Bluetooth Spying - W32.Flamer Features
 Our new friend W32.Flamer never ceases to amaze. Today we will talk about the potential use of Bluetooth technology by this worm.
Our new friend W32.Flamer never ceases to amaze. Today we will talk about the potential use of Bluetooth technology by this worm.Attackers are able to identify the user's mobile device at a distance of one mile and even track the location of the victim, steal confidential information and listen to conversations.
Of all the threats detected so far for Windows platforms, W32.Flamer is the only malware that is widely used by Bluetooth technology, which is another strong confirmation of its creation as a spyware tool for unauthorized information gathering.
')
The functionality using Bluetooth technology is implemented in the “BeetleJuice” module. It is launched in accordance with the values of the configuration parameters specified by the attacker. At startup, it first searches for all available Bluetooth devices. When a device is detected, its status is requested and the device parameters are recorded, including the identifier, presumably for sending to the attacker. Next, he sets up himself as a Bluetooth beacon. This means that the computer infected with the W32.Flamer worm will always be visible when searching for Bluetooth devices. In addition to self-highlighting, W32.Flamer encodes information about an infected computer and then saves it in a special “description” field.
Below are several scenarios for using the Bluetooth worm W32.Flamer.
Scenario number 1 - Definition of social relations of the victim
Constant monitoring of Bluetooth devices within the reach of an infected W32.Flamer worm computer allows an attacker to fix devices detected during the day. This is especially effective if the infected computer is a laptop, because the victim usually carries it with him. After some time, the attacker receives a list of various detected devices - mainly mobile phones of friends and acquaintances of the victim. And based on such observations, he creates a scheme of the relationship of the victim with other people and determines its social connections and professional circle of friends.
Scenario number 2 - Identification of the location of the victim

After infecting a computer, an attacker may decide that its owner is especially interesting to him. Perhaps he knows the building in which the victim is located, but not her office. However, using Bluetooth technology, an attacker can determine the location of infected devices.
By measuring the level of a radio signal, an attacker can determine if a victim is approaching or moving away from a particular infected device. Using the Bluetooth beacon mode and information about the infected device allows an attacker to determine the physical location of the infected computer or device of the victim.
The preferred alternative to locating a computer is to identify the victim’s mobile phone. The “BeetleJuice” module has already compiled a list of device identifiers located next to the infected computer, so the attacker knows which devices belong to the victim. One of them is a mobile phone, which most of the time is located directly next to the person. And now the attacker can conduct passive monitoring without the need to install or modify its devices. Bluetooth monitoring equipment can be installed at airports, train stations and any transportation hubs; and this equipment will search for device identifiers belonging to the victim. Some types of attacks allow you to identify a Bluetooth device at a distance of more than a mile (1609 m). The most sinister aspect of such surveillance is the possibility of accurate localization of the victim and easier tracking it in the future.
Scenario number 3 - Advanced collection of information
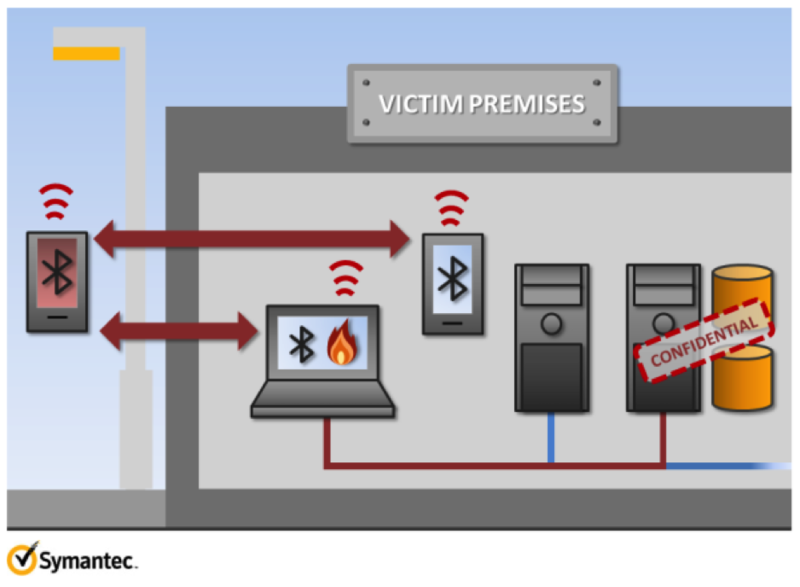
A significant part of the W32.Flamer functionality is implemented as Lua scripts, or “applications” ('apps') downloaded from the application storage ('apprepository') FLAME. It’s easy for an attacker to place a newly infected Bluetooth Lua application in FLAME storage for downloading to an infected device. With increased functionality, an attacker who has already identified Bluetooth devices within range can launch a series of attacks:
- To steal contacts from the address book, SMS-messages, pictures and much more;
- Use a Bluetooth device for eavesdropping, connecting the infected computer to it as an audio headset; when a Bluetooth device is in a conference room or a call is being made from it, an attacker can hear everything;
- Transfer stolen data through the communication channels of another device, which allows you to bypass firewalls and network monitoring tools. To do this, an attacker can use their own Bluetooth device within a mile of the source.
It is possible that W32.Flamer contains undisclosed code that already achieves these goals. For example, despite the fact that we have not yet discovered the beacon code, one infected computer may communicate with another via Bluetooth. And if the second computer connected to the protected network was infected via a USB connection, then the only available network for it could be an existing Bluetooth connection to the infected computer. A code to ensure this may already be available in Win32.Flamer.
The assumptions described are actionable attacks that can be easily implemented with proper technical training. And the complexity of W32.Flamer indicates a very good technical training of intruders, and such attacks are possible.
To be continued…
Source: https://habr.com/ru/post/145438/
All Articles