TSM service for managing NFC SIM applications
Definition
TSM (Trusted Service Manager) is a service that allows service providers and mobile operators to manage their contactless applications remotely, providing access to secure items on NFC-enabled terminals. The owner of the TSM server acts as an intermediary who establishes business agreements and technical communications between the mobile operator, service providers or other persons controlling access to the secure elements of the contactless application on the NFC-enabled mobile terminals.
Main functions
- providing communication between the mobile operator and the service provider;
- guarantee of secure data exchange;
- lifecycle management contactless applications;
- registration of new users (creation of the Security Domain, downloading and personalizing a contactless application via OTA);
- activation and deactivation of services;
- update user interface;
- management of NFC client database;
- EMV balance update (Europay, MasterCard and VISA card balance) for payment;
- management of value-added services such as ticket re-registration;
- key management for secure access to the application.
TSM tasks
It is assumed that in the near future, end users will use NFC technology in mobile phones to make various payments, purchase transport tickets, ensure loyalty, access and many other contactless services. Similar systems have already been implemented in several places around the world, but they are usually limited in scale and number of participants in the process. The main task is the introduction of such systems to the masses.
The question of how to create a compatible, mobile NFC system, which provides a simple exchange between service providers (SP) and mobile operators for collaboration.
The answer of the GSM Association was to create a hardware-software complex (TSM), which establishes the connection between service providers and MNO. The task of TSM is also to ensure the level of trust and confidentiality between the parties.
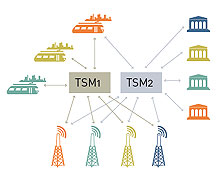
Figure 1 illustrates the chaotic nature of the business environment without TSM.
')
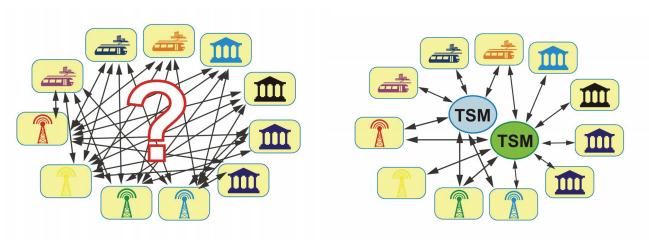
Figure 1. The main task of TSM.
A mobile NFC system requires the connection of several individuals or subjects from different business environments and the use of heterogeneous systems, thus facilitating the exchange of data to support business functionality. This will require changes in current process streams to provide new functionality.
NFC application
The memory area on the smart card can be effectively used as storage for an NFC application. One example is the e-wallet concept. Today, the wallet contains a large number of plastic cards of various types. All of them can be submitted as NFC applications at UICC. In addition, loyalty cards, tickets, door-lock systems, membership cards, any magnetic stripe cards can be presented and implemented as NFC applications on UICC.
The advantage of using UICC is the personal nature (binding of the card to the subscriber), compatibility between mobile phones, and its own security system.
As in any application environment, there is a need to add new applications, remove old ones, update existing ones with new versions, and provide actual data to applications. Such a management system will require the use of the OTA platform. The mobile operator plays a key role here, as it has the infrastructure that today allows management using the OTA platform.
An NFC application on a UICC may be resident, but it may be necessary to provide a user interface to the application. Examples of applications that require a user interface: activation of an application when buying from a vending machine (terminal), status and information, a list of credit / debit cards available for use, confirmation of a monthly purchase of a transport ticket.
RAM (Remote Applet Manager) functionality is required to load, update, and delete NFC applications on UICC. Also, downloading applications can be done via SMS. This becomes especially problematic for updating large batches of UICCs simultaneously. Using high-speed communications, such as BIP, which uses GPRS and UMTS channels to transfer data, is the preferred way to perform an application update on a UICC.
Implementation examples
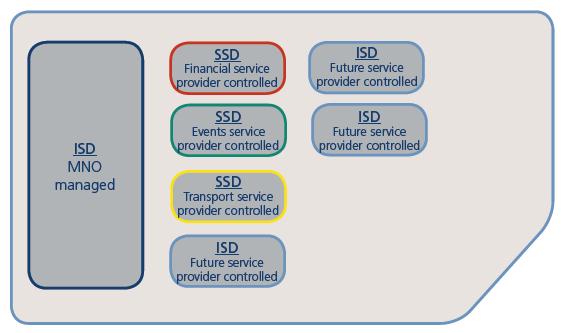
In the NFC system, the MNO (mobile network operator) provides for the storage of applications distributed among subscribers of the SIM card. Thus, MNO has the opportunity to choose the appropriate business model and, therefore, choose personalization rights that will be supported on the side of the SIM card and that will be available to its partners (service providers and service managers). Three main scenarios for different business models:
- Simple Mode: issuer oriented model, where the card content management is performed only by the MNO, but is controlled by the TSM;
- Delegated Mode: the card content management can be delegated by TSM, but each operation requires authorization from the MNO;
- Authorized Mode: card content management is fully delegated to TSM.
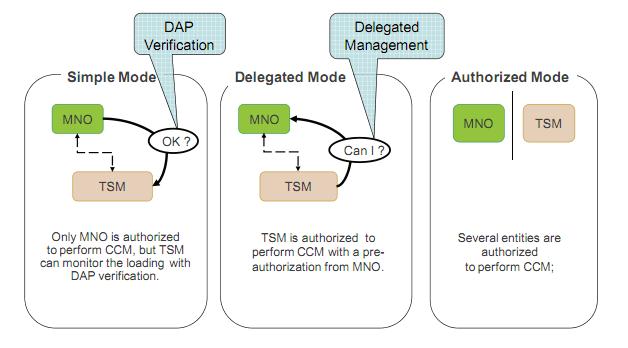
Figure 2. The difference in business models for managing a contactless application.
In Simple Mode, content management is performed by MNO. Only MNO can download payment applications to the SIM card.
In the Delegated Mode model, MNO is no longer responsible for downloading, installing, activating, or deleting an application. The card content is managed by TSM with permission (pre-authorization) of the MNO. In some cases, for reasons of confidentiality, SP can manage the process of personalizing the application.
The features of the Authorized Mode model are that TSM has the ability to manage the contents of the SP application without prior authorization from the MNO.
Implementation on the MNO side
On the MNO side, implementation is possible in two versions:
- TSM is implemented by the MNO itself;
- TSM is implemented by third parties.
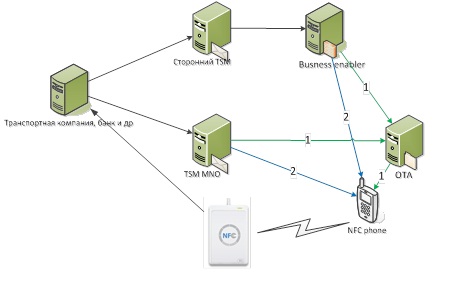
In the first case, when organizing TSM on the operator’s side, the transfer of transaction data is possible both directly to the terminal (NFC-enabled phone) and through the OTA platform. OTA is preferable to use if necessary, for example, to share the load, when the application will download through OTA, and control the application directly from TSM.
In the case of TSM implementation by third-party organizations, the data transfer on the operation occurs through the Business Enabler, in order to be able to control operations from the MNO. Business Enabler allows MNO to activate or deactivate third party TSM. After successfully completing the transaction through the Business Enabler, further data transfer is possible both directly to the terminal and through the OTA platform.
findings
As a rule, the NFC services provided to the end user require the protection of the transmitted data. Meeting this requirement from the point of view of using a mobile phone means that the phone has a secure element, which can be included either in the SIM card or in a separate chip (directly on the phone card or as part of an external memory card). In turn, such an element of security must have a single owner, possessing keys to access information stored in the memory of the element of security.
Obviously, the principle of the existence of a single owner of access keys is in contradiction with the completely logical desire to provide services to the user from several independent suppliers. Such service providers can operate in non-intersecting markets (for example, a transport company and a bank) or they can be direct competitors. But even in the first case, companies, as a rule, do not want to provide third-party structures with access to their data.
Such a contradiction can be resolved by implementing Trusted Service Manager, a third-party structure trusted by all service providers.
The emergence of Trusted Service Manager to work with applications will allow service providers and mobile operators to optimize their investments in equipment and speed up the implementation of projects without any compromises in the control of applications and data.
Abbreviations and acronyms
AP (Application Provider) - Application Provider
APSD (Application Provider Security Domain) - Application Provider Security Domain
AM (Authorized Management) - Authorized Management
CA (Controlling Authority) - Authorization Controller
CASD (Controlling Authority Security Domain) - Authorization Controller Security Domain
CCM (Card Content Management) - Card Content Management
CKLA (Confidential Key Loading Authority) - Sector Key Loading Controller
DM (Delegated Management) - Delegated Management
DAP (Data Authentication Pattern) - DAP Verification
ISD (Issuer Security Domain) - Domain Security Controller
LPO (Link Platform Operator) - Platform Operator
MNO (Mobile Network Operator) - Mobile Operator
NFC (Near Field Communication) - Contactless Data Transfer Technology
OTA (Over-The-Air) - OTA Platform
SCP (Smart Card Platform) - SCP platforms: 02 - a secure channel on hex key; 80 - OTA
SE (Secure Element) - Security Module
SP (Service Provider) - Service Provider
SSD (Supplementary Security Domain) - Additional Security Domain
TSD (Trusted Service Manager Security Domain) - TSM Security Domain
TSM (Trusted Service Manager) - TSM Service
UICC (Universal Integrated Circuit Card) - Smart Card
Sources
Some images and text of this article are contained in open presentations from SmartTrust and GlobalPlatform.
Source: https://habr.com/ru/post/142861/
All Articles