Vulnerabilities of the Android platform. Present and future
Dear and much-loved habravchane, we invite you to familiarize yourself with the very interesting material of our analyst Alexander Goryachev, written specifically for Habrahabr. The article is devoted to a review of existing vulnerabilities in the highly popular Android mobile platform, as well as how it could be made more secure. Comments and your own thoughts on the topic are welcome.
Android OS for a short period of time has become one of the most popular systems for all kinds of mobile devices. It is used by both large manufacturers with a worldwide reputation and small companies, so the price dispersion of finished products, such as smartphones and tablet computers, allows us to satisfy the needs of consumers almost one hundred percent. It was a wide assortment, flexible pricing and platform support from an impressive number of manufacturers that became one of the main success factors and allowed the system to occupy the current market position.
However, such a huge number of users simply could not remain without attention from the attackers. Having built an entire industry with its own laws on the development and distribution of malware, they have become extremely indifferent to any source of easy money.
Like any other system, Android, unfortunately, cannot be completely secure, as the people involved in the development will never be able to create the perfect code. Nevertheless, developers are making efforts to ensure that consumers ultimately receive a quality product. On the example of Android, we can observe another confirmation that the more popular a product is, the more susceptible it is to attacks by intruders. Further in this material we will in detail consider what threats this operating system is exposed to and, as a result, its users.
')
Viruses for Android? No, I did not hear!
When the first Android malware was discovered in August 2010, many users perceived this news as a kind of attempt by antivirus companies to intimidate them and raise money for their products. Over time, the number of threats to Android continued to grow. More than a year and a half has passed since the first Trojan appeared, but despite the fact that at the end of 2011 the number of malicious programs for this platform increased at least 20 times, a large number of users are still skeptical about the issue under discussion.
So, what are the malicious programs for the Android OS and how are they dangerous?
The list is confidently headed by SMS Trojans (Android.SmsSend family). The purpose of such programs is to send messages with increased billing to short numbers. Part of the value of these messages goes into the pocket of intruders, enriching them. Such programs practically do not differ from each other, except for minor changes in the interface and short numbers to which messages will be sent. Most often they are distributed under the guise of popular applications and games, such as Opera Mini, ICQ, Skype, Angry Birds, etc., using the corresponding icon.

Next on the list are more “heavyweight” Trojans. These include, for example, Android.Gongfu, Android.Wukong, Android.DreamExploid, Android.Geinimi, Android.Spy, etc. Depending on the family, these malicious programs have features such as, for example, collecting user confidential information, adding bookmarking browsers, executing commands from intruders (backdoor and bot functions), sending SMS messages, installing other applications, etc. To realize the ability to install applications without arousing suspicion from the user, Trojans need root rights ( with whom you work system kernel). To do this, they use various methods, which will be discussed in more detail a little later.
It is also important to note commercial spyware. These applications are used to spy on users. Their arsenal, depending on the class, cost and manufacturer, includes such functions as intercepting incoming and outgoing SMS messages and calls, audio recording of the environment, tracking coordinates, collecting statistical data from the browser (for example, bookmarks, history of visits), etc. Despite the fact that most of these programs require initial setup and manual installation, they pose a significant threat, since after insertion into the device they do not create an icon among other installed programs, and their presence can be detected only by indirect signs, including by going to the system menu with a list of applications. If you closely follow the installed programs and know the names of legal applications, then you can quite successfully recognize the uninvited guest, but an ordinary user will most likely not suspect anything.
Other malware can combine the various functions described above.
Separately, it should be said about the advertising modules used by the creators of programs and games and used for earnings. When the user clicks on the displayed advertising message and goes to the advertised product or service, the application developer receives a certain amount of money. In most cases, such modules do not pose a danger to the user, however among them there are less harmless ones. For example, advertising messages can appear not inside applications, but in the status bar of a device. Such messages can easily be mistaken for system messages, which the attackers use when they use advertising phrases like “Urgent update of the system” (almost certainly, instead of updating, you will receive another Trojan).
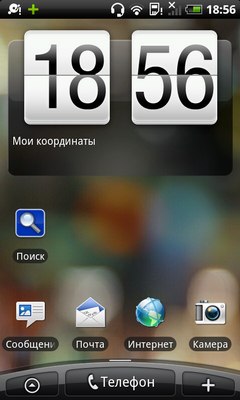
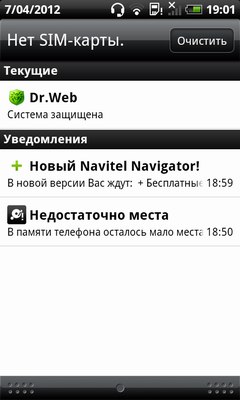
A number of modules behave too aggressively, collecting confidential user information (IMEI, phone number, operator name, etc.), as well as adding shortcuts to the desktop and bookmarks to the browser. Applications using such modules are detected as adware or Adware (for example, Adware.Airpush, Adware.Leadbolt, Adware.Startapp, etc.).
Vulnerabilities of the Android operating system and the software it uses
The Android architecture is built in such a way that all applications work with limited rights and do not have access to the protected data of other applications.
As noted above, Android is not an ideal system, so it is not surprising that it contains vulnerabilities. One of the main problems that users may encounter is system vulnerabilities, which allow to get root rights. There are special applications, scripts and software modules that perform this task. In everyday life, such things are not frightening to users, as they most often use them consciously to gain more control over the device. Another thing is that the same vulnerabilities (for example, CVE-2009-1185, CVE-2011-1823) were adopted by the creators of malicious applications. Using exploits (the same software modules and scripts) to raise their rights to the root level, they can, for example, easily install other programs without the user's permission (as various modifications of Android.Gongfu and Android.DreamExploid do). Some malicious programs do not use the exploits themselves, directly, but mislead the user and encourage him to perform the necessary actions, thereby giving the malicious program the capabilities it needs.
One of the key elements of Android security is the Permission System. When installing applications, the user is shown a list of all the functions that will be available to a particular program. After installation, applications can perform their functions without user intervention. On the one hand, demonstration of the capabilities of the programs before installation should ensure an adequate level of security, but not all users carefully study the list of functions. Moreover, it is impossible to say with certainty whether this or that function will not be used further to the detriment of the user. But this is not the last drawback of this system. For example, it is possible to create applications that will not require any permissions for their work, which may create a false sense of complete security. However, in reality, such applications will be able to access certain information (for example, files stored on a memory card in an unprotected form, a list of installed programs used by the mobile operator) and even send this information to attackers via the Internet.
The use of unofficial or third-party firmware may also pose a threat. There are several reasons for concern. First, malicious programs can be built into such firmware from the very beginning. Secondly, when an application is signed with a digital signature of a system image, it receives the same rights as the system in which it operates. As part of the Android Open Source Project (AOSP), signatures for images are private, so this scenario is possible, for example, in case of theft of the corresponding signature. A similar infection method was used, in particular, by the Android.SmsHider malware, which could unnoticeably for users using certain third-party firmware to install the Trojan apk contained in it.
System applications, both standard and applications from suppliers of Android devices, are also vulnerable to vulnerabilities. For example, some WebKit browser vulnerabilities allow potential malware to execute arbitrary JavaScript code and gain access to protected browser data.
If application software developers do not pay enough attention to security when working with user data, this data can be compromised. The unencrypted registration data, bank card passwords and other confidential information can be attacked. If, during the operation of the application, the same data is transmitted over the network directly in the unencrypted form, then they are also potentially subject to compromise by the intruders. One of the notable precedents of a similar problem was the situation with the Skype application, where user data, including profile information, contacts, and correspondence history, were stored in an unencrypted form and, if desired, could be easily obtained by attackers.
Openness
The openness of the Android system lies in several factors. First, it is the availability of code that can be used, modified, and improved by developers depending on their needs and ideas. On the one hand, for device manufacturers and developers, this is a definite plus, on the other hand, it enables not only researchers, but also attackers to more productively find vulnerabilities and errors.
Secondly, it is possible to install applications from the official Google Play application catalog (previously called the Android Market), or from any other available source.
Thirdly, the creation of applications is practically public, since it is necessary to pay only $ 25 if the developer wants to place their products in the official catalog, and for distributing programs outside of it, their costs are not needed at all.
Fourthly, programs placed on Google Play have not been subjected to preliminary testing or testing by Google until recently. Most recently, the Bouncer system was announced, which should check applications hosted in the Play catalog for the presence of malicious functions; developer accounts will also be checked. Undoubtedly, this should to some extent increase security, but still does not solve the problem, since the creators of malicious programs can use various tricks to successfully bypass the Bouncer system.
Platform fragmentation
Due to the fact that the Android system uses a large number of manufacturers of mobile devices, and at the same time there is no specific framework for their technical characteristics, devices with the most diverse functionality are available to consumers. As the next system update is released, not only new functions are added to it, but also vulnerabilities discovered earlier are being closed. Manufacturers at their discretion to release the appropriate version of the update. Sometimes it happens that the device, which was recently a flagship, does not receive a new version of the OS or software and, accordingly, remains unprotected from potential threats. The reason for this may be both economic considerations (adaptation of the update will require too large financial investments, or the manufacturer simply wants to make money on sales of new devices) and purely technical ones (the update will not function correctly on outdated hardware, or the installation will not have enough physical memory devices).
Human factor
Whatever the level of security of the system, the human factor plays a significant role in ensuring security. As an example, we can cite elements of social engineering that are used by attackers, for example, the previously mentioned method of distributing malware through advertising in applications using loud phrases (“Urgent update of the system”, “Your browser version is outdated”, “Install Skype update immediately " etc.). The same can be said about the cases of the spread of malicious programs using spam e-mails via SMS (in this way, for example, the Android.Crusewind backdoor was distributed).
Another element of social engineering is playing on the desire of many people for something free (“New version of Need for Speed”, “Upgrading Asphalt for free!”), As well as using the theme “for adults” (“Supergirls, download it here!” "Collection of photos of nude beauty", etc.).


In addition, the attentiveness of the users themselves is important. Very often attackers fake known sites, imitating their design, structure, or trying to create an exact copy. At first glance, such a site may look just like a real one, but upon closer scrutiny you will notice a catch. For example, in the address bar you will see a site that is completely different from the original, or has small distortions (for example, vkontlakte.com, vkontakne.b1.ru, androldmarket.com), or some familiar element will not work on it, or will be missing something familiar.
Applications can also be faked, and an inattentive user is more likely to share his personal data with the attackers (username and password from the social network, credit card information, etc.). There may be many options.
findings
So, we have considered the most common threats that users of devices running the Android operating system may face. Now we can summarize and draw some conclusions.
One of the main security problems when working with the Android OS, first of all, is the human factor. No matter how secure the operating system is, carelessness, inattention, self-confidence and simple ignorance will sooner or later endanger the owner of a smart device. For example, the user's confidence in the fact that he is not in danger, forces him to ignore security tools, such as anti-virus programs. In the case of the use of tempting offers by attackers, for example, downloading free versions of paid applications and games, people use the desire to gain profit without loss for themselves. When a well-known site, game or application is faked, and the user is inexperienced, he may not be aware that he is at risk by installing a program or entering his own confidential information.
The next important problem is indirectly related to the first one and concerns the software vulnerability of both the operating system itself and the application software. Android is created by people who, by nature, can make mistakes. These errors may never be noticed, but may appear at the most inopportune moment. The detected error in the code is adopted by the attackers, if it brings them a certain benefit. Thus, users are faced, for example, with malicious programs that use root-exploits to elevate privileges in the system. Most of these exploits were initially thought of as an aid to more experienced users, but quickly moved into the arsenal of cybercriminals.
Despite the efforts of Android developers to ensure maximum system and user security, there are ways to circumvent security barriers. In addition to root-exploits, an example is the signature of malicious applications with a security certificate of third-party firmware, which allows such programs to work with the system rights on the corresponding OS image. The permit system is also flawed.The previously described case of creating an application that does not require any permissions for its work at all is also an example of the fact that mistakes are made and any protection can be circumvented.
If application developers do not pay enough attention to security, this can affect the level of protection. The Skype case confirmed this. Similar gaps can be found in other applications, which can not be called good news for users.
Despite the positive aspects of Google’s open platform policy, there are also negative aspects. First, it increases the likelihood of detecting vulnerabilities that attackers can exploit. Secondly, a very liberal attitude towards the process of creating applications and the wide possibilities for their installation by end users is also exploited by enterprising cybercriminals. Google’s introduction of the Bouncer system is a step towards increasing security without major changes in the openness policy of the Android ecosystem, but cannot be the solution to all problems.
The next major weakness of the Android OS is its fragmentation. The existence of a large number of manufacturers of devices and different versions of the system creates certain difficulties, since users can not always get the necessary update, which significantly affects security. The desire of some manufacturers to release new models as often as possible may even force some consumers to abandon the further use of devices with Android. This may be due to the fact that they can not get the desired update of the system, and the fact that the characteristics of devices after the release of new models have time to become outdated and no longer meet the requirements of users.
And, of course, malware is dangerous. Using the above-mentioned features of Android, attackers quickly adapted to the new structure of the mobile device market and began to master all possible and most profitable schemes for them. In their dark deeds, they use SMS Trojans to make quick and easy profits; the use of Trojans that steal confidential user data also allows them to earn money, for example, from reselling email information, logins and passwords from various social networks and other services that are beneficial for them. The use of social engineering also makes a significant contribution to their prosperity.
Do not forget about the manufacturers of commercial spyware programs that sell their solutions for a decent amount. At first glance, prices may seem very high, but the benefits that potential customers may receive may be several times higher.
What is in the future?
With a certain degree of confidence, we can say that in the near future, the owners of Android devices will continue to be threatened by malicious programs, especially SMS Trojans. Spyware Trojans and hijackers that collect confidential information will not be left behind. In the future, malware will also appear, combining various functions, including those using root exploits. It is also possible the use of detected vulnerabilities in popular applications.
The organization of large botnets capable of carrying out attacks on Internet resources or carrying out mass spam sending is not excluded. An increase in cases of infection by malicious programs of users who use third-party and unofficial firmware is possible. Such attacks can also be local, targeted, when attackers will select the most interesting for them firmware versions.
Probably the appearance of Trojans blockers and extortionists already familiar to Windows users. Attacks of such malware can be distributed, for example, among owners of devices with root rights, but it is also possible that these Trojans will themselves perform the necessary actions to elevate privileges in the system or encourage the user to do this using social engineering techniques.
In addition to the "classic" Trojan spies, cases of detection of the so-called. analytic applications like Carrier IQ. Such programs can be used by device manufacturers and telecom operators to collect statistical and analytical information, however, as the Carrier IQ case showed, the information collected may be excessive and directly threaten the privacy of users. Manufacturers should at least inform consumers about the availability of such applications and the features of their work. Nevertheless, there are cases when the manufacturers themselves will not fully know how the information collected meets the security requirements.
One way or another, social engineering will remain one of the main vectors of attack. An important role in ensuring security should be played by the attentiveness and caution of users. The appropriate level of security must come from mobile device manufacturers, as well as from application vendors. They need to release system and application updates as soon as they become aware of vulnerabilities. It is also necessary to ensure an adequate level of user privacy and the protection of their personal information.
In the direction of enhancing Android security, improvements are still possible. For example, the functionality of the applied permission system can be expanded by adding an additional degree of application control. Now users can see which functions a particular application can use only during installation and when opening the corresponding information in the system menu of the device. If, however, a system is introduced that reflects the need for programs to perform an action, as well as allowing the user to decide for himself what opportunities to provide to the program, this can increase the level of security.
Android OS for a short period of time has become one of the most popular systems for all kinds of mobile devices. It is used by both large manufacturers with a worldwide reputation and small companies, so the price dispersion of finished products, such as smartphones and tablet computers, allows us to satisfy the needs of consumers almost one hundred percent. It was a wide assortment, flexible pricing and platform support from an impressive number of manufacturers that became one of the main success factors and allowed the system to occupy the current market position.
However, such a huge number of users simply could not remain without attention from the attackers. Having built an entire industry with its own laws on the development and distribution of malware, they have become extremely indifferent to any source of easy money.
Like any other system, Android, unfortunately, cannot be completely secure, as the people involved in the development will never be able to create the perfect code. Nevertheless, developers are making efforts to ensure that consumers ultimately receive a quality product. On the example of Android, we can observe another confirmation that the more popular a product is, the more susceptible it is to attacks by intruders. Further in this material we will in detail consider what threats this operating system is exposed to and, as a result, its users.
')
Viruses for Android? No, I did not hear!
When the first Android malware was discovered in August 2010, many users perceived this news as a kind of attempt by antivirus companies to intimidate them and raise money for their products. Over time, the number of threats to Android continued to grow. More than a year and a half has passed since the first Trojan appeared, but despite the fact that at the end of 2011 the number of malicious programs for this platform increased at least 20 times, a large number of users are still skeptical about the issue under discussion.
So, what are the malicious programs for the Android OS and how are they dangerous?
The list is confidently headed by SMS Trojans (Android.SmsSend family). The purpose of such programs is to send messages with increased billing to short numbers. Part of the value of these messages goes into the pocket of intruders, enriching them. Such programs practically do not differ from each other, except for minor changes in the interface and short numbers to which messages will be sent. Most often they are distributed under the guise of popular applications and games, such as Opera Mini, ICQ, Skype, Angry Birds, etc., using the corresponding icon.

Next on the list are more “heavyweight” Trojans. These include, for example, Android.Gongfu, Android.Wukong, Android.DreamExploid, Android.Geinimi, Android.Spy, etc. Depending on the family, these malicious programs have features such as, for example, collecting user confidential information, adding bookmarking browsers, executing commands from intruders (backdoor and bot functions), sending SMS messages, installing other applications, etc. To realize the ability to install applications without arousing suspicion from the user, Trojans need root rights ( with whom you work system kernel). To do this, they use various methods, which will be discussed in more detail a little later.
It is also important to note commercial spyware. These applications are used to spy on users. Their arsenal, depending on the class, cost and manufacturer, includes such functions as intercepting incoming and outgoing SMS messages and calls, audio recording of the environment, tracking coordinates, collecting statistical data from the browser (for example, bookmarks, history of visits), etc. Despite the fact that most of these programs require initial setup and manual installation, they pose a significant threat, since after insertion into the device they do not create an icon among other installed programs, and their presence can be detected only by indirect signs, including by going to the system menu with a list of applications. If you closely follow the installed programs and know the names of legal applications, then you can quite successfully recognize the uninvited guest, but an ordinary user will most likely not suspect anything.
Other malware can combine the various functions described above.
Separately, it should be said about the advertising modules used by the creators of programs and games and used for earnings. When the user clicks on the displayed advertising message and goes to the advertised product or service, the application developer receives a certain amount of money. In most cases, such modules do not pose a danger to the user, however among them there are less harmless ones. For example, advertising messages can appear not inside applications, but in the status bar of a device. Such messages can easily be mistaken for system messages, which the attackers use when they use advertising phrases like “Urgent update of the system” (almost certainly, instead of updating, you will receive another Trojan).


A number of modules behave too aggressively, collecting confidential user information (IMEI, phone number, operator name, etc.), as well as adding shortcuts to the desktop and bookmarks to the browser. Applications using such modules are detected as adware or Adware (for example, Adware.Airpush, Adware.Leadbolt, Adware.Startapp, etc.).


Vulnerabilities of the Android operating system and the software it uses
The Android architecture is built in such a way that all applications work with limited rights and do not have access to the protected data of other applications.
As noted above, Android is not an ideal system, so it is not surprising that it contains vulnerabilities. One of the main problems that users may encounter is system vulnerabilities, which allow to get root rights. There are special applications, scripts and software modules that perform this task. In everyday life, such things are not frightening to users, as they most often use them consciously to gain more control over the device. Another thing is that the same vulnerabilities (for example, CVE-2009-1185, CVE-2011-1823) were adopted by the creators of malicious applications. Using exploits (the same software modules and scripts) to raise their rights to the root level, they can, for example, easily install other programs without the user's permission (as various modifications of Android.Gongfu and Android.DreamExploid do). Some malicious programs do not use the exploits themselves, directly, but mislead the user and encourage him to perform the necessary actions, thereby giving the malicious program the capabilities it needs.
One of the key elements of Android security is the Permission System. When installing applications, the user is shown a list of all the functions that will be available to a particular program. After installation, applications can perform their functions without user intervention. On the one hand, demonstration of the capabilities of the programs before installation should ensure an adequate level of security, but not all users carefully study the list of functions. Moreover, it is impossible to say with certainty whether this or that function will not be used further to the detriment of the user. But this is not the last drawback of this system. For example, it is possible to create applications that will not require any permissions for their work, which may create a false sense of complete security. However, in reality, such applications will be able to access certain information (for example, files stored on a memory card in an unprotected form, a list of installed programs used by the mobile operator) and even send this information to attackers via the Internet.
The use of unofficial or third-party firmware may also pose a threat. There are several reasons for concern. First, malicious programs can be built into such firmware from the very beginning. Secondly, when an application is signed with a digital signature of a system image, it receives the same rights as the system in which it operates. As part of the Android Open Source Project (AOSP), signatures for images are private, so this scenario is possible, for example, in case of theft of the corresponding signature. A similar infection method was used, in particular, by the Android.SmsHider malware, which could unnoticeably for users using certain third-party firmware to install the Trojan apk contained in it.
System applications, both standard and applications from suppliers of Android devices, are also vulnerable to vulnerabilities. For example, some WebKit browser vulnerabilities allow potential malware to execute arbitrary JavaScript code and gain access to protected browser data.
If application software developers do not pay enough attention to security when working with user data, this data can be compromised. The unencrypted registration data, bank card passwords and other confidential information can be attacked. If, during the operation of the application, the same data is transmitted over the network directly in the unencrypted form, then they are also potentially subject to compromise by the intruders. One of the notable precedents of a similar problem was the situation with the Skype application, where user data, including profile information, contacts, and correspondence history, were stored in an unencrypted form and, if desired, could be easily obtained by attackers.
Openness
The openness of the Android system lies in several factors. First, it is the availability of code that can be used, modified, and improved by developers depending on their needs and ideas. On the one hand, for device manufacturers and developers, this is a definite plus, on the other hand, it enables not only researchers, but also attackers to more productively find vulnerabilities and errors.
Secondly, it is possible to install applications from the official Google Play application catalog (previously called the Android Market), or from any other available source.
Thirdly, the creation of applications is practically public, since it is necessary to pay only $ 25 if the developer wants to place their products in the official catalog, and for distributing programs outside of it, their costs are not needed at all.
Fourthly, programs placed on Google Play have not been subjected to preliminary testing or testing by Google until recently. Most recently, the Bouncer system was announced, which should check applications hosted in the Play catalog for the presence of malicious functions; developer accounts will also be checked. Undoubtedly, this should to some extent increase security, but still does not solve the problem, since the creators of malicious programs can use various tricks to successfully bypass the Bouncer system.
Platform fragmentation
Due to the fact that the Android system uses a large number of manufacturers of mobile devices, and at the same time there is no specific framework for their technical characteristics, devices with the most diverse functionality are available to consumers. As the next system update is released, not only new functions are added to it, but also vulnerabilities discovered earlier are being closed. Manufacturers at their discretion to release the appropriate version of the update. Sometimes it happens that the device, which was recently a flagship, does not receive a new version of the OS or software and, accordingly, remains unprotected from potential threats. The reason for this may be both economic considerations (adaptation of the update will require too large financial investments, or the manufacturer simply wants to make money on sales of new devices) and purely technical ones (the update will not function correctly on outdated hardware, or the installation will not have enough physical memory devices).
Human factor
Whatever the level of security of the system, the human factor plays a significant role in ensuring security. As an example, we can cite elements of social engineering that are used by attackers, for example, the previously mentioned method of distributing malware through advertising in applications using loud phrases (“Urgent update of the system”, “Your browser version is outdated”, “Install Skype update immediately " etc.). The same can be said about the cases of the spread of malicious programs using spam e-mails via SMS (in this way, for example, the Android.Crusewind backdoor was distributed).
Another element of social engineering is playing on the desire of many people for something free (“New version of Need for Speed”, “Upgrading Asphalt for free!”), As well as using the theme “for adults” (“Supergirls, download it here!” "Collection of photos of nude beauty", etc.).


In addition, the attentiveness of the users themselves is important. Very often attackers fake known sites, imitating their design, structure, or trying to create an exact copy. At first glance, such a site may look just like a real one, but upon closer scrutiny you will notice a catch. For example, in the address bar you will see a site that is completely different from the original, or has small distortions (for example, vkontlakte.com, vkontakne.b1.ru, androldmarket.com), or some familiar element will not work on it, or will be missing something familiar.

Applications can also be faked, and an inattentive user is more likely to share his personal data with the attackers (username and password from the social network, credit card information, etc.). There may be many options.
findings
So, we have considered the most common threats that users of devices running the Android operating system may face. Now we can summarize and draw some conclusions.
One of the main security problems when working with the Android OS, first of all, is the human factor. No matter how secure the operating system is, carelessness, inattention, self-confidence and simple ignorance will sooner or later endanger the owner of a smart device. For example, the user's confidence in the fact that he is not in danger, forces him to ignore security tools, such as anti-virus programs. In the case of the use of tempting offers by attackers, for example, downloading free versions of paid applications and games, people use the desire to gain profit without loss for themselves. When a well-known site, game or application is faked, and the user is inexperienced, he may not be aware that he is at risk by installing a program or entering his own confidential information.
The next important problem is indirectly related to the first one and concerns the software vulnerability of both the operating system itself and the application software. Android is created by people who, by nature, can make mistakes. These errors may never be noticed, but may appear at the most inopportune moment. The detected error in the code is adopted by the attackers, if it brings them a certain benefit. Thus, users are faced, for example, with malicious programs that use root-exploits to elevate privileges in the system. Most of these exploits were initially thought of as an aid to more experienced users, but quickly moved into the arsenal of cybercriminals.
Despite the efforts of Android developers to ensure maximum system and user security, there are ways to circumvent security barriers. In addition to root-exploits, an example is the signature of malicious applications with a security certificate of third-party firmware, which allows such programs to work with the system rights on the corresponding OS image. The permit system is also flawed.The previously described case of creating an application that does not require any permissions for its work at all is also an example of the fact that mistakes are made and any protection can be circumvented.
If application developers do not pay enough attention to security, this can affect the level of protection. The Skype case confirmed this. Similar gaps can be found in other applications, which can not be called good news for users.
Despite the positive aspects of Google’s open platform policy, there are also negative aspects. First, it increases the likelihood of detecting vulnerabilities that attackers can exploit. Secondly, a very liberal attitude towards the process of creating applications and the wide possibilities for their installation by end users is also exploited by enterprising cybercriminals. Google’s introduction of the Bouncer system is a step towards increasing security without major changes in the openness policy of the Android ecosystem, but cannot be the solution to all problems.
The next major weakness of the Android OS is its fragmentation. The existence of a large number of manufacturers of devices and different versions of the system creates certain difficulties, since users can not always get the necessary update, which significantly affects security. The desire of some manufacturers to release new models as often as possible may even force some consumers to abandon the further use of devices with Android. This may be due to the fact that they can not get the desired update of the system, and the fact that the characteristics of devices after the release of new models have time to become outdated and no longer meet the requirements of users.
And, of course, malware is dangerous. Using the above-mentioned features of Android, attackers quickly adapted to the new structure of the mobile device market and began to master all possible and most profitable schemes for them. In their dark deeds, they use SMS Trojans to make quick and easy profits; the use of Trojans that steal confidential user data also allows them to earn money, for example, from reselling email information, logins and passwords from various social networks and other services that are beneficial for them. The use of social engineering also makes a significant contribution to their prosperity.
Do not forget about the manufacturers of commercial spyware programs that sell their solutions for a decent amount. At first glance, prices may seem very high, but the benefits that potential customers may receive may be several times higher.
What is in the future?
With a certain degree of confidence, we can say that in the near future, the owners of Android devices will continue to be threatened by malicious programs, especially SMS Trojans. Spyware Trojans and hijackers that collect confidential information will not be left behind. In the future, malware will also appear, combining various functions, including those using root exploits. It is also possible the use of detected vulnerabilities in popular applications.
The organization of large botnets capable of carrying out attacks on Internet resources or carrying out mass spam sending is not excluded. An increase in cases of infection by malicious programs of users who use third-party and unofficial firmware is possible. Such attacks can also be local, targeted, when attackers will select the most interesting for them firmware versions.
Probably the appearance of Trojans blockers and extortionists already familiar to Windows users. Attacks of such malware can be distributed, for example, among owners of devices with root rights, but it is also possible that these Trojans will themselves perform the necessary actions to elevate privileges in the system or encourage the user to do this using social engineering techniques.
In addition to the "classic" Trojan spies, cases of detection of the so-called. analytic applications like Carrier IQ. Such programs can be used by device manufacturers and telecom operators to collect statistical and analytical information, however, as the Carrier IQ case showed, the information collected may be excessive and directly threaten the privacy of users. Manufacturers should at least inform consumers about the availability of such applications and the features of their work. Nevertheless, there are cases when the manufacturers themselves will not fully know how the information collected meets the security requirements.
One way or another, social engineering will remain one of the main vectors of attack. An important role in ensuring security should be played by the attentiveness and caution of users. The appropriate level of security must come from mobile device manufacturers, as well as from application vendors. They need to release system and application updates as soon as they become aware of vulnerabilities. It is also necessary to ensure an adequate level of user privacy and the protection of their personal information.
In the direction of enhancing Android security, improvements are still possible. For example, the functionality of the applied permission system can be expanded by adding an additional degree of application control. Now users can see which functions a particular application can use only during installation and when opening the corresponding information in the system menu of the device. If, however, a system is introduced that reflects the need for programs to perform an action, as well as allowing the user to decide for himself what opportunities to provide to the program, this can increase the level of security.
Source: https://habr.com/ru/post/142993/
All Articles