quality indicators of the functioning of network services or the complete elimination of the possibility of access to them for authorized users. For this purpose, for example, the network can be filled up with “garbage” packets (with an incorrect checksum, etc.) sent from a legitimate address. In the case of a wireless network, it is simply impossible to trace the source of such an attack without special tools. he can be anywhere. In addition, it is possible to organize DoS on the physical level by simply running a fairly powerful interference generator in the desired frequency range.
Tools for organizing attacks on wireless networks are widely available and constantly updated with new tools, ranging from all known AirCrack and ending with cloud services to decrypt hashes. Plus, as soon as access is gained - the traditional toolkit of higher levels is used.
Almost all wireless networks at some point are connected to the wired. Accordingly, any wireless access point can be used as a springboard for an attack. But that's not all: some errors in the configuration of access points in combination with wired network configuration errors may open ways for information leaks. The most common example is access points operating in bridge mode (Layer 2 Bridge) connected to a flat network (or a network with segmented VLAN violations) and broadcasting broadcast packets from the wired segment, ARP requests, DHCP, STP frames, etc. . Some of this data may be useful for organizations of Man-in-The-Middle attacks, various Poisoning and DoS attacks, or simply intelligence.
Another common scenario is based on the implementation features of the 802.11 protocols. In the case when several ESSIDs are configured on one access point at once, the broadcast traffic will be distributed to all ESSIDs at once. As a result, if a secure network and a public hot spot are set up on a single point, an attacker connected to a hot spot may, for example, disrupt DHCP or ARP in a secure network. This can be corrected by organizing proper binding of the ESS to the BSS, which is supported by almost all manufacturers of equipment of the Enterprise class (and very few from the Consumer class), but you need to know about it.
Some features of the functioning of wireless networks pose additional problems that can affect the overall availability, performance, security and cost of operation. To solve these problems correctly, you need special support and maintenance tools, special administration and monitoring mechanisms that are not implemented in the traditional wireless network management tools.
Since wireless networks are not limited to the premises, as wired, you can connect to them anywhere and at any time. Because of this, many organizations limit the availability of wireless networks in their offices only working hours (up to the physical disabling of access points). In light of this, it is natural to assume that any wireless activity on the network during off-hours should be considered suspicious and subject to investigation.
Access points that allow connections at low speeds allow connections at longer range. Thus, they represent an additional possibility of secure remote hacking. If in an office network, where everyone works at speeds of 24/36/54 Mbit / s, a connection of 1 or 2 Mbit / s suddenly appears - this may be a signal that someone is trying to get into the network from the street. The picture has already resulted. Read more about slow speeds here (p 3.1) .
Since wireless networks use radio waves, the quality of network performance depends on many factors. The most striking example is the interference of radio signals, which can significantly degrade the throughput and the number of supported users, up to the complete impossibility of using the network. The source of interference can be any device that emits a signal of sufficient power in the same frequency range as the access point: from neighboring access points to a densely populated office center, to electric motors in production, Bluetooth headsets, and even microwaves. On the other hand, attackers can use interference to organize a DoS attack on a network.
The aliens working on the same channel as the legitimate access points open up not only the access to the network, but also disrupt the performance of the “correct” wireless network. In addition, to launch attacks against end users and to penetrate the network with the Man-In-The Middle attack, attackers often silence access points of a legitimate network, leaving only one - their access point with the same network name.
In addition to interference, there are other aspects that affect the quality of communication in wireless networks. Since the wireless environment is a shared medium, each misconfigured client, or a failed access point antenna, can cause problems both on the physical and data link levels, leading to a deterioration in the quality of service of other network clients.
In total, wireless networks generate new classes of risks and threats against which it is impossible to protect against traditional wired devices. Even if Wi-Fi is formally prohibited in an organization, this does not mean that any of the users will not install an outsider and will reduce all investments in the network security to zero. In addition, due to the peculiarities of wireless communication, it is important to control not only the security of the access infrastructure, but also to monitor users who may be targeted by an attacker, or simply accidentally or deliberately switch from a corporate network to an unprotected connection.
The good news, after such a depressive statement, is that most of the listed risks can be minimized or even reduced to zero. To ensure the safe operation of the wireless network (including infrastructure and users), an approach that is generally consistent with the “layered security” approach used for traditional wired networks (adjusted for WLAN specifics) is used. But this is a topic for a separate article of no lesser length, which will follow later.
Introduction
The popularity of wireless local area networks has already passed the stage of explosive growth and has reached the state of "familiar to everyone" technology. Home access points and mini Wi-Fi routers are inexpensive and widely available, hotspots are quite common, a laptop without Wi-Fi is an anachronism. Like many other innovative technologies, the use of wireless networks brings not only new benefits, but also new risks. The Wi-Fi boom has spawned a whole new generation of hackers specializing in inventing more and more new ways of hacking wireless and attacking users and corporate infrastructure. Since 2004, Gartner has warned that WLAN security will be one of the main problems - and the forecast is justified.
The wireless communication and mobility it provides are interesting and beneficial to many. However, as long as the issue of wireless security is not completely clear, opinions differ dramatically: some (for example, warehouse operators) are no longer afraid to tie up their key business processes to Wi-Fi, while others barricade themselves and prohibit the use of wireless elements in their networks. Which of them chose the right strategy? Is Wi-Fi ban a guarantee of protection against wireless threats? And in general - is this Wi-Fi so dangerous and unreliable, as they say about it? The answer is far from obvious!
')
In this article we will consider:
- what are the important security features of a wireless connection,
- why “not using” or banning Wi-Fi does not save you from wireless threats,
- what new risks should be considered.
What are the security features of a wireless connection?
A shared environment that is almost impossible to control
Traditional wired networks use cable to transmit information. The cable is considered to be a “controlled” environment, protected by the buildings and premises in which it is located. External "foreign" traffic, which is included in a protected network segment, is filtered by a firewall and analyzed by IDS / IPS systems. In order to gain access to such a wired network segment, an attacker needs to overcome either the building's physical security system or a firewall.
Wireless networks use radio waves. Ether is an environment with common access and almost no control. Providing the equivalent of physical security of wired networks here is simply impossible. As soon as a user connects an access point to a wired network, its signal can pass through walls, interfloor overlaps, and windows of a building. Thus, the connected network segment becomes available from another floor or even from a neighboring building, parking or other end of the street - the radio signal can extend hundreds of meters outside the building. The only physical boundary of the wireless network is the level of this signal itself.
Therefore, unlike wired networks, where the user’s connection point to the network is well defined and known - this is a wall outlet - in wireless networks you can connect to the network from anywhere, as long as the signal is of sufficient strength.
Also, the air is a shared medium. All wireless devices are included in one giant “hub” (hub) - and any wireless device can “see” all wireless neighbors in the network. In this case, a receiver operating in the passive mode (only listening) cannot be determined at all.

The perimeter of the wireless network is not limited to the perimeter of the building.
Easy to deploy and mobility
Thanks to the efforts of suppliers of consumer Wi-Fi equipment, even the most unprepared user can now deploy a wireless network. A set of inexpensive access point and wireless adapter will cost $ 50-80. At the same time, most devices are supplied already configured by default, which allows you to immediately start working with them - even without looking at the configuration. It is precisely this amount that the intentional or unintentional breaking of your network by its own employees, who have established their own access point without coordination and who have not taken care of ensuring its proper security, can do so.
An even bigger problem is that wireless users are by definition mobile. Users can appear and disappear, change their location, and are not tied to fixed entry points, as is the case with wired networks - they can be anywhere in the coverage area! All this greatly complicates the task of “keeping uninvited guests out of the door” and tracking the sources of wireless attacks.
In addition, such an important component of mobility as roaming is another wireless security problem. This time - users. Unlike wired networks, where the user is “tied” by a cable to a specific outlet and port of an access switch — in wireless networks, the user is not tied to anything. With the help of special software, it is quite simple to “transplant” it from an authorized access point to an unauthorized or even an attacker’s laptop operating in Soft AP mode (software-based access point), opening the possibility for a number of attacks on an unsuspecting user.
Easy to attack
Since radio signals have a broadcasting nature, they are not limited to the walls of buildings and are accessible to all receivers whose location is difficult or impossible to fix - it is especially easy and convenient for attackers to attack wireless networks. Therefore, formally, even a teenager with a smartphone in his pocket, now riding on a bicycle in the yard, can do radio intelligence of your network - purely from youthful curiosity. The huge variety of ready-made tools for analyzing protocols and vulnerabilities available on the Internet will also help him find an access point cleanly out of curiosity that some employee recently brought to work and did not bother to reconfigure from the default settings, purely out of curiosity in the instructions there will be a key network access - and voila!

Traditional defenses do not save from new classes of attacks.
Six key wireless risks
So, wireless technologies that work without the physical and logical limitations of their wired counterparts, greatly increasing workflow flexibility and user efficiency, reducing network deployment costs, also expose network infrastructure and users to significant risks. In order to understand how to ensure the safe operation of wireless networks, let's take a closer look at them.
Risk One - Strangers (Rogue Devices, Rogues)
Foreigners are devices that allow unauthorized access to the corporate network, often bypassing the protection mechanisms defined by the corporate security policy. Most often these are the most arbitrarily set access points. Statistics around the world, for example, point to outsiders as the cause of most hacking into networks of organizations. Even if the organization does not use wireless communication and considers itself as a result of such a ban protected from wireless attacks - an implanted (intentionally or not) stranger will easily correct this situation. The availability and low cost of Wi-Fi devices have led to the fact that in the USA, for example, almost every network with more than 50 users has managed to become familiar with this phenomenon.
In addition to access points, a home router with Wi-Fi, a Soft AP software access point, a laptop with a wired and wireless interface simultaneously turned on, a scanner, a projector, etc. can play the role of an alien.

Wireless threats are subject to those who do not use Wi-Fi. For $ 50, you can [not] deliberately create a hole in the security system for $ 50,000.
Second risk - non-fixed nature of communication
As mentioned above, wireless devices are not “tied” by cable to the outlet and can change the points of connection to the network during the work. For example, there may be “Random Associations” when a laptop with Windows XP (fairly trustingly related to all wireless networks) or simply an incorrectly configured wireless client automatically associates and connects the user to the nearest wireless network. Such a mechanism allows attackers to "switch to themselves" of nothing knowing the user for subsequent scanning of vulnerabilities, phishing, or Man-in-The-Middle attacks. In addition, if a user is simultaneously connected to a wired network — he has just become a convenient entry point — that is, classic stranger.
Also, many users of laptop devices equipped with Wi-Fi and wired interfaces and not satisfied with the quality of the wired network (slowly, the evil admin has set URL filtering, ICQ does not work), they like to switch to the nearest available hotspot (or the OS does it for them automatically). case, for example, a wired network failure). Needless to say, in this case, all the attempts of the IT department to ensure network security remain literally "overboard."
Ad-Hoc networks — direct peer-to-peer connections between wireless devices without access points — are a convenient way to quickly transfer a file to a colleague or print the desired document on a Wi-Fi printer. However, this way of organizing the network does not support most of the security methods needed, providing attackers with an easy way to hack into the computers of Ad-Hoc users. The recently available VirtualWiFi and Wi-Fi Direct technologies only exacerbate the situation.
Risk Three - Network and Device Vulnerabilities
Some network devices may be more vulnerable than others — they may be misconfigured, use weak encryption keys, or authentication methods with known vulnerabilities. It is not surprising that first of all the attackers attack them. Analyst reports claim that more than 70 percent of successful hacks of wireless networks occurred precisely as a result of incorrect configuration of access points or client software.
Incorrectly configured access points
A single incorrectly configured access point (including a stranger) can cause hacking of the corporate network. The default settings of most access points do not include authentication or encryption, or use static keys recorded in the manual and therefore well known. Combined with the low price of access points, this factor significantly complicates the task of monitoring the integrity of a wireless infrastructure configuration and its level of protection. Employees of the organization can voluntarily bring access points and connect them wherever they like. At the same time, it is unlikely that they will pay enough attention to their competent and safe configuration and coordinate their actions with the IT department. Such points also create the greatest threat to wired and wireless networks.
Incorrectly configured wireless clients
Incorrectly configured user devices present a greater threat than incorrectly configured access points. These devices literally come and go from the enterprise, often they are not specifically configured to minimize wireless risks and are content with the default configuration (which, by default, cannot be considered secure). Such devices provide invaluable assistance to hackers in their penetration into the wired network, providing a convenient entry point for scanning the network and distributing malware in it.
Breaking encryption
Attackers have long had access to special tools for hacking networks based on the WEP encryption standard (see risk 4). These tools are widely covered on the Internet and do not require special skills to apply. They exploit WEP vulnerabilities by passively collecting traffic statistics on the wireless network until the collected data is sufficient to recover the encryption key. Using the latest generation of WEP hacking tools that use special traffic injection methods, the term “until then” ranges from 15 minutes to 15 seconds. Similarly, there are vulnerabilities of varying degrees of danger and complexity that can break TKIP and even WPA2. The only "impenetrable" method so far remains the use of WPA2-Enterprise (802.1x) with at least server certificates.
Fourth risk - new threats and attacks
Wireless technologies have created new ways of realizing the old threats, as well as some new, hitherto impossible in wired networks. In all cases, it became much harder to fight the attacker, because it is impossible to either track its physical location or isolate it from the network.
Intelligence service
Most traditional attacks begin with intelligence, as a result of which the attacker determines the further development of the attack. Wireless intelligence is used as a means of scanning wireless networks (NetStumbler, Wellenreiter, JC client), and means of collecting and analyzing packets, because many WLAN control packets are unencrypted. It is very difficult to distinguish a station collecting information from a regular station attempting to gain authorized access to the network or from attempting a random association.
Many people try to protect their networks by hiding the network name in beacons (Beacon) sent by access points, and by disabling the answer to the ESSID (Broadcast ESSID) broadcast request. These methods, belonging to the class Security through Obscurity, are generally recognized as insufficient, since the attacker still sees the wireless network on a certain radio channel, and all that remains for him is to wait for the first authorized connection to such a network, since during such a connection, the ESSID is transmitted in an unencrypted form on the air. After that, such a security measure simply loses its meaning. Some features of the wireless client of Windows XP SP2 (corrected in SP3) further aggravated the situation, because the client constantly sent the name of such a hidden network on the air, trying to connect. As a result, the attacker not only received the name of the network, but could also “hook” such a client on his access point.
Impersonation and Identity Theft
Impersonation of an authorized user is a serious threat to any network, not only wireless. However, in the wireless network to determine the authenticity of the user more difficult. Of course, there are SSIDs and you can try to filter by MAC addresses, but both are transmitted on the air in the open form, and it is easy to fake both, and forging - at least to “bite off” part of the network bandwidth, insert incorrect frames with the aim of Violations of authorized communications, and splitting at least a little encryption algorithms - to organize attacks on the network structure (for example, ARP Poisoning, as is the case with the recently discovered TKIP vulnerability). Not to mention in the WEP hacking, discussed in the paragraph above!
There is a false belief that user impersonation is possible only in the case of MAC authentication or using static keys, that 802.1x-based schemes are completely secure. Unfortunately, this is no longer the case. Some mechanisms (LEAP) are cracked as easily as WEP. Other schemes, such as EAP-FAST or PEAP-MSCHAPv2, are more reliable, but do not guarantee resistance to a complex attack using several factors at the same time.
Denial of Service (DoS)
The task of the Denial of Service attack is either a violation of the quality indicators of the functioning of network services or the complete elimination of the possibility of access to them for authorized users. For this purpose, for example, the network can be filled up with “garbage” packets (with an incorrect checksum, etc.) sent from a legitimate address. In the case of a wireless network, it is simply impossible to trace the source of such an attack without special tools. he can be anywhere. In addition, it is possible to organize DoS on the physical level by simply running a fairly powerful interference generator in the desired frequency range.
Attacker's specialized tools
Tools for organizing attacks on wireless networks are widely available and constantly updated with new tools, ranging from all known AirCrack and ending with cloud services to decrypt hashes. Plus, as soon as access is gained - the traditional toolkit of higher levels is used.
Fifth risk - information leakage from the wired network
Almost all wireless networks at some point are connected to the wired. Accordingly, any wireless access point can be used as a springboard for an attack. But that's not all: some errors in the configuration of access points in combination with wired network configuration errors may open ways for information leaks. The most common example is access points operating in bridge mode (Layer 2 Bridge) connected to a flat network (or a network with segmented VLAN violations) and broadcasting broadcast packets from the wired segment, ARP requests, DHCP, STP frames, etc. . Some of this data may be useful for organizations of Man-in-The-Middle attacks, various Poisoning and DoS attacks, or simply intelligence.
Another common scenario is based on the implementation features of the 802.11 protocols. In the case when several ESSIDs are configured on one access point at once, the broadcast traffic will be distributed to all ESSIDs at once. As a result, if a secure network and a public hot spot are set up on a single point, an attacker connected to a hot spot may, for example, disrupt DHCP or ARP in a secure network. This can be corrected by organizing proper binding of the ESS to the BSS, which is supported by almost all manufacturers of equipment of the Enterprise class (and very few from the Consumer class), but you need to know about it.
The risk of the sixth - features of the functioning of wireless networks
Some features of the functioning of wireless networks pose additional problems that can affect the overall availability, performance, security and cost of operation. To solve these problems correctly, you need special support and maintenance tools, special administration and monitoring mechanisms that are not implemented in the traditional wireless network management tools.
Activity after hours
Since wireless networks are not limited to the premises, as wired, you can connect to them anywhere and at any time. Because of this, many organizations limit the availability of wireless networks in their offices only working hours (up to the physical disabling of access points). In light of this, it is natural to assume that any wireless activity on the network during off-hours should be considered suspicious and subject to investigation.
Speeds
Access points that allow connections at low speeds allow connections at longer range. Thus, they represent an additional possibility of secure remote hacking. If in an office network, where everyone works at speeds of 24/36/54 Mbit / s, a connection of 1 or 2 Mbit / s suddenly appears - this may be a signal that someone is trying to get into the network from the street. The picture has already resulted. Read more about slow speeds here (p 3.1) .
Interference
Since wireless networks use radio waves, the quality of network performance depends on many factors. The most striking example is the interference of radio signals, which can significantly degrade the throughput and the number of supported users, up to the complete impossibility of using the network. The source of interference can be any device that emits a signal of sufficient power in the same frequency range as the access point: from neighboring access points to a densely populated office center, to electric motors in production, Bluetooth headsets, and even microwaves. On the other hand, attackers can use interference to organize a DoS attack on a network.
The aliens working on the same channel as the legitimate access points open up not only the access to the network, but also disrupt the performance of the “correct” wireless network. In addition, to launch attacks against end users and to penetrate the network with the Man-In-The Middle attack, attackers often silence access points of a legitimate network, leaving only one - their access point with the same network name.
Connection
In addition to interference, there are other aspects that affect the quality of communication in wireless networks. Since the wireless environment is a shared medium, each misconfigured client, or a failed access point antenna, can cause problems both on the physical and data link levels, leading to a deterioration in the quality of service of other network clients.
What to do?
In total, wireless networks generate new classes of risks and threats against which it is impossible to protect against traditional wired devices. Even if Wi-Fi is formally prohibited in an organization, this does not mean that any of the users will not install an outsider and will reduce all investments in the network security to zero. In addition, due to the peculiarities of wireless communication, it is important to control not only the security of the access infrastructure, but also to monitor users who may be targeted by an attacker, or simply accidentally or deliberately switch from a corporate network to an unprotected connection.
The good news, after such a depressive statement, is that most of the listed risks can be minimized or even reduced to zero. To ensure the safe operation of the wireless network (including infrastructure and users), an approach that is generally consistent with the “layered security” approach used for traditional wired networks (adjusted for WLAN specifics) is used. But this is a topic for a separate article of no lesser length, which will follow later.
Source: https://habr.com/ru/post/151126/
All Articles