Networks for the smallest. Part Five ACL and NAT
All issues
8. Networks for the smallest. Part Eight BGP and IP SLA
7. Networks for the smallest. Part Seven. VPN
6. Networks for the smallest. Part six. Dynamic routing
5. Networks for the smallest: Part Five. NAT and ACL
4. Networks for the smallest: Part Four. STP
3. Networks for the smallest: Part Three. Static routing
2. Networks for the smallest. Part two. Switching
1. Networks for the smallest. Part one. Connection to the equipment cisco
0. Networks for the smallest. Part zero. Planning
7. Networks for the smallest. Part Seven. VPN
6. Networks for the smallest. Part six. Dynamic routing
5. Networks for the smallest: Part Five. NAT and ACL
4. Networks for the smallest: Part Four. STP
3. Networks for the smallest: Part Three. Static routing
2. Networks for the smallest. Part two. Switching
1. Networks for the smallest. Part one. Connection to the equipment cisco
0. Networks for the smallest. Part zero. Planning
We continue the development of our small cozy network Elevator mi Up. We have already discussed issues of routing and stability, and now, finally, have grown to connect to the Internet. Enough imprisonment within our corporate environment!
But with the development there are new problems.
First, the virus paralyzed the web server, then someone jammed a worm that spread across the network, taking up part of the bandwidth. And some villain got into the habit of picking up passwords for ssh to the server.
Can you imagine what will begin when we connect to the Internet ?!
So today:
1) learn to configure various access control lists (Access Control List)
2) trying to understand the difference between the restriction of incoming and outgoing traffic
3) understand how NAT works, its pros, cons and opportunities
4) in practice, we organize the connection to the Internet through NAT and increase the network security using access lists.
Access Control List
So, what do we have to say about access lists? In fact, the topic is relatively simple and only the lazy ones from the CCNA course are not copied. But do not we break our amazing story because of some prejudice?
')
What is the purpose of access lists? It would seem that the obvious answer is to restrict access: for example, to forbid something to someone. In general, this is true, but it is necessary to understand it in a wider sense: it is not only about security. That is, initially, probably, it was so, hence permit and deny when setting up. But in fact, ACL is a versatile and powerful filtering mechanism. With their help, it is possible to determine on whom to hang certain politicians, and on whom not, who will participate in certain processes, and who will not, whom we limit to a speed of up to 56k, and who up to 56M.
To make it a little clearer, we give a simple example. Relying on access lists, Policy-Based Routing (PBR) works. Here you can make the packets coming from the network 192.168.1.0/24 go to the next-hop 10.0.1.1, and from the network 192.168.2.0/24 to 10.0.2.1 (note that the usual routing relies on the destination address of the packet and automatically packets are sent to one next-hop):

At the end of the article is an example of PBR setting and ACL-based speed limits .
ACL Types
Okay, let's forget this lyrics for a while.
Generally speaking, access lists are different:
- Standard
- Extended
- Dynamic
- Reflexive
- timed
We will focus our attention today on the first two, and in more detail about all you can read at tsiska .
Inbound and outbound traffic
For the initiative, let's deal with one thing. What is meant by incoming and outgoing traffic? We will need this in the future. Incoming traffic is the one that comes to the interface from the outside.

Outbound - the one that is sent from the interface to the outside.

You can apply the access list either to incoming traffic, then unwanted packets will not even get to the router and, accordingly, further into the network, or outgoing, then the packets arrive at the router, are processed by it, reach the target interface and only drop on it.
A standard access list checks only the sender's address. Extended - address of the sender, address of the recipient, as well as the port. Standard ACLs are recommended to be placed as close as possible to the recipient (in order not to cut more than necessary), and extended ones closer to the sender (in order to drop unwanted traffic as soon as possible).
Practice
Let's go straight to practice. What would we do to limit this in our small network “Elevator mi Up”?
a) WEB-server. Allow access to everyone over TCP port 80 (HTTP protocol). For the device from which management will be performed (we also have an admin), you need to open telnet and ftp, but we will give it full access. All the rest hang up.
b) File server. We have to get resident Lift me Up on ports for shared folders, and all the rest via FTP.
c) Mail Server. Here we have started SMTP and POP3, that is, TCP ports 25 and 110. We also open access to management for the admin. Others are blocking.
d) For the future DNS server you need to open UDP port 53
e) Allow ICMP messages to the server network
e) Since we have the Other network for all non-partisan who have not entered into the EF, VET and Accounting, we will restrict them all, and only give access to some (among them we and the admin)
g) In the control network, you need to start again just the admin, and of course yourself a loved one.
g) We will not build barriers to communication among the employees of the departments.
a) Access to the WEB-server
Here we have a policy that prohibits everything that is not allowed. Therefore, we now need to open something, and close everything else.
Since we are protecting the network of servers, we will hang the list on the interface going in the direction of them, that is, on FE0 / 0.3. Only in question or out we need to do this? If we do not want to allow packets towards servers that are already on the router, then this will be outgoing traffic. That is, we will have destination addresses in the network of servers (of which we will choose which server traffic is going to), and source addresses can be any - both from our corporate network and from the Internet.
One more note: since we will be filtering, including at the destination address (some rules on the WEB server, others on the mail server), we will need an extended (extended) access control list, only it allows us to do this.
The rules in the access list are checked in order from top to bottom until the first match. As soon as one of the rules has worked, regardless of whether to permit this or deny, the check is stopped and the traffic is processed based on the rule that was triggered.
That is, if we want to protect the WEB-server, then first of all we need to give permission, because if we configure deny ip any any in the first line, then it will always work and traffic will not go at all. Any is a special word that means network address and reverse mask 0.0.0.0 0.0.0.0 and means that absolutely all nodes from any networks fall under the rule. Another special word - host - it means the mask 255.255.255.255 - that is, it is one single specified address.
So, the first rule: allow access to all on port 80
msk-arbat-gw1 (config) # ip access-list extended Servers-out
msk-arbat-gw1 (config-ext-nacl) # remark WEB
msk-arbat-gw1 (config-ext-nacl) # permit tcp any host 172.16.0.2 eq 80
Allowing ( permit ) TCP traffic from any node ( any ) to a host ( host is exactly one address) 172.16.0.2 addressed to port 80.
We try to hang this access list on the FE0 / 0.3 interface:
msk-arbat-gw1 (config) # int fa0 / 0.3
msk-arbat-gw1 (config-subif) # ip access-group Servers- out
We check from any of our connected computers:
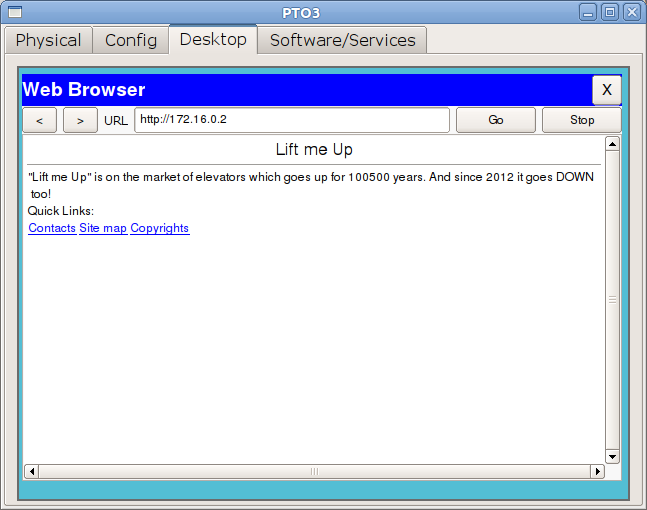
As you can see the page opens, but what about our ping?
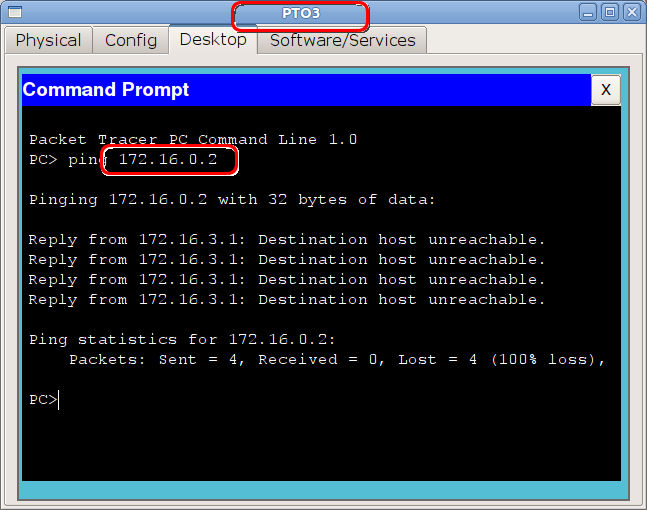
And so from any other node?
The fact is that after all the rules in the ciskov ACL at the end implicit deny ip any any (implicit deny) is added. What does this mean for us? Any packet leaving the interface and not responding to any rule from the ACL falls under implicit deny and is discarded. That is, at least ping, at least ftp, at least anything here will not work.
Go ahead: you need to give full access to the computer from which the control will be made. This will be the computer of our admin with the address 172.16.6.66 from the Other network.
Each new rule is added automatically to the end of the list if it already exists:
msk-arbat-gw1 (config) # ip access-list extended Servers-out
msk-arbat-gw1 (config-ext-nacl) # permit tcp host 172.16.6.66 host 172.16.0.2 range 20 ftp
msk-arbat-gw1 (config-ext-nacl) # permit tcp host 172.16.6.66 host 172.16.0.2 eq telnet
That's all. We check from the right node (since telnet is not supported by servers in RT, we check for FTP):
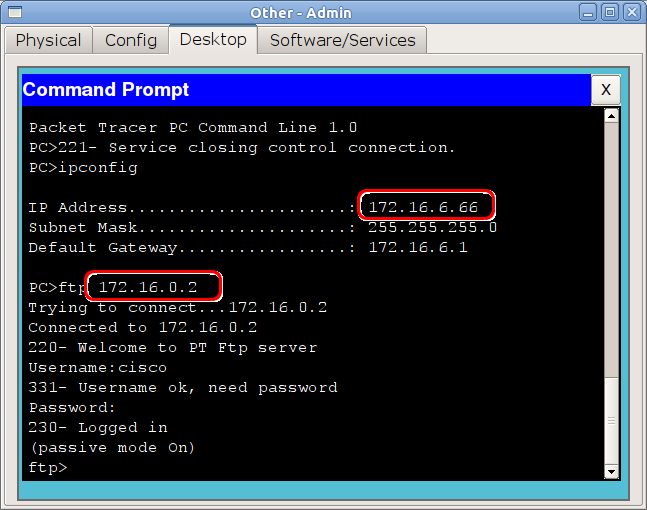
That is, an FTP message arrived at the router and should go away from the FE0 / 0.3 interface. The router checks and sees that the packet matches the rule added by us and skips it.
And from an outside node
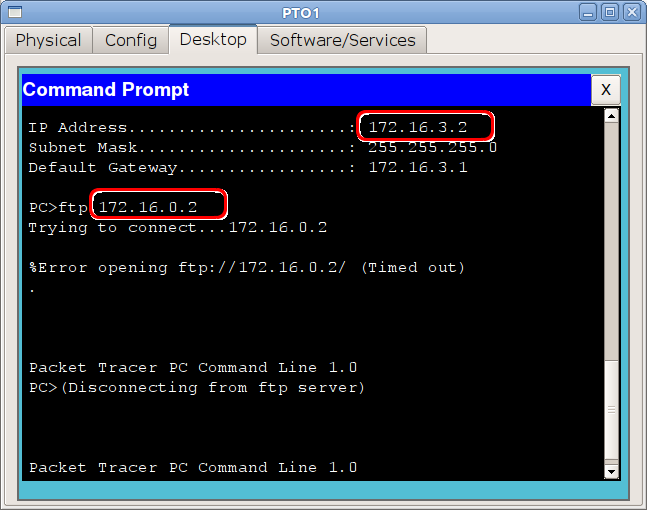
FTP package does not fall under any of the rules, except for the implicit deny ip any any and is discarded.
b) Access to the file server
Here it would be necessary first of all to decide on who will be a “resident”, who needs to be given access. Of course, those who have an address from the network 172.16.0.0/16 - only they will be given access.
Now with shared folders. Most modern systems already use the SMB protocol for this, which needs TCP port 445. On older versions, NetBios was used, which was fed through three ports: UDP 137 and 138 and TCP 139. After negotiating with our administrator, we will configure port 445 (though check within RT, of course, will not work). But besides that, we will need ports for FTP - 20, 21, and not only for internal hosts, but also for connections from the Internet:
msk-arbat-gw1 (config) # ip access-list extended Servers-out
msk-arbat-gw1 (config-ext-nacl) # permit tcp 172.16.0.0 0.0.255.255 host 172.16.0.3 eq 445
msk-arbat-gw1 (config-ext-nacl) # permit tcp any host 172.16.0.3 range 20 21
Here we reapplied the range 20 21 construction - in order to specify several ports in one line. For FTP, generally speaking, port 21 is not enough. The fact is that if you open only it, then you will be logged in, and there is no file transfer.
0.0.255.255 - reverse mask (wildcard mask). About what it is, let's talk a little later
c) Access to the mail server
We continue to turn out the practice - now with the mail server. Within the same access list, we add new records we need.
Instead of port numbers for common protocols, you can specify their names:
msk-arbat-gw1 (config) # ip access-list extended Servers-out
msk-arbat-gw1 (config-ext-nacl) #permit tcp any host 172.16.0.4 eq pop3
msk-arbat-gw1 (config-ext-nacl) #permit tcp any host 172.16.0.4 eq smtp
d) DNS server
msk-arbat-gw1 (config) # ip access-list extended Servers-out
msk-arbat-gw1 (config-ext-nacl) # permit udp 172.16.0.0 0.0.255.255 host 172.16.0.5 eq 53
e) ICMP
It remains to correct the situation with the ping. There is nothing wrong with adding rules to the end of the list, but somehow it will be aesthetically more pleasant to see them at the beginning.
Use simple cheat for this. For this you can use a text editor, for example. Copy there from the show run a piece about ACL and add the following lines:
no ip access-list extended Servers-out
ip access-list extended Servers-out
permit icmp any any
remark WEB
permit tcp any host 172.16.0.2 eq www
permit tcp host 172.16.6.66 host 172.16.0.2 range 20 ftp
permit tcp host 172.16.6.66 host 172.16.0.2 eq telnet
remark FILE
permit tcp 172.16.0.0 0.0.255.255 host 172.16.0.3 eq 445
permit tcp any host 172.16.0.3 range 20 21
remark MAIL
permit tcp any host 172.16.0.4 eq pop3
permit tcp any host 172.16.0.4 eq smtp
remark DNS
permit udp 172.16.0.0 0.0.255.255 host 172.16.0.5 eq 53
In the first line we delete the existing list, then create it anew and list all the new rules in the order we need. Using the command in the third line, we allowed all ICMP packets from any hosts to any hosts.
Further simply we copy everything in a crowd and we insert into the console. The interface interprets each line as a separate command and executes it. So we replaced the old list with a new one.
Check that ping is:

Perfectly.
This “cheat” is good for the initial configuration or if you understand exactly what you are doing. On a working network, when you configure an ACL remotely, you risk being left without access to a custom piece of hardware.
To insert a rule at the beginning or at any other desired place, you can resort to this method:
ip access-list extended Servers-out
1 permit icmp any any
Each rule in the list is numbered with a certain step, and if before the word permit / deny you put a number, the rule will be added not to the end, but to the place you need. Unfortunately, this feature does not work in RT.
If it is suddenly necessary (all consecutive numbers between rules are occupied), you can always renumber the rules (in this example, the number of the first rule 10 (the first number) and the increment 10 are assigned):
ip access-list resequence Servers-out 10 10
As a result, the Access List to the server network will look like this:
ip access-list extended Servers-out
permit icmp any any
remark WEB
permit tcp any host 172.16.0.2 eq www
permit tcp host 172.16.6.66 host 172.16.0.2 range 20 ftp
permit tcp host 172.16.6.66 host 172.16.0.2 eq telnet
remark FILE
permit tcp 172.16.0.0 0.0.255.255 host 172.16.0.3 eq 445
permit tcp any host 172.16.0.3 range 20 21
remark MAIL
permit tcp any host 172.16.0.4 eq pop3
permit tcp any host 172.16.0.4 eq smtp
remark DNS
permit udp 172.16.0.0 0.0.255.255 host 172.16.0.5 eq 53
Now our admin has access only to the WEB-server. Open to him full access to the entire network. This is the first homework.
e) Rights of users from the Other network
Until now, we had to not let someone in somewhere, so we paid attention to the destination address and the access list hung on outgoing traffic from the interface.
Now we need not to let out : no requests from computers from the Other network should go beyond. Well, of course, except for those that we specifically allow.
msk-arbat-gw1 (config) # ip access-list extended Other-in
msk-arbat-gw1 (config-ext-nacl) # remark IAM
msk-arbat-gw1 (config-ext-nacl) # permit ip host 172.16.6.61 any
msk-arbat-gw1 (config-ext-nacl) # remark ADMIN
msk-arbat-gw1 (config-ext-nacl) # permit ip host 172.16.6.66 any
Here we could not ban all at first, and then allow the elect, because absolutely all packets would fall under the rule of deny ip any any and would not work at all.
We apply on the interface. This time to the entrance:
msk-arbat-gw1 (config) #int fa0 / 0.104
msk-arbat-gw1 (config-subif) #ip access-group Other-in in
that is, all IP packets from the host with the address 172.16.6.61 or 172.16.6.66 are allowed to be transmitted wherever they are intended. Why are we also using an extended access list here? After all, it would seem, we only check the address of the sender. Because we gave the admin full access, but for a guest of the company “Elevator mi Up”, for example, who will get to the same network absolutely nowhere else, except to access the Internet.
g) Management Network
Nothing complicated. The rule will look like this:
msk-arbat-gw1 (config) # ip access-list extended Management-out
msk-arbat-gw1 (config-ext-nacl) # remark IAM
msk-arbat-gw1 (config-ext-nacl) # permit ip host 172.16.6.61 172.16.1.0 0.0.0.255
msk-arbat-gw1 (config-ext-nacl) # remark ADMIN
msk-arbat-gw1 (config-ext-nacl) # permit ip host 172.16.6.66 172.16.1.0 0.0.0.255
We apply this ACL on out to the FE 0 / 0.2 interface:
msk-arbat-gw1 (config) # int fa0 / 0.2
msk-arbat-gw1 (config-subif) #ip access-group Management-out
g) No more restrictions
Is done
Mask and reverse mask
So far, without explanation, we have given a strange parameter of the form 0.0.255.255, suspiciously resembling a subnet mask.
A bit difficult to understand, but it is the reverse mask that is used to determine the hosts that fall under the rule.
To understand what a reverse mask is, you need to know what a normal one is.
Let's start with the simplest example.
A typical network is 256 addresses: 172.16.5.0/24, for example. What does this record mean?
But it means exactly the following
| IP address. Decimal notation | 172 | sixteen | five | 0 |
| IP address. Binary recording | 10101100 | 00010000 | 00000101 | 00000000 |
| Subnet mask. Binary recording | 11111111 | 11111111 | 11111111 | 00000000 |
| Subnet mask. Decimal notation | 255 | 255 | 255 | 0 |
An IP address is a 32-bit parameter divided into 4 parts that you are used to seeing in decimal form.
The subnet mask also has a length of 32 bits - it is actually a template, a stencil, by which the address of a subnet is determined. Where units are in the mask, the value cannot change, that is, part 172.16.5 is completely unchanged and it will be the same for all hosts on this subnet, but the one where the zeros vary.
That is, in the example we took, 172.16.5.0/24 is the network address, and the hosts will be 172.16.5.1-172.16.5.254 (the last 255 is broadcast), because 00000001 is 1 and 11111110 is 254 (this is the last octet of the address ). / 24 means that the mask length is 24 bits, that is, we have 24 units - the constant part and 8 zeros.
Another case is when we have a mask, for example, 30 bits, and not 24.
For example, 172.16.2.4/30. Let's write it like this:
| IP address. Decimal notation | 172 | sixteen | 2 | four |
| IP address. Binary recording | 10101100 | 00010000 | 00000010 | 00000100 |
| Subnet mask. Binary recording | 11111111 | 11111111 | 11111111 | 11111100 |
| Subnet mask. Decimal notation | 255 | 255 | 255 | 252 |
As you can see, only the last two bits can change for this subnet. The last octet can take the following 4 values:
00000100 - subnet address (4 in decimal)
00000101 - host address (5)
00000110 - node address (6)
00000111 - broadcast (7)
Anything beyond this is another subnet
That is, now it should be a little clear to you that the subnet mask is a sequence of 32 bits, where units, meaning the address of the subnet, first come, and then zeros, meaning the host address. In this case, the zeros alternate and the units in the mask cannot alternate. That is, the mask 11111111.11100000.11110111.00000000 is impossible
And what is the reverse mask (wildcard)?
For the vast majority of administrators and some engineers - this is nothing more than the inverse of the usual mask. That is, the zeros initially set the address of the part, which must necessarily coincide, and the units on the contrary the free part.
That is, in the first example we took, if you want to filter all hosts from the 172.16.5.0/24 subnet, then you will specify a rule in the Access list:
... 172.16.5.0 0.0.0.255
Because the reverse mask will look like this:
00000000.00000000.00000000.11111111
In the second example with the network 172.16.2.4/30, the inverse mask will look like this: 30 zeros and two ones:
| Back mask Binary recording | 00000000 | 00000000 | 00000000 | 00000011 |
| Back mask Decimal notation | 0 | 0 | 0 | 3 |
Accordingly, the parameter in the access list will look like this:
... 172.16.2.4 0.0.0.3
Later, when you eat a dog on the miscalculations of masks and inverse masks, you will remember the most used figures, the number of hosts in one mask or another, you will understand that in the described situations the last octet of the reverse mask is obtained by subtracting the last octet from 255 digits of the usual mask (255-252 = 3), etc. In the meantime, you need to work hard and count)
But in fact, the inverse mask is a somewhat richer tool; here you can combine addresses within one subnet or even combine subnets, but the most important difference is that you can alternate zeros and ones. This allows you, for example, to filter a specific node (or group) on several subnets in one line.
Example 1
Given: network 172.16.16.0/24
It is necessary: filter the first 64 addresses (172.16.16.0-172.16.16.63)
Solution: 172.16.16.0 0.0.0.63
Example 2
Given: Networks 172.16.16.0/24 and 172.16.17.0/24
Need to: filter addresses from both networks
Solution: 172.16.16.0 0.0.1.255
Example 3
Given: Networks 172.16.0.0-172.16.255.0
Necessary: filter the host with the address 4 of all subnets
Solution: 172.16.16.0 0.0.255.4
To admit never in a life it was not necessary to meet the last scenario of application. These are some terribly specific tasks.
More details about the reverse masks can be found here: http://habrahabr.ru/post/131712/
Work ACL in pictures
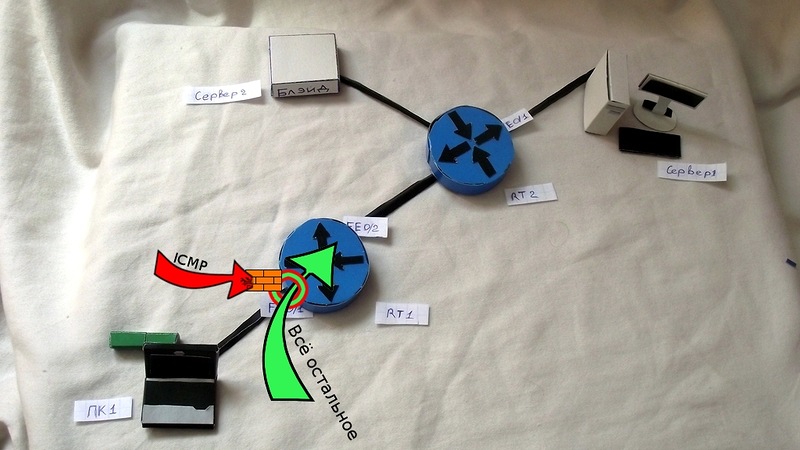
Hypothetical network:

1) On the RT1 router on the FE0 / 1 interface, everything is allowed at the input, except for ICMP.
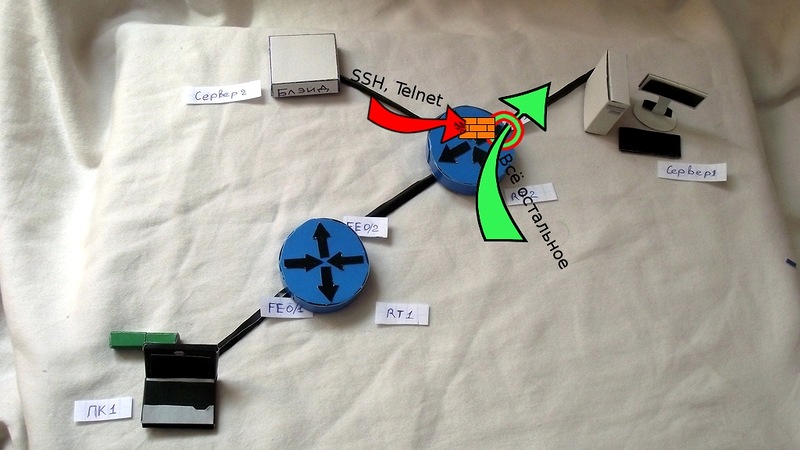
2) On RT2 router on FE0 / 1 interface, SSH and TELNET are not allowed on the output
Tests
clickable
1) Ping from PC1 to Server1

2) TELNET from PC1 to Server1
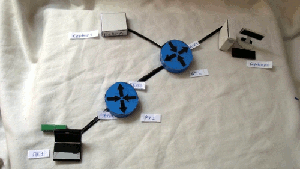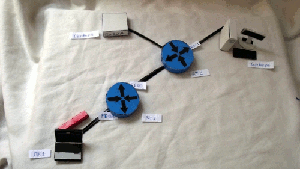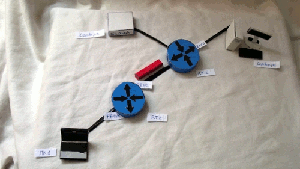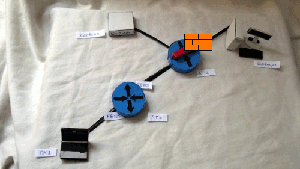
3) SSH from PC1 to Server2
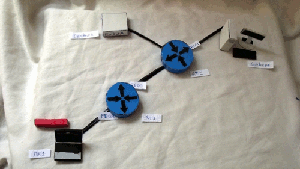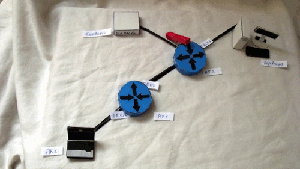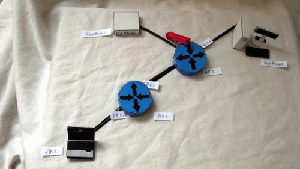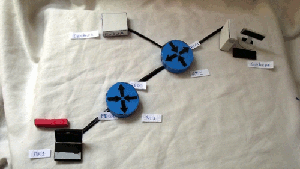
4) Ping from Server2 to PC1
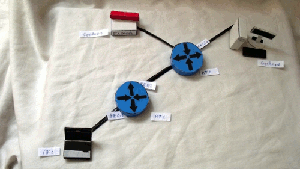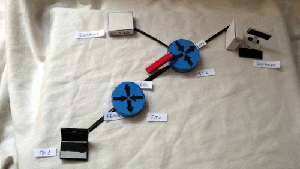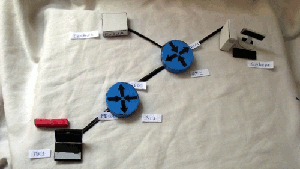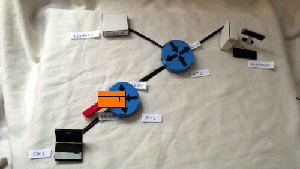
Additions
1) Rules acting on outgoing traffic (out) will not filter the traffic of the device itself. That is, if you need to deny access to the tsiska itself, then you will have to filter incoming traffic on this interface (return from where you need to deny access).
2) C ACL need to be careful. If there is a small error in the rule, the wrong order of settings or a badly thought out list in general, you can remain without access to the device.
For example, you want to close access anywhere for the network 172.16.6.0/24, except for your address 172.16.6.61 and set the rules like this:
deny ip 172.16.6.0 0.0.0.255 any
permit ip host 172.16.6.61 any
As soon as you apply an ACL on the interface, you will immediately lose access to the router, because you fall under the first rule and the second is not even checked.
The second is an unpleasant situation that may happen to you: under the ACL will get traffic that should not have come.
Imagine such a situation: we have a FTP server in passive mode in the server. To access it, you opened the 21st port in the Servers-out ACL. After the initial connection is established, the FTP server informs the client of the port through which it is ready to transfer / receive files, for example, the 1523rd. The client is trying to establish a TCP connection to this port, but stumbles upon a Servers-out ACL, where there is no such permission — the story ends with a successful transfer. In our example above, where we set up access to the file server, we opened access only on the 20th and 21st, because for example this is enough. In real life will have to tinker. A few ACL configuration examples for common cases.
3) A very similar and interesting problem arises from the 2nd point.
I thought up, for example, hang up on the interface on the Internet such ACLs here:
access-list out permit tcp host 1.1.1.1 host 2.2.2.2 eq 80
access-list in permit tcp host 2.2.2.2 any eq 80
It would seem: a host with the address 1.1.1.1 is allowed access via port 80 to the server 2.2.2.2 (the first rule). And back from the server 2.2.2.2 allowed connections inside.
But the nuance here is that computer 1.1.1.1 establishes a connection to port 80, but C from some other, for example, 1054, that is, the response packet from the server comes to socket 1.1.1.1:1054, does not fall under the rule ACL to IN and discarded due to implicit deny ip any any.
To avoid such a situation, and not open ports with the whole bundle, you can resort to such tricks in in ACL:
permit tcp host 2.2.2.2 any established.
Details of such a decision in one of the following articles.
4) Speaking about the modern world, it is impossible to bypass such a tool as object groups (Object-group).
Suppose you need to create an ACL that issues three specific Internet addresses on three identical ports with the prospect of expanding the number of addresses and ports. What it looks like without the knowledge of object groups:
ip access-list extended TO-INTERNET
permit tcp host 172.16.6.66 any eq 80
permit tcp host 172.16.6.66 any eq 8080
permit tcp host 172.16.6.66 any eq 443
permit tcp host 172.16.6.67 any eq 80
permit tcp host 172.16.6.67 any eq 8080
permit tcp host 172.16.6.67 any eq 443
permit tcp host 172.16.6.68 any eq 80
permit tcp host 172.16.6.68 any eq 8080
permit tcp host 172.16.6.68 any eq 443
With an increase in the number of parameters, it becomes more and more difficult to accompany such an ACL; it is easy to make a mistake when setting up.
But, if we turn to object groups, then it takes the following form:
object-group service INET-PORTS
description ports for some hosts
tcp eq www
tcp eq 8080
tcp eq 443
object-group network HOSTS-TO-INET
Hosts allowed to browse the net
host 172.16.6.66
host 172.16.6.67
host 172.16.6.68
ip access-list extended INET-OUT
permit object-group INET-PORTS object-group HOSTS-TO-INET any
at first glance it looks somewhat threatening, but if you look at it, it is very convenient.
4) Information that is very useful for troubleshooting can be obtained from the output of the show ip access-lists% command name ACL% . In addition to the actual list of rules of the specified ACL, this command shows the number of matches for each rule.
nat-inet
Extended IP access list list
tcp 172.16.3.0 0.0.0.255 host 192.0.2.2 eq www
permit ip 172.16.5.0 0.0.0.255 host 192.0.2.3
permit ip 172.16 .5.0 0.0.0.255 host 192.0.2.4
permit ip host 172.16.4.123 any
permit ip host 172.16.6.61 any
permit ip host 172.16.6.66 any (4 match (es))
permit ip host 172.16.16.222 any
permit ip host 172.16.17.222 any
permit ip host 172.16.24.222 any
And adding at the end of any rule log , we will be able to receive messages about every match in the console. (the latter does not work in PT)
NAT
Network Address Translation - a mechanism in the household has been absolutely necessary since 1994. Many sessions about him are broken and packets are lost.
You need it most often to connect your local network to the Internet. The fact is that theoretically there are 255 * 255 * 255 * 255 = 4 228 250 625. 4 billion addresses. Even if each inhabitant of the planet had only one computer, there would not be enough addresses. And here, except that the irons are not connected to the Internet. Smart people realized this in the early 90s and, as a temporary solution, they suggested dividing the address space into public (white) and private (private, gray) addresses.
The latter include three ranges:
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16
You can freely use them in your private network, and therefore, of course, they will be repeated. How to be with uniqueness? Who will be responsible for the WEB-server, which received a request with the return address 192.168.1.1? Rostelecom? Tatneft companies? Or your room Dlinka? On the Internet, no one knows anything about private networks - they are not routed.
This is where NAT comes into play. By and large, this is a hoax, a setup. On the device, your private address, roughly speaking, is simply replaced by the white address, which will appear later in the package as it travels to the WEB server. But the white addresses are very well routed, and the packet will definitely return back to the tension device.
But how will it in turn understand what to do with it next? Here with it we will understand.
NAT types
Static
In this case, one internal address is converted to one external address. And at the same time all requests coming to the external address will be transmitted to the internal one. As if this host is the owner of this white IP address.
Configured by the following command:
Router (config) # ip nat inside source source static 172.16.6.5 198.51.100.2
What happens:
1) Site 172.16.6.5 addresses the WEB server. It sends an IP packet, where the recipient's address is 192.0.2.2, and the sender is 172.16.6.5.

2) On the corporate network, the packet is delivered to the gateway 172.16.6.1, where NAT is configured
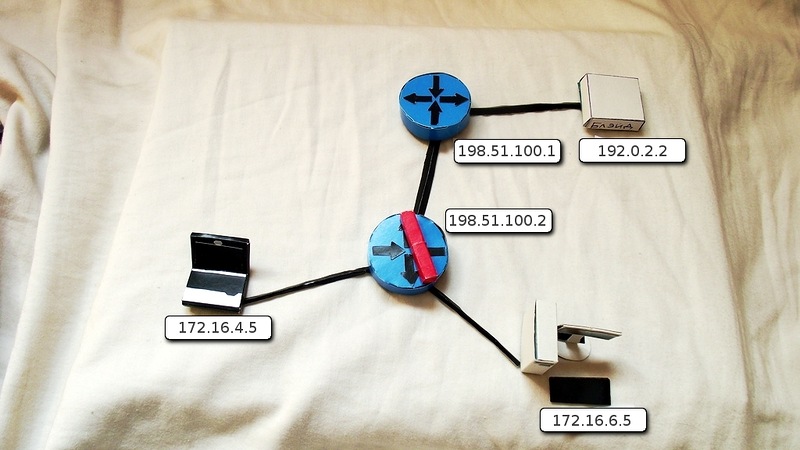
3) According to the configured command, the router removes the current IP header and changes it to a new one, where the white address 198.51.100.2 already appears as the sender's address.
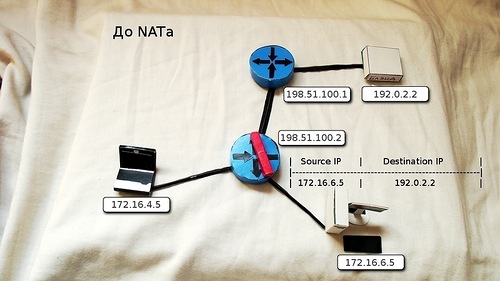

4) On the big Internet, the updated package reaches the server 192.0.2.2.
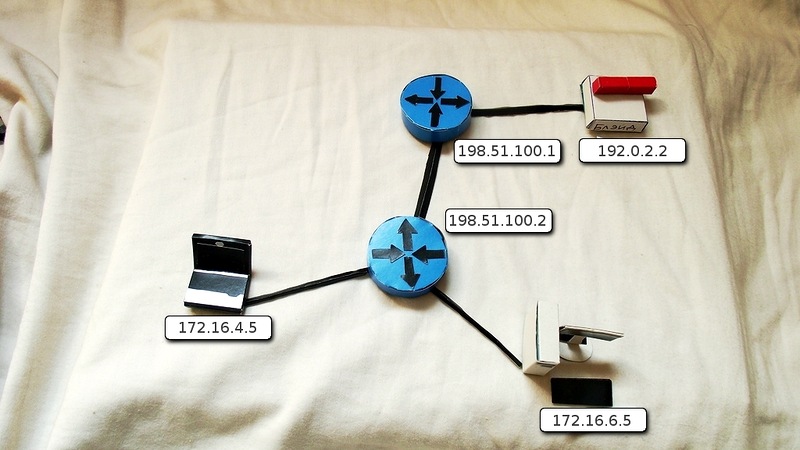
5) He sees that the answer must be sent to 198.51.100.2 and prepares a response IP packet. As the address of the sender, the actual address of the server is 192.0.2.2, the destination address is 198.51.100.2
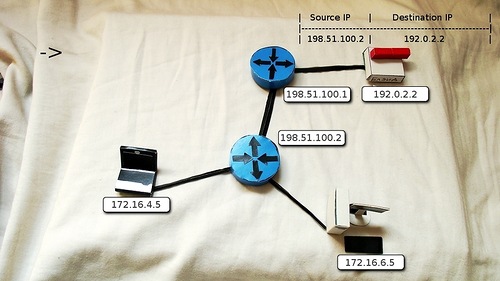

6) The package flies back through the Internet, and not the fact that it is the same way.
7) On the saturating device it is indicated that all requests to the address 198.51.100.2 should be redirected to 172.16.6.5. The router undresses the hidden TCP segment again and sets a new IP header (the sender's address does not change, the destination address is 172.16.6.5).
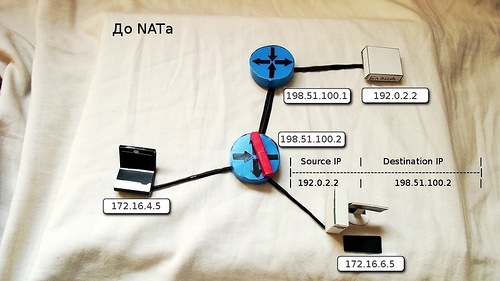
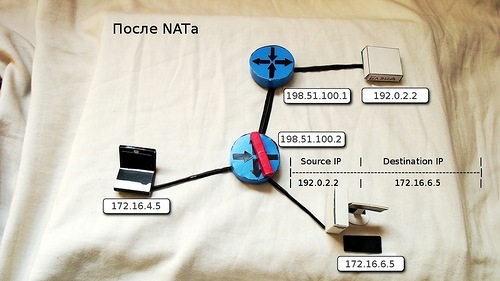
8) On the internal network, the packet is returned to the initiator, who even did not know what miracles were happening to him at the border.
And so it will be with everyone.
In this case, if the connection is initiated from the Internet, the packets automatically, passing through the saturating device, get to the internal host.
This approach can be useful when you have a server inside your network that needs full access from the outside. Of course, you cannot use this option if you want to release three hundred hosts on the Internet through a single address. This option NAT does not help save white IP-addresses, but nevertheless it is useful.
Dynamic
You have a pool of white addresses, for example, the provider allocated to you a network 198.51.100.0/28 with 16 addresses. Two of them (the first and the last) are the network and broadcast address, two more addresses are assigned to the equipment to provide routing. You can use the 12 remaining addresses for NAT and release your users through them.
The situation is similar to static NAT — one private address is translated to one external address — but now the external one is not clearly fixed, but will be selected dynamically from the specified range.
It is configured as follows:
Router (config) #ip nat pool lol_pool 198.51.100.3 198.51.103.14
Set a pool (range) of public addresses from which the address for a natirovaniye will be selected
Router (config) # access-list 100 permit ip 172.16.6.0 0.0.0.255 any
We specify an access list that passes all packets with source address 172.16.6.x, where x varies 0-255.
Router (config) #ip nat inside source list 100 pool lol_pool
This team we dock the created ACL and pool.
This option is also not universal, you will not be able to release everyone on the Internet to your 300 users unless you have 300 external addresses. Once the white addresses are exhausted, no one will be able to access the Internet anymore. At the same time, those users who have already managed to grab their external address will work. The clear ip nat translation command will help you to drop all current translations and free up external addresses. *
In addition to dynamically allocating external addresses, this dynamic NAT is different from static in that without a separate port forwarding setting, an external connection to one of the pool addresses is no longer possible.
Many-to-one
The following type has several names: NAT Overload, Port Address Translation (PAT), IP Masquerading, Many-to-One NAT.
The last name speaks for itself - through a single external address goes into the world of many private. This allows you to solve the problem of lack of external addresses and release into the world of all comers.
Here it would be necessary to give an explanation of how this works. How two private addresses are translated into one can be represented, but how does the router understand who needs to send a packet that returns from the Internet to this address?
It's very simple:
Suppose that from two hosts from the internal network come packets on a natriate device. Both with a request to the WEB-server 192.0.2.2.
The data from the hosts look like this:
| Sender's address | Sender port | Address of the recipient | Receiver port |
| 172.16.6.5 | 23761 | 192.0.2.2 | 80 |
| 172.16.4.5 | 39800 | 192.0.2.2 | 80 |
The router uncovers the IP packet from the first host, extracts a TCP segment from it, prints it out and finds out from which port the connection is being made. He has an external address 198.51.100.2, which will change the address from the internal network.
Then he chooses a free port, for example, 11874. And what does he do next? It packs all the data of the application level into a new TCP segment, where 80 still remains as the destination port (the WEB-server waits for it), and the port of the sender changes from 23761 to 11874. This TCP-segment is encapsulated into a new IP- packet where the sender's IP address changes from 172.16.6.5 to 198.51.100.2.
The same thing happens for a packet from a second host, only the next free port is selected, for example 11875. “Free” means that it is not yet occupied by other such connections.
The data that is sent to the Internet, will now look like this.
| Sender's address | Sender port | Address of the recipient | Receiver port |
| 198.51.100.2 | 11874 | 192.0.2.2 | 80 |
| 198.51.100.2 | 11875 | 192.0.2.2 | 80 |
It enters the senders and recipients data into its NAT table.
| Local Sender Address | Local Sender Port | Global Sender Address | Global Sender Port | Address of the recipient | Receiver port |
| 172.16.6.5 | 23761 | 198.51.100.2 | 11874 | 192.0.2.2 | 80 |
| 172.16.4.5 | 39800 | 198.51.100.2 | 11875 | 192.0.2.2 | 80 |
For a web server, these are two completely different requests that it must process each one individually. After that, he sends an answer that looks like this:
| Sender's address | Sender port | Address of the recipient | Receiver port |
| 192.0.2.2 | 80 | 198.51.100.2 | 11874 |
| 192.0.2.2 | 80 | 198.51.100.2 | 11875 |
When one of these packets reaches our router, it matches the data in this packet with its entries in the NAT table. If a match is found, the reverse procedure occurs — the packet and the TCP segment are returned its original parameters only as an assignment:
| Sender's address | Sender port | Address of the recipient | Receiver port |
| 192.0.2.2 | 80 | 172.16.6.5 | 23761 |
| 192.0.2.2 | 80 | 172.16.4.5 | 39800 |
And now the packets are delivered on the internal network to the initiating computers, which even didn’t even know that they had been so hard on the border somewhere with their data.
Your every appeal is a separate connection. That is, you tried to open a WEB-page - this is the HTTP protocol that uses port 80. To do this, your computer must establish a TCP session with a remote server. Such a session (TCP or UDP) is defined by two sockets: local IP address: local port and remote IP address: remote port. In a normal situation, you have one server computer connection, in the case of a NAT connection, there will be two: a router-server and the computer thinks that it has a computer-server session.
The setting is completely insignificant: the additional word overload:
Router (config) # access-list 101 permit 172.16.4.0 0.0.0.255
Router (config) #ip nat inside list source interface 101 fa0 / 1 overload
In this case, of course, it is possible to configure the address pool:
Router (config) #ip nat pool lol_pool 198.51.100.2 198.51.103.14
Router (config) # access-list 100 permit 172.16.6.0 0.0.0.255
Router (config) #ip nat inside list list 100 pool lol_pool overload
Port Forwarding
Otherwise they say port forwarding or mapping.
When we started talking about NAT, we had one-to-one translation and all requests coming from outside were automatically redirected to the internal host. Thus it would be possible to expose the server out to the Internet.
But if you do not have such an opportunity - you are limited in white addresses, or do not want to expose the whole bundle of ports to the outside, what should you do?
You can specify that all requests coming to a specific white address and a specific port of the router should be redirected to the correct port of the desired internal address.
Router (config) #ip nat inside source source static tcp 172.16.0.2 80 198.51.100.2 80 extendable
The use of this command means that a TCP request that comes from the Internet to the address 198.51.100.2 on port 80 will be redirected to the internal address 172.16.0.2 to the same 80th port. Of course, you can also forward UDP and redirect from one port to another. This, for example, can be useful if you have two computers that need access via RDP from the outside. RDP uses port 3389. You cannot forward the same port to different hosts (using the same external address). Therefore, you can do this:
Router (config) # ip nat inside source source static tcp 172.16.6.61 3389 198.51.100.2 3389
Router (config) # ip nat inside source source static tcp 172.16.6.66 3389 198.51.100.2 3398
Then, to get to the computer 172.16.6.61, you start the RDP-session on port 198.51.100.2:34389, and on 172.16.6.66 - 198.51.100.2:37398. The router itself scatters everything where it is necessary.
By the way, this command is a special case of the very first: ip nat inside source static 172.16.6.66 198.51.100.2. Only in this case we are talking about forwarding all traffic, and in our examples - specific ports of the TCP protocol.
This is how in general it functions NAT. A lot of articles have been written about its features, pros and cons, but it is impossible not to mention them.
Weaknesses and strengths of NAT
+
- First of all, NAT allows you to save public IP addresses. Actually for this he was created. Through one address, theoretically, it is possible to release more than 65000 gray addresses (by the number of ports).
- Secondly , PAT and dynamic NAT is to some extent a firewall, preventing external connections from reaching end computers where your firewall and antivirus may not be present. The fact is that if a package comes from the outside to the saturating device, which is not expected or not allowed here, it is simply discarded.
In order for a packet to be missed and processed, the following conditions must be met:
1) The NAT table must have an entry for this external address, specified as the sender's address in the packet
AND
2) The sender port in the packet must match the port for this white address in the entry
AND
3) The destination port in the packet matches the port in the entry.
OR
Port forwarding is configured.
But it is not necessary to consider NAT as a firewall - it is nothing more than an additional bun.
- Thirdly , NAT hides the internal structure of your network from prying eyes - when you trace a route from the outside, you will not see anything further than the saturating device.
-
NAT has some disadvantages. The most tangible of them, perhaps, are the following:
- Some protocols cannot work through NAT without crutches. For example, FTP or tunneling protocols (despite how simple I set up FTP in the lab, in real life this can create a lot of problems)
- Another problem lies in the fact that there are a lot of requests for one server from one address. Many have witnessed this when you go to some Rapidshare, and he says that you already had a connection from your IP, you think that “lying, dog”, and this is your neighbor already sucking. For the same reason, there were problems with ICQ when the server was denied registration.
- The problem is not very relevant now: the load on the processor and RAM. Since the amount of work is quite large compared to simple routing (it’s not just to look at the IP header, you need to remove it, remove the TCP header, add new headers to the table) in small offices there are problems with this.
I came across such a situation.
One of the possible solutions is to bring the NAT function to a separate PC or to a specialized device, such as the Cisco ASA.
For big players who have routers pushing 3-4 BGP full-views, this is not a problem now.
What else do you need to know?
- NAT is used mainly to provide Internet access to hosts with private addresses. But there is another use - the connection between two private networks with overlapping address spaces.
For example, your company buys a branch in Aktyubinsk. You have the addressing 10.0.0.0-10.1.255.255, and they have 10.1.1.0-10.1.10.255. The ranges are clearly intersected; it is impossible to configure routing in any way, because the same address can be in Aktyubinsk and at your headquarters.
In this case, NAT is configured at the interface. Since we do not have gray addresses, for example, we can single out a range of 10.2.1.0-10.2.10.255 and do one-to-one translation:
10.1.1.1-10.2.1.1
10.1.1.2-10.2.1.2
...
10.1.10.255-10.2.10.255
- In large adult toys, NAT can be implemented on a separate board (and often it is) and will not work without it. And on the office glands, by contrast, there is almost always.
- With the widespread adoption of IPv6, the need for NAT will be eroded. Already, large customers are beginning to be interested in the functionality of NAT64 - this is when you have access to the world via IPv4, and the internal network is already on IPv6
- Of course, this is only a superficial look at NAT and there is still a sea of nuances that will not help you to educate yourself.
NAT practice
What does reality require of us?
1) The management network does not have access to the Internet at all
2) Hosts from the VET network have access only to specialized sites, for example, Linkmeup.ru
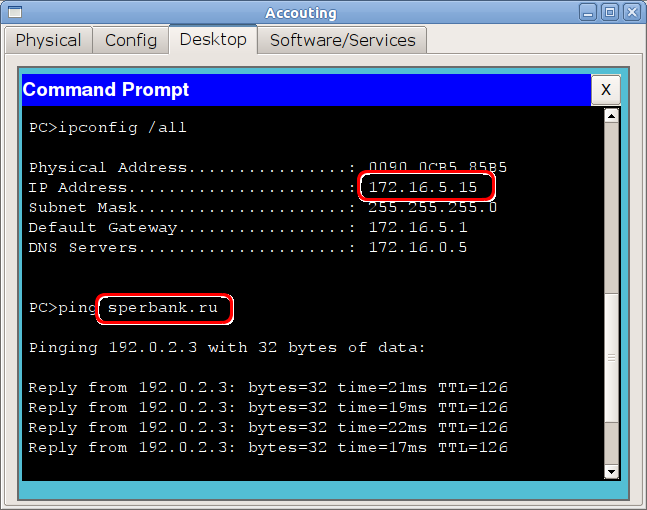
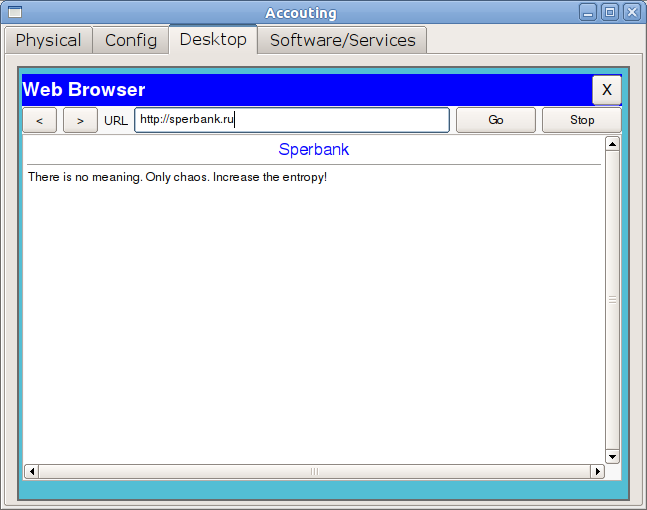
3) For lovely ladies from accounting, you need to cut down the window into the world of client-banks.
4) Do not release the FDO anywhere except for the financial director
5) On the Other network, our computer and the administrator's computer - we will give them full access to the Internet. All others can be opened by written request.
6) Do not forget about the branches in St. Petersburg and Kemerovo. For simplicity, we configure full access for the eniki from these subnets.
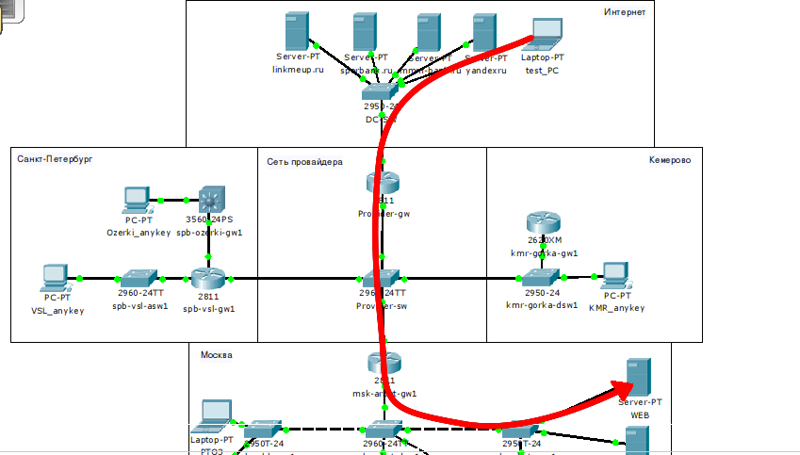
7) With servers, a separate song. For them, we set up port forwarding. All we need is:
a) The web server should be accessible on port 80
b) Mail server on the 25th and 110th
c) File server is accessible from the world via FTP.
8) Admin and our computers should be accessible from the Internet via RDP. Actually, this is the wrong way - for a remote connection, you need to use a VPN connection and already using RDP on the local network, but this is a separate topic for a completely different article.
At first we will prepare a test platform:
Internet connection will be organized through an existing link provided by the provider.
He goes to the network provider. We remind you that everything in this cloud is an abstract network, which in reality can consist of dozens of routers and hundreds of switches. But we need something manageable and predictable, so we are installing another router here. On the one hand there is a link to it from the switch, from another server on the Internet.
We will need the following servers:
1. Two client-banks for accountants (sperbank.ru, mmm-bank.ru)
2. Linkmeup.ru for PTOshchnikov
3. Yandex (yandex.ru)
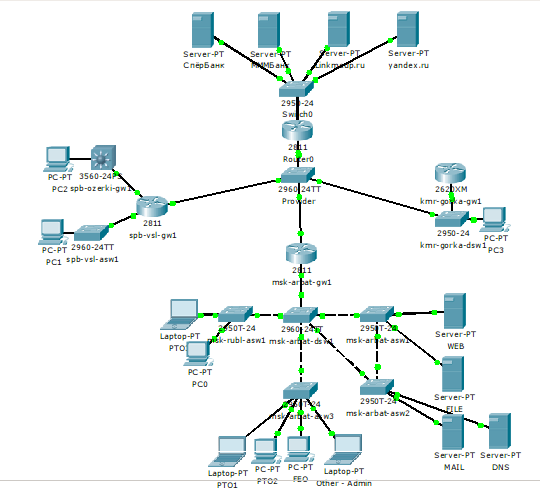
For such a connection, we will raise one more vlan to msk- arbat-gw1. His number, of course, is consistent with the provider. Let it be VLAN 6
Suppose a provider provides us with a subnet 198.51.100.0/28. The first two addresses are used to organize the link (198.51.100.1 and 198.51.100.2), and we use the remaining ones as a pool for NAT. However, no one absolutely prevents us from using the address 198.51.100.2 for the pool. So let's do it: pool: 198.51.100.2-198.51.100.14
For simplicity, let's assume that we have public servers on the same subnet:
192.0.2.0/24 .
How to set up a link and addresses you are already quite up to date.
Since we have only one router in the network of the provider, and all the networks are connected directly to it, there is no need to configure the routing.
But our msk-arbat-gw1 should know where to send packets to the Internet, so we need a default route:
msk-arbat-gw1 (config) # ip route 0.0.0.0 0.0.0.0 198.51.100.1
Now, in order.
First, set up an address pool.
msk-arbat-gw1 (config) # ip nat pool main_pool 198.51.100.2 198.51.100.14 netmask 255.255.255.240
Now we collect ACL:
msk-arbat-gw1 (config) # ip access-list extended nat-inet
1) Management Network
doesn't have internet access at all
Is done
2) Hosts from the PTO network
They have access only to specialized sites, for example, Linkmeup.ru
msk-arbat-gw1 (config-ext-nacl) # permit tcp 172.16.3.0 0.0.0.255 host 192.0.2.2 eq 80
3) Accounting
We give access to all hosts on both servers.
msk-arbat-gw1 (config-ext-nacl) # permit ip 172.16.5.0 0.0.0.255 host 192.0.2.3
msk-arbat-gw1 (config-ext-nacl) # permit ip 172.16.5.0 0.0.0.255 host 192.0.2.4
4) FEO
We give permission only to the financial director - this is only one host.
msk-arbat-gw1 (config-ext-nacl) # permit ip host 172.16.4.123 any
5) Other
Our full access computers
msk-arbat-gw1 (config-ext-nacl) # permit ip host 172.16.6.61 any
msk-arbat-gw1 (config-ext-nacl) # permit ip host 172.16.6.66 any
6) Branches in St. Petersburg and Kemerovo
Let enikiev addresses be the same: 172.16.x.222
msk-arbat-gw1 (config-ext-nacl) # permit ip host 172.16.16.222 any
msk-arbat-gw1 (config-ext-nacl) # permit ip host 172.16.17.222 any
msk-arbat-gw1 (config-ext- nacl) # permit ip host 172.16.24.222 any
This is what the ACL looks like now:
ip access-list extended nat-inet
remark PTO
permit tcp 172.16.3.0 0.0.0.255 host 192.0.2.2 eq www
remark ACCOUNTING
permit ip 172.16.5.0 0.0.0.255 host 192.0.2.3
permit ip 172.16.5.0 0.0.0.255 host 192.0.2.4
remark FEO
permit ip host 172.16.4.123 any
remark IAM
permit ip host 172.16.6.61 any
remark ADMIN
permit ip host 172.16.6.66 any
remark SPB_VSL_ISLAND
permit ip host 172.16.16.222 any
remark SPB_OZERKI
permit ip host 172.16. 17.222 any
remark KMR
permit ip host 172.16.24.222 any
Run:
msk-arbat-gw1 (config) # ip nat inside source list list nat-inet pool main_pool overload
But happiness will not be complete without configuring the interfaces:
On the external interface, you must give the command ip nat outside
On the inside: ip nat inside
msk-arbat-gw1 (config) # int fa0 / 0.101
msk-arbat-gw1 (config-subif) # ip nat inside
msk-arbat-gw1 (config) # int fa0 / 0.102
msk-arbat-gw1 (config-subif) # ip nat inside
msk-arbat-gw1 (config) # int fa0 / 0.103
msk-arbat-gw1 (config-subif) # ip nat inside
msk-arbat-gw1 (config) # int fa0 / 0.104
msk-arbat-gw1 ( config-subif) # ip nat inside
msk-arbat-gw1 (config) # int fa0 / 1.6
msk-arbat-gw1 (config-subif) # ip nat outside
This will allow the router to understand where to wait for the packets that need to be processed and where to send them then.
In order for servers on the Internet to be accessible by a domain name, it would be nice for us to acquire a DNS server on our network:


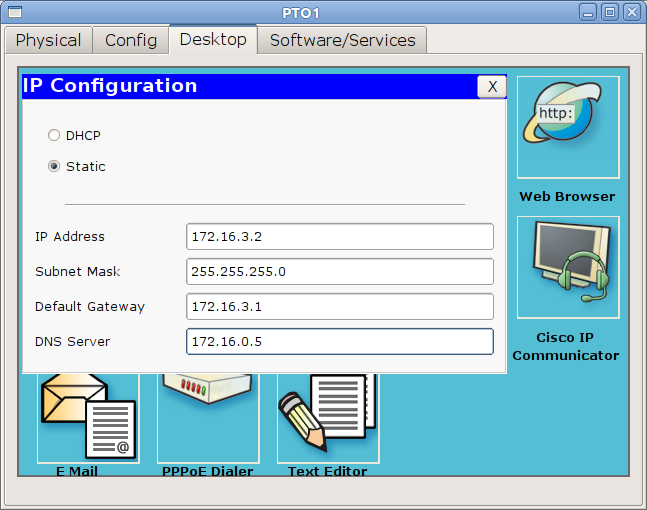
Naturally, we need to register it on those devices from which we will check access:
Show must go on!
Everything
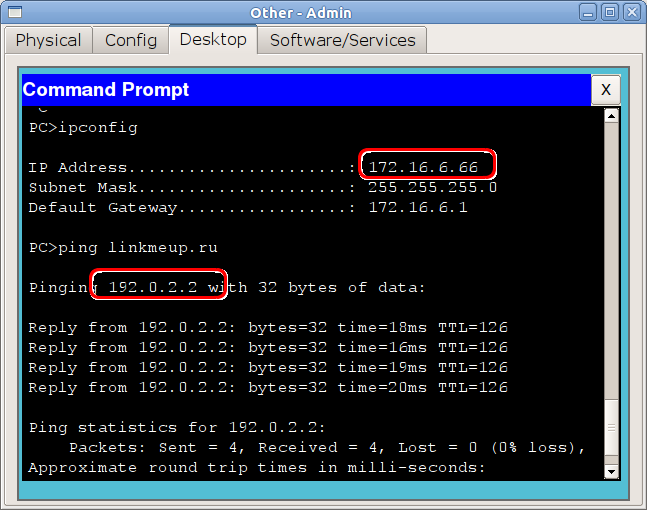
is available from the administrator's computer: From the TVET network there is only access to the site linkmeup.ru on port 80 (HTTP):


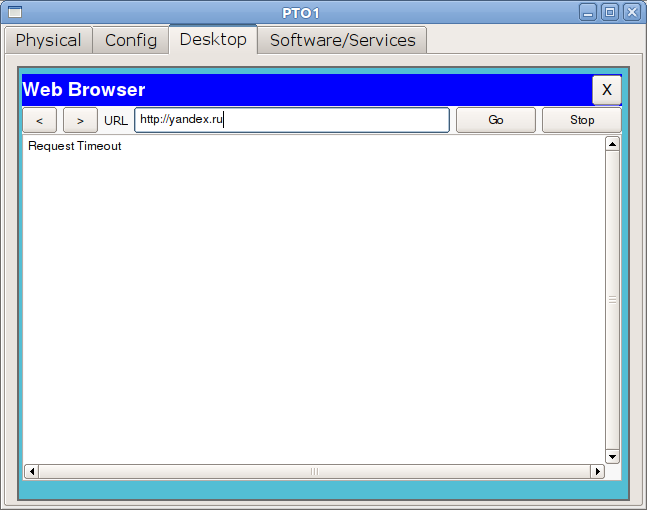
Only 4.123 goes to the world in the FD network (


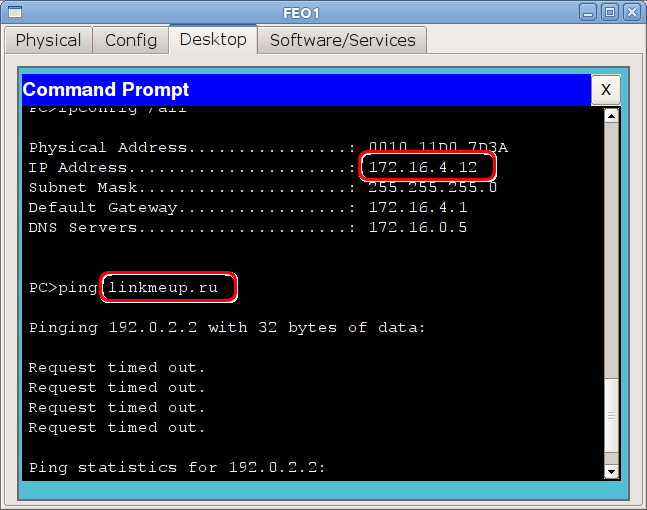
financial director) Only client-bank websites work in the accounting department. But, since permission is given entirely on the IP protocol, they can also be pinged:
7) Server
Here we need to configure port forwarding so that they can be accessed from the Internet:
a) Web server
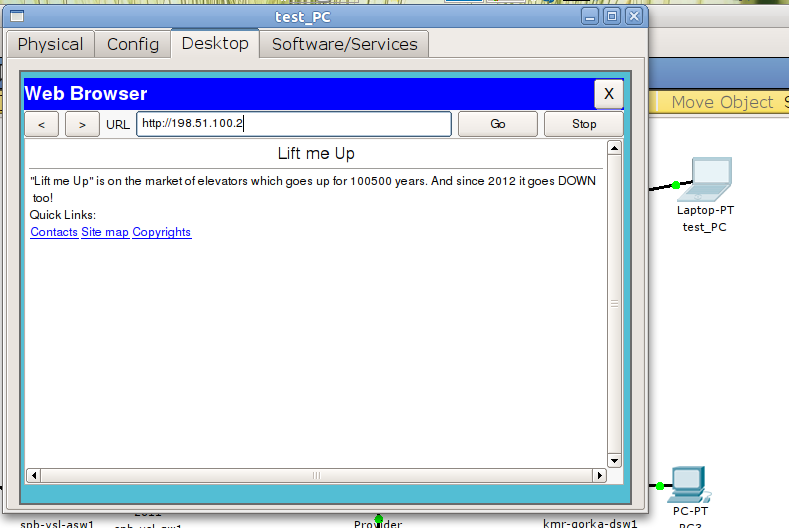
msk-arbat-gw1 (config) # ip nat inside static source tcp 172.16.0.2 80 198.51.100.2 80
Immediately check, for example, we can do this with a test PC with ares 192.0.2.7.
Now nothing will work, because for the network of servers we have not configured the interface on msk-arbat-gw1:
msk-arbat-gw1 (config) # int fa0 / 0.3
msk-arbat-gw1 (config-subif) # ip nat inside
And now:
b) File server
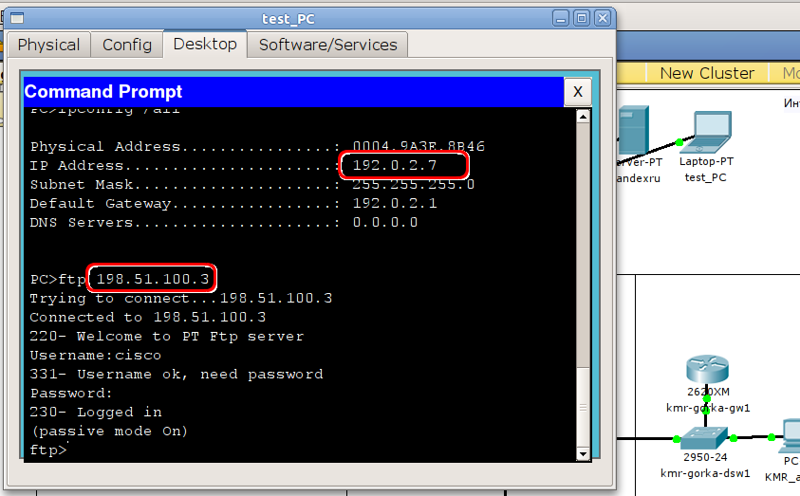
msk-arbat-gw1 (config) # ip nat inside static source tcp 172.16.0.3 20 198.51.100.3 20
msk-arbat-gw1 (config) # ip nat inside static tcp 172.16.0.3 21 198.51.100.3 21
For this purpose, in the servers-out ACL, we also opened ports 20-21 for all
c) Mail Server
msk-arbat-gw1 (config) # ip nat inside source static tcp 172.16.0.4 25 198.51.100.4 25
msk-arbat-gw1 (config) # ip nat inside source static tcp 172.16.0.4 110 198.51.100.4 110
Check is also not difficult. Follow the instructions:
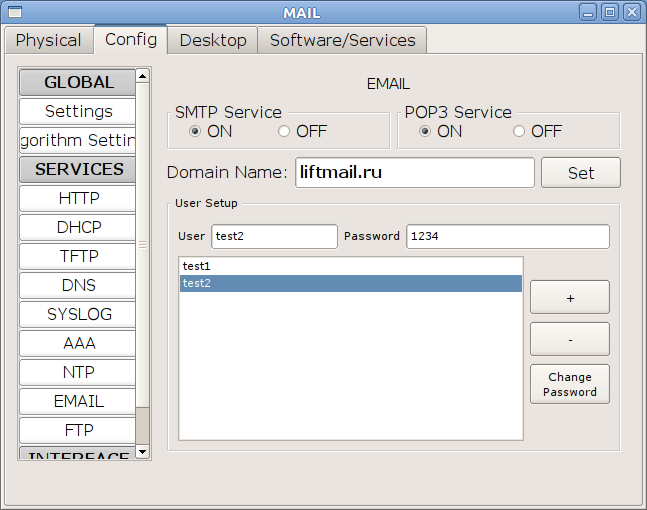
First, we configure the mail server. Specify the domain and create two users.
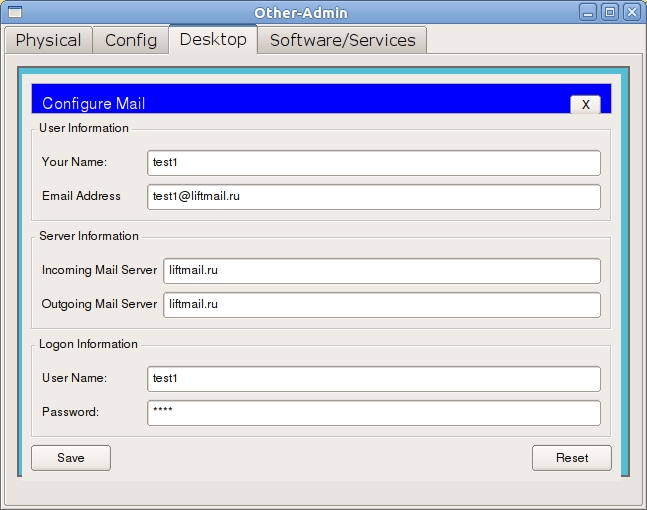
Next, make the domain in DNS. This step is optional - you can also access the server by IP, but why not?

We configure the computer from our network:
From the outside:
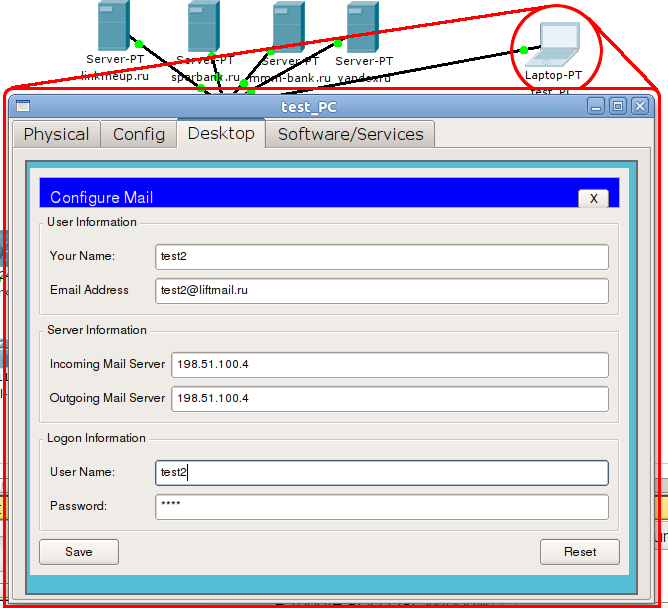
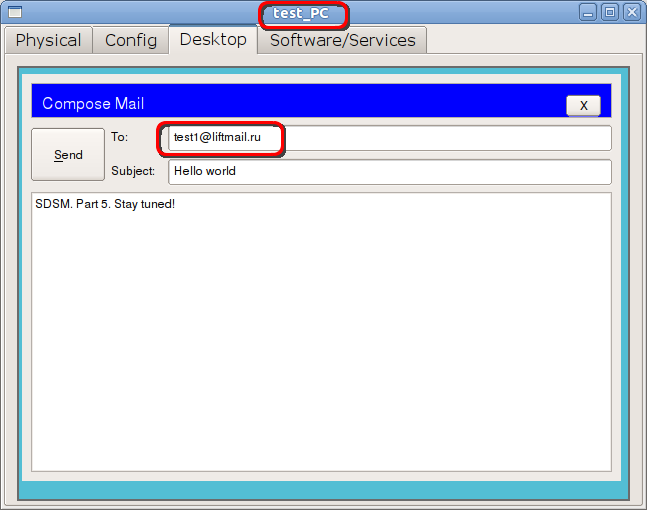
We are preparing a letter:
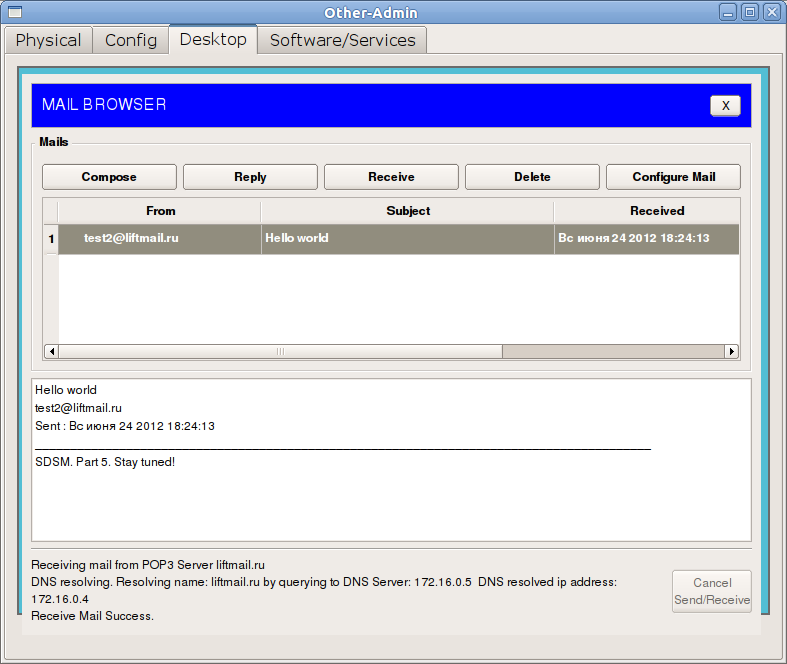
On the local host, press Receive:
8) Access via RDP to the computers of the administrator and ours
msk-arbat-gw1 (config) # ip nat inside static source tcp 172.16.6.61 3389 198.51.100.10 3389
msk-arbat-gw1 (config) # ip nat inside source static static tcp 172.16.6.66 3389 198.51.100.10 3398
Security
Lastly, one remark. Most likely a natatorial device, you have your ip nat outside interface looking outside - on the Internet. Therefore, on this interface would not hurt to hang the ACL, where you deny, allow what you need. We will not dwell on this question in this article.
At this first acquaintance with the technology of NAT can be considered complete.
As one more remote answer, answer the question why there is no Internet access from enike computers in St. Petersburg and Kemerovo. After all, we have already added them to the access list.
Release materials
New IP plan, switching plans for each point and regulations
File RT with laboratory
Device configuration
Additional links:
General information and TCP load distribution
Two providers + NAT
Useful information from cisco
Our colleague habrayuzer wrote several articles on the features of NAT . This article may be of particular interest .
But be that as it may, no one will write about cisco better than cisco.
Back mask
Bonuses
Setting up PBR for an example from the article
In global configuration mode.
Add a default route:
In the access list, we filter traffic from the 192.168.2.0/24 network.
, , 192.168.2.0/24, next-hop 10.0.2.1 ( 10.0.1.1)
:
Policy-Based Routing, , , .
Add a default route:
ip route 0.0.0.0 0.0.0.0 10.0.1.1
In the access list, we filter traffic from the 192.168.2.0/24 network.
access-list 101 permit ip 192.168.2.0 0.0.0.255 any
, , 192.168.2.0/24, next-hop 10.0.2.1 ( 10.0.1.1)
route-map CLIENT permit 5
match ip address 101
set ip next-hop 10.0.2.1
:
ip policy route-map CLIENT
Policy-Based Routing, , , .
ACL-based interface speed limits
192.168.1.0/24 1.5 /, 192.168.2.0/24 64 /.
10.0.1.1 :
10.0.1.1 :
Router(config)# access-list 100 permit ip 192.168.1.0 0.0.0.255 any
Router(config)# access-list 101 permit ip 192.168.2.0 0.0.0.255 any
Router(config)# interface fa0/0
Router(config-if)# rate-limit output access-group 100 1544000 64000 64000 conform-action transmit exceed-action drop
Router(config-if)# rate-limit output access-group 101 64000 16000 16000 conform-action transmit exceed-action drop
Urgent questions bezhabernym people can be realized in the LJ .
Thanks to my co-author of thegluck. Special
thanks for helping us with the JDima article .
Source: https://habr.com/ru/post/147996/
All Articles