A tweet about a XSS bug on Google+ led to XSS on the InformationWeek website
Independent Internet security researcher Niels Dühnemann specializes in finding vulnerabilities in Google services and is rewarded by the Vulnerability Reward Program . Recently, he found a lot of vulnerabilities in all major Google products and earned good money. On April 27, Nils posted a post on his blog describing the latest discovery - the XSS vulnerability on Google+, a reward for which he donated to build a school in Ethiopia.
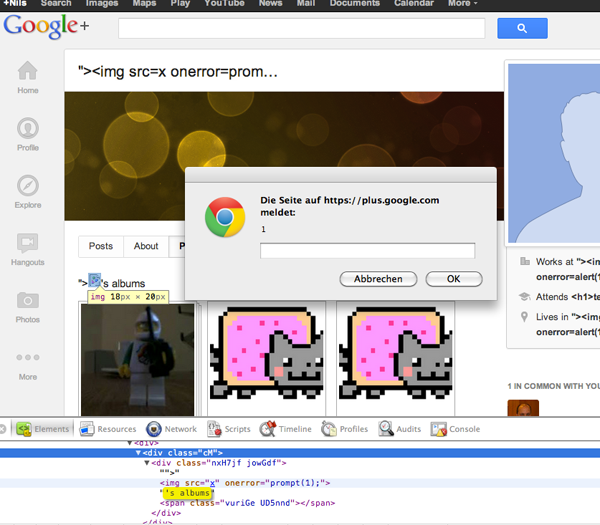
A specific code that causes an error on Google+ was indicated in Juneemann’s article: you need to create a profile with the name "> <img src = x onerror = prompt (1);> .
The story that holes in Google help build schools for African children touched the hearts of colleagues, and the famous hacker Charlie Miller published a retweet for himself - and then an interesting thing happened.
')
The InformationWeek publication leads Charlie Miller’s “author’s heading,” posting links from his tweets. Last night, this rubric got into Jununemann’s blog post as well. Unfortunately, the editors of the publication have inserted into the text of the page and that ill-fated code. As a result, the same bug appeared on InformationWeek as on Google+ ( link , screenshot )
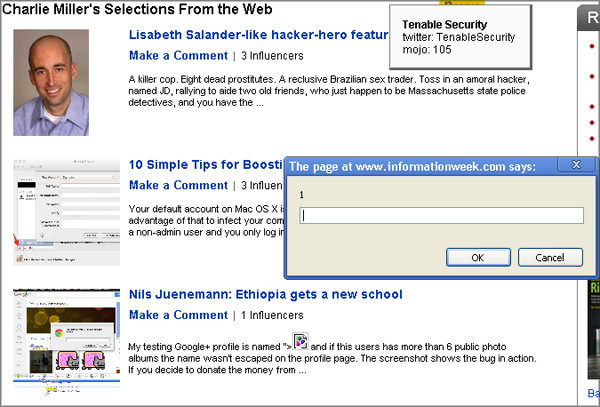
A specific code that causes an error on Google+ was indicated in Juneemann’s article: you need to create a profile with the name "> <img src = x onerror = prompt (1);> .

The story that holes in Google help build schools for African children touched the hearts of colleagues, and the famous hacker Charlie Miller published a retweet for himself - and then an interesting thing happened.
')
The InformationWeek publication leads Charlie Miller’s “author’s heading,” posting links from his tweets. Last night, this rubric got into Jununemann’s blog post as well. Unfortunately, the editors of the publication have inserted into the text of the page and that ill-fated code. As a result, the same bug appeared on InformationWeek as on Google+ ( link , screenshot )

Source: https://habr.com/ru/post/143048/
All Articles