Hacking hashes at PHDays 2012: Hash Runner contest

At PHDays 2012 there were a lot of highly technical, interesting, spectacular contests, but one of them was almost unnoticed by the visitors of the forum: it was Hash Runner, whose members were hacking hashes.
At such competitions, as a rule, the dominance of a number of individual teams is preserved : Hashcat , Inside Pro , john-users ... And it is not surprising, since these are communities of developers, testers and users who use the most popular tools for breaking hashes. The secret of success is not only huge experience, well-trained teams and access to impressive computing resources, but also the ability to modify the toolkit on the fly depending on current needs.
The teams listed above took an active part in the Hash Runner competition at PHDays 2012. For two days, the participants fought for the main prize - the AMD Radeon HD 7970 graphics card (the competition started at 10:00 on May 30 and ended at 18:00 on May 31).
')
rules
Any Internet user was admitted to the competition, and in the end, 19 participants from different countries came together in the competition.
The competitors were offered a list of hash functions generated by various algorithms (MD5, SHA-1, BlowFish, GOST3411, etc.). Points for each hacked hash were added depending on the complexity of the algorithm, the rules of generation and the dictionary used. To become a winner, it was necessary to score as many points as possible in a limited time, overtaking all competitors.
Members
Both Russian and foreign hackers took part in the competition. The fight was mainly between the teams InsidePro Team 2012, Teardrop and Xanadrel.
Strategies
In order to successfully complete the competition, participants had to understand the rules for generating passwords. To generate them, dictionaries in different languages were used, as well as dictionaries with names. The rule that participants first picked up was the repetition of a word from the dictionary, for example:
fayettefayette
jeweljewel
hamlethamlet
Each type of hash contained a certain number of passwords generated by the same rules. Picking up a password for a hash encrypted with a simple algorithm, and understanding the generation algorithm, you could apply this knowledge to the rest of the list and pick passwords for more complex hashes.
A rigorous analysis of the rules and laws ultimately allowed the three leaders to be far from their pursuers.
The teams used different tactics: someone tried to pick up passwords to the most difficult hashes and get more points, and on the contrary, someone tried to take in quantities and light up hashes.
Xanadrel (France), who previously performed on the Hashcat team, this time decided to test himself as a human orchestra and took part in the competition alone.
The hardware used by the participant is PC (i7 950, 1x 5770 and 1x 7970) and i5 2300k core for 4 LM hashes. Soft:
- Hashcat;
- oclHashcat-plus;
- ophcrack;
- rcracki_mt;
- passwordspro;
- maskprocessor.
Passwords were cracked using dictionary brute force attacks with writing basic / common rules in Hashcat and passwordspro for GOST hashes. For the entire contest, the participant failed to crack a single DES, phpbb3, ssha, or Wordpress hash (they had an unusual length and could not be cracked using Hashcat).
Already at the end of the contest, Xanadrel remembered brute force and with its help got a couple of passwords of the form 6 {x # _a or 9Mv) 0. Passwords in the form of ddyyyy (for example, “08march1924”) came across: for such cases, you had to create rules for adding or deleting a year (day) and a separate file with the names of the months.
The original of the Xanadrel raitap [eng]
Unlike Xanadrel , who fought alone, the guys from the Insidepro team worked together. Their strategy was simple: try to attack any algorithm at the first opportunity using any technique (read: brute force, dictionaries).
The list of hardware and software used by the command:

Note: since team members broke hashes not all at once, but in turn, the listed software and hardware were used not at the same time, but at different points during the competition.
The guys relied primarily on the software of their development - InsidePro's Extreme GPU Bruteforcer and PasswordsPro, because they supported Wordpress hashes "without salt" - already out of the box. However, one of the team members, during the competition, was able to patch JtR to support hashes without salt, which made it possible to attack such hashes even more successfully.
Details of the competition in the ratirep [eng] Insidepro team.
Another leader of the competition was the Teardrop team, which was formed specifically for participation in the competition by those members of the Hashcat team who were able to take part in it. For work, the guys used the following software:
- Hashcat;
- oclHashcat-plus;
- phillass and DCC2;
- Hashcat-utils and Maskprocessor;
- John the Ripper;
- rcracki_mt for LM;
- PasswordsPro for GOST.
During the competition, team members had to make changes to the oclHashcat-plus and John the Ripper utilities code in order to load PHPass and BFcypt hashes, respectively. Details - in a post on the forum team Hashcat .
Statistics
Some beautiful graphs. This is how the schedule of the participants' progress looks in time
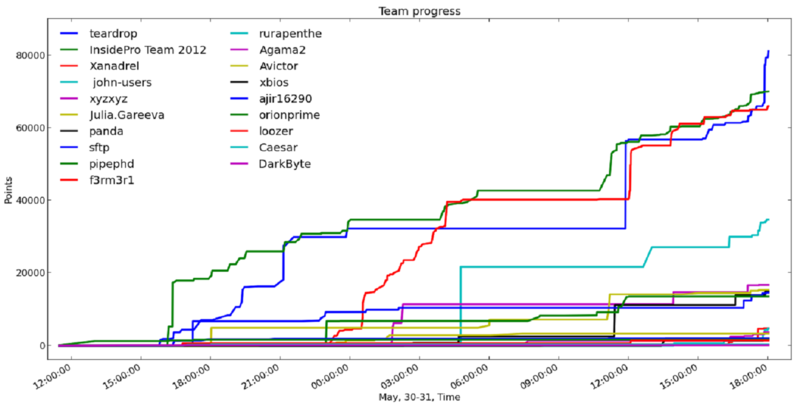
Note that in such contests, teams often wait and do not send answers to the last in order to disorient other participants.
Progress of teams on hacked hashes:
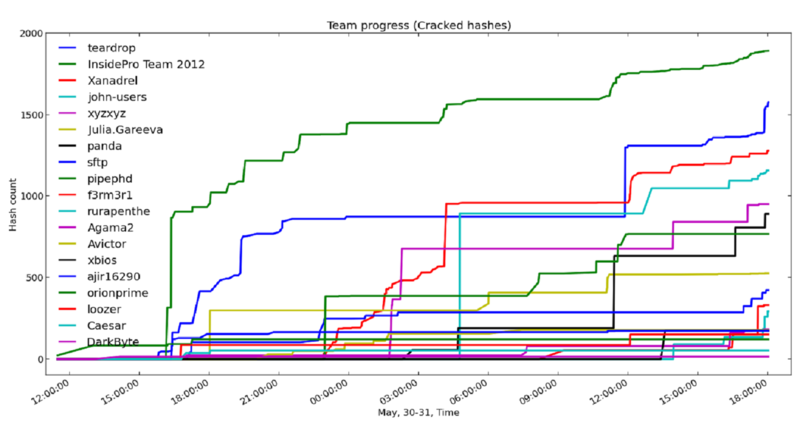
The types of hashes that best served the participants:

Hacked hashes of the top five teams
Teardrop

InsidePro Team 2012

Xanadrel

John-users
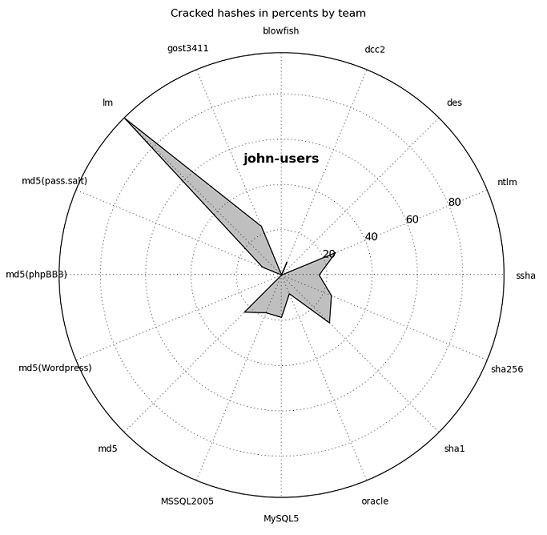
Xyzxyz

Winners
The ending of the competition turned out to be extremely tense: the winner was determined in a few minutes before the end of the competition. Participants stopped their programs a few minutes before the end, and sent those passwords that they managed to pick up.
For a long time, the team was leading InsidePro Team 2012, but the guys from Teardrop managed to snatch the victory and break away by 11,000 points. The pedestal of honor looks like this:
1. Teardrop (Hashcat)
2. InsidePro Team 2012
3. Xanadrel
It is worth noting that the winners were able to pick up passwords for only 11% of all competition hashes.
All participants received gifts from the organizers of the forum and sponsors of the event. Special prize - AMD Radeon HD 7970 graphics card - went to the champions from Teardrop (Hashcat). Congratulations again!
PS The official blog of the PHDays forum contains links to video presentations and slides of presentations.
Source: https://habr.com/ru/post/147271/
All Articles