WPA2-Enterprise, or the right approach to Wi-Fi network security
 Recently, there have been many “exposing” publications about hacking into any regular protocol or technology that compromises the security of wireless networks. Is it really so, what is it worth being afraid of, and how to ensure that access to your network is as secure as possible? The words WEP, WPA, 802.1x, EAP, PKI mean little to you? This short overview will help bring together all the applied encryption technology and authorization of radio access. I will try to show that a properly configured wireless network is an insurmountable barrier for an attacker (up to a certain limit, of course).
Recently, there have been many “exposing” publications about hacking into any regular protocol or technology that compromises the security of wireless networks. Is it really so, what is it worth being afraid of, and how to ensure that access to your network is as secure as possible? The words WEP, WPA, 802.1x, EAP, PKI mean little to you? This short overview will help bring together all the applied encryption technology and authorization of radio access. I will try to show that a properly configured wireless network is an insurmountable barrier for an attacker (up to a certain limit, of course).The basics
Any interaction between the access point (network) and the wireless client is built on:
')
- Authentication - as the client and the access point are presented to each other and confirm that they have the right to communicate with each other;
- Encryption - which scrambling algorithm of the transmitted data is applied, how the encryption key is generated, and when it changes.
Wireless network settings, first of all its name (SSID), are regularly announced by the access point in broadcast beacon packets. In addition to the expected security settings, wishes are transmitted on QoS, on 802.11n parameters, supported speeds, information on other neighbors, and so on. Authentication defines how a client is presented to a point. Possible options:
- Open - the so-called open network, in which all connected devices are authorized immediately
- Shared - the authenticity of the device to be connected must be verified with a key / password
- EAP - the authenticity of the connected device must be verified by the EAP protocol by an external server
The openness of the network does not mean that anyone can work with it with impunity. In order to transmit data in such a network, it is necessary to match the encryption algorithm used, and, accordingly, to establish the encrypted connection correctly. The encryption algorithms are as follows:
- None - no encryption, data is transmitted in the clear
- WEP - cipher based on RC4 algorithm with different length of static or dynamic key (64 or 128 bits)
- CKIP is Cisco's proprietary replacement of WEP, an early version of TKIP
- TKIP - Improved WEP Replacement with Additional Checks and Security
- AES / CCMP is the most advanced algorithm based on AES256 with additional checks and security.
The combination of Open Authentication, No Encryption is widely used in guest access systems such as the provision of the Internet in a cafe or hotel. To connect you need to know only the name of the wireless network. Often such a connection is combined with an additional check on the Captive Portal by redirecting a custom HTTP request to an additional page where you can request confirmation (login and password, agreement with the rules, etc.).
WEP encryption is compromised and cannot be used (even in the case of dynamic keys).
The widely used terms WPA and WPA2 define, in fact, the encryption algorithm (TKIP or AES). Since client adapters support WPA2 (AES) for quite some time, it makes no sense to use TKIP encryption.
The difference between WPA2 Personal and WPA2 Enterprise is where the encryption keys come from, which are used in the mechanics of the AES algorithm. For private (home, small) applications, a static key (password, code word, PSK (Pre-Shared Key)) is used with a minimum length of 8 characters, which is set in the access point settings, and all clients of this wireless network are the same. The compromise of such a key (they let the neighbor talk, the employee was dismissed, the laptop was stolen) requires that all remaining users immediately change the password, which is realistic only in the case of a small number of them. For corporate applications, as the name implies, a dynamic key is used that is individual for each working client at the moment. This key can be periodically updated as you work without breaking the connection, and an additional component — the authorization server — is responsible for generating it, and it is almost always a RADIUS server.
All possible security parameters are summarized in this table:
| Property | Static WEP | Dynamic WEP | WPA | WPA 2 (Enterprise) |
| Identification | User, computer, WLAN card | User computer | User computer | User computer |
| Authorization | Shared key | EAP | EAP or Shared Key | EAP or Shared Key |
Integrity | 32-bit Integrity Check Value (ICV) | 32-bit ICV | 64-bit Message Integrity Code (MIC) | CRT / CBC-MAC (Counter Mode Cipher Block Chain Auth Code - CCM) Part of AES |
Encryption | Static key | Session key | Per key via TKIP | CCMP (AES) |
Key distribution | Single, manually | Pair-wise Master Key (PMK) Segment | Derived from PMK | Derived from PMK |
Initialization vector | 24 bit text | 24 bit text | Extended vector, 65 bits | 48-bit packet number (PN) |
Algorithm | RC4 | RC4 | RC4 | AES |
Key length, bit | 64/128 | 64/128 | 128 | up to 256 |
Required infrastructure | Not | RADIUS | RADIUS | RADIUS |
If everything is clear with WPA2 Personal (WPA2 PSK), the corporate solution requires additional consideration.
WPA2 Enterprise
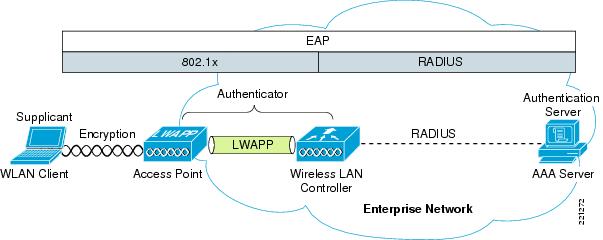
Here we are dealing with an additional set of different protocols. On the client side, a special software component, supplicant (usually part of the OS), interacts with the authorizing part, the AAA server. This example displays the operation of a unified radio network built on lightweight access points and a controller. In case of using “with brains” access points, the entire point of intermediary between clients and the server can be assumed by the point itself. In this case, the data of the client supplikant are transmitted by radio to the 802.1x protocol (EAPOL), and on the controller side, they are wrapped in RADIUS packets.
The use of EAP authorization mechanism in your network leads to the fact that after successful (almost certainly open) client authentication by the access point (together with the controller, if any), the latter asks the client to authorize (confirm its credentials) from the RADIUS infrastructure server
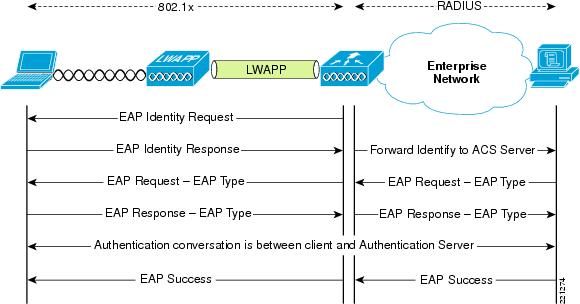
Using WPA2 Enterprise requires that you have a RADIUS server on your network. To date, the most efficient are the following products:
- Microsoft Network Policy Server (NPS), formerly IAS - configurable via MMC, is free, but you need to buy Windows
- Cisco Secure Access Control Server (ACS) 4.2, 5.3 — configurable via a web interface, enhanced by functionality, allows you to create distributed and fault-tolerant systems, it is expensive
- FreeRADIUS is free, configurable by text configs, it is not convenient to manage and monitor
In this case, the controller closely monitors the ongoing exchange of information, and waits for successful authorization, or failure of it. If successful, the RADIUS server is able to transfer additional parameters to the access point (for example, in which VLAN to place the subscriber, which IP address, QoS profile, etc.) to assign to it. At the end of the exchange, the RADIUS server allows the client and the access point to generate and exchange encryption keys (individual, valid for this session only):
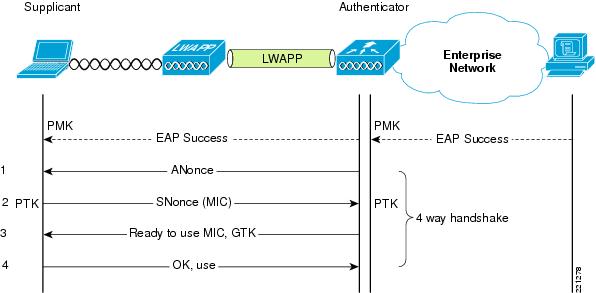
EAP
The EAP protocol itself is containerized, that is, the actual authorization mechanism is given at the mercy of the internal protocols. To date, the following have become of some significant distribution:
- EAP-FAST (Flexible Authentication via Secure Tunneling) - developed by Cisco; allows to perform authorization using a login password transmitted within the TLS tunnel between the supplikant and the RADIUS server
- EAP-TLS (Transport Layer Security). It uses the public key infrastructure (PKI) to authorize the client and server (supplikant and RADIUS server) through certificates issued by a trusted authority (CA). It requires the issuance and installation of client certificates for each wireless device, therefore, it is suitable only for a managed corporate environment. Windows Certificate Server has the means to allow the client to independently generate a certificate if the client is a member of a domain. Blocking a client is easily done by revoking his certificate (or through accounts).
- EAP-TTLS (Tunneled Transport Layer Security) is similar to EAP-TLS, but a client certificate is not required when creating a tunnel. In such a tunnel, similar to the SSL connection of the browser, additional authorization is made (by password or something else).
- PEAP-MSCHAPv2 (Protected EAP) - similar to EAP-TTLS in terms of the initial establishment of an encrypted TLS tunnel between a client and a server, requiring a server certificate. Further, in such a tunnel, authorization occurs according to the well-known MSCHAPv2 protocol.
- PEAP-GTC (Generic Token Card) - similar to the previous one, but requires one-time password cards (and the corresponding infrastructure)
All of these methods (except EAP-FAST) require a server certificate (on a RADIUS server) issued by a certification authority (CA). At the same time, the CA certificate itself must be present on the client device in the trusted group (which is easy to implement using Group Policy in Windows). Additionally, EAP-TLS requires an individual client certificate. Client authentication is performed both digitally and (optionally) comparing the certificate provided by the client to the RADIUS server with what the server extracted from the PKI infrastructure (Active Directory).
Support for any of the EAP methods should be provided by the client side supplicant. Standard, built-in Windows XP / Vista / 7, iOS, Android provides at least EAP-TLS, and EAP-MSCHAPv2, which makes these methods popular. Intel client adapters for Windows come with a ProSet utility that extends the available list. The Cisco AnyConnect Client does the same.

How reliable is it
In the end, what does an attacker need to hack into your network?
For Open Authentication, No Encryption - nothing. Connected to the network, that's all. Since the radio environment is open, the signal spreads in different directions, blocking it is not easy. With the appropriate client adapters that allow you to listen to the broadcast, the network traffic is visible just as if the attacker connected to the wire, to the hub, to the SPAN port of the switch.
WEP-based encryption requires only an IV scan time, and one of many freely available scanning utilities.
For encryption based on TKIP or AES, direct decryption is possible in theory, but in practice there have been no cases of hacking.
Of course, you can try to find a PSK key, or a password to one of the EAP methods. Common attacks on these methods are not known. You can try to apply the methods of social engineering, or thermorectal cryptanalysis .
You can get access to the network protected by EAP-FAST, EAP-TTLS, PEAP-MSCHAPv2 only if you know the username and password of the user (hacking is not possible as such). Brute-force attacks, or those aimed at vulnerabilities in MSCHAP, are also not possible or difficult because the client-server EAP channel is protected by an encrypted tunnel.
Access to a network closed by PEAP-GTC is possible either by hacking the token server or by stealing a token with its password.
Access to a network closed by EAP-TLS is possible by stealing a user certificate (along with its private key, of course), or by issuing a valid, but fake certificate. This is only possible if the certification center is compromised, which in normal companies is protected as the most valuable IT resource.
Since all the above-mentioned methods (except PEAP-GTC) allow saving (caching) passwords / certificates, then if a mobile device is stolen, an attacker gets full access without unnecessary questions from the network. As a measure of prevention, full encryption of the hard disk can be used with a password request when the device is turned on.
Remember: with proper design, the wireless network can be very well protected; means of hacking such a network does not exist (to a certain limit)
Source: https://habr.com/ru/post/150179/
All Articles