Audit of Active Directory Domain Services in Windows Server 2008 R2

Audit of Active Directory Domain Services in Windows Server 2008 R2
IT environment is not static. Every minute thousands of changes occur in the systems that need to be tracked and recorded. The larger the size and complexity of the structure, the higher the likelihood of errors in administration and disclosure of data. Without constant analysis of changes (successful or unsuccessful), it is impossible to build a truly safe environment. The administrator must always answer who, when and what changed, who was delegated rights, what happened in case of changes (successful or unsuccessful), what the values of old and new parameters are, who could or could not log in or access the resource, who deleted data and so on. Auditing changes has become an integral part of managing the IT infrastructure, but organizations do not always pay attention to auditing, often due to technical problems. After all, it is not entirely clear what and how to monitor, and the documentation in this matter does not always help. The number of events that need to be monitored is in itself complex, data volumes are large, and standard tools do not differ in convenience and ability to simplify the task of tracking. The specialist must independently set up the audit, setting the optimal audit parameters, in addition, he is responsible for analyzing the results and building reports on the selected events. Considering that several services are running on the network — Active Directory / GPO, Exchange Server, MS SQL Server, virtual machines, and so on, which generate a very large number of events, it is very difficult to select from those that are really necessary, following only the descriptions.
As a result, administrators consider backup events sufficient, preferring to roll back to the old settings in case of problems. The decision to introduce an audit is often made only after serious incidents. Next, consider the process of configuring Active Directory auditing on the example of Windows Server 2008 R2.
Audit Active Directory by regular means
')
In Windows Server 2008, compared to the previous Windows Server 2003, the capabilities of the audit subsystem are updated that are configured through security policies, and the number of monitored parameters is increased by 53. In Windows Server 2003, there was only the Audit directory service access policy that controlled enabling and disabling directory event auditing . Now you can manage auditing at the category level. For example, Active Directory audit policies are divided into 4 categories, in each of which specific parameters are configured:
- Directory Service Access (access to the directory service);
- Directory Service Changes (directory service changes);
- Directory Service Replication (directory service replication);
- Detailed Directory Service Replication (detailed replication of the directory service).
When you enable the global audit policy Audit directory service access, all subcategories of the directory service policy are automatically activated.
The audit system in Windows Server 2008 tracks all attempts to create, modify, move, and restore objects. The previous and current values of the changed attribute and the user account of the user who performed the operation are logged. But if the default parameters were used when creating objects for attributes, their values are not logged.
NOTE: In Windows Server 2003, the audit registered only the name of the attribute that was changed.
In Windows Server 2008 R2, auditing is implemented using:
- Global Audit Policy (GAP);
- access control list (System access control list, SACL) - defines the operations for which the audit will be performed;
- Schemes - used for the final formation of the list of events.
By default, audit is disabled for client systems, Active Directory subcategory is active for server systems, the rest are disabled. To enable the global policy “Audit directory service access”, you need to call the Group Policy Management Editor switch to the Security Settings / Local Policies / Audit Policy branch, where you activate the policy and set controlled events (success, failure).
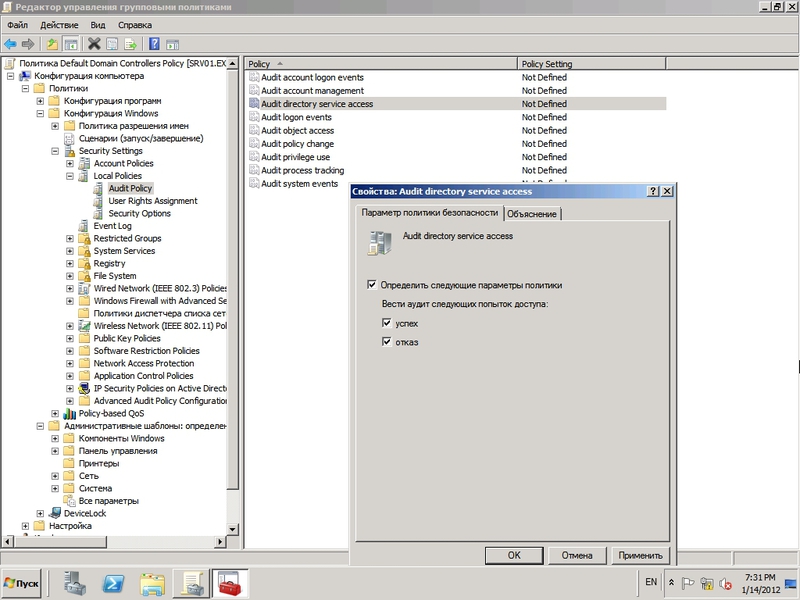
Figure 1 Enable Directory Service Access audit policy
The second way is to use the auditpol command line utility for configuration, get a complete list of GAP with the parameters set. With auditpol, just enter the command:
> auditpol /list /subcategory:*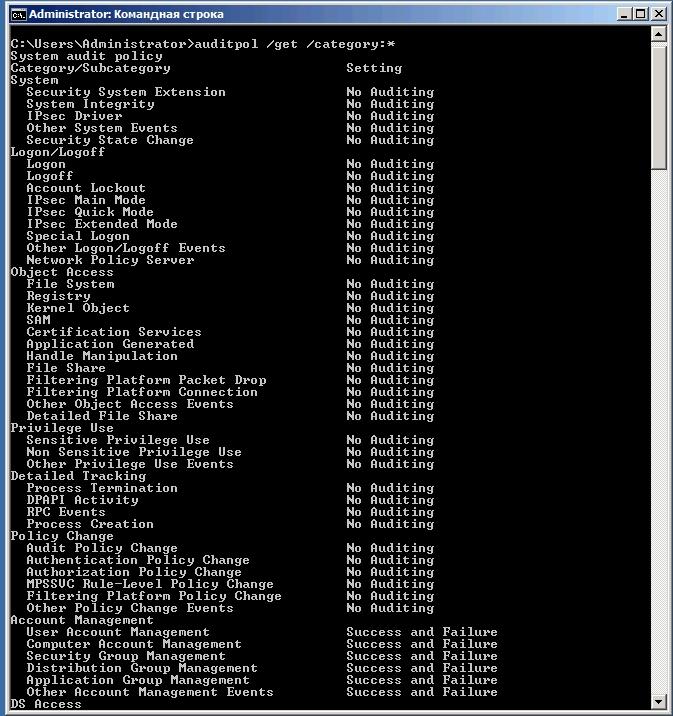
Fig.2 Get the list of settings with auditpol
Activate the policy “directory service access” :
> auditpol /set /subcategory:"directory service changes" /success:enableNOTE: Detailed information about the command can be obtained by running it in the form
auditpol / h
Not to wait, we will update the domain controller policy:
> gpupdateAudit policy subcategory Directory service access generates events in the security log with code 4662 , which can be viewed using the Event Viewer in the Windows Logs - Security tab.
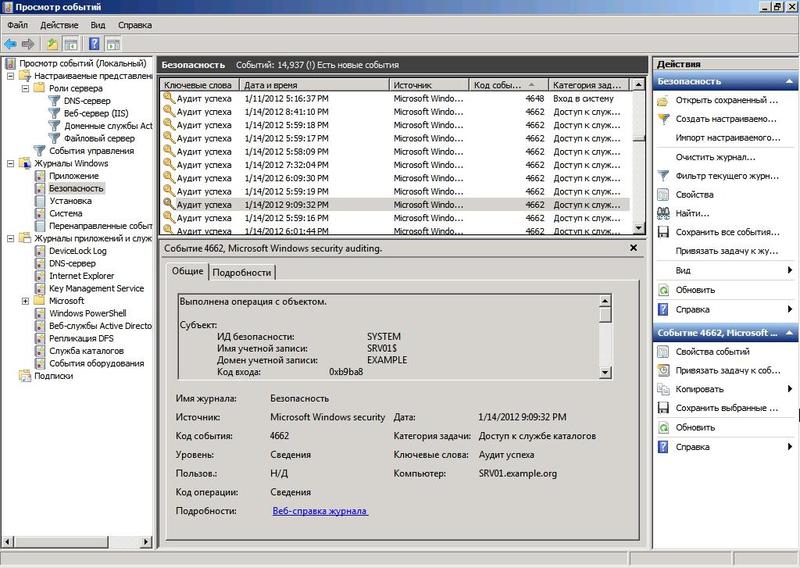
Fig.3 Viewing events using the Event Viewer
As an alternative to viewing events, you can use the Get-EventLog cmdlet in PowerShell. For example:
PS> Get-EventLog security | ?{$_.eventid -eq 4662}NOTE: The Get-EventLog cmdlet can take 14 parameters that allow you to filter events based on certain criteria: After, AsBaseObject, AsString, Before, ComputerName, EntryType, Index, InstanceID, List, LogName, Message, Newest, Source and UserName.
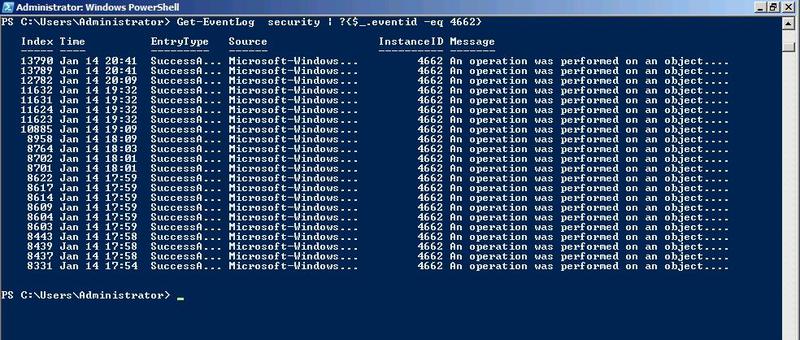
Fig.4 Get the event list using Get-EventLog
In addition, a number of other events 5136 (attribute change), 5137 (attribute creation), 5138 (undo attribute deletion) and 5139 (attribute movement) are registered.
For the convenience of selecting certain events in the Event Viewer console, filters and custom views are used, as well as a subscription that allows you to collect log data from other servers.
Table 1. List of Active Directory event audit events in Windows Server 2008
Verification of credentials
IDENTIFIER Message
4774 The account was mapped to log on.
4775 Failed to match the login account.
4776 An attempt was made to verify credentials for a domain controller account.
4777 Unable to verify credentials for domain controller account.
Computer account management
IDENTIFIER Message
4741 A computer account has been created.
4742 Computer account changed.
4743 Computer account removed.
Managing Distribution Groups
IDENTIFIER Message
4744 A local group was created with security checks disabled.
4745 Changed local group with disabled security check.
4746 A user has been added to a local group with security checking disabled.
4747 Removed a user from a local group with security checking disabled.
4748 A local group has been removed with security checks disabled.
4749 A global group has been created with security checking disabled.
4750 A global group has been modified with security checks disabled.
4751 User added to global group with security check disabled.
4752 A user was removed from the global group with security checking disabled.
4753 A global group has been removed with security checks disabled.
4759 A universal group was created with the security check disabled.
4760 Changed the universal group with disabled security checks.
4761 A member has been added to the universal group with the security check disabled.
4762 A user was deleted from the universal group with the security check disabled.
Other Account Management Events
IDENTIFIER Message
4739 Changed domain policy.
4782 Password hash account access to it.
4793 The API called password policy checker was called.
Security team management
IDENTIFIER Message
4727 A global security group has been created.
4728 User added to security-enabled global group.
4729 Removed user from global group with security enabled.
4730 Global security enabled group removed.
4731 A local security group was created.
4732 A user has been added to a local group with security enabled.
4733 Removed a user from a local security-enabled group.
4734 Local security group removed.
4735 Local security group changed.
4737 Global security enabled group changed.
4754 A universal group has been created with security enabled.
4755 Changed the universal group with security enabled.
4756 Added user to universal group with security enabled.
4757 Removed a user from the universal group with security enabled.
4758 Removed universal group with security enabled.
4764 Group type changed.
User Account Management
IDENTIFIER Message
4720 User account created.
4722 User account is enabled.
4723 Account password changed.
4724 Reset user password.
4725 User account is disabled.
4726 User account deleted.
4738 Changed user account.
4740 User account is locked.
4765 SID log has been added to the account.
4766 Failed to add account SID log.
4767 User account has been unlocked.
4780 The Access Control List has been set up for accounts that are members of the Administrators group.
4781 The account name has been changed.
4794 An attempt was made to set the directory services recovery mode.
5376 Credential Manager: Credentials have been saved.
5377 Credential Manager: Credentials have been restored from backup.
Other events
IDENTIFIER Message
1102 Cleared security log
4624 Successful Login
4625 Not a successful login
Other features are also activated in the Audit Policy branch (see Figure 1): login / exit audit, account management audit, object access, policy changes, and so on. For example, set up an object access audit using the example of a shared folder. To do this, activate, as described above, the Audit object access policy, then select the folder and call the Folder Properties menu, in which we go to the Security sub-item and click the Advanced button. Now in the “Advanced Security Settings for ..” window that opens, go to the Audit tab and click the Edit button and then Add and specify the account or group for which the audit will be performed. Next, we mark the tracked events (execution, reading, creating files, etc.) and the result (success or failure). Using the “ Apply ” list, specify the scope of the audit policy. We confirm the changes.
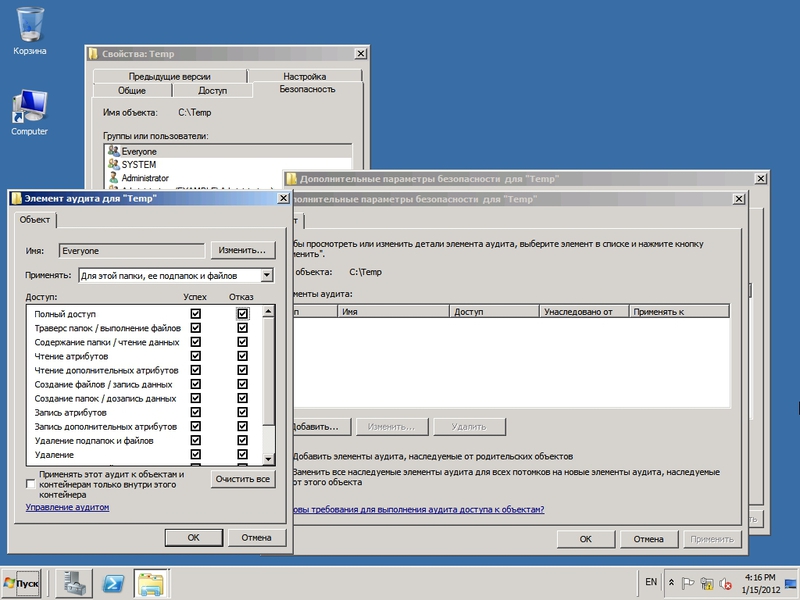
Fig.5 Configure auditing of shared folders
Now all specified operations will be displayed in the security log.
To simplify the configuration of auditing with a large number of objects, you should activate the Inheritance of parameters from the parent object checkbox. In this case, the parent object, from which the settings are taken, will be displayed in the Inherited from field.
Greater control over the events recorded in the log is achieved by applying the Granular Audit Policy, which is configured in Security Settings / Local Policies / Advanced Audit Policy Configuration . Here are 10 sub-clauses:
- Account login - audit credentials verification, Kerberos authentication services, Kerberos service ticket operations, other login events;
- Account Management - audit management of application groups, computer and user accounts, security and distribution groups;
- Detailed tracking - RPC and DPAPI events, creating and terminating processes;
- Access to the DS directory service - audit of access, changes, replication and detailed replication of the directory service;
- Login / Logout - audit account blocking, login and logout, use IPSec, network policy server;
- Access to objects - audit of kernel objects, work with descriptors, events created by applications, certification services, file system, shared folders, filtering platform;
- Policy change - changes in audit policy, authentication, authorization, filtering platform, rules of the MPSSVC security service and others;
- Use of rights - audit of access rights to various categories of data;
- System - audit of the system integrity, changes and extensions of the security state, IPSec driver and other events;
- Audit of access to global objects - audit of the file system and registry.
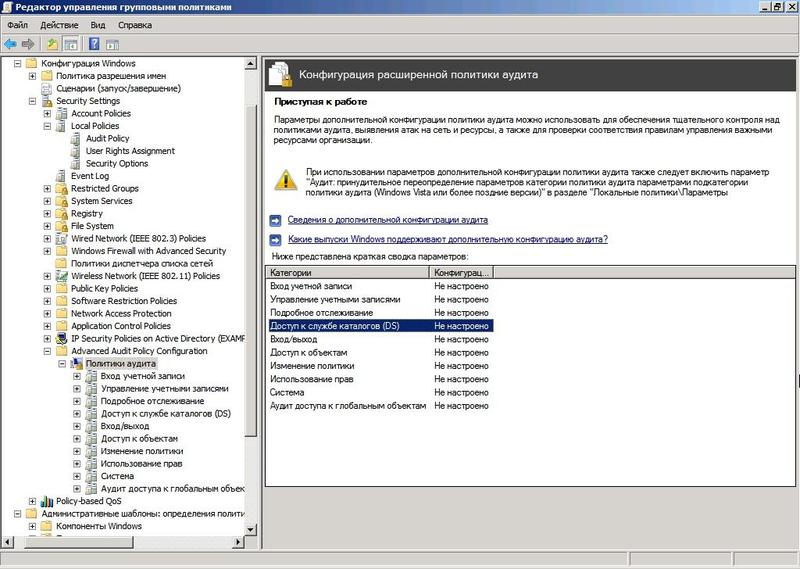
Fig.6 Available settings Advanced Audit Policy Configuration
Activating user account management audits will allow you to track: create, modify, delete, block, enable, and other account settings, including a password and permissions. Let's see how it works in practice - select the User Account Management subcategory and activate it. The command for auditpol looks like this:
> auditpol /set /subcategory:"User Account Management" /success:enable /failure:enable
> gpudateThe audit system in the Event Viewer Console will immediately show event number 4719. The change in audit parameters shows the name of the policy and the new values.
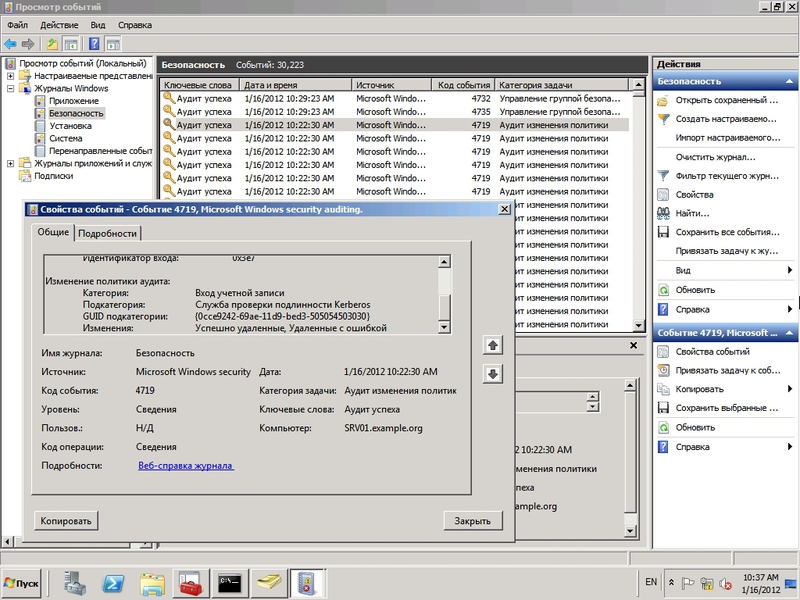
Fig.7 Fixing policy changes by the audit system
To create an event, open the Active Directory console for users and computers and change one of the parameters of any account — for example, add a user to the security group. In the Event Viewer console, several events will be generated immediately: events numbered 4732 and 4735 , showing a change in the composition of the security group, and the addition of a new security group account (in Figure 8 are highlighted in purple).
Create a new account - the system generates several events: 4720 (creating a new account), 4724 (trying to reset the account password), several events with code 4738 (changing the account) and, finally, 4722 (switching on the new account). According to the audit, the administrator can track the old and new attribute values - for example, when creating an account, the UAC value changes.
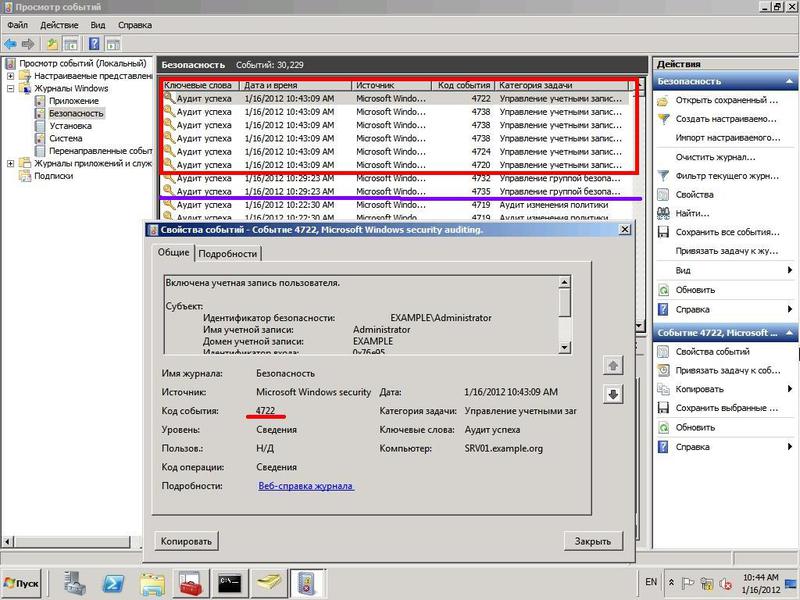
Fig.8 When creating a new account audit system, Windows Server 2008 generates several events
Disadvantages of a regular audit system
Standard operating system tools often offer only basic sets of analysis tools. The official documentation (http://technet.microsoft.com/ru-ru/library/dd772623(WS.10).aspx) very similarly describes the capabilities of the tool itself, with little help in choosing the parameters whose changes need to be monitored. As a result, the solution of this task lies entirely on the shoulders of the system administrator, who must fully understand the technical aspects of the audit, and depends on its level of preparation, which means that there is a high probability of error. In addition, on his shoulders lies the analysis of the result, the construction of a variety of reports.
For the convenience of selecting certain events, the interface of the Event Viewer console allows you to create filters and custom views. As parameters for the selection of data, you can specify: date, log and source of events, level (critical, warning, error, etc.), code, user or computer and keywords. An organization may have a large number of users grouped into subdivisions for which an audit must be set up individually, but this feature is not provided in the interface.
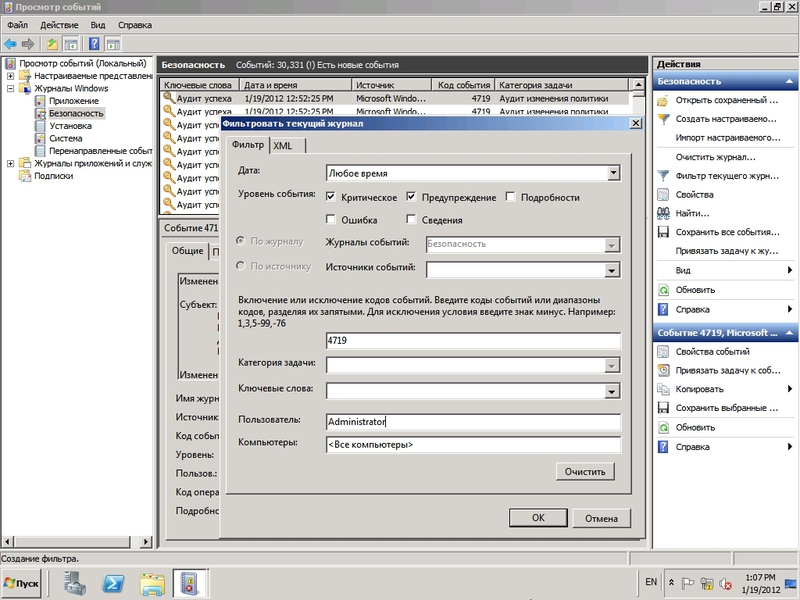
Fig. 9 Configuring an Event Filter in the Event Viewer Console
If the rules are triggered in the custom view, you can create a task (menu Bind a task to an event ): start the program, send an email or display a message on the desktop.
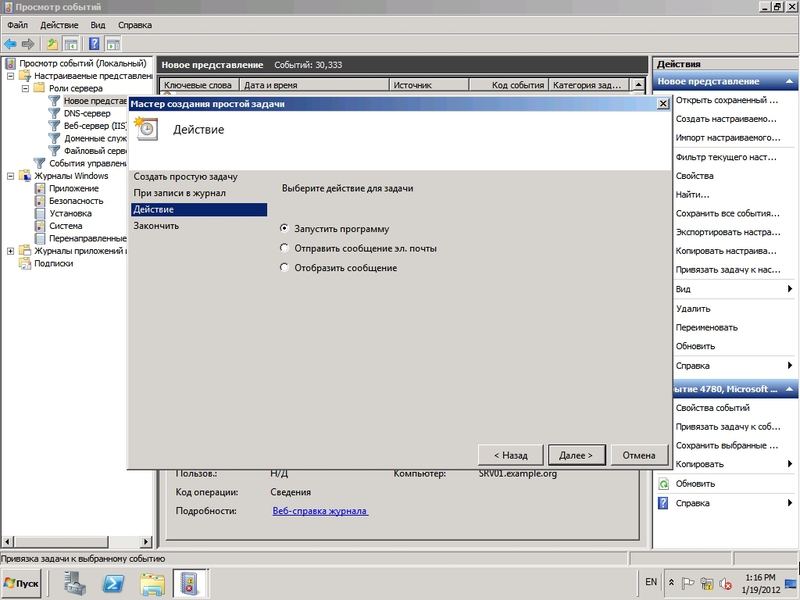
Fig.10 Creating a task in the Event Viewer console
But, again, the implementation of alerts, in particular the choice of events, lies entirely with the administrator.
If it is necessary to roll back the changed attribute to the previous value, this action is performed manually - the console only shows the value of the parameters.
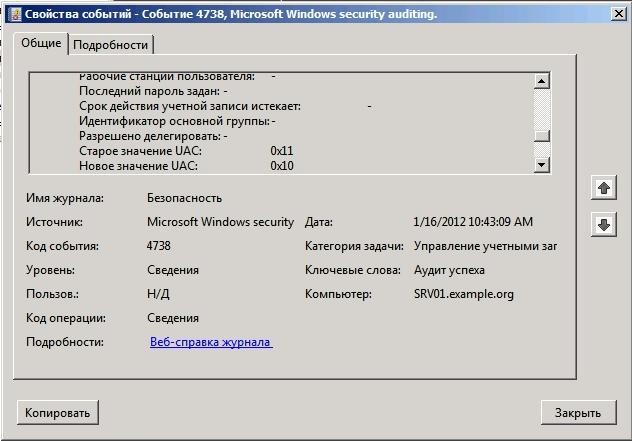
Pic.11 The audit system of Windows Server 2008 only returns the old and new attribute values without providing the means for convenient rollback.
Some security standards require the storage of data collected during an audit for a long time (for example, SOX up to 7 years). System tools can do this, but it is very difficult. The size of the security log (as well as others) is limited to 128 MB, and with a large number of events, the data can be overwritten (i.e., lost) after a few hours. To avoid this, you need to call the properties window of the log in the Event Viewer, where you can increase the size of the log and activate its archiving by checking the box “ Archive the log when filled. Do not overwrite events . ”
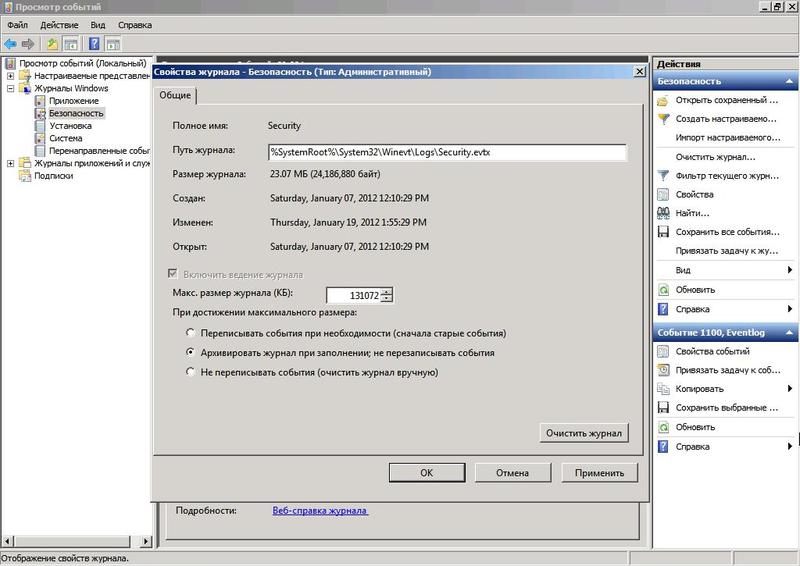
Fig.12 In order not to lose the old security events, you should increase the size of the log and enable archiving
But now it will be necessary to solve the problem of finding events in a variety of archives.
It is also worth noting that the shortcomings of the standard audit system include limited monitoring of group policies. While the fact of this change can be monitored by standard means, the values of the changed parameters are not recorded and, thus, it is impossible to answer the question of what exactly was changed and what the new value became. In some situations it is enough, but it is difficult to call it a full-fledged audit.
***
This article is part of the Complete Guide to Auditing Active Directory in Windows Server 2008 R2 [PDF]. You can download it from this link by filling out a small form.
Source: https://habr.com/ru/post/143878/
All Articles