Remote control of a windows user session using standard tools
Once I wanted to manage one of the home computers remotely, but at the same time interact with the current user, but the computer was rather weak and, for example, when starting TeamViewer, the processor load rose to 98% and the computer started to slow down noticeably. I tried the standard RDP, but then the current user was “knocked out” and to log in locally I had to type a password. But a bit later, I accidentally came across the shadow command.
Watch for another remote desktop services session.
SHADOW {<session name> | <Session ID>} [/ SERVER: <server>] [/ V]
<session name> Session name.
<Session ID> Session ID.
/ SERVER: <server> Terminal Server (current by default).
/ V Displays information about actions taken.
For example, to control a console session (a user who is directly sitting in front of a computer) of the current terminal server, just enter the command to execute - shadow 0 . Logout is done via alt * on a regular computer and via ctrl * on a terminal server.
But there is an unpleasant feature: this command works only from under rdp session. But my managed computer was running windows xp so I had to expand its capabilities by making it a terminal server (there are a lot of articles on the Internet how to do this). Then everything became quite simple, we connect with any user with administrator rights in rdp and run the command to execute - shadow 0 we get into the console session, which was exactly what I needed. To reduce hardware costs, when creating an rdp connection, select the function “ On connection, run the next program ” and type shadow 0 there as in the figure.
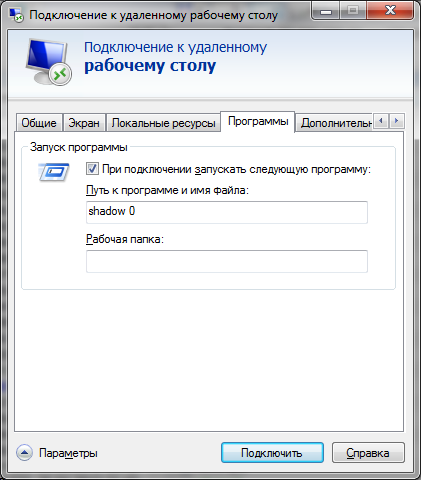
')
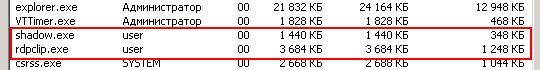
Then it turns out that only 2 processes are started.
In order for all this to work, we must first enable RemoteRPC, for example, through the registry:
[HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Control \ Terminal Server]
“AllowRemoteRPC” = dword: 00000001
After that, it will be possible through the Remote Desktop Services Manager to see which users are logged on to the computer, what id and their processes are running (sorry only for the name, there is no information about the load).
By default, the user will be asked a question with permission to control, you can disable the question or do only remote monitoring, change through the registry:
[HKEY_LOCAL_MACHINE \ SOFTWARE \ Policies \ Microsoft \ Windows NT \ Terminal Services]
“Shadow” = dword: 0000000 x
Where x can be:
0 - remote control is not allowed
1 - full control with the permission of the client
2-complete control without the permission of the client
3-session monitoring with client permission
4 — monitoring the session without the client’s permission
By default, this line does not exist at all and will need to be created.
You can also enable local or domain group policies. To enable it, run gpedit.msc locally - select administrative templates - add and remove templates , add System.adm from the WINDOWS \ inf folder
Now we configure: computer configuration — administrative templates — windows service components — terminal services — sets the rules for remote management . For windows xp.
And the computer configuration — administrative templates — windows components — Remote Desktop Services — Remote Desktop Session Host — Connections — sets remote control rules for remote desktop service user sessions . For windows 7.
All this works in the domain, if the user has the appropriate rights.
In the domain settings of the user profile there is also a setting of such rights (I have seen these settings even in the win 2000 domain)

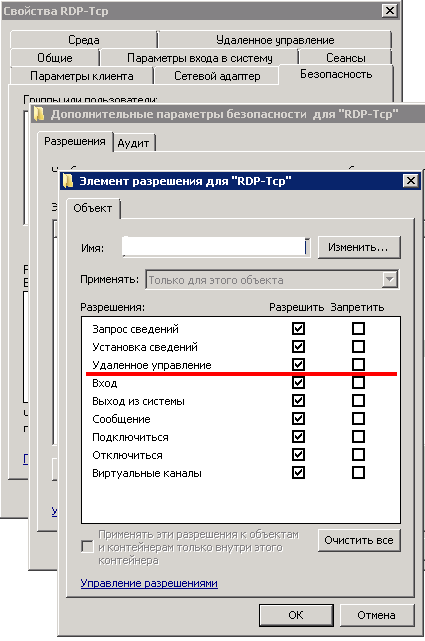
If we consider the terminal server, then there through the RDP properties (through the configuration of the remote desktop session node ) you can set any remote control rights for any user,
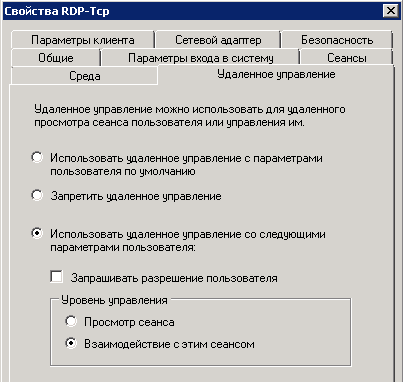
and separately set up interaction or remote session management.
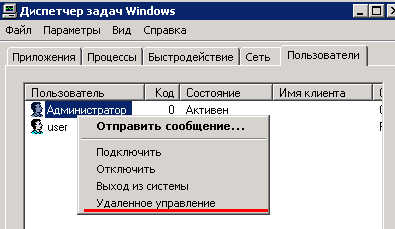
For convenience, you can connect via Task Manager
Watch for another remote desktop services session.
SHADOW {<session name> | <Session ID>} [/ SERVER: <server>] [/ V]
<session name> Session name.
<Session ID> Session ID.
/ SERVER: <server> Terminal Server (current by default).
/ V Displays information about actions taken.
For example, to control a console session (a user who is directly sitting in front of a computer) of the current terminal server, just enter the command to execute - shadow 0 . Logout is done via alt * on a regular computer and via ctrl * on a terminal server.
But there is an unpleasant feature: this command works only from under rdp session. But my managed computer was running windows xp so I had to expand its capabilities by making it a terminal server (there are a lot of articles on the Internet how to do this). Then everything became quite simple, we connect with any user with administrator rights in rdp and run the command to execute - shadow 0 we get into the console session, which was exactly what I needed. To reduce hardware costs, when creating an rdp connection, select the function “ On connection, run the next program ” and type shadow 0 there as in the figure.

')
Then it turns out that only 2 processes are started.

In order for all this to work, we must first enable RemoteRPC, for example, through the registry:
[HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Control \ Terminal Server]
“AllowRemoteRPC” = dword: 00000001
After that, it will be possible through the Remote Desktop Services Manager to see which users are logged on to the computer, what id and their processes are running (sorry only for the name, there is no information about the load).
By default, the user will be asked a question with permission to control, you can disable the question or do only remote monitoring, change through the registry:
[HKEY_LOCAL_MACHINE \ SOFTWARE \ Policies \ Microsoft \ Windows NT \ Terminal Services]
“Shadow” = dword: 0000000 x
Where x can be:
0 - remote control is not allowed
1 - full control with the permission of the client
2-complete control without the permission of the client
3-session monitoring with client permission
4 — monitoring the session without the client’s permission
By default, this line does not exist at all and will need to be created.
You can also enable local or domain group policies. To enable it, run gpedit.msc locally - select administrative templates - add and remove templates , add System.adm from the WINDOWS \ inf folder
Now we configure: computer configuration — administrative templates — windows service components — terminal services — sets the rules for remote management . For windows xp.
And the computer configuration — administrative templates — windows components — Remote Desktop Services — Remote Desktop Session Host — Connections — sets remote control rules for remote desktop service user sessions . For windows 7.
All this works in the domain, if the user has the appropriate rights.
In the domain settings of the user profile there is also a setting of such rights (I have seen these settings even in the win 2000 domain)

If we consider the terminal server, then there through the RDP properties (through the configuration of the remote desktop session node ) you can set any remote control rights for any user,

and separately set up interaction or remote session management.

For convenience, you can connect via Task Manager

Source: https://habr.com/ru/post/147273/
All Articles