Protecting an Ajax Application Against Cross Site Request Attacks (CSRF)
Most recently, I had the task of protecting a web application completely built on ajax from CSRF attacks .
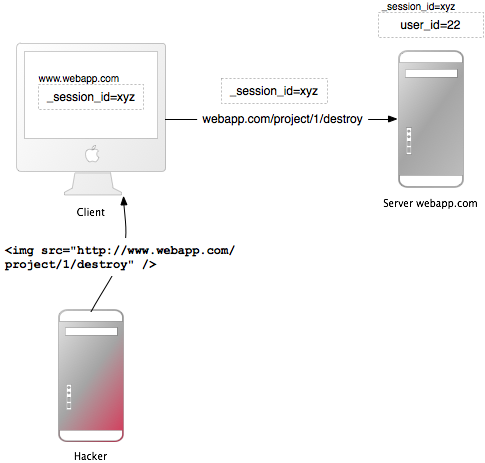
What is the mechanism of such an attack? The bottom line is to execute a request from another site under the authorization data of the user. For example, we have the action of deleting our example.com/login/dropme account. If there is no protection against a CSRF attack, we can place a tag on the site we need:
Immediately after the user enters the page we have prepared and uploads the contents of img, his account on example.com will be deleted. I will tell about protection against it under a cat.
The essence of the attack is to install a tag that loads content via url from another site. This tag can be img, script, link (for css), iframe and maybe others that did not immediately come to my head.
')
There is a simple way to protect: checking HTTP_REFERER. He did not suit me because the browser in anonymous mode may not send this header. In this case, all "anonymous" users will be subject to such an attack.
There is a more advanced method of protection: adding a token to the url and checking the token when performing an action. Than it did not suit me? There is a ready-made application in which there are already more than 100 links to various pages and actions, they are executed in code in the form of <a href="..."> </a>, and not in the form of a function call with the transfer of the url, accordingly, you will have to edit more 100 places There is a risk to forget something.
The solution was found quickly. Since everything in the application works through ajax, we can add a header with a token to the ajax request. In our case, on jQuery, this is done like this:
In addition to ajax requests, there can be openings in a new tab, and the most important is the first entry into the application. These requests do not contain a token, but we must process them. To process them, we use the following solution. If there is no token in the request, give the following html-code:
Here $ url is the url for which the request was made with the signed at the end of & csrf_token. If such code is given to the img, script, link tag - it will not be executed and the attacker will not achieve the goal. If the code is embedded in the iframe, the condition in the if will cut its execution.
Accordingly, it remains for us to learn how to handle the token from the GET parameter and give it to the client side for our header. Actually giving it is not particularly problematic. After loading the page, for example example.com/profile, we always get to the page example.com/profile?csrf_token= ...
accordingly, it remains for us to pull out the token from the get parameter using js.
All that is described above, I organized the library and posted on github . There are several flaws in that library, but I will correct them as soon as time appears. This library is already working on a real project.
What is the mechanism of such an attack? The bottom line is to execute a request from another site under the authorization data of the user. For example, we have the action of deleting our example.com/login/dropme account. If there is no protection against a CSRF attack, we can place a tag on the site we need:
<img src="http://example.com/login/dropme"> Immediately after the user enters the page we have prepared and uploads the contents of img, his account on example.com will be deleted. I will tell about protection against it under a cat.
Attack mechanism
The essence of the attack is to install a tag that loads content via url from another site. This tag can be img, script, link (for css), iframe and maybe others that did not immediately come to my head.

')
Standard methods of protection and what they did not suit me
There is a simple way to protect: checking HTTP_REFERER. He did not suit me because the browser in anonymous mode may not send this header. In this case, all "anonymous" users will be subject to such an attack.
There is a more advanced method of protection: adding a token to the url and checking the token when performing an action. Than it did not suit me? There is a ready-made application in which there are already more than 100 links to various pages and actions, they are executed in code in the form of <a href="..."> </a>, and not in the form of a function call with the transfer of the url, accordingly, you will have to edit more 100 places There is a risk to forget something.
Decision
The solution was found quickly. Since everything in the application works through ajax, we can add a header with a token to the ajax request. In our case, on jQuery, this is done like this:
$.ajaxSetup({ headers: { 'X-Csrf-Token':token } }); In addition to ajax requests, there can be openings in a new tab, and the most important is the first entry into the application. These requests do not contain a token, but we must process them. To process them, we use the following solution. If there is no token in the request, give the following html-code:
<html> <body> <?php echo $loading_text; ?> <script type='text/javascript'> <?php /** check img and other left src tags **/ ?> if (parent.document.location.href == document.location.href){ <?php /** check iframe **/ ?> document.location.href='<?php echo $url; ?>'; } </script> </body> </html> Here $ url is the url for which the request was made with the signed at the end of & csrf_token. If such code is given to the img, script, link tag - it will not be executed and the attacker will not achieve the goal. If the code is embedded in the iframe, the condition in the if will cut its execution.
Accordingly, it remains for us to learn how to handle the token from the GET parameter and give it to the client side for our header. Actually giving it is not particularly problematic. After loading the page, for example example.com/profile, we always get to the page example.com/profile?csrf_token= ...
accordingly, it remains for us to pull out the token from the get parameter using js.
Afterword
All that is described above, I organized the library and posted on github . There are several flaws in that library, but I will correct them as soon as time appears. This library is already working on a real project.
Source: https://habr.com/ru/post/144406/
All Articles