Fight WordPress worm GetMama
Hello!
The vile GetMama virus devoured a bunch of WordPress sites. Including some mine. And I will tell you how to clean this essence in the form of a gnome.
It began with the fact that some sites began to open for a very long time. And only those on WordPress.
I could not understand for a long time what kind of trouble happened. I updated all the software on the server completely (I thought that you can use wp to use some cunning shit). But it did not help.
Then I began to look for, what function is performed like that, bitch, for a long time.
For this, I used xhprof .
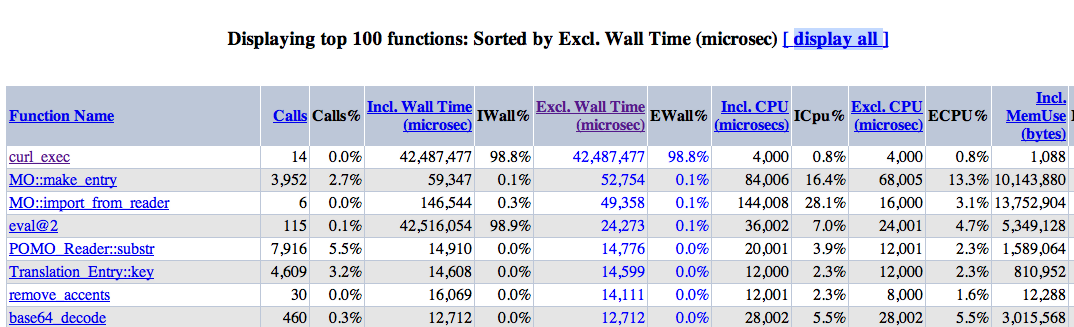
It turned out that it is curl_exec.
')
Kurl_ekzek called by a function with some Arabic name "ahfudflfzdhfhs"
And this function, in turn, caused a certain amount of failure, including GetMama
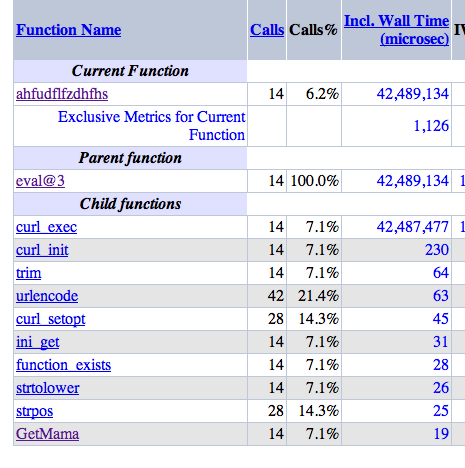
The name of this function is called a virus.
Getm mother knocks on her server and downloads the code from there, which is already executed in the site code.
In order to temporarily save the situation, I simply added “function GetMama () {}” to the beginning of each index.php of my WordPress sites. It gave me time to look for a real threat.
No search returned results. Neither “GetMama”, nor “ahfudflfzdhfhs” was found in the code. This is certainly not surprising. But surprisingly, base64_decode also did not come across in the wrong places.
I had to google. According to his comrades in trouble, getmama began with the words “/ * god_mode_on * /”, but I could not find this entry in any of the files.
I puzzled for a long time, looking at the files, and could not understand where the infected site was.
It turned out that everywhere. In fact, every php WordPress file was infected, but I could not see it.
When I realized how they did it, I felt a little ashamed.
At the beginning. After “<? Php” the guys added a bunch of gaps, and only then signed the malicious code.
Here it is: http://pastebin.com/vER6azvS
Now this garbage also / * god_mode_on * / encrypted.
But in the end, the problem was solved in one small script:
Go through all the php files in the directory with WordPress and remove the virus.
If you do not have ssh access to your hosting, download the files to yourself and delete the code locally. If you have Windows, then think up how to perform a regular expression replacement on a bunch of files.
The vile GetMama virus devoured a bunch of WordPress sites. Including some mine. And I will tell you how to clean this essence in the form of a gnome.
It began with the fact that some sites began to open for a very long time. And only those on WordPress.
I could not understand for a long time what kind of trouble happened. I updated all the software on the server completely (I thought that you can use wp to use some cunning shit). But it did not help.
Then I began to look for, what function is performed like that, bitch, for a long time.
For this, I used xhprof .
It turned out that it is curl_exec.

')
Kurl_ekzek called by a function with some Arabic name "ahfudflfzdhfhs"

And this function, in turn, caused a certain amount of failure, including GetMama

The name of this function is called a virus.
Getm mother knocks on her server and downloads the code from there, which is already executed in the site code.
In order to temporarily save the situation, I simply added “function GetMama () {}” to the beginning of each index.php of my WordPress sites. It gave me time to look for a real threat.
No search returned results. Neither “GetMama”, nor “ahfudflfzdhfhs” was found in the code. This is certainly not surprising. But surprisingly, base64_decode also did not come across in the wrong places.
I had to google. According to his comrades in trouble, getmama began with the words “/ * god_mode_on * /”, but I could not find this entry in any of the files.
I puzzled for a long time, looking at the files, and could not understand where the infected site was.
It turned out that everywhere. In fact, every php WordPress file was infected, but I could not see it.
When I realized how they did it, I felt a little ashamed.
At the beginning. After “<? Php” the guys added a bunch of gaps, and only then signed the malicious code.
Here it is: http://pastebin.com/vER6azvS
Now this garbage also / * god_mode_on * / encrypted.
But in the end, the problem was solved in one small script:
find . -type f -name "*.php" -print | xargs perl -pi -e's/\/\*[a-z0-9]{32}_on\*\/.*\/\*[a-z0-9]{32}_off\*\///gi' *.phpGo through all the php files in the directory with WordPress and remove the virus.
If you do not have ssh access to your hosting, download the files to yourself and delete the code locally. If you have Windows, then think up how to perform a regular expression replacement on a bunch of files.
Source: https://habr.com/ru/post/143375/
All Articles