We read passport data of students, schoolchildren and pensioners from their pocket.

Thanks to the government of Moscow and personally to comrade Gaev
Introduction
As you know, all students, pensioners and schoolchildren in Moscow are issued a Muscovite social card (SCM), which simultaneously serves as a bank card and a travel card for various types of transport.
Technically, the card is a Mifare Classic RFID card in one of two versions, 1K or 4K.
The Mifare Classic map is divided into sectors (16 and 40 respectively), access to each of which is provided by key (6 bytes). The Mifare Classic card implements proprietary encryption and restricts access to sectors independently.
')
In SCM, sectors are divided between different organizations.
Some sectors (13-14) are open, they are accessed according to the standard key A0 ... A5 defined in the card description .
According to the developers of the system, this standard key can only be known as “an organization registered by the MCP State Unitary Enterprise as an acceptor of a social card,” which, to put it mildly, is not true.
However, the open sectors of the card do not contain anything serious: they contain only the name of the cardholder, gender and date of birth and social card number, which naturally has nothing to do with the number of the banking component of the card.
The remaining sectors of the map, for example, containing travel cards, are closed and can be accessed only by knowing the corresponding keys.
Keys
Starting from 2008, when the proprietary encryption algorithm was restored, you can access the data on the card without keys. There are at least three types of key attacks:
- with the interception of information transmitted over the air between the card and the reader, "knowing" the keys
- using vulnerability of software RNG and encryption algorithm using only the card
- accelerated modification of the previous method, using only the map and knowledge of the key to at least one sector
Because Since SCM has open sectors, the simplest is to use a third attack.
Key recovery
This type of attack is carried out, for example, by the MFOC utility. To launch an attack, you will need a reader supported by libnfc, for example SCM SCL3711 . More available in Russia readers ACR122T or ACR122U on the same chip.
Recovering keys to all private sectors takes about 5 minutes. The result of the work will be a complete memory dump of the card, including keys to all sectors. With this dump, you can then freely read and write dumps.
We look inside
Inside is nothing interesting. Of all the closed sectors information is contained only in the sectors of the metro, electric trains and buses. You can view this information, but you cannot change it, much less copy it to other cards in accordance with Art. 327 of the Criminal Code.
The most interesting
It turned out that, starting from recent times, probably from last year, SCM are based on Mifare Classic 4K, and not on 1K, as it was before. Having restored the keys to such a card and looking at the contents of the new closed sectors (17-40), in the 17th sector you may stumble upon the following:
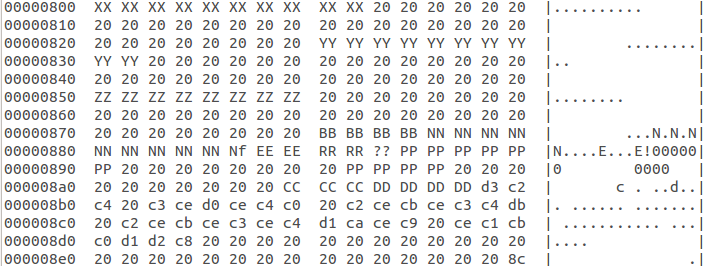
Here
- XX, YY, ZZ - surname, name and patronymic in CP-1251
- BB is the date of birth in the format YYYYMMDD, written in numbers in hex, i.e. 2012-05-13 will be encoded as 0x20 0x12 0x05 0x13
- NN - social card number, the format is the same.
- EE - end date (month, two digits of the year), RR - region of issue (0177).
- ?? - unknown, 0x21 (document type?)
- PP - Passport Number and Series, ASCII
- SS - unit code, digits in hex
- DD - issue date, YYYYMMDD, digits in hex
- further - issued by whom, CP1251 in large letters, left in the dump
- byte at the end - 0x8C - is unknown.
In the dump, personal data is smeared.
Those. in this undocumented sector, the full passport details of the person are recorded! It should be noted that this information appeared on SCM after 2008, i.e. when Mifare Classic encryption was already compromised, and on one-time metro tickets and in the trains, strong encryption methods were already used.
Why is this dangerous?
Anyone who has $ 30 to buy a reader can restore the keys to SCM. Let me remind you that these keys are the same for all social cards. Knowing these keys, an attacker can read data from SCM, lying in your pocket from a distance of several meters, using an external antenna. The obtained passport data could be used further for criminal purposes, if not for the FZ-152.
How to live?
There are two ways to prevent this. First, it is possible, by restoring the keys, to overwrite this sector, filling it with garbage or passport data of a neighbor.
Secondly, you can use the old, proven method: wrap the card with foil and get it if necessary. You can turn around at the same time foil yourself.
Source: https://habr.com/ru/post/143807/
All Articles