Show me the money! Big Q $ h Contest at PHDays 2012

Visitors to the Positive Hack Days 2012 forum, which took place recently at the Digital October techno center, could not only listen to the reports of the information security professionals and watch the epic battle of CTF hackers, but also took part in the discussion of important issues of the security industry in the specialized sections.
One of such discussion venues was the section “How do they protect money?”, Moderated by Artem Sychev (Head of the Information Security Department of the Russian Agricultural Bank). In addition to the theory — discussing the pressing issues facing the banking security industry — there was also a practical part in the section — the Big Q $ h Contest. Participants were required to demonstrate their skills in the field of exploiting typical vulnerabilities in the services of RBS systems - mainly logical, rather than web vulnerabilities.
')
Especially for this competition, we have developed our own RB System from scratch and put into it typical vulnerabilities identified by Positive Technologies experts during the security analysis of such systems. The development was named PHDays I-Bank and was a typical Internet bank with a web interface, PIN codes for access to the account and processing.

The day before the contest, participants received an OS image with a deployed RBS system and a test base, as well as, of course, the source codes of this RBS itself. Accordingly, the search for vulnerabilities and writing an exploit was given about a day. During the competition, each participant received his account in the RBS and a real bank card tied to a specific account.

The contest lasted 30 minutes, during which time the participants had to hack the combat base, transfer money from other accounts to theirs, and then - with the help of a issued card - cash the money in the ATM, which was waiting for the winners in the lobby, filled with money.

Although this possibility was not advertised, it was possible to steal money not only from the accounts of the “bank”, but also from other participants of the competition;) The state of the accounts was displayed on a large screen and the audience watched the process going for half an hour and who could
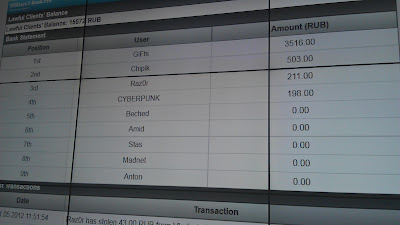
As a result, the winner of the competition was Gifts , which was able to withdraw 3500 rubles., Chipik took the second place (900 rubles), and Raz0r became the third. ATM issued money without problems: everything is fair.

CTF vs Online HackQuest
Further to the competition joined the team of CTF. Their task was to protect RBS. They also got an OS image with a DBO system (and source codes), as well as a test base. They spent 4 hours searching for and fixing vulnerabilities, and it was possible to eliminate vulnerabilities — only without disrupting the system’s operation: a situation in which the system could not be hacked because it didn’t work was not allowed.
The hackers in this competition were Internet users participating in the Online HackQuest competition. After gaining access to the VPN, they had half an hour to launch an attack and withdraw money from the CTF team’s accounts (see our special habratopeke for detailed rules). The winners of this fight left the team CTF: they managed to save almost all their money.
Following the results of the competition, both the participants and the audience agreed that he was a success and became the highlight of the competitive program of the forum. We already have ideas on how to make the competition even more exciting and entertaining, we will try to implement them at PHDays 2013. See you next year!
PS Once again we recall that the above-mentioned RBS system was developed by the specialists of Positive Technologies especially for the competitions within the framework of the PHDays 2012 forum. It is NOT a system that actually works in any of the existing banks; while it is as close as possible to similar systems and contains their characteristic vulnerabilities.
Source: https://habr.com/ru/post/146308/
All Articles