Increase web application stack security (LAMP virtualization)
By the web application stack, we will mean a lot of open source software products: an operating system, a web server, a database server, and an executable code environment. The most famous and common stack is LAMP. This is an acronym for a stack of free open source web applications. The name is composed of the first letters of the product included in it: Linux (operating system), Apache web server , MySQL database , and PHP (sometimes Perl or Python). Previously published security materials recommend keeping various network services on dedicated servers or virtual machines for this purpose. This will allow to isolate the elements of the system compromised and cracked by the attacker if the latter gets the opportunity to exploit errors in one of the links in the service network. The article is also an answer to the questions most frequently asked by our readers, sent to us by e-mail. In the guide, I will explain how to build a solution based on physical or virtual servers, equally suitable for distributing static and dynamic content for applications that require databases and caching.
')
What happens if, say, an Apache web server is compromised? An attacker will gain access to your database, cache, and, as well, to other elements of the system or network. In this case, you need to separate the server services as follows:
Fractional installation has a number of advantages:
Add to this advanced features from the High-availability area, such as failover (transfer of images / containers of fractional parts of the system to other resources due to the initial configuration of the vm00 host system for similar network interaction [Virtual-IP at the vm00 level]), load balancing CDNs are becoming much more convenient in the case of a similar system setup.
Let's see how our system works with a reverse proxy server. In this example, I will place the proxy and HTTP server to the firewall. (see fig. 1). The website www.example.com will be hosted on a static IPv4-address 202.54.1.1 , which is assigned to the eth0 device. The internal IP 192.168.1.1 is assigned to the eth1 device. This is the node of our reverse proxy server. The remaining servers are inside the local network and cannot be directly accessed via the Internet.

The hardware or software (OpenBSD / Linux) firewall rules for host 202.54.1.1 allow access only to ports 80 and 443. All other ports are blocked. Iptables also works on every VM node and access is allowed only to the required ports. Your reverse proxy server defines a pool of HTTP servers as follows:
Apache and Lighttpd servers access files through an NFS server configured on vm05 . The Apache web server is configured to work with PHP. Our PHP application is configured to connect to a database server hosted on vm04 . Our PHP application uses vm03 as a SQL cache by using the Memcached server.
Note: You can also place a reverse proxy server on the DMZ , and HTTP and other servers behind the firewall for increased security. But it will increase the cost of the project.
From the translator:
The author of the original cycle of articles is extremely laconic and difficult to read. We will try to keep it concise where it is possible and add explanations where the author himself doesn’t understand what he wants to say. The translation allows for a number of deviations from the terms used in the professional environment and stable expressions. The translator asks to show condescension to such cases in the form of personal messages if the found out makes it difficult to understand the text and exposes the ignorance of the writer.
LAMP: Typical and fractional installations
Most likely, your solution based on one dedicated or virtual server looks like this: / +-----------------------------------------+ | Apache + PHP / Perl @ 75.126.153.206:80 | | Mysql@127.0.0.1: 3306 ( UNIX ) | | Pgsql@127.0.0.1: 5432 ( UNIX ) | | Netfilter | +-----------------------------------------+ *** LAMP *** : RHEL/CentOS/Debian/Ubuntu/*BSD/Unix : 4-8GiB ECC : Intel / AMD : RAID-1/5 - SATA/SAS ')
What happens if, say, an Apache web server is compromised? An attacker will gain access to your database, cache, and, as well, to other elements of the system or network. In this case, you need to separate the server services as follows:
////////////////////////// / / / ////////////////////////// \ \ ----------| vm00 75.126.153.206:80 - eth0 192.168.1.1 - eth1 +-----------------------------+ | - | | (Firewall) | eth0:192.168.1.10/vm01 +-----------------------------+ +----------------------+ | | Lighttpd | +-----------------------------------+ | | | /var/www/static | | +----------------------+ | | eth0:192.168.1.11/vm02 +-----------------------------------+-----------------------+ | | Apache+php+perl+python| | | /var/www/html | | +-----------------------+ | | eth0:192.168.1.12/vm03 +-----------------------------------+-----------------------+ | | SQL | | |Redis/Memcached .. | | +-----------------------+ | | eth0:192.168.1.13/vm04 | ( RAID-10) +-----------------------------------+------------------------+ | | Mysql/pgsql | | | @192.168.1.13:3306/5432| | +------------------------+ | | eth0:192.168.1.14/vm05 | ( - NFSv4 RAID-10) +-----------------------------------+------------------------+ | NFSv4 Linux | | /export/{static,html | +------------------------+ Fractional installation has a number of advantages:
- Security
- Scalability
- Optimization
- Ease of use
- Easy monitoring
Add to this advanced features from the High-availability area, such as failover (transfer of images / containers of fractional parts of the system to other resources due to the initial configuration of the vm00 host system for similar network interaction [Virtual-IP at the vm00 level]), load balancing CDNs are becoming much more convenient in the case of a similar system setup.
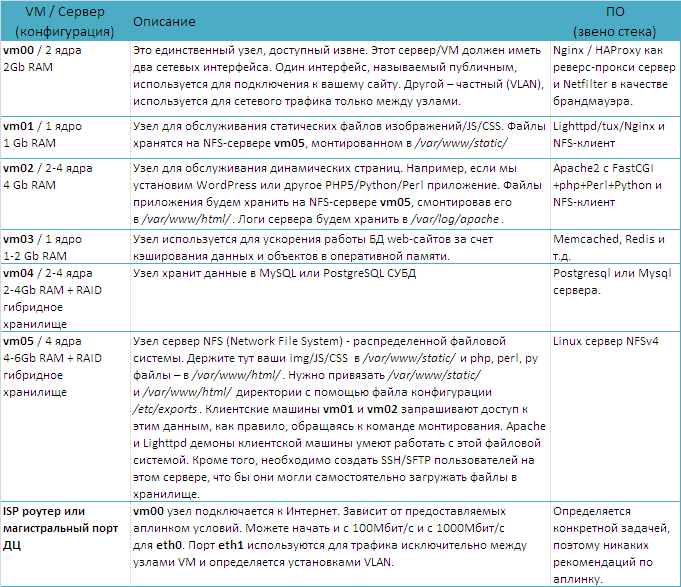
Roles of each virtual machine / server:
Below is detailed information on the appointment of machines. A WordPress blog, a Drupal-based website, or a bespoke application hosted on such servers can easily serve millions of hits per month.
How it works?
Let's see how our system works with a reverse proxy server. In this example, I will place the proxy and HTTP server to the firewall. (see fig. 1). The website www.example.com will be hosted on a static IPv4-address 202.54.1.1 , which is assigned to the eth0 device. The internal IP 192.168.1.1 is assigned to the eth1 device. This is the node of our reverse proxy server. The remaining servers are inside the local network and cannot be directly accessed via the Internet.

The hardware or software (OpenBSD / Linux) firewall rules for host 202.54.1.1 allow access only to ports 80 and 443. All other ports are blocked. Iptables also works on every VM node and access is allowed only to the required ports. Your reverse proxy server defines a pool of HTTP servers as follows:
## - www.example.com ## upstream mybackend { server 192.168.1.10:80; #server1 server 192.168.1.11:80; #server2 .... .. .. server 192.168.1.100:80; # server100 } Apache and Lighttpd servers access files through an NFS server configured on vm05 . The Apache web server is configured to work with PHP. Our PHP application is configured to connect to a database server hosted on vm04 . Our PHP application uses vm03 as a SQL cache by using the Memcached server.
Note: You can also place a reverse proxy server on the DMZ , and HTTP and other servers behind the firewall for increased security. But it will increase the cost of the project.
Stop talking, show me the server setup process.
Most of the actions listed in this note are written with the assumption that they will be performed by the root user in the CentOS 6.x / Red Hat Enterprise Linux 6.x bash console. However, you can easily copy the settings to any other * NIX-like operating systems.- Prologue
- Step # 1: Setup / Installation: NFS File Server
- Step 2: Setup / Installation: MySQL Database Server
- Step 3: Configure / Install: Memcached Caching Server
- Step # 4: Setup / Installation: Apache + php5 web server application
- Step 5: Configure / Install: Lighttpd Web Server for Static Assets </ a
Step 6: Setup / Installation: Nginx reverse (reverse) proxy server
Source: https://habr.com/ru/post/147864/
All Articles