Enigma - encrypting messages to war
 Many have heard that during the Great Patriotic War, the German side used a special encryption machine, Enigma, for encryption.
Many have heard that during the Great Patriotic War, the German side used a special encryption machine, Enigma, for encryption.According to sources, this device was a new word in the cryptography of that time.
How did she work?
Replacement cipher
For starters, you should know what the "replacement code" is. This is the usual replacement of one letter for another. Those. in such a cipher, instead of the letter “A”, for example, “T” is used, instead of “B” - “S”, etc.
')
Hacking such a cipher is quite simple. If there is a more or less long encrypted message, you can make a frequency analysis and compare it with the frequency of letters in the language. Those. if there are many letters “T” in the ciphering cipher message, then this is a clear sign that there is some vowel behind this letter (for example, “A” or “O” because usually these letters are the most common in the language) .
Enigma device
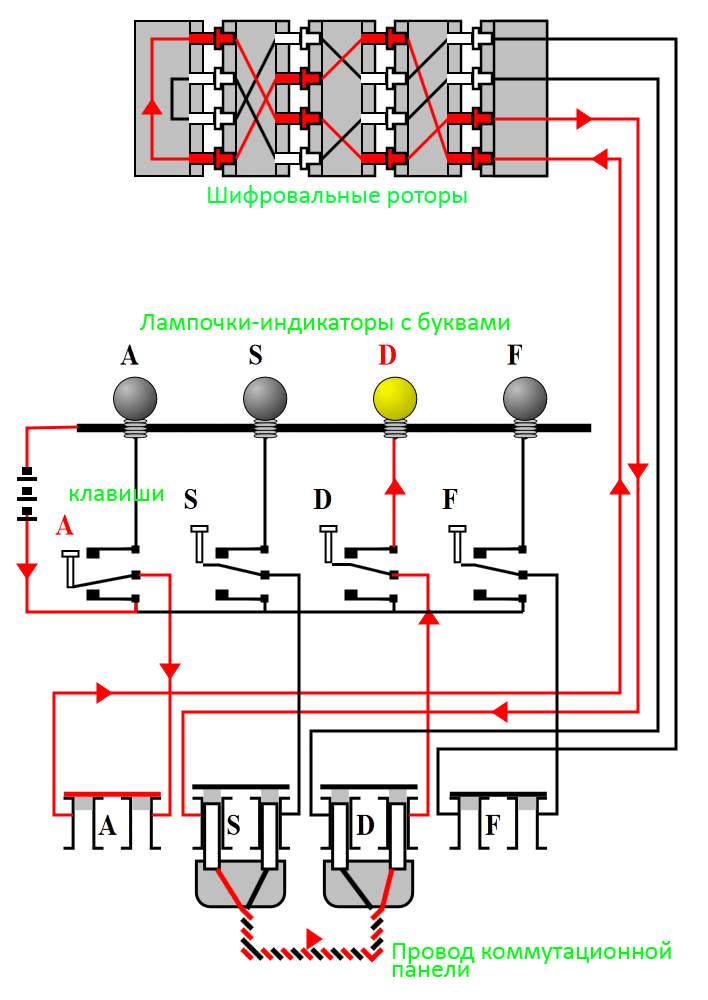
Enigma was a kind of Caesar dynamic cipher. Those. Initially, a certain initial value was set on the drum (a sort of random seed), which was the key. Further, when typing letters, each letter was encrypted with Caesar's cipher, and then, this cipher was changed to another.
The cipher change was provided with the help of rotors.

The rotors were disks, which had 26 contacts on each side, connected inside the rotor in a certain (random) way. Passing through the rotor, the signal was transformed from the letter “A” to the letter “T”, etc.
There were several rotors and they turned after dialing each character (in the manner of a drum counter).
In addition, there was also a switching panel, in which it was possible to insert wires that changed letters in pairs. Those. sticking the wire at one end into the socket "A", and the other - in the "E", you changed these letters in some places.

The principle of operation can be understood by looking at the schematic diagram:
The number of rotors varied in different years and for different purposes (for example, Enigmas with a large number of rotors were used in the fleet).
To complicate hacking, operators coded frequently used words (names) each time in different ways. For example, the word "Minensuchboot" could be written as "MINENSUCHBOOT", "MINBOOT", "MMMBOOT" or "MMM354"
Accessories.
As with any popular device, there were a large number of accessories to the Enigme (yes, it started already then).
For example, there were auto-printing devices (in the normal version, the coding was performed by lighting lamps, the values of which the operator had to record).
In addition, there were remote printers (on the wires, of course). So that the operator who drives the encrypted message into the machine does not have access to the decrypted one.
Related Links:
Source: https://habr.com/ru/post/143526/
All Articles