One Time Secret - burn after reading
If you have ever worried that data that you send over the web (passwords, addresses, meeting points) can be intercepted and stored by an attacker, or simply do not like to leave traces on the web, http s : //onetimesecret.com can can I help you.
This service allows you to create one-time "secrets" - by sending a secret, you get a one-time link to it, after which the secret is deleted.

The service, in addition to simply keeping secrets, can also protect the secret with your password and automatically send a link to it to the specified e-mail address.
You can configure the deadline for self-destruction of a secret, ranging from 5 minutes to 30 days.
')
After creating a "secret", you get two links at once, one, like
onetimesecret.com/secret/SECRET_KEY onetimesecret.com/secret/SECRET_KEY , by which the secret itself is available, and another type onetimesecret.com/private/META_KEY onetimesecret.com/private/META_KEY , by clicking on which you will find out if your “secret” has already been “opened” and how much time is left until self-destruction.Before opening:
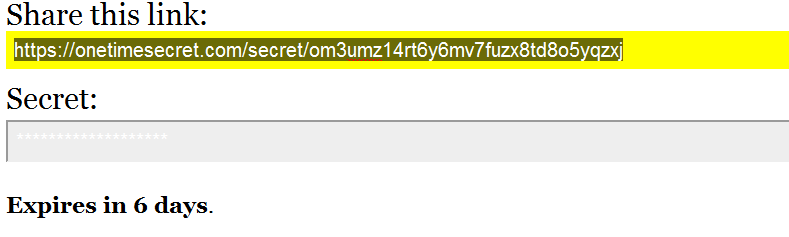
And after:

And, finally, the promised bonus for Habr :)
One Time Secret compares favorably with similar services by the existence of its own API .
Already there are his wrappers for Perl, PHP, Ruby.
I present to you a small Python wrapper:
git: github.com/utter-step/py_onetimesecret
Example of use:
from onetimesecret import OneTimeSecret o = OneTimeSecret("YOUR_EMAIL", "YOUR_OTS_APIKEY") secret = o.share(u", ") # {u'updated': 1340611352, # u'created': 1340611352, # u'recipient': [], # u'metadata_key': u'653lzljgwgj74ys6hvrpta2wmhaamrg', ### (/, , ..). # https://onetimesecret.com/private/META_KEY # u'metadata_ttl': 86400, # u'secret_ttl': 86400, # u'state': u'new', # u'passphrase_required': False, # u'ttl': 86400, # u'secret_key': u'3ery270erhtk1gjsti90d70z5h8aqgd', ### , # https://onetimesecret.com/secret/SECRET_KEY # # u'custid': u'anon'} print o.retrieve_secret(secret[u"secret_key"]) # {u'secret_key': u'dtr7ixukiolpx1i4i87kahmhyoy2q65', # u'value': u', '} print o.retrieve_meta(secret["metadata_key"]) # {u'received': 1340731164, # u'updated': 1340731164, # u'created': 1340731159, # u'recipient': [], # u'metadata_key': u'qvu20axsugif3fo4zjas5ujvp1q9k75', # u'metadata_ttl': 86398, # u'state': u'received', ### # u'ttl': 86400, # u'custid': u'anon'} Thanks for attention!
UPD: as questions like “how can you trust this service” are increasingly being asked, I provide the answer of its authors themselves:
Why should I trust you?
In addition to being really cool guys, we can't really do anything with your information. If it's a password for example, we don’t know the username or even the application that the credentials are for.
If you include a passphrase (available under "Privacy Options"), we can use it to encrypt the secret. It is not possible to decrypt it.
Why can I trust you?
Besides the fact that we are cool guys, we still can not do anything with your information. For example, if it is a password, we do not know the user name, even the site / application to which it relates.
You can also provide a password with which we will encrypt your secret. We do not store your passwords (only bcrypt-hashes from them), so we will never know your secret, as we will not decrypt it.
Source: https://habr.com/ru/post/146588/
All Articles