Android & iOS: Application Distribution Concepts and Security Issues
Now smartphones running Android and iOS are among the most popular among consumers around the world, although the number of devices sold and there is a significant gap. So, according to the NPD Group report, the share of Android smartphones in the US market is 61%, while the share of iOS is 29%. Despite the growing popularity of the two competing platforms, their security concerns are dramatically different. While reports of another attack by attackers on users of Android devices appear with enviable regularity, the owners of Apple i-products actually have no fears, and most of them could not even hear about the attacks that took place.

What is the reason for such a big difference? We will try to answer this question. To begin, consider the technical features of each operating system.
')
The Android OS is based on the Linux Kernel, which acts as a bridge between the hardware capabilities of the smartphone and the software functions of Android. Most of the applications for this system are created using the Java language and run in the Dalvik virtual environment, which is an interpretation of the Java Virtual Machine. In addition to the Java language, other languages can be used to write programs, but regardless of how the applications are created, they work in a special protected environment - the sandbox. Thanks to this sandbox, applications cannot access other program processes or their data.
In Android, all applications are assigned a unique User ID or UID. During operation, each program runs under its own user and in a separate process, which is an integral part of the sandbox. For the same application installed on different devices, this identifier may be different, but it is always kept by the application during the entire time it is in the system. By default, only the kernel and some key system applications have access to root (a superuser account with unlimited rights in the system).
A prerequisite for the correct operation of applications in the Android OS is that they have a digital signature. If not, the system simply will not allow the installation of the program. The digital signature is used to identify the developer, as well as to ensure the mutual security of applications. When a developer creates and tests a program, it is signed with a temporary key used for debugging. A ready application requires a personal digital signature of the developer, which is created after compiling the application and then used to sign an already finished software package. The peculiarity of Android is that the developer independently signs his application, without the intervention of anyone from outside, after which the application is immediately ready for use.
Due to the limitations imposed by the sandbox, two or more applications cannot work under the same process, since each of them must have its own unique user account. Nevertheless, developers have the opportunity to assign a single UID for several programs, but for this all applications must have the same digital signature. If this condition is met, applications can work with a single user account.
The basic Android application does not contain functions that require access to data controlled by the sandbox or protected by a sandbox. If it is necessary to use a specific functionality or data access, the developer must specify the appropriate permissions (Permissions) in the AndroidManifest.xml configuration file for the application. During the installation of such an application, the user will see a message containing information about the functions necessary for its operation. The operating system leaves the user the right to decide whether to trust the selected program. After installation, the execution of one or another function will not require the participation of the user.
Android provides the ability to remotely remove installed applications. Google may use this feature, for example, if an application is a threat.
The iOS operating system, like OS X, on which it is based, is based on the Mach kernel and BSD interfaces and is a UNIX-like system. The system core is responsible for managing memory, working with the file system, accessing hardware functions, networking, etc. The drivers play a connecting role between the hardware and system functions. Access to the kernel and drivers is limited, and only some system applications and libraries have it.
To ensure security, each installed application is placed in the sandbox - sandbox. Applications have a separate place in the file system (the directory containing the program itself and its data), access to which for other applications is restricted. In addition, the sandbox controls access to various functions of the system, the network, the hardware capabilities of the smartphone, etc. For example, restrictions affect access to SMS and mail correspondence, performing hidden dialing, sending messages. If the application provides for the exchange of certain data with other programs, developers have the opportunity to provide such access. All applications installed by users work with limited rights.
IOS apps must be signed with a digital certificate. This certificate serves as a developer identifier and ensures that the application was created by him, as well as that the developer is a registered member of the Developer Program. To obtain a certificate, the developer must send a request to Apple. In the case of a positive solution to this issue, he receives a digital security certificate, which is later used to create applications.
Like Google, Apple, if necessary, can remotely remove dangerous or violating any application rules from users' smartphones.
As we can see, both operating systems provide an acceptable level of security. Why are messages about the next threats for owners of Android-devices sound much more often than about threats for smartphones from Apple?
Consider what methods are most often found in the arsenal of intruders who pursue their own selfish goals. There are three main attack vectors:
- online fraud;
- social engineering;
- the creation of malicious and unwanted programs.
Almost always, these “tools” are found in a combined form, which allows cybercriminals to use them most effectively.
Owners of mobile devices running Android face all three problems at once, among which malware is the most acute. For smartphones from Apple, on the contrary, the problem of malware is virtually absent. To understand why this is happening, it is necessary to study in more detail the logic of the operation of both operating systems with applications, as well as the peculiarities of the process of their creation and distribution to end users.
As for the Android OS, first of all, it is worth noting the fact that the SDK - development tools - are available for Windows, Linux and Mac OS X. This ensures coverage of the widest range of developers.
Created applications can be distributed in several ways. The first one is through the main official platform - the Google Play catalog. For a small one-time fee of $ 25, anyone can register a developer account and distribute the applications created by him in this directory. Placed on Google Play programs almost immediately become available for download by users. Until recently, the applications published in this directory were not subjected to any checks, but due to the fact that attackers periodically placed malicious programs in it, Google had to introduce a special Bouncer system that should search for suspicious and unwanted applications based on existing data . However, there is no question of any strict policy of checking and testing applications before placing.
The Google Play catalog has an online version. It contains not only information about the applications available in it, but also the possibility of installing them directly from the website. To do this, the owner of the smartphone must log in under their email account, which is associated with his mobile device. With a simple click of a button, you can initiate an installation, which, if you have access to the Internet, will be immediately executed, and no requests will appear on the device itself.
The second way is free installation of applications outside the official catalog: it can be downloading from various web portals, third-party directories, via a computer or exchanging between devices. By default, this feature is disabled, but nothing prevents the user from activating it. For developers who distribute their applications, bypassing the Google Play catalog, no registration is required, and the software products created by them are immediately ready for use.

Fig.1. Diagram of possible channels for receiving applications in Android OS
Using this freedom, virus writers quickly mastered. Quite affordable cost of an account on Google Play allows them to create new accounts without special financial losses in case of their blocking. Various social engineering methods make it easy to force users to download and install Trojan programs that extend even outside the official catalog, for example, under the guise of some kind of system update or popular application (a popular tactic used to deliver Android.SmsSend SMS Trojans - one of the main and most common threats).
The Android permissions system provides the user with information about the functions that the installed program can perform, but it is far from always possible to unequivocally say exactly what the application will do with this or that function, which the attackers use. For example, the need to access the Internet, browser bookmarks, contacts, GPS coordinates, phone number, etc., can be either a completely harmless program or a Trojan that spreads under its appearance.
Do not forget that Google is positioning Android as an open source operating system. Despite the fact that some components are still inaccessible (for example, key system drivers and proprietary applications), the code available in the public domain allows you to more effectively detect various vulnerabilities that attackers use and use in their malicious programs. One of the most striking examples of such applications are Android.DreamExploid., Android.Wukong and Android.Gongfu Trojans, which exploit operating system vulnerabilities that allow elevating the privileges of the software environment to the root level. This gives them more opportunities to perform their malicious functions, for example, installing other applications without user intervention.
Since Android is available to a large number of manufacturers that produce smartphones with different technical characteristics and operating system versions, there is a wide variety of mobile devices on the market, which causes fragmentation. Despite Google’s attempts to promptly release system updates that cover detectable vulnerabilities, platform fragmentation often prevents users from receiving these updates in a timely manner, as each manufacturer has its own strategy for releasing them. It also happens that the manufacturer generally refuses to further update some models because of their obsolescence, economic or technical considerations, or for some other reason. Thus, users become defenseless against the threat of Trojans using root-exploits mentioned above.
Available Android source code can also be used by various enthusiasts who build their operating system builds. Virus writers have mastered this niche. They can distribute Trojans (such as, for example, Android.SmsHider) that are digitally signed with one of the images of such an assembly. Thanks to this method, the application receives the superuser rights that are not normally available in the system that owns the security certificate used for signing. And some attackers may even embed Trojans into such third-party firmware.
Thus, virus writers have several ways to deliver their creations to users.
Creating and distributing applications for the iOS operating system has a number of differences. Firstly, development tools are available only for Mac OS X computers. Secondly, the developer must select the appropriate distribution model for the created applications:
- iOS Developer Program Individual or iOS Developer Program Company - for individual developers and companies that create applications for the mass market;
- iOS Developer Enterprise Program - for corporate customers who need applications for internal needs;
- iOS Developer University Program - for educational institutions to improve the skills of students and familiarize them with the process of creating applications for the mobile system from Apple.
The first model is standard, designed for the general consumer market (this model will be used as the basis for consideration in the future). Applications created on the basis of it are available only through the official App Store application catalog, and before they see the light, they undergo a certain test. The process of creating an application, checking and adding to the App Store is as follows: first, the developer must go through a simple registration on the site developer.apple.com , after which the development environment will be available to him. However, in order to be able to distribute the created applications in the App Store, he needs to choose one of the appropriate distribution models (in the case of the iOS Developer Program or the iOS Developer Program Company, membership costs $ 99 per year).
In order to place the created application in the App Store catalog, the developer needs to send it to Apple for review. This requires a program already compiled and ready to use. When checking, attention is paid to compliance with many requirements, among which are the design of the application and the logic of building the interface, screening out low-content applications, as well as programs that duplicate the existing functionality and mislead the user with their similarity to standard software. Also, applications whose icon is similar to the system applications icon are not allowed. It is obligatory to check for compliance with the established safety rules. Among them are the following:
- the functionality corresponds to the stated capabilities, that is, there are no hidden and undeclared functions;
- the application can download files if it is necessary for its main work, and the user should be notified of this;
- if the required download volume via the mobile network exceeds the limit of 50 MB, the download should take place only via Wi-Fi or individual sessions;
- the application does not install or run other programs;
- the application runs in its environment and does not have access to areas of other applications, including their files;
- The application does not use undocumented functions of the system;
- the user must be notified of the collection of personal information (including location coordinates) performed by the application, and must give consent to such actions before performing them;
- the application must notify the user about the purpose of collecting personal information and possible areas of their application.
Application verification is performed automatically first and then manually. In case of successful completion of this process, the application enters the App Store, from where it becomes available to users.
In addition to installing programs directly from a smartphone, there is another standard method that is performed using iTunes installed on the computer of the device owner. Having connected the smartphone to the computer, the user can easily download the desired program from the App Store catalog.
The second model, the iOS Developer Enterprise Program, is targeted at corporate customers who need to create applications for internal needs. As in the previous case, to access it requires a paid registration, which costs already $ 299 per year. Applications subsequently created can be distributed to company employees and installed in the following ways: through a computer with iTunes, using the iPhone Configuration Utility administrative application, or through a specially created website. In addition to corporate, it is also possible to install publicly available applications hosted in the App Store catalog.
— iOS Developer University Program — , .
iOS, . jailbreak — . jailbreak, , App Store. -, — Cydia. , , .
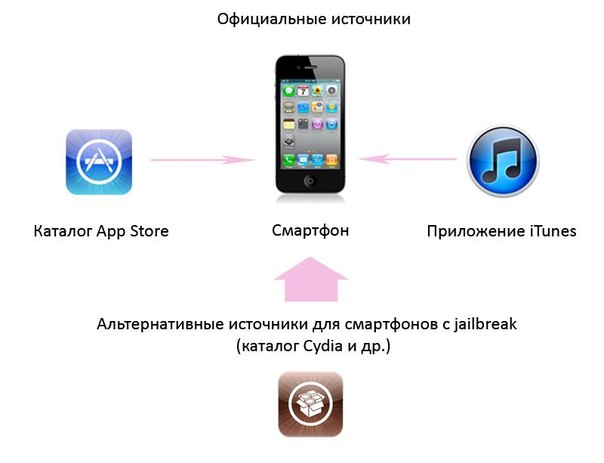
Fig. 2. iOS
, App Store, , Apple. , , , , , , .
, iOS, , , Ike. , jailbreak. SSH root- : alpine. (Rick Astley). . , , , .
Ike, iOS -. , jailbreak, , App Store. .
, iOS, , Apple, . , . , , , jailbreak. , jailbreak' , . , - , , , ( ) .
, iOS . , . , , , , , , Android. , iOS 5.1.1, , -, , . Apple.
, Android iOS , — . Apple , . , — Android — .
, Apple, -. :

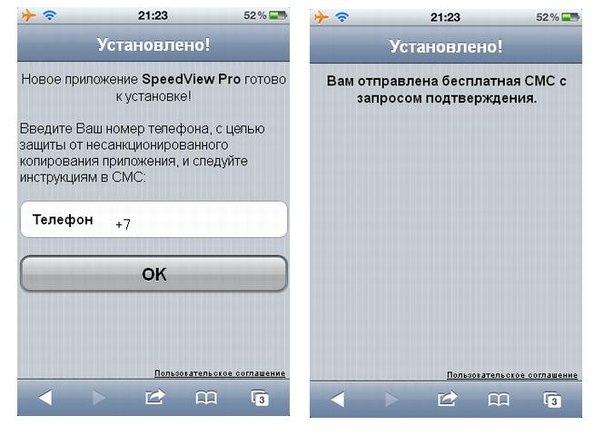
-. , , , , «», «-» , . — , , , Android, Apple .

What is the reason for such a big difference? We will try to answer this question. To begin, consider the technical features of each operating system.
')
The Android OS is based on the Linux Kernel, which acts as a bridge between the hardware capabilities of the smartphone and the software functions of Android. Most of the applications for this system are created using the Java language and run in the Dalvik virtual environment, which is an interpretation of the Java Virtual Machine. In addition to the Java language, other languages can be used to write programs, but regardless of how the applications are created, they work in a special protected environment - the sandbox. Thanks to this sandbox, applications cannot access other program processes or their data.
In Android, all applications are assigned a unique User ID or UID. During operation, each program runs under its own user and in a separate process, which is an integral part of the sandbox. For the same application installed on different devices, this identifier may be different, but it is always kept by the application during the entire time it is in the system. By default, only the kernel and some key system applications have access to root (a superuser account with unlimited rights in the system).
A prerequisite for the correct operation of applications in the Android OS is that they have a digital signature. If not, the system simply will not allow the installation of the program. The digital signature is used to identify the developer, as well as to ensure the mutual security of applications. When a developer creates and tests a program, it is signed with a temporary key used for debugging. A ready application requires a personal digital signature of the developer, which is created after compiling the application and then used to sign an already finished software package. The peculiarity of Android is that the developer independently signs his application, without the intervention of anyone from outside, after which the application is immediately ready for use.
Due to the limitations imposed by the sandbox, two or more applications cannot work under the same process, since each of them must have its own unique user account. Nevertheless, developers have the opportunity to assign a single UID for several programs, but for this all applications must have the same digital signature. If this condition is met, applications can work with a single user account.
The basic Android application does not contain functions that require access to data controlled by the sandbox or protected by a sandbox. If it is necessary to use a specific functionality or data access, the developer must specify the appropriate permissions (Permissions) in the AndroidManifest.xml configuration file for the application. During the installation of such an application, the user will see a message containing information about the functions necessary for its operation. The operating system leaves the user the right to decide whether to trust the selected program. After installation, the execution of one or another function will not require the participation of the user.
Android provides the ability to remotely remove installed applications. Google may use this feature, for example, if an application is a threat.
The iOS operating system, like OS X, on which it is based, is based on the Mach kernel and BSD interfaces and is a UNIX-like system. The system core is responsible for managing memory, working with the file system, accessing hardware functions, networking, etc. The drivers play a connecting role between the hardware and system functions. Access to the kernel and drivers is limited, and only some system applications and libraries have it.
To ensure security, each installed application is placed in the sandbox - sandbox. Applications have a separate place in the file system (the directory containing the program itself and its data), access to which for other applications is restricted. In addition, the sandbox controls access to various functions of the system, the network, the hardware capabilities of the smartphone, etc. For example, restrictions affect access to SMS and mail correspondence, performing hidden dialing, sending messages. If the application provides for the exchange of certain data with other programs, developers have the opportunity to provide such access. All applications installed by users work with limited rights.
IOS apps must be signed with a digital certificate. This certificate serves as a developer identifier and ensures that the application was created by him, as well as that the developer is a registered member of the Developer Program. To obtain a certificate, the developer must send a request to Apple. In the case of a positive solution to this issue, he receives a digital security certificate, which is later used to create applications.
Like Google, Apple, if necessary, can remotely remove dangerous or violating any application rules from users' smartphones.
As we can see, both operating systems provide an acceptable level of security. Why are messages about the next threats for owners of Android-devices sound much more often than about threats for smartphones from Apple?
Consider what methods are most often found in the arsenal of intruders who pursue their own selfish goals. There are three main attack vectors:
- online fraud;
- social engineering;
- the creation of malicious and unwanted programs.
Almost always, these “tools” are found in a combined form, which allows cybercriminals to use them most effectively.
Owners of mobile devices running Android face all three problems at once, among which malware is the most acute. For smartphones from Apple, on the contrary, the problem of malware is virtually absent. To understand why this is happening, it is necessary to study in more detail the logic of the operation of both operating systems with applications, as well as the peculiarities of the process of their creation and distribution to end users.
As for the Android OS, first of all, it is worth noting the fact that the SDK - development tools - are available for Windows, Linux and Mac OS X. This ensures coverage of the widest range of developers.
Created applications can be distributed in several ways. The first one is through the main official platform - the Google Play catalog. For a small one-time fee of $ 25, anyone can register a developer account and distribute the applications created by him in this directory. Placed on Google Play programs almost immediately become available for download by users. Until recently, the applications published in this directory were not subjected to any checks, but due to the fact that attackers periodically placed malicious programs in it, Google had to introduce a special Bouncer system that should search for suspicious and unwanted applications based on existing data . However, there is no question of any strict policy of checking and testing applications before placing.
The Google Play catalog has an online version. It contains not only information about the applications available in it, but also the possibility of installing them directly from the website. To do this, the owner of the smartphone must log in under their email account, which is associated with his mobile device. With a simple click of a button, you can initiate an installation, which, if you have access to the Internet, will be immediately executed, and no requests will appear on the device itself.
The second way is free installation of applications outside the official catalog: it can be downloading from various web portals, third-party directories, via a computer or exchanging between devices. By default, this feature is disabled, but nothing prevents the user from activating it. For developers who distribute their applications, bypassing the Google Play catalog, no registration is required, and the software products created by them are immediately ready for use.

Fig.1. Diagram of possible channels for receiving applications in Android OS
Using this freedom, virus writers quickly mastered. Quite affordable cost of an account on Google Play allows them to create new accounts without special financial losses in case of their blocking. Various social engineering methods make it easy to force users to download and install Trojan programs that extend even outside the official catalog, for example, under the guise of some kind of system update or popular application (a popular tactic used to deliver Android.SmsSend SMS Trojans - one of the main and most common threats).
The Android permissions system provides the user with information about the functions that the installed program can perform, but it is far from always possible to unequivocally say exactly what the application will do with this or that function, which the attackers use. For example, the need to access the Internet, browser bookmarks, contacts, GPS coordinates, phone number, etc., can be either a completely harmless program or a Trojan that spreads under its appearance.
Do not forget that Google is positioning Android as an open source operating system. Despite the fact that some components are still inaccessible (for example, key system drivers and proprietary applications), the code available in the public domain allows you to more effectively detect various vulnerabilities that attackers use and use in their malicious programs. One of the most striking examples of such applications are Android.DreamExploid., Android.Wukong and Android.Gongfu Trojans, which exploit operating system vulnerabilities that allow elevating the privileges of the software environment to the root level. This gives them more opportunities to perform their malicious functions, for example, installing other applications without user intervention.
Since Android is available to a large number of manufacturers that produce smartphones with different technical characteristics and operating system versions, there is a wide variety of mobile devices on the market, which causes fragmentation. Despite Google’s attempts to promptly release system updates that cover detectable vulnerabilities, platform fragmentation often prevents users from receiving these updates in a timely manner, as each manufacturer has its own strategy for releasing them. It also happens that the manufacturer generally refuses to further update some models because of their obsolescence, economic or technical considerations, or for some other reason. Thus, users become defenseless against the threat of Trojans using root-exploits mentioned above.
Available Android source code can also be used by various enthusiasts who build their operating system builds. Virus writers have mastered this niche. They can distribute Trojans (such as, for example, Android.SmsHider) that are digitally signed with one of the images of such an assembly. Thanks to this method, the application receives the superuser rights that are not normally available in the system that owns the security certificate used for signing. And some attackers may even embed Trojans into such third-party firmware.
Thus, virus writers have several ways to deliver their creations to users.
Creating and distributing applications for the iOS operating system has a number of differences. Firstly, development tools are available only for Mac OS X computers. Secondly, the developer must select the appropriate distribution model for the created applications:
- iOS Developer Program Individual or iOS Developer Program Company - for individual developers and companies that create applications for the mass market;
- iOS Developer Enterprise Program - for corporate customers who need applications for internal needs;
- iOS Developer University Program - for educational institutions to improve the skills of students and familiarize them with the process of creating applications for the mobile system from Apple.
The first model is standard, designed for the general consumer market (this model will be used as the basis for consideration in the future). Applications created on the basis of it are available only through the official App Store application catalog, and before they see the light, they undergo a certain test. The process of creating an application, checking and adding to the App Store is as follows: first, the developer must go through a simple registration on the site developer.apple.com , after which the development environment will be available to him. However, in order to be able to distribute the created applications in the App Store, he needs to choose one of the appropriate distribution models (in the case of the iOS Developer Program or the iOS Developer Program Company, membership costs $ 99 per year).
In order to place the created application in the App Store catalog, the developer needs to send it to Apple for review. This requires a program already compiled and ready to use. When checking, attention is paid to compliance with many requirements, among which are the design of the application and the logic of building the interface, screening out low-content applications, as well as programs that duplicate the existing functionality and mislead the user with their similarity to standard software. Also, applications whose icon is similar to the system applications icon are not allowed. It is obligatory to check for compliance with the established safety rules. Among them are the following:
- the functionality corresponds to the stated capabilities, that is, there are no hidden and undeclared functions;
- the application can download files if it is necessary for its main work, and the user should be notified of this;
- if the required download volume via the mobile network exceeds the limit of 50 MB, the download should take place only via Wi-Fi or individual sessions;
- the application does not install or run other programs;
- the application runs in its environment and does not have access to areas of other applications, including their files;
- The application does not use undocumented functions of the system;
- the user must be notified of the collection of personal information (including location coordinates) performed by the application, and must give consent to such actions before performing them;
- the application must notify the user about the purpose of collecting personal information and possible areas of their application.
Application verification is performed automatically first and then manually. In case of successful completion of this process, the application enters the App Store, from where it becomes available to users.
In addition to installing programs directly from a smartphone, there is another standard method that is performed using iTunes installed on the computer of the device owner. Having connected the smartphone to the computer, the user can easily download the desired program from the App Store catalog.
The second model, the iOS Developer Enterprise Program, is targeted at corporate customers who need to create applications for internal needs. As in the previous case, to access it requires a paid registration, which costs already $ 299 per year. Applications subsequently created can be distributed to company employees and installed in the following ways: through a computer with iTunes, using the iPhone Configuration Utility administrative application, or through a specially created website. In addition to corporate, it is also possible to install publicly available applications hosted in the App Store catalog.
— iOS Developer University Program — , .
iOS, . jailbreak — . jailbreak, , App Store. -, — Cydia. , , .

Fig. 2. iOS
, App Store, , Apple. , , , , , , .
, iOS, , , Ike. , jailbreak. SSH root- : alpine. (Rick Astley). . , , , .
Ike, iOS -. , jailbreak, , App Store. .
, iOS, , Apple, . , . , , , jailbreak. , jailbreak' , . , - , , , ( ) .
, iOS . , . , , , , , , Android. , iOS 5.1.1, , -, , . Apple.
, Android iOS , — . Apple , . , — Android — .
, Apple, -. :


-. , , , , «», «-» , . — , , , Android, Apple .
Source: https://habr.com/ru/post/143971/
All Articles