Access to the information. Internal audit
Tedious Brief Introduction.
As a rule, when protecting information, the entire security perimeter is built from the outside. Probably logical because the main threats are coming from there. But the search for vulnerabilities from the outside is quite a laborious and creative exercise, involving the search for holes in php, SQL injection, network vulnerabilities, searching a couple of billions of md5 hashes, etc.
This leaves out of consideration the possibility of access to information from within. Which is protected as a rule is much weaker. Apparently it is believed that if there are holes - they are all outside - because inside something monolithic and impenetrable.
So. In my short article I want to slightly immerse the reader in the slightly childlike and naive world of large organizations, where the majority believe in

Situation:
- Big company (thousands of PCs)
- Availability of database and software of own or third-party developers
- There is no pass-through authentication between the domain account, database and software. Those. dozens of applications - everywhere your login and password
')
Classic problems:
- Shaggy programs are not obvious enough and changing the password is difficult. Those. after the user's entry, he continues to use the password given to him. Often, the user even thinks that it is necessary. I personally used the application from one of the largest corporations in the world every day many times, and only 2 years later I found a dialogue with the proposal to change the password. Before that, I used the standard password “12345”
- In large firms, a large staff turnover. An annual turnover of 10-30% of staff is ridiculous for a firm of 10, 20 or 50 people. And if the company has 1,000 people? Those. several hundred people annually leave and, of
course,as a rule, access to the domain is blocked. What about other applications? - And if the employee did not quit, and moved from one unit to another? For example, the former domain administrator and moved to the business unit. The perfect insider through which you can get all the information about the company. He not only knows where the key information of the company is, but how to get it.
- The employee goes on a very long vacation. Do everyone remember to block access in these cases?
- An employee does not leave or translate anywhere. But it uses the password "" (no password) or "12345678"
- All of the above problems can be multiplied by human negligence, laziness and the banal overloading of personnel service and iT, which already lack enough turnover.
In general, the result of this list of problems - the larger the company, the more internal problems it accumulates. Because in small ones, as a rule, everything is tied to a domain, 1C and a pair of standard software complexes
Solutions (Ideally)
- user training (“meaning? teach - tomorrow quit” - management response)
- tie everything to the domain and to the domain account (technically it is not always realizable, it requires, as a rule, money and resources that are difficult to justify)
- get rid of the keyboard password, with reference to the tangible medium (difficulties in using specialized software and hardware, as well as constant “oh - forgotten at home” and combating it - screwing the hardware key to the reader connector)
- use "captcha", limiting login attempts by the number of attempts, ip-address and other creative approaches in self-written software
Solutions (in practice)
- wait for an incident - plug a specific hole
- regular perimeter audit
The last pro-active option, which I want to consider in practice. A general algorithm that fits most applications:
- open the list of employees
- open the program
- we select application for check
- enter the login / password combinations until the list of employees and simple passwords is over
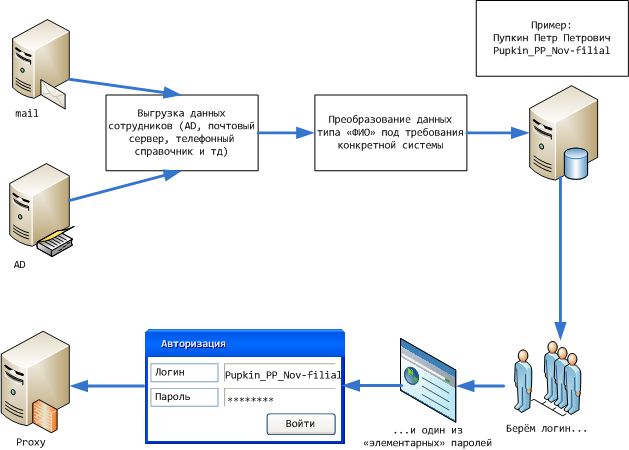
Agree - nothing complicated, but rather time-consuming process if done by hand. Even the "sweetness" of victory - the detection of 1.2, well, or 100 "bad guys" will not give anything. After a few months, when you re-check, you will have to shovel the entire list + bonus in the form of new employees. Need to automate.
You can write on anything. Personally, I will not break copies - previously I did such things on Delphi and VS, but after a casual acquaintance with the scripting language AutoIT stopped on it. This piece is just made for the FAST writing of click-intro universal utility tools. Those. when there is no goal to count 9 ^ 9 ^ 9 combinations per second as hashes, working directly with the API application (especially if it is under Citrix), and it’s enough to click on a dozen different applications across several password combinations — for the real list of employees.
As the simplest example in my article, I want to set an example of an audit of Internet access in an organization.
Specific example
Squid-proxy. There is no limit on password selection. Those. it is possible to go through logins until the blue one at a high speed also in parallel. But let's be honest - the result in 1 minute or a few days - it does not matter. The speed of checking one password is about 5 seconds per one account. The main thing is the lack of manual labor and so far the only program in the world sorting out passwords on a proxy server is enough for success. Leaving in the evening from work, we start, in the morning we are reaping the result.
The results of the scan in my case I do not publish, because they were
; (c) lokkii ; ProxyLoginChecker v. 0.1 beta ; 1) (passwd) Squid Win- ( -8) ; 2) : out.txt , , , log.txt login:time $file_in = FileOpen("passwd", 0) ; If $file_in = -1 Then MsgBox(0, "Error", " passwd") Exit EndIf $file_out = FileOpen("out.txt", 2) ; If $file_out = -1 Then MsgBox(0, "Error", " out.txt") Exit EndIf $file_log = FileOpen("log.txt", 2) ; If $file_log = -1 Then MsgBox(0, "Error", " log.txt") Exit EndIf ; , While 1 $line = FileReadLine($file_in) if @error = -1 Then ExitLoop ; squid ; : ;pupkin_pp:x:544:502:% :/dev/null:/dev/null ; : $login = pupkin_pp ; $pwd = pup123 ; $fio = $login = StringLeft($line, StringInStr($line, ":x:")-1+”_Nov-filial”); "pupkin_pp_Nov-filial" $pwd = StringLeft($login, 3) & “123”; “pup123" $line = StringTrimLeft( $line, StringInStr($line, "502:")+3 ) ; $line = StringTrimLeft( $line, StringInStr($line, "%")) ; ( ) "%" - $fio = StringReplace ( $line, ":/dev/null:/dev/null", "") ; $proxy = "192.168.0.1:8080" HttpSetProxy ( 2 , $proxy , $login, $pwd); $size = InetGetSize("http:// /.txt") if $size == 33333 then FileWriteLine($file_out, $login & ";"& $pwd & ";" & $fio & @CRLF) FileWriteLine($file_log, $login & ";" & @HOUR & ":" & @MIN & ":" & @SEC & @CRLF) Wend FileClose($file_in) FileClose($file_out) FileClose($file_log) findings
Now you can
Thanks for reading! I hope that the article was interesting for you (only the source code was omitted), makes you think and bring new ideas to your work.
ps Though I prefer to use passwords like “password”, on Wi-Fi access points “123456789”, etc. But nevertheless I cry - do not do it!
Source: https://habr.com/ru/post/149859/
All Articles