Google chrome hacker is not an assistant
, Chrome XSS-. Why am I looking for vulnerabilities?
Like many of you, I do a Code Review and the first thing I’m looking for is of course a vulnerability. When a vulnerability is found in the code, it would be good to check if it actually exists through the browser, because there are “false alarms”. These are those cases when the data already comes filtered and XSS is impossible. It is always useful to be able to show the developer an attack in action, because this is a good argument and helps to quickly move to a constructive solution to the problem if there is any doubt that the vulnerability does exist. But I do not often check in the browser - either the problem is obvious directly from the code, or they believe in the word. In general, looking for vulnerabilities is interesting.
The beginning of this story
A friend dropped links to the site, which a year ago had XSS vulnerability, which I wrote to the owners of the resource. It became interesting to check again. I checked - there is XSS, but I couldn't get the simplest confirmation of JS execution! ..
')

I do not break websites and do not engage in security auditing, so it is possible that what I found out has long been known to specialists, but for me this was a revelation.
First suspicions
So, I began to check all sorts of code injection options - but without result. Along the way, I found out what and how is filtered, what are the checks and so on, but alert (1); persistently not performed. Along the way, XSRF was also found - a nice bonus!
There was a suspicion that the browser changes the code it received from the server. I tried using wget to get the HTML code of the page - yes, it does, but in a strange way. At first I suspected that he was trying to close the tags in order to fix the broken markup, but it turned out that the matter was different. All this time I used Google Chrome and the idea to try another browser somehow did not occur (but in vain!).
In the end, the simplest XSS test in FireFox gave a positive result - super! I did prove that there is a vulnerability, but it’s not clear why nothing happened in chrome?! .. I understand that browsers can render the same code in different ways, but Chrome did take a bite out of my embedded code, no matter how sophisticated I am did! A screenshot from Chrome, where the link to the external JS file is replaced with
about:blank :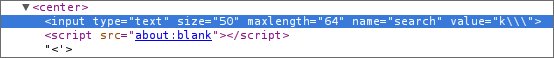
Thus, it is possible to attack users of FF, Opera, IE, but not Chrome. This is some kind of infringement of users. The problem did not give me rest, and the reason was still found! It turned out that Google Chrome from version 7 has an XSS filter (Cross Site Scripting Auditor ! It was this XSS Auditor that did not give me the opportunity to check for XSS.
The reason is clear, but the problem is not solved. Has Chrome become an unapproachable fortress ?! Is there no way to bypass this filter? If so, it is worth everyone recommends using Chrome and forget about XSS. Life is getting easier and better!
How to bypass XSS Auditor in Google Chrome?
But you can't be like that, right? So I did not believe it.

It is necessary to somehow bypass the XSS Auditor in Chrome to restore the universal equilibrium. I found such methods:
- You need to start the browser with the
--disable-xss-auditorkey. Great for testing. - If you control 2 parameters, they are inserted in 2 places on the page. We break the code into 2 parts and use multi-line comments to comment out HTML between these 2 points - details in Issue 96616: Security: Google Chrome Anti-XSS filter circumvention
- If there is an opportunity to leave one tag unclosed, then the browser itself will try to close it. And at first XSS Auditor will work, and then the browser will try to close the tags.
- Send a special HTTP header that disables XSS Auditor ( Proof ):
header("X-XSS-Protection: 0");
findings
Use Google Chrome to test XSS without add. movements will not work - it's easier to take any other browser.
But to protect yourself from XSS is quite possible, but it is worth remembering that Google uses its browser to collect information - so there’s a double-edged sword.
What else can you read?
Source: https://habr.com/ru/post/143022/
All Articles