Banks. Errors and Vulnerabilities
I decided for the sake of interest to dedicate the day to the review of the sites of banks.
The first of these was the official site of Rosselkhoz Bank (advertising made itself felt :)), the next Russian Standard Bank, then X Bank (X Bank is a bank that did not respond to 2 of my notices and did not close the hole) and finally Alfa Bank .
The goal was not to hack or get any sensitive information to be displayed, but just to check how well the official websites of banks are made.
Powered by CMS Bitrix
The first thing that caught my eye was the news output module, because there are options for choosing the year, month, day, and more news on one page.
')
In the address bar, specifying the year 200 and month 20, I saw that there were no error messages and moreover - this data appeared in the selection on the page, which means the incoming data is displayed on the page.
Then I decided to check the possibility of SQL injection - unsuccessfully.
The next step was to check for XSS - this is where it became interesting.
Specialist. characters are not escaped and html characters are not converted to html entities, which means you can embed any code.
Unfortunately (or, fortunately, the bank) all attempts to implement XSS such as an alert or iframe call failed because a space was inserted into the first tag.
Incoming data:
At the exit:
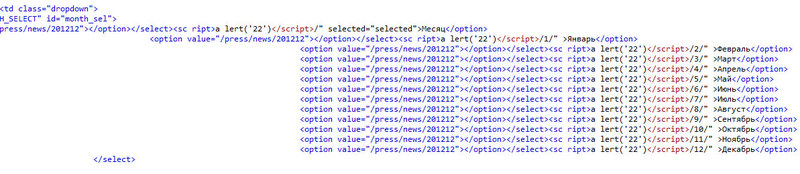
The maximum that can be done is to insert a picture or link (without calling the js code).

The next step was to check the restrictions, on the page you can choose from 5 to 20 news.
But as you probably already understood, the restriction can be circumvented.
You can safely indicate 100,000 news items, after which all the news will appear on the site.
The news page also saw that links to news had a strange ending.

All attempts to manipulate this variable failed, although I suspect that if Register_Globals were enabled, then XSS could be performed.
Then I decided to go to the press center page, there I saw a similar error, but without the $ page variable
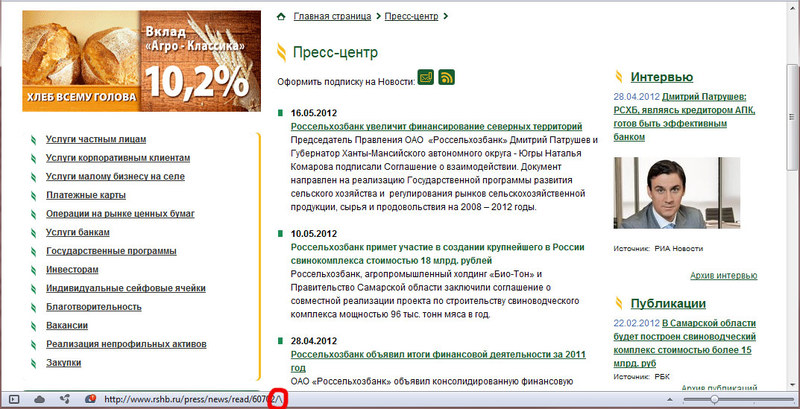
I decided to make manipulations on this page - successfully. When the page was passed to the GET variable, the entire content of the variable was output in the link, but the double quote was converted.

The answer came a few hours later, thanked and asked where such care about their bank came from :)
The errors themselves were corrected in about 3-4 days, except for the output of all the news, apparently, did not consider this a mistake.
CMS site did not recognize.
The essence of the XSS vulnerability is that the parameter from the GET request is transferred to the page code in several places, but the most important thing is in the js code.
In this js code, the variable requestUri is defined (responsible for the address of the current page), but when passing parameters, there is no single quote escaping, which allows us to execute arbitrary js code.

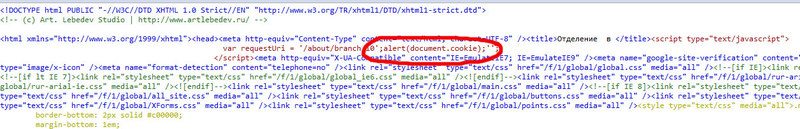
Then did not check the site, because this is enough.
The answer received 31.05.
X bank is a bank that did not respond to my 2 notifications and did not close the hole like that, so I decided not to “shine” it.
The banal error is the search form.
There is no filtering, add a quotation mark and close the input, then insert any code.
Then did not check the site, because this is enough.
The answer has not yet been followed, as well as the correction of errors.
I had a glimpse of the long-suffering Alfa-Bank, namely, the subdomain of the idea.alphabank - also found XSS, the only thing that prevented the successful execution of the code is a slash, it is perceived as a separator, parameters passed through GET (idea.alfabank.ru/accepted/page88 any_code )
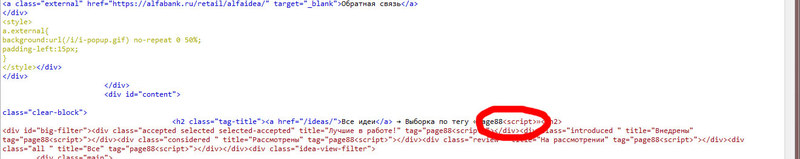
The first message apparently did not reach or for some reason was missed. From the second notification - answered quickly and patched the hole.
Unfortunately, such errors are corrected very slowly, especially for some people had to re-send a message with a description of the errors, so that they finally closed.
When navigating external links, be sure to check their path, even if the link leads to a reliable site, so as not to become a victim of a hacker.
The first of these was the official site of Rosselkhoz Bank (advertising made itself felt :)), the next Russian Standard Bank, then X Bank (X Bank is a bank that did not respond to 2 of my notices and did not close the hole) and finally Alfa Bank .
The goal was not to hack or get any sensitive information to be displayed, but just to check how well the official websites of banks are made.
Russian Agricultural Bank
Powered by CMS Bitrix
Errors.
The first thing that caught my eye was the news output module, because there are options for choosing the year, month, day, and more news on one page.
')
Date picker
In the address bar, specifying the year 200 and month 20, I saw that there were no error messages and moreover - this data appeared in the selection on the page, which means the incoming data is displayed on the page.
Then I decided to check the possibility of SQL injection - unsuccessfully.
The next step was to check for XSS - this is where it became interesting.
Specialist. characters are not escaped and html characters are not converted to html entities, which means you can embed any code.
Unfortunately (or, fortunately, the bank) all attempts to implement XSS such as an alert or iframe call failed because a space was inserted into the first tag.
Incoming data:
20"></option></select><script> At the exit:
20"></option></select><sc ript> 
The maximum that can be done is to insert a picture or link (without calling the js code).

Limit the number of news.
The next step was to check the restrictions, on the page you can choose from 5 to 20 news.
But as you probably already understood, the restriction can be circumvented.
You can safely indicate 100,000 news items, after which all the news will appear on the site.
Links to news.
The news page also saw that links to news had a strange ending.

All attempts to manipulate this variable failed, although I suspect that if Register_Globals were enabled, then XSS could be performed.
Then I decided to go to the press center page, there I saw a similar error, but without the $ page variable

I decided to make manipulations on this page - successfully. When the page was passed to the GET variable, the entire content of the variable was output in the link, but the double quote was converted.

Answer.
The answer came a few hours later, thanked and asked where such care about their bank came from :)
The errors themselves were corrected in about 3-4 days, except for the output of all the news, apparently, did not consider this a mistake.
Russian Standard Bank
CMS site did not recognize.
Xss
The essence of the XSS vulnerability is that the parameter from the GET request is transferred to the page code in several places, but the most important thing is in the js code.
In this js code, the variable requestUri is defined (responsible for the address of the current page), but when passing parameters, there is no single quote escaping, which allows us to execute arbitrary js code.


Then did not check the site, because this is enough.
Answer.
The answer received 31.05.
X bank
X bank is a bank that did not respond to my 2 notifications and did not close the hole like that, so I decided not to “shine” it.
The banal error is the search form.
There is no filtering, add a quotation mark and close the input, then insert any code.
Then did not check the site, because this is enough.
Answer.
The answer has not yet been followed, as well as the correction of errors.
Alfa Bank
I had a glimpse of the long-suffering Alfa-Bank, namely, the subdomain of the idea.alphabank - also found XSS, the only thing that prevented the successful execution of the code is a slash, it is perceived as a separator, parameters passed through GET (idea.alfabank.ru/accepted/page88 any_code )

Answer.
The first message apparently did not reach or for some reason was missed. From the second notification - answered quickly and patched the hole.
Total.
Unfortunately, such errors are corrected very slowly, especially for some people had to re-send a message with a description of the errors, so that they finally closed.
Council
When navigating external links, be sure to check their path, even if the link leads to a reliable site, so as not to become a victim of a hacker.
Source: https://habr.com/ru/post/144904/
All Articles