Yandeks.Afisha. Xss
All Friday I spent searching for XSS vulnerabilities in some large sites. As a result, I found XSS on several official websites of banks and on the site of Biglion.
The administration of these sites was notified of the vulnerabilities, after fixing them - I will post a post with a detailed description of errors on the sites of banks.
At the end of the day, I decided to check if there was such a hole in Yandex.
I decided to follow a simple path and look for errors in the search bar, reviewing the Nth number of Yandex services, and found that there was no query filtering in the Posters.
As a result, the insertion of js code was a success, as can be seen from the screenshots.
')
Output Cooks:
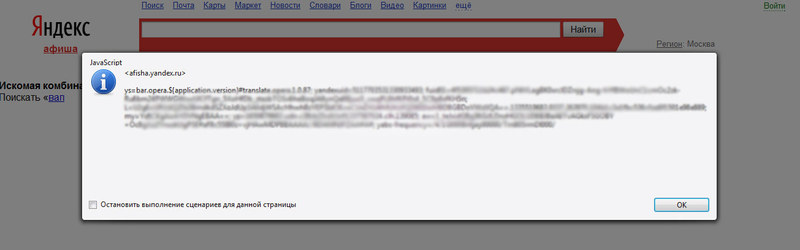
How does the XSS on the page:

On Friday evening, notified of the error of those. support ya. Posters.
This afternoon, the vulnerability was closed.
The administration of these sites was notified of the vulnerabilities, after fixing them - I will post a post with a detailed description of errors on the sites of banks.
At the end of the day, I decided to check if there was such a hole in Yandex.
XSS search.
I decided to follow a simple path and look for errors in the search bar, reviewing the Nth number of Yandex services, and found that there was no query filtering in the Posters.
As a result, the insertion of js code was a success, as can be seen from the screenshots.
')
Output Cooks:

How does the XSS on the page:

On Friday evening, notified of the error of those. support ya. Posters.
This afternoon, the vulnerability was closed.
Source: https://habr.com/ru/post/144225/
All Articles