Assembler: we hide several teams in a team
It will be about how you can hide the "extra" assembler commands in normal code. This method is useful for complicating the disassembling of the code, especially if the generation of "hidden" commands to automate.
Toolkit: OllyDbg debugger.
Strange strange code
Take a look at the following code, which hides a lot more commands than can be seen on the first view:
MOV EAX,1EBC031
MOV EBX,90DB3190
CMP EAX,EBX
JNE SHORT 0000009E
NOP
(It may be difficult to insert this fragment, the code using the assembler in OllyDbg, therefore I advise you to use the built-in HEX editor: “B8 31 C0 EB 01 BB 90 31 DB 90 39 D8 75 F3 90”)
Do you think this code will run indefinitely, since EAX and EBX are not equal, and the JNE team will make the transition to the first team area until these two registers are the same?
Let's put a break-point on the last NOP operator, run and see the result.
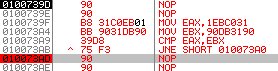
We set a break-point (the address is highlighted in red, the execution position is black), we press the start button.

After starting, the execution process stopped at the desired point.
Oddly enough, but the program is not frozen and the value of the register EAX and EBX are zero. But how could this happen?
Let's look at the code more closely. The first command places the value 1EBC031 in the EAX register, the second command places the value 90DB3190 in EBX. CMP compares two registers. JNE makes the transition if the register values do not match. And here the most interesting thing is that the transition is not done to the beginning of the first command, but to the second byte of the first command. Let's trace the code one by one.
')
We put on the first position.
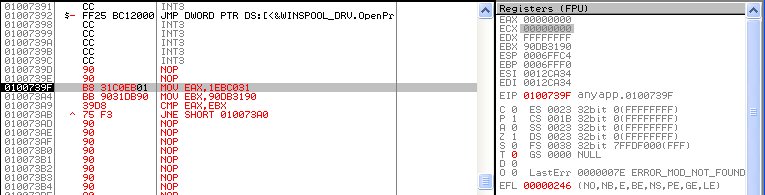
Commands are executed as usual.

... and so we reach the transition.

A short transition has been completed, and what do we see? The two hidden commands are XOR EAX, EAX clears the EAX register.

And a short transition that transfers control inside another MOV.


Another place left :)

Zero second register

We reach the check. At this time, the EAX and EBX registers are zero.

Successfully passes the test.


The fact is that the EAX register is not a prime number, but a machine instruction code. Due to such “overlays”, it is practically impossible to present the code in assembly language. Assembler commands have different sizes. The “MOV EAX, 1EBC031” command takes 5 bytes, while the XOR EAX command, 2 bytes, is a EAX command. With the help of the binary shift commands and using the half-registers AL and AH, it is possible with such "jumps" to type in the processing and input of the whole register EAX.
I want to note that when inserting machine commands, as a parameter MOV, you need to change the sequence of bytes, so for example the command 31CO (XOR EAX, EAX) placed in the command MOV will look like "MOV EAX, C031".
This method is used in many software protection systems, making it difficult to search for a transition. Also, the values entered in the registers can be used for simple encryption using the XOR method. I think you can create a program that automates the process of recompiling a piece of assembler code into such small fragments that will definitely complicate the process of reverse engineering.
In addition to 32-bit registers, 64-bit systems have 64-bit registers, these are: RAX, RBX, RCX, RDX. They can be placed in 2 times more teams.
Insert assembly code into the application
You can use the standard tools of the high-level development environment: for C ++, this code will look like this:
int someint=123; __asm { MOV EAX, someint INC EAX // ... MOV someint,EAX } for Delphi:
Var someint: Integer; somelong: Longint;
begin
asm
mov ax,i
mov ebx,somelong
// ...
end;
end.
You can also use OllyDbg by first allocating space for the code.
It should not be forgotten that the programs into which you insert a piece of assembly code use some registers themselves, so do not forget to save the values of the registers before they are changed (PUSH) and restore them upon completion (POP).
Source: https://habr.com/ru/post/144076/
All Articles