Restore Active Directory Objects: Script Collection

Undoubtedly, many of you have repeatedly encountered this problem - removed user accounts. There are many articles on restoring accounts, and probably the best written by Microsoft , but all of them lack clarity. We will try to overcome this drawback by reducing the procedure for recovering user accounts to simple steps.
As you know, you can restore objects in different ways, each of which is best suited in a given situation.
In this case, it is preferable to restore from tombstone objects. There are several reasons for this:
- no need to take the domain controller offline (all work, nothing is disabled)
- tombstone recovery is much better than simply recreating a new version of a remote object
Part of the attributes is deleted along with the deletion of the object - they can no longer be restored. For example, membership in security groups.
If you re-create an object, it will always have the new objectGUID and objectSid attributes (if it is a member of a security policy, such as a user). As a result, any external object references, such as an ACL, will need to be updated to reflect the new object identifier. This can be a very big problem.
Therefore, in this post, we will first consider methods using tombstone objects, and only at the end provides information on forced recovery. At the end of the post, the capabilities of the NetWrix Active Directory Object Restore Wizard will be reviewed. The information for the post is taken from the document "Restore Active Directory Objects: a collection of scripts" prepared by NetWrix. We invite interested persons under cat.
')
What needs to be restored: an example
Given:
OU Finance_Department with its Oleg and Dmitry accounts and its sub-account OU Admins, which contains the Sergey account, has been removed from the acme.com domain.
Task:
Restore the OU to all members (including the embedded OU) and attributes of the accounts.
And this task will be solved in all possible ways.
1. Restore objects using ldp.exe
Procedure:
1) Enable console display of deleted objects (CN = Deleted Objects)
First, you need to make the deleted objects appear (and by default the container CN = Deleted Objects is not displayed. Use ldp.exe in Active Directory (requires Domain Admins membership).
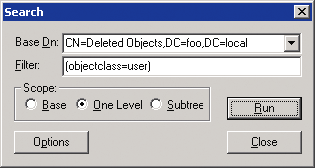
1. Run ldp.exe. ( Start - Run - ldp.exe )
2. In the Options menu, select Controls (Controls)

3. In the dialog box that appears, select the menu Load Predefined (Predefined reboot) , select the item Return deleted objects in it and click Ok
4. Check how the container of deleted objects is displayed:
a. To connect and bind to the server where the root domain of the Active Directory environment forest is located, in the Connections section, select Connect and click Bind .
b. Click the Browse button, select Structure and in the Distinguished Name (DN) field enter DC =, DC =.
c. In the console tree, double-click the distinguished name (DN) of the root domain and find the container CN = Deleted Objects, DC = acme, DC = com.
Restoring objects:
Consider the restoration of the example of the account Oleg, part of the OU Finance_Department.
1) Run ldp.exe
2) In the Connections section, select the Connect option - Bind Connect and bind to the server that hosts the root domain of the Active Directory environment forest

3) In the console tree, go to the container CN = Deleted Objects (we also write DC = acme, DC = com for the example domain)
searching results
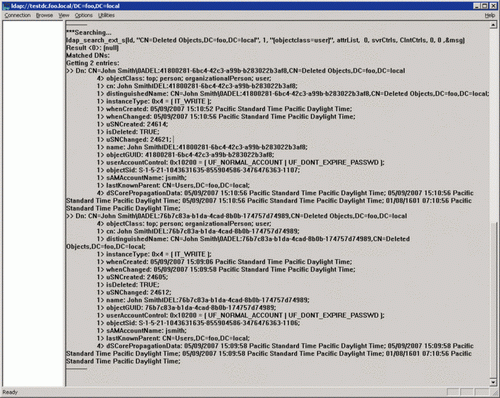
4) Find an object in the container CN = Deleted Objects that we want to restore, right-click on it and select the Modify item.
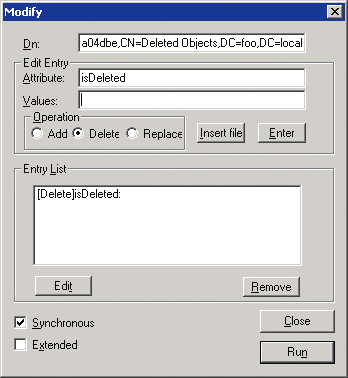
5) In the Modify window, change the following parameters
a. In the Edit Entry field of the attribute, enter isDeleted
b. Leave the Values field empty.
c. In the Operation section, select Delete and press the Enter key.
d. In the Edit Entry Attribute field, enter distinguishedName
e. In the Values field, enter the initial distinguished name (DN) of this Active Directory object.
f. In the section Operation (Operation) we select Replace (to Replace)
g. Select the Extended checkbox, press the Enter key, and then Run.
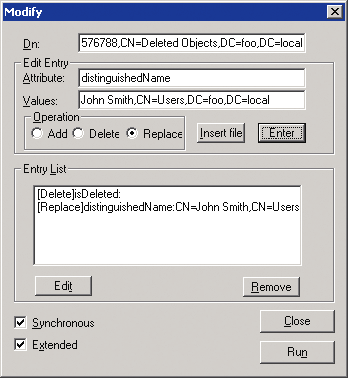
Account restored, but deactivated. It will need to be enabled manually. You also need to manually restore group membership and reset the password.
We repeat the same actions for the remaining objects:
OU Finance_Department
Ou admins
Account Dmitry
Account Sergey
Total:
You need to do a lot of actions before the object is restored.
All actions will have to be repeated for each of the deleted objects.
2. We use ADRESTORE
Restoring burial sites with LDP is simple. However, uncomfortable and long. For these purposes, there is ADRESTORE , which is designed specifically for restoring AD objects.
The utility works in two modes:
• Run without parameters . It will list all the tombstone objects in the CN = Deleted Objects container of the default domain. You can add a string to search in the command line to select objects to display:
C:\> adrestore Finance_Department All objects in the CN = Deleted Objects container that contain the string “Finance_Department” in the CN or OU attribute are displayed — the LDAP search filter cn = * Finance_Department * and ou = * Finance_Department * is used. The figure below shows the results of the search returned by the ADRESTORE program.
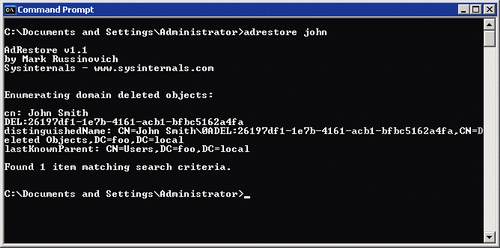
• Restore objects
If you need to restore a tombstone, and not just find it, you must specify the –r parameter along with an additional line, for example, like this:
C:\> adrestore –r Finance_Department To restore accounts, use the following commands:
C:\> adrestore –r Oleg C:\> adrestore –r Dmitry C:\> adrestore –r Admins C:\> adrestore –r Sergey The team will offer to restore each burial object that satisfies the condition. The object is restored to the container specified by the lastKnownParent attribute of the tombstone object (and no other).
This command will offer to restore every suitable burial object. ADRESTORE always restores the object to the container indicated by the lastKnownParent attribute of the tombstone object; there is no way to specify another container.
Total:
ADRESTORE is easier to use than LDP.
The utility allows you to quickly restore objects, but again without the necessary attributes - group membership and passwords will have to be restored manually. One of the most popular ways to restore objects.
3. Using AD Recycle Bin (Windows Server 2008 R2)
In Windows Server 2008 R2, an Active Directory Recycle Bin (AD RB) basket has appeared. To activate it, you need the forest level to be Windows Server 2008 R2. AD RB resembles an ordinary Windows recycle bin - an accidentally deleted object can be quickly and with all attributes restored. Moreover, the object restored from AD RB immediately receives all its attributes. By default, the life time of a remote object in AD RB is 180 days, after that it goes into the Recycle Bin Lifetime state, loses attributes and after some time is completely removed.
In the simplest case, the object is restored using the Powershell cmdlets Get-ADObject and Restore-ADObject (if you know exactly what you need to restore). The Get-ADObject cmdlet is used to retrieve a remote object, which is then passed through a pipeline to the Restore-ADObject cmdlet:
1. Run as administrator Active Directory Module for Windows PowerShell .
2. At the Active Directory module for Windows PowerShell command prompt, type the following command:
PS C:\> Get-ADObject -Filter {displayName -eq "user"} -IncludeDeletedObjects | Restore-ADObject In this example
-Filter {displayName -eq "user"} indicates what information about the AD object needs to be obtained (in the example, about the object with the display name of the user “user),
-IncludeDeletedObjects means that the search is carried out on remote objects
Restore-ADObject directly restores the AD object.
Search for deleted objects
1. Run as administrator Active Directory Module for Windows PowerShell.
2. In the Active Directory module for Windows PowerShell command line, enter the following commands to get the necessary information:
Displaying information about deleted objects in the acme.com domain
Get-ADObject -SearchBase "CN=Deleted Objects,DC=acme,DC=com" –IncludeDeletedObjects Get information about which OU the remote user was in
Get-ADObject -SearchBase "CN=Deleted Objects,DC=acme,DC=com" -ldapFilter:"(msDs-lastKnownRDN=User)" –IncludeDeletedObjects –Properties lastKnownParent Where User is the display name of the user.
As a result, we obtain information about the belonging to the OU of the specified user (using -Properties lastKnownParent )
Search for all deleted objects that belonged to this OU
As an example, take the distinguished name OU Finance_Department, which was obtained after the launch of the previous cmdlet (Finance_Department \\ 0ADEL: e954edda-db8c-41be-bbbd-599bef5a5f2a).
Get-ADObject –SearchBase "CN=Deleted Objects,DC=acme,DC=com" -Filter {lastKnownParent -eq 'OU=Finance_Department\\0ADEL:e954edda-db8c-41be-bbbd-599bef5a5f2a,CN=Deleted Objects,DC=acme,DC=com'} -IncludeDeletedObjects -Properties lastKnownParent | ft Attention! If you have a nested OU, recovery is performed starting from the highest level of the hierarchy. In this case, it is OU = Finance_Department.
Object Recovery
1. Launch the Active Directory Module for Windows PowerShell
2. Restore the Finance_Department subdivision by executing the following command on the command line:
Get-ADObject -ldapFilter:"(msDS-LastKnownRDN=Finance_Department)" –IncludeDeletedObjects | Restore-ADObject 3. We restore the accounts and OUs that are direct subsidiaries of the OU Finance_Department (remember that at this stage the distinguished name Finance_Department has already been restored to OU = Finance_Department, DC = acme, DC = com)
Get-ADObject -SearchBase "CN=Deleted Objects,DC=acme,DC=com" -Filter {lastKnownParent -eq "OU=Finance_Department,DC=acme,DC=com"} -IncludeDeletedObjects | Restore-ADObject Optional (restore nested OUs)
4. We restore the accounts included in the nested OU (for example, OU Admins, which is part of the OU Finance Department. The distinguished name in our example was restored to OU = Admins, OU = Finance_Department, DC = acme, DC = com)
Get-ADObject -SearchBase "CN=Deleted Objects,DC=acme,DC=com" -Filter {lastKnownParent -eq "OU=Admins,OU=Finance_Department,DC=acme,DC=com"} -IncludeDeletedObjects | Restore-ADObject Detailed help on cmdlets and their parameters by calling the Get-Help cmdlet, for example, Get-Help Get-ADObject
Total:
Objects will be restored to their original form - with all attributes.
However, as we can see, this method is rather complicated when you have to work with a large number of objects.
Also required, all servers in the forest must be Windows 2008 R2.
To restore objects with attributes when the AD basket is enabled, you can use the LDP and AdRestore tools described above.
4. Force recovery using NTDSUTIL
The standard way (but, however, not the most appropriate) is to force a restore from a backup in Directory Service Restore Mode . It has serious drawbacks: you need to restart the server, and secondly, restore the state of the system from the backup and mark which objects will not be overwritten by the replication process.
Restoration is performed using the NTDSUTIL command line utility . The utility becomes available after installing the AD DS role. Using it, you can restore both the OU with all its contents and a separate object.
The utility is based on snapshots of Active Directory, which are made using VSS.
Attention! During the forced recovery of AD, the internal version number of the objects being restored is increased. After connecting the domain controller to the network, these objects will be replicated throughout the domain, and the restored version becomes globally active.
Procedure:
1. We need to restore OU Finance_Department from the domain acme.com
2. Boot into DSRM mode (in the boot menu, press F8) and register with the password, DSRM, set during Dcpromo . AD does not load, the database is taken offline.
Attention! Recovery cannot be performed if NTDS AD is stopped on Server 2008 and above domain controllers.
3. Restore the system state from the backup created before the accident.
Attention! Do not restart the computer.
In the snapshot obtained using ntdsutil, there is both the object itself and its attributes. The image can be mounted and mounted as a virtual LDAP server exporting objects. Run ntdsutil :
> ntdsutil ntdsutil: snapshot View the list of available images:
: list all 1: 2009/04/22: 23: 18 {8378f4fe-94c2-4479-b0e6-ab46b2d88225}
2: C: {732fdf7f-9133-4e62-a7e2-2362227a8c8e}
3: 2009/04/23: 00: 19 {6f7aca49-8959-4bdf-a668-6172d28ddde6}
4: C: {cd17412a-387b-47d1-9d67-1972f49d6706}
Mount with mount command with number or {ID}:
: mount 4 {cd17412a-387b-47d1-9d67-1972f49d6706} C:\$SNAP_200904230019_VOLUMEC$\ The picture is mounted.
4. Run the command
To restore Finance_Department
> ntdsutil "authoritative restore" "restore subtree ou=Finance_Department,dc=acme,dc=com" qq As a result, OU Finance_Department with its member accounts and OU Admins will be restored.
To restore a separate account, for example, with the display name Oleg
> ntdsutil "authoritative restore" "restore object cn=Oleg,ou=Finance_Department,dc=acme,dc=com" qq 5. You must confirm the safety warnings. Then a message similar to that shown in Figure 3 will be displayed. Note the generated text and LDIF files.

Reboot the DC in the normal operating system startup mode.
7. Log on to DC and open a command prompt. Import the LDIF file exported in step 5 by executing
ldifde -i -f ar_20110221-151131_links_contoso.com.ldf where ar_20110221-151131_links_contoso.com.ldf is the name of the generated LDIF file.
8. As a result, the values of the associated attributes (such as group membership) for the restored objects will be imported.
Attention! If the forest contains multiple domains, you must use the text file exported in step 6 to restore local group memberships of other domains.
Total:
Accounts and objects were restored, but the Active Directory database was unavailable for a certain period of time. You also depend on the availability of up-to-date AD databases, relying on this recovery method.
5. NetWrix Active Directory Object Restore Wizard
The process of restoring objects can be greatly simplified if you use the NetWrix Active Directory Object Restore Wizard .
Just want to note that our company is constantly being contacted by administrators who have deleted AD objects and now want to restore them. The solution we propose — the NetWrix Active Directory Object Restore Wizard — although it can simplify the process of restoring objects (for example, restore OU with all objects and their attributes in a couple of clicks), it still does not work wonders - the program should be installed in the domain and periodically snapshots AD. Therefore, we recommend after reading the article still put the program to work (there is a free version with a recovery period for the last 4 days), so that next time you do not have such problems with the restoration of objects.
The utility allows you to recover deleted objects in a couple of clicks, and if the program worked before deleting objects in the domain, then all the attributes are restored. As a result, you get returned accounts in a couple of minutes without major disruptions in the organization. Also note that the program allows you to recover deleted mailboxes.
Work with the program is reduced to the following steps:
1. The NetWrix Active Directory Object Restore Wizard starts.

2. Select the recovery mode:
• Only from tombstone objects (if the program has not been installed before in the domain)
• Recovery using snapshots (if the program was installed and at least one snapshot was made)

3. Based on the analysis results, a list of deleted objects with their original hierarchy and objects is displayed.

4. Select those OU or objects that you want to restore, and click on
5. Depending on whether the program was installed earlier or not:
• If not, then you must manually restore group memberships and user passwords.
• If the program was installed, then the recovery is complete and everything will work as if nothing had happened.

As you can see, the restoration of objects takes much less time than using standard tools for repairing Active Directory objects.
But the restoration of objects is only one of the sides of the program. You can also roll back changes to objects - up to the value of a single attribute - the program is designed for this too.
Total:
Restoring objects with attributes is reduced to a couple of simple steps. It is possible not only to restore objects, but also to roll back only some of their values.
All these recovery methods are listed in the “First Aid Kit for AD Object Recovery”, which you can download on our website.
Source: https://habr.com/ru/post/150460/
All Articles