Windows 8 tells Microsoft about any installable programs.

As promised, in early August, Microsoft released the release preview version of its most controversial operating system in recent years, Windows 8, for almost free download. It was immediately accessed by researchers and interested people, including Nadeem Kobeissi, who is 24 August 2 published data that one of the poorly known utilities of Windows 8 sends information about all installed Microsoft applications. Such a collection of data about the user could potentially lead to persecution - not only judicial, but also political, for example, in those regions where the situation is unstable.
For some time on one of his computers, Nadim used the RTM version of Windows 8 with great pleasure, noting the excellent speed and design of the functionality of a representative of a popular line of operating systems. But while studying security issues, the problem that interested him was revealed.
')
Windows 8 has a feature called Windows SmartScreen, which is turned on by default. This function is intended to monitor all applications that the user tries to install in order to warn about the security status of the installed program.
The scheme of work is simple: after opening the installer of any software package - for example, a browser, image editor or text editor - Windows SmartScreen collects some identification information about the application and sends data to the Microsoft server. If an answer is received that the application is not signed with the necessary certificate, the user will decide whether to start the installer or ignore it. If there is no Internet connection, a warning will be displayed that it is impossible to verify that the launch of the application is valid.

In addition to the direct problem of the presence of default surveillance for any attempts to install programs as violations of the privacy of actions, it is worth noting the possibility of pressure on Microsoft to issue data to government agencies and legal representatives of major copyright holders.
The flow of information sent can also be intercepted. So you can learn what programs the user installs. Nadeem noticed that SmartScreen connects via HTTPS to the apprep.smartscreen.microsoft.com server, where requests are processed by the Microsoft IIS 7.5 server.

The server on the Microsoft side is configured in such a way that it can receive requests encrypted by the SSLv2 protocol, which is known to have been compromised. Encryption certificate provided by GTE CyberTrust Global Root to Microsoft Secure Server Authority; previously, the digital certificate center model has proven its vulnerability.
According to Microsoft , SmartScreen only sends the installer’s hash and its digital signature (if any). However, knowing the external IP address is enough to establish, if necessary, that a certain person has tried to install a specific program. Another researcher studied the chronicles of Nadim’s panic and found that the file name was also sent.
<Rq V="1.2">
<RqT>0</RqT>
<App>
<FName>U2FtZUdhbWUuZXhl</FName>
<FHash>d3ff5939726c9f8fa6e514fb65eb470a1f9ec7a65b2706732
a03749226c2520</FHash>
<Sig>0</Sig>
<Sz>45056</Sz>
<M>1</M>
<SR>100</SR>
</App>
<ID>0F98AD9C-D498-42B3-B421-E6C97A8E61E7</ID>
<G>B68802CA-B396-4773-8FD9-EEECA4DE65D9</G>
<L>ZW4tVVM=</L>
<OS>6.2.9200.0.0</OS>
<I>OS4xMC45MjAwLjE2Mzg0</I>
<C>10.00.9200.16384</C>
<DJ>2</DJ>
</Rq>FName — base64 - , FHash — SHA-256 .
SmartScreen , .
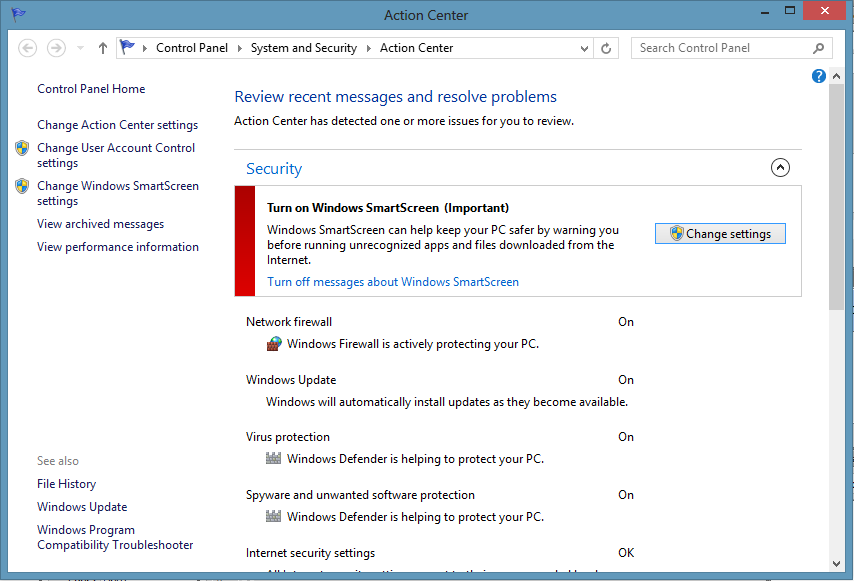
SmartScreen, System and Security, Action Center Windows SmartScreen.

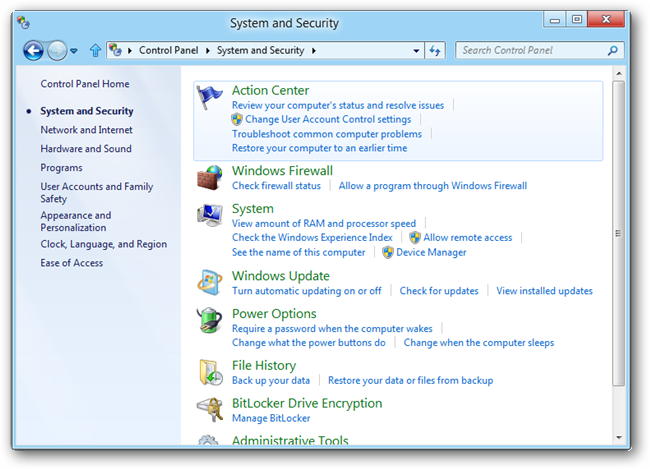

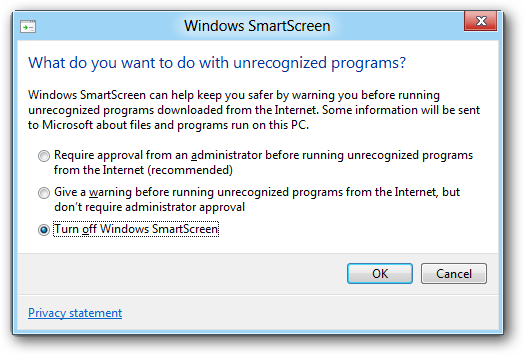
, , , IP-. , : Microsoft , , Metro. , , SmartScreen .
Source: https://habr.com/ru/post/150192/
All Articles