Developed a system for storing passwords in the subconscious
 An interdisciplinary team of scientists from Stanford and Northwestern University, consisting of specialists in cryptography and neuropsychology, has developed a fundamentally new authentication method that combines the strengths of biometrics and passwords. It allows you to save long sequences of random characters in the subconscious so that they can not be extracted either by torture or under hypnosis.
An interdisciplinary team of scientists from Stanford and Northwestern University, consisting of specialists in cryptography and neuropsychology, has developed a fundamentally new authentication method that combines the strengths of biometrics and passwords. It allows you to save long sequences of random characters in the subconscious so that they can not be extracted either by torture or under hypnosis.The method is not intended for mass everyday use - it takes about 45 minutes of training for subconsciously remembering a password, moreover, it does not give particular advantages in the case of remote access - attackers can always force or threaten the user to log in. Its main purpose is the physical control of access to closed areas and premises, for example, secret laboratories or bank vaults.
 To memorize a secret combination is used something like a computer game, reminiscent of Guitar Hero. Black circles fall along the six vertical tracks, and the user must press one of the six keys - S, D, F, J, K, or L, when they reach the bottom. (You can try the game live on the site , which scientists used to experiment with the help of Mechanical Turk ). Circles fall fast enough so that all the attention of the player is occupied by pressing the desired buttons. For 45 minutes of play, the user presses the buttons about 4000 times. 80% of these clicks are used to train the 30-character secret sequence. 20% are random and serve to prevent the brain from remembering the combination at a conscious level.
To memorize a secret combination is used something like a computer game, reminiscent of Guitar Hero. Black circles fall along the six vertical tracks, and the user must press one of the six keys - S, D, F, J, K, or L, when they reach the bottom. (You can try the game live on the site , which scientists used to experiment with the help of Mechanical Turk ). Circles fall fast enough so that all the attention of the player is occupied by pressing the desired buttons. For 45 minutes of play, the user presses the buttons about 4000 times. 80% of these clicks are used to train the 30-character secret sequence. 20% are random and serve to prevent the brain from remembering the combination at a conscious level.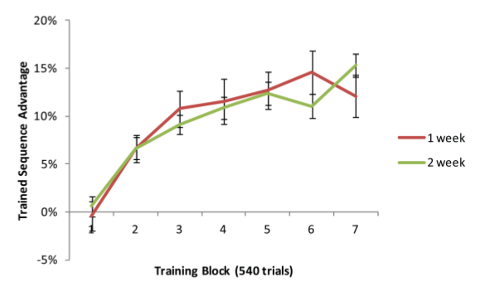 In order to be authenticated, you need to play the same game for a couple of minutes, in which the same combination will be involved, plus random characters. A trained user in the correct sequence will show a result 10-15% better than on a random set of letters. This is reminiscent of behavioral biometrics methods (using plain text on the keyboard, gait, and other usual activities to authenticate the dynamics of typing), but with two important advantages.
In order to be authenticated, you need to play the same game for a couple of minutes, in which the same combination will be involved, plus random characters. A trained user in the correct sequence will show a result 10-15% better than on a random set of letters. This is reminiscent of behavioral biometrics methods (using plain text on the keyboard, gait, and other usual activities to authenticate the dynamics of typing), but with two important advantages.')
A person performs usual actions every day, they can be recorded on video or using a keylogger, analyzed and learned to imitate. But to know the secret combination stored in the subconscious, it is impossible, even with a copy of the game on the local computer of the attacker. You can force the user to play it over and over again, but he will not be able to demonstrate his knowledge in any way until the right combination is presented to him.
Of course, it is theoretically possible to use statistical methods to extract a combination in parts, selecting and combining short sequences that work out slightly better than others, but this will take more than one hour (if not a week). And here comes the second advantage of this method. It took 45 minutes to memorize the correct sequence. If you play for a few more hours, provided that the game patched by the attacker tries to guess the sequence, which means that he repeatedly shoots the same, supposedly correct fragments, the brain will almost certainly forget the old combination.
Thanks to the same feature of the method, flexibility that is unattainable for biometrics appears. Unlike the retina pattern, fingerprints, voice, or gait, the combination can always be changed.
Here is a link to a PDF with a detailed description of the method, and a discussion of it at HackerNews .
Source: https://habr.com/ru/post/148122/
All Articles