Overview of vulnerabilities on the Big Three sites
Introduction
Some time ago I came across the usual xss on the MTS website.
To my surprise, there was no limit, how could the developers of such a company make such a banal mistake ?!
A couple of days ago, remembering that xss, it was decided to conduct a search for vulnerabilities on the sites of the big three.
Then I realized that they were flowers.
A friend of mine told this story:
Search for potential targets
The search was carried out by hand, so far not all were found, I am sure.
But what was found shocked me.
')
For the search was used dork site: site.com inurl: php
Beeline
It's all not so much scary, how much.
But it was the only operator on which the disclosures were found.
Do not be surprised that with them there sql inj, but my hacker skill is not so pumped, that would unleash them.
Disclosure ways:
wap.privet.beeline.ru

Uncovering paths # 2 + chopped xss:
wap.privet.beeline.ru
It is cut by the fact that the output function truncates the input data.
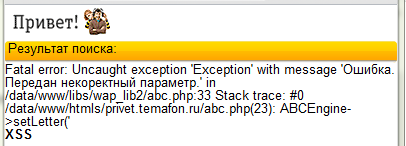
Full xss:
ts.beeline.ru

Full xss # 2:
signup.beeline.ru

What the hell This is generally a strange thing. Muscle error is caused by the transfer of Russian characters. Moreover, judging by the search results, it once worked for a long time normally, but now it has broken.
eshop.beeline.ru
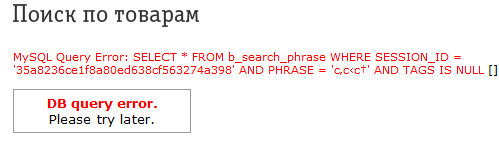
At this point I ended up with biline. Despite the fact that there I found the most, and not turned off the error output, I did not find critical vulnerabilities (at least obvious ones).
Megafon
For some reason, I thought that a megaphone should have fewer errors.
And, in part, I was right.
For all that you can pops up 500 error, such as here or here .
But then suddenly SQL Injection was found!
For objective reasons, I will not post a link to it, who should find it myself, and in Megafon they are already aware of it. As evidence, you can only show the following:
http://fy2011.megafon.ru

Shell failed to upload to the server, due to competently set rights, but passwords 111 and 123 are brute force.
But on the site of creators with the rights of no one bother.
And by the way, I was not the first who appeared on their website: D
By the way, the creators made a presentation for Skolkovo, which was shown to the President, and they are very proud of it .
www.downstream.ru .
Mts
From the very beginning, I wanted to start writing exactly with MTS.
But then everything turned out not as beautiful as it should have been, but I will write more in detail about it.
For starters, this is the xss on the store website.
www.shop.mts.ru-

The second was on the wap portal:
pulse.mts.ru
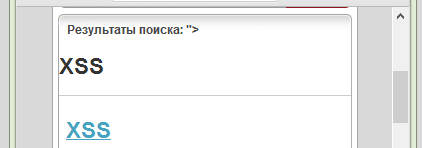
And then SQL Injection was found
I must say that it did not belong to MTS, it belonged to the Ukrainian supplier of resources for mobile phones.
Server admin, and probably adminit still some Slava and Anton, according to some data found on the site, it seems that Slava is the creator of travel.org.ua.
Programmers from the guys came out not very much, because they didn't seem to know about filtering the input at all, but I would even like to praise them for their server administration skills.
Unfortunately, my shell was removed after a few hours, after pouring, but I did not manage to spin the server.
Yes, and I think they would have burned it too.
Shell was flooded via video.sport.mts.ru.
Actually for the inability to create users of mysql with limited rights, Glory should be reprimanded.
On his website, connecting to mysql is made with the help of a user with root rights.
Conclusion
All vulnerabilities are sent to support operators.
Thank you for inspecting the text to the end.
Criticism and indications of errors in the text with pleasure I will accept in HP.
Information for admins sites:
remained
http://pulse.mts.ru (but not for long, I think)
http://signup.beeline.ru
http://eshop.beeline.ru
And to a megaphone, or downstream - change the passwords, otherwise I may not know them alone.
Source: https://habr.com/ru/post/149596/
All Articles