LinkedIn started using salt
LinkedIn has published an addendum to the security rules in the corporate blog: now password hashes on the server will be stored with the addition of salt. LinkedIn employs good IT security experts who have been preparing an upgrade for a long time to have hashes stored with salt. By the time of the leakage, the upgrade has already been made; now we are working on additional security levels.
The LinkedIn director also emphasizes that the email database of users was not indicated in the leaked database , and the FBI was already looking for intruders.
Meanwhile, since the leakage, more than half of the passwords from the published database have been picked up. For example, SophosLabs managed to pick up 3.5 million passwords , i.e. 60% of all unique hashes from a published LinkedIn file (out of 6.5 million hashes, only 5.8 million are unique).
Programs like John the Ripper allow you to brute force vocabulary with word addition and character addition / replacement, so long passwords such as linkedinpassword or p455w0rd are quite easily decoded. Moreover, the program allows you to replenish the dictionary with the passwords found in the process, so after seven passes a password such as m0c.nideknil (from vocabulary linkedin) was found.
')
Example
1st pass. pwdlink from pwlink with the rule “add d to the third position”
2. pwd4link from pwdlink with the rule "insert 4 into fourth position"
3. pwd4linked from pwd4link with the rule “add ed”
4. pw4linked from pwd4linked with the rule “remove the 3rd symbol”
5. pw4linkedin from pw4linked with the rule “add in”
6. mpw4linkedin from pw4linkedin with the rule “add m to the beginning”
7. mw4linkedin from mpw4linkedin with the rule “remove the second character”
8. smw4linkedin from mw4linkedin with the rule “add s to the beginning”
9. sw4linkedin from smw4linkedin with the rule “remove the second character”
10. lsw4linkedin from sw4linkedin with the rule “add l to the beginning”
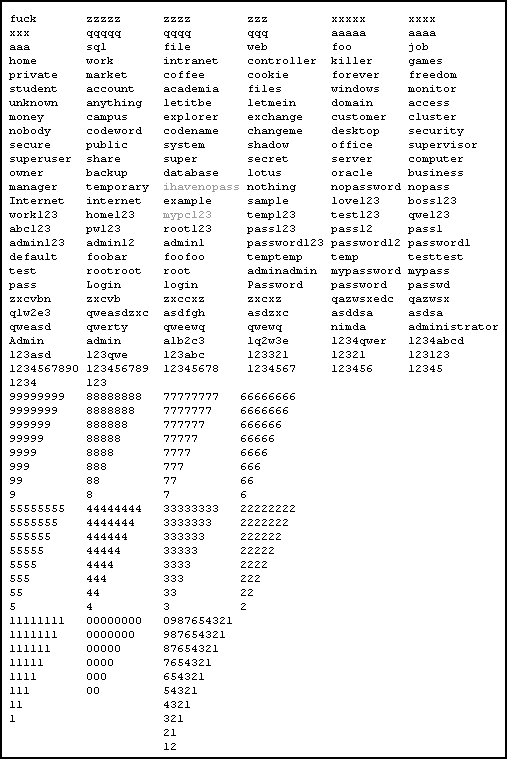
In SophosLabs, besides the usual dictionaries, they also took the dictionary that was used by the Conficker worm. Below is a list of passwords from the Conficker dictionary, all of them were in LinkedIn, except for two (mypc123 and ihavenopass).
See also the 30 most popular passwords stolen from LinkedIn .
The LinkedIn director also emphasizes that the email database of users was not indicated in the leaked database , and the FBI was already looking for intruders.
Meanwhile, since the leakage, more than half of the passwords from the published database have been picked up. For example, SophosLabs managed to pick up 3.5 million passwords , i.e. 60% of all unique hashes from a published LinkedIn file (out of 6.5 million hashes, only 5.8 million are unique).
Programs like John the Ripper allow you to brute force vocabulary with word addition and character addition / replacement, so long passwords such as linkedinpassword or p455w0rd are quite easily decoded. Moreover, the program allows you to replenish the dictionary with the passwords found in the process, so after seven passes a password such as m0c.nideknil (from vocabulary linkedin) was found.
')
Example
1st pass. pwdlink from pwlink with the rule “add d to the third position”
2. pwd4link from pwdlink with the rule "insert 4 into fourth position"
3. pwd4linked from pwd4link with the rule “add ed”
4. pw4linked from pwd4linked with the rule “remove the 3rd symbol”
5. pw4linkedin from pw4linked with the rule “add in”
6. mpw4linkedin from pw4linkedin with the rule “add m to the beginning”
7. mw4linkedin from mpw4linkedin with the rule “remove the second character”
8. smw4linkedin from mw4linkedin with the rule “add s to the beginning”
9. sw4linkedin from smw4linkedin with the rule “remove the second character”
10. lsw4linkedin from sw4linkedin with the rule “add l to the beginning”
In SophosLabs, besides the usual dictionaries, they also took the dictionary that was used by the Conficker worm. Below is a list of passwords from the Conficker dictionary, all of them were in LinkedIn, except for two (mypc123 and ihavenopass).

See also the 30 most popular passwords stolen from LinkedIn .
Source: https://habr.com/ru/post/145642/
All Articles