Overview of Runet DDoS Attacks: 9: 1 in favor of the primitive
Reporting article on the seminar "DDoS attacks and protection against them" (RIGF, May 14, 2012, Moscow)
Speaker: Artyom Gavrichenkov , leading network filtering developer Qrator
Topic: DDoS attacks in 2011-2012: nature and trends
We give an overview of DDoS-attacks over the past year and a half and talk about what should be feared and what not. Let's start with the trivial statistics, the data of which are based on the HLL client base: unfortunately, no company has a universal all-seeing eye. So, for 2011-2012. We have witnessed more than 2,500 DDoS attacks.
')

ICMP / UDP / SYN / ACK flood is only 18%. The average attack power is 300 Mbit / s. Over 1 Gbit / s had 40 incidents. The largest total attack traffic on the band - 56 Gbit / s - was recorded on the online store of magnetic toys in July 2011. The attack was partially directed at our domain, there is reason to believe that the attackers tried to bring down Qrator entirely, “spreading” the attack traffic over the network.
The number of DDoS attacks on the strip is constantly decreasing. And all because most mid-level hosting providers have become ready for them. Small attacks are easy to resist, but powerful ones cannot last for long, as even trunk providers begin to experience problems with them.
Criminals prefer high-level attacks of transport and application level (82%). They are counting on the exhaustion of server resources within established TCP connections, so the number of IP addresses involved in the attack is important. Intellectual attacks on the application are insidious because even with a protection strategy, you are likely to lose some, albeit scanty, part of legitimate users.
At least 50% of attacks of Layer 7 are “swotting” into one URI, intellectual attacks are only about 10% . The first mass robot that had a well-written network stack with HTTP and Javascript and correctly navigated the site was Minerbot , which attacked German and Russian e-commerce sites last fall. The number of bots with full Web browser capabilities (TCP, HTTP / 1.1, JS) is steadily increasing, especially in expensive custom attacks. Probably, the industry is moving towards using full-fledged browsers to perform DDoS attacks.

Note one more unpleasant trend - the owners of botnets began to cooperate. During the year, Qrator detected 4 attacks carried out simultaneously by several botnets with different attack strategies. Recall the high-profile cases with Ekho Moskvy (3 botnets) and Habrahabrom (4-5).
From January to December 2011, the maximum duration of the attack was 486 hours. How it was? A botnet from the CIS and Baltic countries attacked the online store of cedar barrels. The first three days he tried to break through the defense, but disappointed, went to make money somewhere else. But as soon as we started unblocking IP-addresses, he immediately returned. The attacker kept two or three bots, and as soon as the request passed, he called up another 5,000. In this mode, the botnet can function forever, carrying out attacks on several sites with minimal resources.
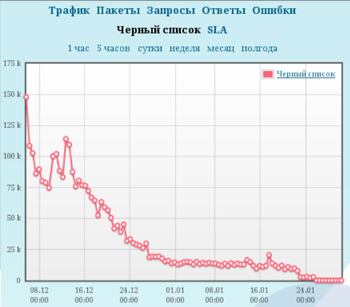 December 4, 2011, it turned out that not everyone cares about the resources of a botnet. The maximum duration of DDoS attacks reached 1228 hours. If slon.ru were not under protection, then it would lie for 2 months. Within a couple of hours, more than 200 thousand bots from the countries of South and Southeast Asia entered the site. Thus, the attack set another record in the history of Qrator - the size of the botnet. And although it did not bring any result anymore, the attacker still kept the traffic, and there were a lot of bots. But the most interesting thing is that, apparently, this same botnet with the size of about 182,000 machines returned to slon.ru and to tvrain.ru on May 6, 2012, and the intersection of the “December” and “May” stop-lists was about 500 IP Addresses For six months, the botnet of a couple of hundreds of thousands of machines has been updated almost completely - or in fact it is many times more.
December 4, 2011, it turned out that not everyone cares about the resources of a botnet. The maximum duration of DDoS attacks reached 1228 hours. If slon.ru were not under protection, then it would lie for 2 months. Within a couple of hours, more than 200 thousand bots from the countries of South and Southeast Asia entered the site. Thus, the attack set another record in the history of Qrator - the size of the botnet. And although it did not bring any result anymore, the attacker still kept the traffic, and there were a lot of bots. But the most interesting thing is that, apparently, this same botnet with the size of about 182,000 machines returned to slon.ru and to tvrain.ru on May 6, 2012, and the intersection of the “December” and “May” stop-lists was about 500 IP Addresses For six months, the botnet of a couple of hundreds of thousands of machines has been updated almost completely - or in fact it is many times more.
By the way, during the attacks of December 4, 2011, we expected that the botnets would intersect: after all, media outlets similar in ideology were smashed. However, the intersection was not observed. But in May, we clearly saw how one botnet worked against both Russian and Armenian media.
Coordination of botnets is growing. Increasingly, we are not dealing with a botnet that has a single control center, which cannot operate under heavy load, but with a peering network. Therefore, the discovery of the source of the attack is becoming increasingly difficult, especially in the absence of non-technical clues. It is almost impossible to catch the organizers of DDoS attacks.
Although not so long ago, we found the source of a single attack on online media and passed its IP address to the owner of the resource (which, in turn, passed it on to law enforcement agencies). The attacker first used a botnet, but at the time when the site was under protection, he attracted other resources, including a list of anonymous proxies. Some of them were not so anonymous and put the HTTP header X-Forwarded-For, which, in fact, was the IP-address of the attacking server. Quite trivial, but it turns out that not everyone thinks about it. The probability of error is small: the potential artist has found personal motives.
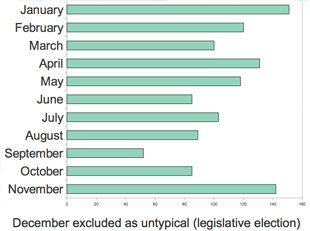 Speaking about the distribution of DDoS-attacks by months , we note that from June to September, criminals reduce their activity. On the days of the week, their efforts are distributed almost evenly with some decline on the weekend. But, as a rule, on weekends the most powerful attacks on the strip happen. What is the reason for this? If, say, an attack of 56 Gbit / s happens on Tuesday, then there are certain reasons to hope that in the near future one of the backers will react and we will be able to agree with him. On weekends, technical support even for large providers often
Speaking about the distribution of DDoS-attacks by months , we note that from June to September, criminals reduce their activity. On the days of the week, their efforts are distributed almost evenly with some decline on the weekend. But, as a rule, on weekends the most powerful attacks on the strip happen. What is the reason for this? If, say, an attack of 56 Gbit / s happens on Tuesday, then there are certain reasons to hope that in the near future one of the backers will react and we will be able to agree with him. On weekends, technical support even for large providers often does not work less efficiently than on weekdays.
So far, ADSL is saving Russia: the entrance is large, the output is small. Therefore, many attacks on the strip does not occur. But do not forget about such a horror story as the work of IXP, which in every way ignore the incoming requests to them. What does this look like? A major attack begins on one of our clients, which creates problems for some of the sites where we are located. And we see that the garbage traffic comes from some Internet Exchange. In order not to balance the network once again, we first write them a polite opus like, “From one of your clients, there is a decent amount of ICMP flood, this is wrong, sort it out.”
“It’s not stopped yet.
It is ICMP traffic with spoofed source addresses.
Our suggestion is that you should be connected to * ^ # $ ^ * - IX. "
We get the answer like this: “Technically, we can’t do anything. In general, we provide a service to a client, he pays us money, maybe you will let him in a null route? ”
“* ^ # $ ^ * - IX only operates the L2 exchange fabric. We are not involved in routing issues ourselves. Please contact your relevant business partners in order to investigate this.
One idea is a route at the border? ”
In the null route we’ll let him go, but then he will come to us not through this IX, but through Rostelecom, for example. No sense from this. We have been saying for quite a long time that providers, IXP and ISP must have some kind of awareness , willingness to work with such things. But, unfortunately, while we do not see it very much.
Let's talk about the objectives of the attackers. The traditional finance-politics-social protest-theft of data-botnet self-promotion was added to the new goal - extortion of bitcoins. Criminals send a letter demanding to issue a certain amount in bitcoins, and in case of disobedience they threaten a large DDoS attack. And, as a rule, the victim’s inaction is indeed accompanied by an intellectual attack on the application. Everyone is probably already accustomed to letters from schoolchildren from the series “Transfer me $ 1000 to Yandex.Money, or your site will be two weeks from now.” This is the same, but at a qualitatively new level, and this should be feared. And since bitcoins are not an official means of payment, it is almost impossible to attract for extortion in this case.
Finally, we want to remind everyone that it is not necessary to have an attack of 6-7 Gbit / s to take shape. It is dangerous just targeted attack on the application, even with a small botnet. Until 2010, the fight against DDoS attacks for Russian web applications was to block foreign traffic. Today, anyone can purchase geo-referenced bots in any region. Yes, Russian botnets are few, but they are.
Focusing on another important point. If an application received an attack of 5,000 bots and it "went into hibernation", this does not mean that the attacker did not have additional bots in stock. As soon as the resource does not stack under a small load, as a rule, the attack power increases 1-2 times, there is a tenfold increase. Therefore, prepare a sleigh in the summer. And remember that in the case of a DDoS attack, you have to pay for a non-working site. If you usually pay the provider for 2-3 megabits, then after the incident, be prepared to account for up to five zeros. Agree, it will be insulting.
90% of DDoS attacks are pretty primitive, uninteresting games. The numerical superiority of the "guests" is not a reason for panic. Escape is not the best strategy. Practice ahead of time, build a tight defense, arm yourself with tactics, improvise. Play by your own rules. In the end, the game goes on your field.
Speaker: Artyom Gavrichenkov , leading network filtering developer Qrator
Topic: DDoS attacks in 2011-2012: nature and trends
We give an overview of DDoS-attacks over the past year and a half and talk about what should be feared and what not. Let's start with the trivial statistics, the data of which are based on the HLL client base: unfortunately, no company has a universal all-seeing eye. So, for 2011-2012. We have witnessed more than 2,500 DDoS attacks.
')

No Time for losers
ICMP / UDP / SYN / ACK flood is only 18%. The average attack power is 300 Mbit / s. Over 1 Gbit / s had 40 incidents. The largest total attack traffic on the band - 56 Gbit / s - was recorded on the online store of magnetic toys in July 2011. The attack was partially directed at our domain, there is reason to believe that the attackers tried to bring down Qrator entirely, “spreading” the attack traffic over the network.
The number of DDoS attacks on the strip is constantly decreasing. And all because most mid-level hosting providers have become ready for them. Small attacks are easy to resist, but powerful ones cannot last for long, as even trunk providers begin to experience problems with them.
The Champions!
Criminals prefer high-level attacks of transport and application level (82%). They are counting on the exhaustion of server resources within established TCP connections, so the number of IP addresses involved in the attack is important. Intellectual attacks on the application are insidious because even with a protection strategy, you are likely to lose some, albeit scanty, part of legitimate users.
At least 50% of attacks of Layer 7 are “swotting” into one URI, intellectual attacks are only about 10% . The first mass robot that had a well-written network stack with HTTP and Javascript and correctly navigated the site was Minerbot , which attacked German and Russian e-commerce sites last fall. The number of bots with full Web browser capabilities (TCP, HTTP / 1.1, JS) is steadily increasing, especially in expensive custom attacks. Probably, the industry is moving towards using full-fledged browsers to perform DDoS attacks.

Note one more unpleasant trend - the owners of botnets began to cooperate. During the year, Qrator detected 4 attacks carried out simultaneously by several botnets with different attack strategies. Recall the high-profile cases with Ekho Moskvy (3 botnets) and Habrahabrom (4-5).
Keep on fighting - till the end
From January to December 2011, the maximum duration of the attack was 486 hours. How it was? A botnet from the CIS and Baltic countries attacked the online store of cedar barrels. The first three days he tried to break through the defense, but disappointed, went to make money somewhere else. But as soon as we started unblocking IP-addresses, he immediately returned. The attacker kept two or three bots, and as soon as the request passed, he called up another 5,000. In this mode, the botnet can function forever, carrying out attacks on several sites with minimal resources.
When I get older I will be stronger
 December 4, 2011, it turned out that not everyone cares about the resources of a botnet. The maximum duration of DDoS attacks reached 1228 hours. If slon.ru were not under protection, then it would lie for 2 months. Within a couple of hours, more than 200 thousand bots from the countries of South and Southeast Asia entered the site. Thus, the attack set another record in the history of Qrator - the size of the botnet. And although it did not bring any result anymore, the attacker still kept the traffic, and there were a lot of bots. But the most interesting thing is that, apparently, this same botnet with the size of about 182,000 machines returned to slon.ru and to tvrain.ru on May 6, 2012, and the intersection of the “December” and “May” stop-lists was about 500 IP Addresses For six months, the botnet of a couple of hundreds of thousands of machines has been updated almost completely - or in fact it is many times more.
December 4, 2011, it turned out that not everyone cares about the resources of a botnet. The maximum duration of DDoS attacks reached 1228 hours. If slon.ru were not under protection, then it would lie for 2 months. Within a couple of hours, more than 200 thousand bots from the countries of South and Southeast Asia entered the site. Thus, the attack set another record in the history of Qrator - the size of the botnet. And although it did not bring any result anymore, the attacker still kept the traffic, and there were a lot of bots. But the most interesting thing is that, apparently, this same botnet with the size of about 182,000 machines returned to slon.ru and to tvrain.ru on May 6, 2012, and the intersection of the “December” and “May” stop-lists was about 500 IP Addresses For six months, the botnet of a couple of hundreds of thousands of machines has been updated almost completely - or in fact it is many times more.By the way, during the attacks of December 4, 2011, we expected that the botnets would intersect: after all, media outlets similar in ideology were smashed. However, the intersection was not observed. But in May, we clearly saw how one botnet worked against both Russian and Armenian media.
Give me freedom, give me fire
Coordination of botnets is growing. Increasingly, we are not dealing with a botnet that has a single control center, which cannot operate under heavy load, but with a peering network. Therefore, the discovery of the source of the attack is becoming increasingly difficult, especially in the absence of non-technical clues. It is almost impossible to catch the organizers of DDoS attacks.
Although not so long ago, we found the source of a single attack on online media and passed its IP address to the owner of the resource (which, in turn, passed it on to law enforcement agencies). The attacker first used a botnet, but at the time when the site was under protection, he attracted other resources, including a list of anonymous proxies. Some of them were not so anonymous and put the HTTP header X-Forwarded-For, which, in fact, was the IP-address of the attacking server. Quite trivial, but it turns out that not everyone thinks about it. The probability of error is small: the potential artist has found personal motives.
And if you fall, get up, eh eh
 Speaking about the distribution of DDoS-attacks by months , we note that from June to September, criminals reduce their activity. On the days of the week, their efforts are distributed almost evenly with some decline on the weekend. But, as a rule, on weekends the most powerful attacks on the strip happen. What is the reason for this? If, say, an attack of 56 Gbit / s happens on Tuesday, then there are certain reasons to hope that in the near future one of the backers will react and we will be able to agree with him. On weekends, technical support even for large providers often
Speaking about the distribution of DDoS-attacks by months , we note that from June to September, criminals reduce their activity. On the days of the week, their efforts are distributed almost evenly with some decline on the weekend. But, as a rule, on weekends the most powerful attacks on the strip happen. What is the reason for this? If, say, an attack of 56 Gbit / s happens on Tuesday, then there are certain reasons to hope that in the near future one of the backers will react and we will be able to agree with him. On weekends, technical support even for large providers often But it's been no bed of roses
So far, ADSL is saving Russia: the entrance is large, the output is small. Therefore, many attacks on the strip does not occur. But do not forget about such a horror story as the work of IXP, which in every way ignore the incoming requests to them. What does this look like? A major attack begins on one of our clients, which creates problems for some of the sites where we are located. And we see that the garbage traffic comes from some Internet Exchange. In order not to balance the network once again, we first write them a polite opus like, “From one of your clients, there is a decent amount of ICMP flood, this is wrong, sort it out.”
“It’s not stopped yet.
It is ICMP traffic with spoofed source addresses.
Our suggestion is that you should be connected to * ^ # $ ^ * - IX. "
We get the answer like this: “Technically, we can’t do anything. In general, we provide a service to a client, he pays us money, maybe you will let him in a null route? ”
“* ^ # $ ^ * - IX only operates the L2 exchange fabric. We are not involved in routing issues ourselves. Please contact your relevant business partners in order to investigate this.
One idea is a route at the border? ”
In the null route we’ll let him go, but then he will come to us not through this IX, but through Rostelecom, for example. No sense from this. We have been saying for quite a long time that providers, IXP and ISP must have some kind of awareness , willingness to work with such things. But, unfortunately, while we do not see it very much.
Choosing your battles
Let's talk about the objectives of the attackers. The traditional finance-politics-social protest-theft of data-botnet self-promotion was added to the new goal - extortion of bitcoins. Criminals send a letter demanding to issue a certain amount in bitcoins, and in case of disobedience they threaten a large DDoS attack. And, as a rule, the victim’s inaction is indeed accompanied by an intellectual attack on the application. Everyone is probably already accustomed to letters from schoolchildren from the series “Transfer me $ 1000 to Yandex.Money, or your site will be two weeks from now.” This is the same, but at a qualitatively new level, and this should be feared. And since bitcoins are not an official means of payment, it is almost impossible to attract for extortion in this case.
Every nations, all around us
Finally, we want to remind everyone that it is not necessary to have an attack of 6-7 Gbit / s to take shape. It is dangerous just targeted attack on the application, even with a small botnet. Until 2010, the fight against DDoS attacks for Russian web applications was to block foreign traffic. Today, anyone can purchase geo-referenced bots in any region. Yes, Russian botnets are few, but they are.
Achtung!
Focusing on another important point. If an application received an attack of 5,000 bots and it "went into hibernation", this does not mean that the attacker did not have additional bots in stock. As soon as the resource does not stack under a small load, as a rule, the attack power increases 1-2 times, there is a tenfold increase. Therefore, prepare a sleigh in the summer. And remember that in the case of a DDoS attack, you have to pay for a non-working site. If you usually pay the provider for 2-3 megabits, then after the incident, be prepared to account for up to five zeros. Agree, it will be insulting.
Let's rejoice in the beautiful game
90% of DDoS attacks are pretty primitive, uninteresting games. The numerical superiority of the "guests" is not a reason for panic. Escape is not the best strategy. Practice ahead of time, build a tight defense, arm yourself with tactics, improvise. Play by your own rules. In the end, the game goes on your field.
Source: https://habr.com/ru/post/145137/
All Articles