Mobile threat detection technologies. A little bit about Origins Tracing ™
Dear habravchane, we have repeatedly told you about the threats to Android and, probably, already you have eaten some skeptics. Today we will offer you to talk, rather, not about malware for this mobile platform, but about the technologies used to detect it. And let's begin our story, perhaps, with the Origins Tracing technology implemented in Dr.Web for Android.
All your questions on this topic today are not answered by marketers of any kind, but by Dr. Web analyst on mobile threats Alexander Goryachev.
One of the highlights of Dr.Web for Android is Origins Tracing technology. It is interesting that it did not appear simultaneously with the birth of the product, but was transferred to it later. The unique technology created solely by Doctor Web employees, Origins Tracing allows you to significantly increase the antivirus’s ability to detect various types of malware. The essence of the technology is that for each threat a description of the behavior algorithm is created, which is added to the anti-virus database. One such record can be quite enough to cover a whole family of malicious applications, due to which detection of new modifications and versions from this family can be provided without their prior analysis in the anti-virus laboratory. At the same time, the volume of the virus database is significantly reduced, since there is no need to make an entry for each specific sample, and it is this method that has been and is fundamental for many antivirus vendors. We can not reveal all the secrets, but something about the main features of Origins Tracing will tell.
First, let's remember what the basic Android application looks like: the main software package with the apk extension (for example, SuperGame.apk) is a standard zip archive containing all the application components. Inside it is the AndroidManifest.xml file, which indicates the name of the application, its version, used libraries, services, as well as the necessary functions for the operation; There is a digital signature of the application, as well as a dex-file, classes.dex - the main executable code (Dalvik Executable) compiled for functioning in the Dalvik virtual machine (Dalvik VM). It is the dex file that is of primary interest, since most malware somehow functions as a standard Android application — in the Dalvik virtual machine.
')
During antivirus scanning of applications, Origins Tracing technology builds a specific model for the dex file, which is based on decompiling into intermediate bytecode. The virus database contains information with such models. The existing special distance function is able to determine the similarities of one model with another, due to which threats are detected.
Consider the work of Origins Tracing for example:
There are two malicious applications designed to send paid SMS messages to premium numbers (typical representatives of Android.SmsSend). The screenshot shows that the main executable file is different in size (194,424 and 233,728 bytes, respectively):
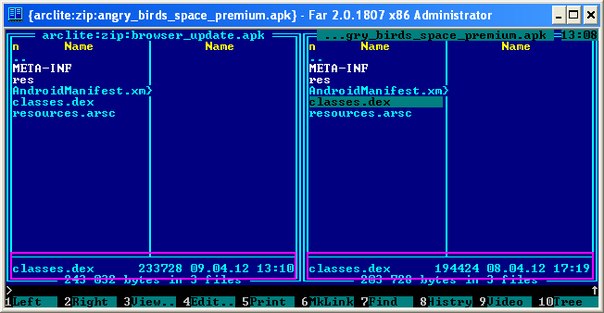
According to AndroidManifest.xml, both applications have the same name, rreh.nyur, and version 1.0. Now consider them directly on your mobile device.




The design and operation of both applications completely coincides. Now let's see how Dr.Web for Android reacts to these programs:
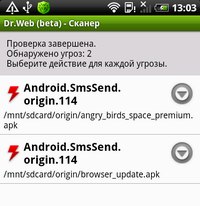
As we see, the name of the threats during detection contains the prefix .origin. This means that the Origins Tracing technology, on the basis of the criteria laid down in it, discovered the next representatives of the Android.SmsSend family of the 114th subfamily.
Differences in the size of the executable dex file (as we saw in the first screenshot) of similar malware, such as the reviewed SMS Trojans, are most often caused by attempts by virus writers to avoid detection by antiviruses using the standard signature-based detection method. For this, simple techniques can be used, such as changing the names of classes, functions, and variables in the source code of an application. After compiling such a code, a dex-file with modified content will be received, which will no longer match the existing signature in the virus database, which, in turn, may prevent detection in the traditional signature-based way.
The great advantage of the Origins Tracing technology is that it uses a non-signature method, and this often allows it to more effectively cope with the detection of updated or modified versions of malicious programs, as well as malicious programs that work on the principle already known.
Another advantage of the technology is the ability to detect not only modified, but also embedded code.
This situation is typical for Android.Gongfu, Android.DreamExploid, Android.Geinimi, Android.ADRD and other Trojans. Unlike malware such as Android.SmsSend or commercial spyware that is self-sufficient, members of these families are distributed by their intruders into legitimate applications. Origins Tracing also handles adware modules, such as Adware.Airpush, Adware.Startapp, and others, which are consciously integrated into applications by developers or unscrupulous personalities when they are modified.
All your questions on this topic today are not answered by marketers of any kind, but by Dr. Web analyst on mobile threats Alexander Goryachev.
One of the highlights of Dr.Web for Android is Origins Tracing technology. It is interesting that it did not appear simultaneously with the birth of the product, but was transferred to it later. The unique technology created solely by Doctor Web employees, Origins Tracing allows you to significantly increase the antivirus’s ability to detect various types of malware. The essence of the technology is that for each threat a description of the behavior algorithm is created, which is added to the anti-virus database. One such record can be quite enough to cover a whole family of malicious applications, due to which detection of new modifications and versions from this family can be provided without their prior analysis in the anti-virus laboratory. At the same time, the volume of the virus database is significantly reduced, since there is no need to make an entry for each specific sample, and it is this method that has been and is fundamental for many antivirus vendors. We can not reveal all the secrets, but something about the main features of Origins Tracing will tell.
First, let's remember what the basic Android application looks like: the main software package with the apk extension (for example, SuperGame.apk) is a standard zip archive containing all the application components. Inside it is the AndroidManifest.xml file, which indicates the name of the application, its version, used libraries, services, as well as the necessary functions for the operation; There is a digital signature of the application, as well as a dex-file, classes.dex - the main executable code (Dalvik Executable) compiled for functioning in the Dalvik virtual machine (Dalvik VM). It is the dex file that is of primary interest, since most malware somehow functions as a standard Android application — in the Dalvik virtual machine.
')
During antivirus scanning of applications, Origins Tracing technology builds a specific model for the dex file, which is based on decompiling into intermediate bytecode. The virus database contains information with such models. The existing special distance function is able to determine the similarities of one model with another, due to which threats are detected.
Consider the work of Origins Tracing for example:
There are two malicious applications designed to send paid SMS messages to premium numbers (typical representatives of Android.SmsSend). The screenshot shows that the main executable file is different in size (194,424 and 233,728 bytes, respectively):

According to AndroidManifest.xml, both applications have the same name, rreh.nyur, and version 1.0. Now consider them directly on your mobile device.





The design and operation of both applications completely coincides. Now let's see how Dr.Web for Android reacts to these programs:

As we see, the name of the threats during detection contains the prefix .origin. This means that the Origins Tracing technology, on the basis of the criteria laid down in it, discovered the next representatives of the Android.SmsSend family of the 114th subfamily.
Differences in the size of the executable dex file (as we saw in the first screenshot) of similar malware, such as the reviewed SMS Trojans, are most often caused by attempts by virus writers to avoid detection by antiviruses using the standard signature-based detection method. For this, simple techniques can be used, such as changing the names of classes, functions, and variables in the source code of an application. After compiling such a code, a dex-file with modified content will be received, which will no longer match the existing signature in the virus database, which, in turn, may prevent detection in the traditional signature-based way.
The great advantage of the Origins Tracing technology is that it uses a non-signature method, and this often allows it to more effectively cope with the detection of updated or modified versions of malicious programs, as well as malicious programs that work on the principle already known.
Another advantage of the technology is the ability to detect not only modified, but also embedded code.
This situation is typical for Android.Gongfu, Android.DreamExploid, Android.Geinimi, Android.ADRD and other Trojans. Unlike malware such as Android.SmsSend or commercial spyware that is self-sufficient, members of these families are distributed by their intruders into legitimate applications. Origins Tracing also handles adware modules, such as Adware.Airpush, Adware.Startapp, and others, which are consciously integrated into applications by developers or unscrupulous personalities when they are modified.
Source: https://habr.com/ru/post/144722/
All Articles