How to steal your mail: gmail fishing
This article does not pretend beyond originality and does not reveal any new attack vectors. I saw a serious implementation of “fake” for Google Mail and decided to warn the habrasoobschestvu.
')
Recently, an interesting letter arrived at the post office, ostensibly to confirm / cancel automatic forwarding to my inbox.
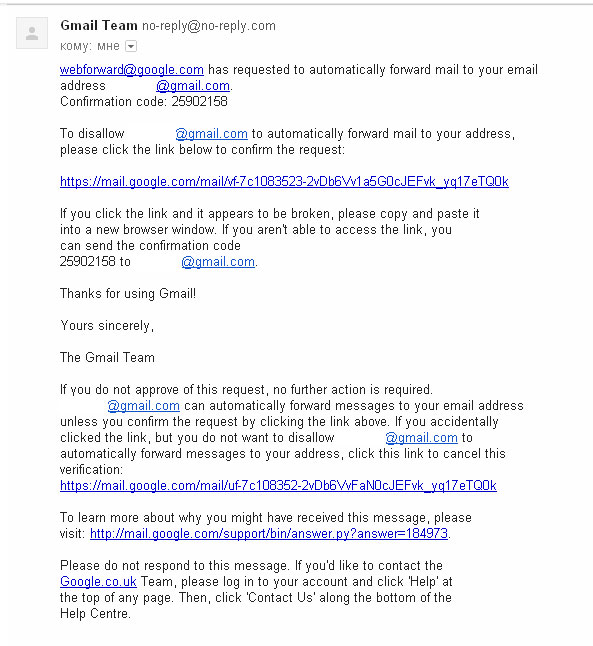
What immediately alerted:
Gmail Team no-reply @ no-reply.com googol seems to be responding from its domains.
forward to mail to webforward@google.com
myprettygooglemailaccount@gmail.com.
I did not install any shipment, and the address is not valid.
We climb into the source of the letter and observe such an interesting movie:
Delivered-To: myprettygooglemailaccount@gmail.com
Received: by 10.52.15.234 with SMTP id a10csp64285vdd;
Fri, 13 Apr 2012 17:15:49 -0700 (PDT)
Received: by 10.216.132.169 with SMTP id o41mr2024248wei.121.1334362548500;
Fri, 13 Apr 2012 17:15:48 -0700 (PDT)
Return-Path: <play8189@4003.ru>
Received: from seromailco.com ([91.220.131.22])
by mx.google.com with ESMTPS id r8si11185472weq.31.2012.04.13.17.15.47
(version = TLSv1 / SSLv3 cipher = OTHER);
Fri, 13 Apr 2012 17:15:48 -0700 (PDT)
Received-SPF: neutral (google.com: 91.220.131.22)
Authentication-Results: mx.google.com; spf = neutral (google.com: 91.220.131.22)
Received: from apache by seromailco.com with local (Exim 4.72)
(envelope from < play8189@4003.ru >)
id 1SIqpO-00026N-Vt
for myprettygooglemailaccount@gmail.com; Sat, 14 Apr 2012 02:26:59 +0200
Date: Sat, 14 Apr 2012 02:26:58 +0200
Message-Id: <E1SIqpO-00026N-Vt@seromailco.com>
To: myprettygooglemailaccount@gmail.com
Subject: =? Utf-8? B? KCM4MzUyMDgwODMpIEdtYWlsIEZvcndhcmRpbmcgQ29uZmlybWF0aW9uIC0gUmVjZWl2ZSBFbWFpbHMgZnJvbSB3ZWhAhp3p4p4AWhAh2ZSBBZZh2ZSBBZZBBBBZZBBBBZZh2GSGBBBBZZH2GSGBGZBBBFZWH2GSH2ZSBFBWFpbHMgZNBBBZF4AWH2AWZh2SB
X-PHP-Script: 4003.ru/sende/send.php for 94.228.220.68
From: =? Utf-8? B? R23QsGlsINCi0LXQsG3CrQ ==? = < No-reply@no-reply.com >
Content-type: text / html; charset = utf-8
Mime-Version: 1.0
What is there flashed: 4003.ru/sende - anonymizer.
Well well. What did they want from us? To unsubscribe, you need to follow the link:
https://mail.google.com/mail/vf-7c1083523-2vDb6Vv1a5G0cJEFvk_yq17eTQ0k which actually:
http://acc.check-googlemail.com/inbox/135410f73da242f/ServiceLogin/ServiceLogin.php?email=myprettygooglemailaccount@gmail.com If you click on the link (it is already blocked in Mozilla), then we’ll get to the phishing page with Google favicon, etc.
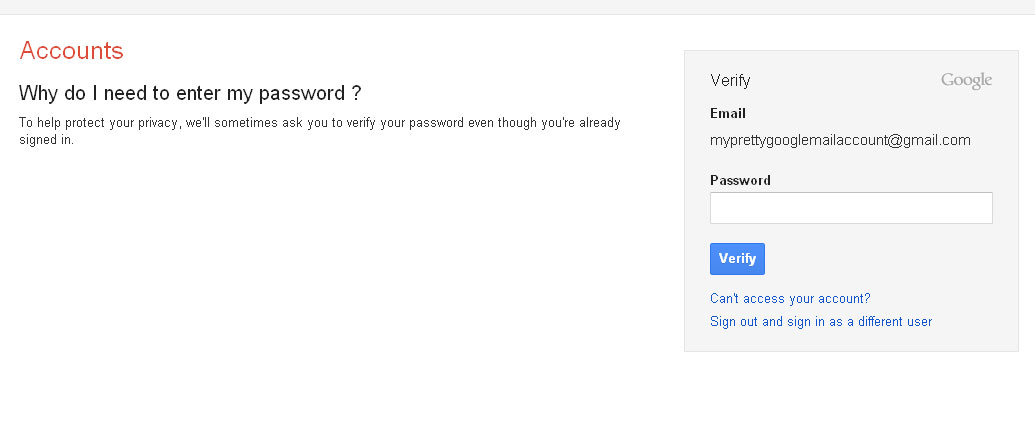
Very similar to the paranoid googol who, for any sneeze, asks for a password. If you enter a password, it will leave the attacker, and when you submit it, you will redirect to your mail (you did not leave it when you clicked the link!).
It turns out very plausible picture. Be careful.
Source: https://habr.com/ru/post/142729/
All Articles