AirOS vulnerability
I decided to talk about the vulnerability of AirOS using the example of hacking NanoStation M2.
It all started with the fact that I was connected to the Internet. And since I live in the private sector, the provider has installed wi-fi directed and on my roof the NanoStation M2 2.4 GHz .
I was very indignant that I was not informed of either the wi-fi password or the NanoStation password (although the reasons are completely clear to me). As I received the password from wi-fi read under a cat.
When I learned that the access point was working on AirOS based on linux, I easily found a description of the vulnerability of this OS on the network.
Further I come on a link 192.168.1 . *** / admin.cgi / ds.css
And I understand that I received almost complete access to the OS.

')
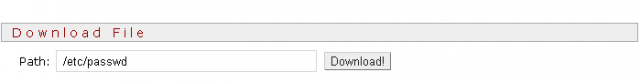
Downloading the / etc / passwd file
Saw the following contents
As well as it is necessary the password is hashed. Of course, it was also possible to download the password change script and understand its algorithm, but I decided to make it easier. The /usr/etc/system.cfg file contains default settings, including the ubnt password hash.
Next, on my machine I edit the downloaded passwd file by changing the password hash to default
and pour it on the access point

then left to put it in place

Profit =)
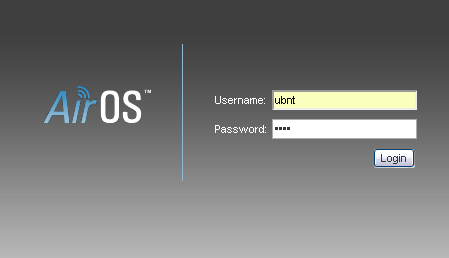
We go to the access point by default login / password ubnt / ubnt
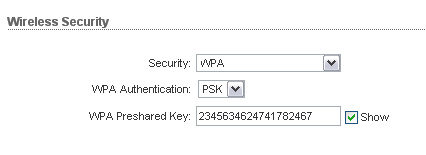
Find out the password from wi-fi is already a matter of technology
These manipulations did not give me full access to the OS. because When changing the password, the OS swears that the password “ubnt” is not correct, but I got the desired result.
I hope someone will tell you how to completely reset / change the password.
It all started with the fact that I was connected to the Internet. And since I live in the private sector, the provider has installed wi-fi directed and on my roof the NanoStation M2 2.4 GHz .
I was very indignant that I was not informed of either the wi-fi password or the NanoStation password (although the reasons are completely clear to me). As I received the password from wi-fi read under a cat.
When I learned that the access point was working on AirOS based on linux, I easily found a description of the vulnerability of this OS on the network.
Further I come on a link 192.168.1 . *** / admin.cgi / ds.css
And I understand that I received almost complete access to the OS.

')
Downloading the / etc / passwd file

Saw the following contents
ubnt:PpI8IMUqKVKCw:0:0:Administrator:/etc/persistent:/bin/sh
As well as it is necessary the password is hashed. Of course, it was also possible to download the password change script and understand its algorithm, but I decided to make it easier. The /usr/etc/system.cfg file contains default settings, including the ubnt password hash.
users.status=enabled
users.1.status=enabled
users.1.name=ubnt
users.1.password=VvpvCwhccFv6QNext, on my machine I edit the downloaded passwd file by changing the password hash to default
ubnt:VvpvCwhccFv6Q:0:0:Administrator:/etc/persistent:/bin/shand pour it on the access point

then left to put it in place

Profit =)
We go to the access point by default login / password ubnt / ubnt

Find out the password from wi-fi is already a matter of technology

These manipulations did not give me full access to the OS. because When changing the password, the OS swears that the password “ubnt” is not correct, but I got the desired result.
I hope someone will tell you how to completely reset / change the password.
Source: https://habr.com/ru/post/149103/
All Articles