Positive Hack Days CTF 2012. How It Was

The battle of hackers on the principle of Capture The Flag was the highlight of the PHDays 2012 forum program: for two days and one night in non-stop mode, 12 teams from 10 countries hacked into the networks of opponents and defended their own.
The conditions of PHDays CTF , unlike many other similar competitions, were as close as possible to the combat ones: all vulnerabilities were not invented, but really are found in modern information systems. In addition, participants could solve game problems blindly - to attack the system without access to them, but most importantly: this year the competitions were built on the principle of "King of the Hill" (points were awarded not only for capturing systems, but also for keeping them).
')
According to the principle of maximum viability, the competitive infrastructure repeated the structure of corporate networks: the external perimeter consisted of web applications, database servers and various directories (LDAP); only after its capture was it possible to get into the inner perimeter - Microsoft Active Directory. Just like in real life.
Show
To add zest to the competition, we prepared a legend, according to which, during the CTF, changes were made to the infrastructure of the game - in the framework of a single storyline. Participants had to not just get ahead of their rivals, but to save the world as much (the legend of the first and second day of the competition was published on the forum blog).
This year, the tournament also found elements of a reality show: random visitors were handed cards with bonus keys to individual visitors of the forum, which they could, at their discretion, hand over to their favorite team at the end of the second day.
Tests
The case for the competitors was not limited to pure hacking. In the foyer of the Digital October Techno Center, a huge container was installed with specially prepared “garbage” in which participants had to look for bonus keys (flags). On Dumpster Diving, each team was given half an hour.

In addition, on the second day of the Positive Hack Days forum, CTF participants were waiting for new surprises. The first of these was the task of intercepting the control of an AR.Drone aircraft, a device that is controlled from the phone via unsafe wireless connections. To solve this problem, participants were given 30 minutes.
Since the weather in Moscow on May 31 was not flying, launches were held in the lobby of the technical center.

The winner of this competition not only earned bonus points for his team, but also received the aircraft himself in the property. Sergey Azovskov from the team HackerDom (Russia) and Matt Dikof from PPP (USA) became the owners of quadcopters.
Within the framework of the section “How to Protect Money,” a competition was held called “Big $ k. Hackers had to withdraw money from the RBS system, specially designed for this competition. At the second stage of the competition, the CTF teams had to work on the DBS protection (they were given four hours to do this), and then the participants of the online HackQuest competition attacked the systems for 30 minutes and tried to withdraw money from the banks of the CTF teams (details are in our script ).

CTF members were able to win this battle and save almost all their money.
results
The victory in Positive Hack Days CTF 2012 was won by the Russian team Leet More: last year the guys took second place, but this time they did not give their opponents a single chance and took away the top prize of 150,000 rubles. The second were the representatives of Switzerland from 0daysober (100,000 rubles), and the third place and the amount of 50,000 rubles. Spaniards conquered from int3pids. Last year's winners - the PPP team from the USA - placed on the fourth position. The final table looks like this.
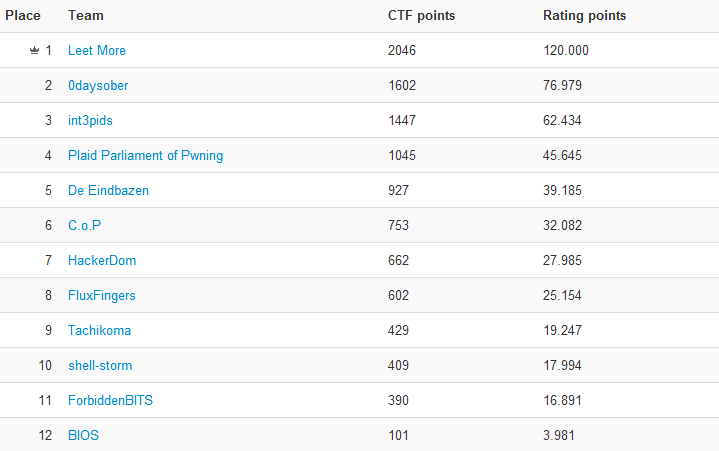
I would like to mention the Tachikoma team from Japan, which consisted of students from four different Japanese universities and debuted on PHDays CTF. The whole Land of the Rising Sun was rooting for the children, and for the first time they performed more than adequately.
0-day
During the CTF, quite interesting vulnerabilities were discovered. Representatives of the Leet More team found a 0-day in freebsd 8.3 release (local vulnerability - bypassing security restrictions). Taking advantage of this vulnerability, it was possible to disrupt the mechanism of protection of flags and remove their flags so that they would not get to rivals. But no one did this :)
In addition, the eindbazen team (the Netherlands) discovered the XSS attack vector against the “King of the Mountain”. The scenario of such a web attack was not provided in preparation for the CTF, so this can also be called a kind of zero-day vulnerability.
Defcon. hello from Moscow
Sadly, Defcon has not moved its qualifying CTF. It is clear that immediately after the forum, the 12 teams that participated in the PHDays CTF could not physically participate normally in the selection: someone was on the plane, and someone was just very tired.
As a result, at the initiative of the PPP team (with a sense of humor, they have order) a photo appeared that “hints as if”.

But everything else was super! Next year we will try to make PHDays CTF even more exciting.
PS The full CTF legend (text + video) and links to forum reviews can be found in the blog of one of the organizers of the competition.
Source: https://habr.com/ru/post/145792/
All Articles