FortNotes - online password manager
Good afternoon.
I want to share a project that I recently completed. I hope someone will come in handy.
Everyone who has used the Internet for a long time has probably accumulated a large amount of various private data, such as usernames and passwords for websites, mailboxes, servers and databases. Someone less, someone more, but everyone has such data. You can store it on scraps of paper, stickers on the monitor, in a notebook on a bedside table, or in a file on the desktop. Many people realize that this is not very safe: someone can spy or tritely lose this precious data, but usually rarely anyone tries to do something about it.
The Internet has entered our lives very tightly and it would be nice to be able to streamline and secure your data. Even if you don’t keep millions in banks and don’t worry that someone steals a password from a bank account, it doesn’t mean that losing access to mail, wm-keeper or facebook will be pleasant. Personal correspondence, business contacts, photos, secret information of a different type - all this should not be available to anyone except the owner.
FortNotes is Fort Knox for user data. The technology behind this project is BlackBox , a black box or an encrypted container. All records created on this site are immediately encrypted directly in the browser using AES (a symmetric block encryption algorithm adopted as the encryption standard by the US government) and only after that are sent to the server already encrypted. This means that no one except the data owner has access to them. Neither the interception of Internet connection data, nor the study of an encrypted container by an overly curious site administrator, will allow access to the original data. Without a user password, this would just be a meaningless jumble of characters. The black box is decrypted in real information only when entering the FortNotes site and entering a password. Thus, users do not trust the storage of their secret data to anyone: the FortNotes server stores only encrypted black boxes and nothing more, no information in the clear. Further, the user's computer and browser does not even leave the login, which is registered in the system. Absolutely everything is encrypted before being sent to the server. When data is needed, a request is sent, a crypto-container is uploaded and decryption occurs. The process is automated and transparent: only a preliminary password is required.
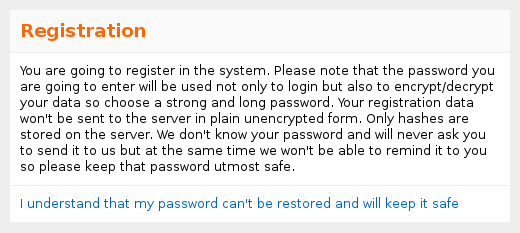
For registration in the system, only a login and password are required, which are converted into a sha256-hash before being sent to the server, which essentially makes the registration anonymous. Instead of user names and their passwords in the database are character sequences of the form "a9dc602f9d82bc6720b2b4bb016edcacf7da4b2b453a466b742da743f3cba15d". The server does not store any data that could identify users. For the same reason, the user's e-mail is not requested, so the recovery of the login and password is impossible. The high level of security imposes certain requirements: there are no backdoors, no “recovery of forgotten passwords”. This means that the loss of this password is equivalent to the loss of the entire database of secret user data. The modal registration window strongly emphasizes this:
')
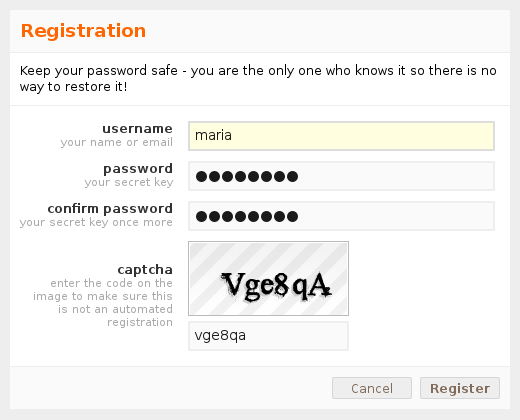
Captcha is used to verify registration:
After successful registration there is a redirect to the user section. Each time you enter this closed section, a password is requested, which is necessary for all data encryption and decryption operations. The password is stored in RAM for a limited (adjustable) time, after which it is cleared and again requested from the user:

Before clearing the password (after its storage time has expired), all data that has not yet been saved is encrypted and temporarily stored in the browser without being sent to the server. After the user enters his password, this data will be restored, and the user will be able to continue working.
Two commands are available in the upper right corner of the screen:
The main unit of information in the system is a note. Notes can be of different types. To create notes there are a dozen basic types, designed in the form of templates. With their help, in one click you can get a note like "mailbox", "site", "jabber account", "ssh / ftp server", etc. Types are not static, but more on that later. List of sample templates for notes:

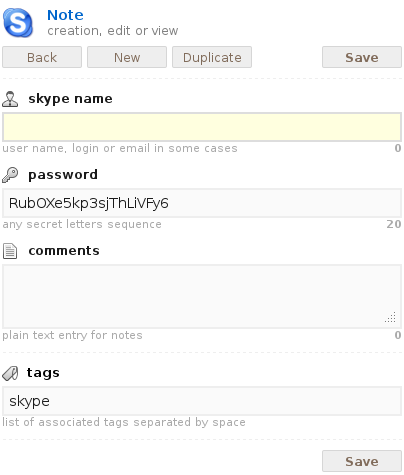
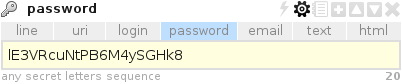
Each note consists of a set of fields ( entry ), which are the final input fields of information, and a list of tags, separated by a space. For example, a skype note consists of three fields: skype name (skype account name), password (password), comments (optional comment field) and looks like this:
Fields, in turn, are also divided by type: simple single-line text, e-mail, URI (for addresses such as sites), password, multi-line text, html.
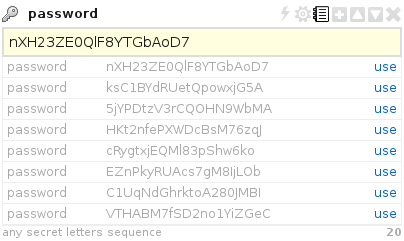
The division by types for the fields allows you to add various auxiliary operations: for example, for the password type field, the function of generating a random password of a given length becomes available;
As mentioned above, the fields in the notes are not static. In a Skype-type note, you can add a new field of any type at any time (for example, e-mail) and position it in the desired location, you can delete any existing field (restore deleted), move higher or lower, change type or just edit text field and title.
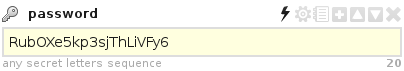
When you hover the mouse over any field, additional controls pop up:
The type of any field can be changed at any time using the appropriate item. The text of the header (if it was changed) and the data is saved.
We should also note the review of the history of changes in each field with the ability to roll back to previously saved values. Both field data and header are restored. When you select the appropriate item in the pop-up menu, a table appears with the ten most recent history values and a link to restore:
When changing the header or data of an existing note, the modified data is highlighted:
After making changes while saving a note, which fields are added visually and which are updated (plus a new field, a check mark is updated):

When editing a note, it is possible to perform a quick save using the Ctrl + Enter key combination.
In addition to saving, two special commands are available - duplicating the current note and creating a new note with the same current one, but with empty fields. It will be convenient when creating a series of similar notes.
The search on the server side is carried out with the help of tags that are listed separated by spaces in the search string. Using a search tag with a minus sign in front of it displays a list of notes where such a tag is not found. In addition to custom tags created when adding notes, there is a set of system tags for getting a list of deleted notes, notes without tags, or filtering by last access time. Such tags are available in the search bar after entering the colon character " : ". The example below shows the search result for records for the last month, where the site , work and dev tags are found, but the php tag is not found:
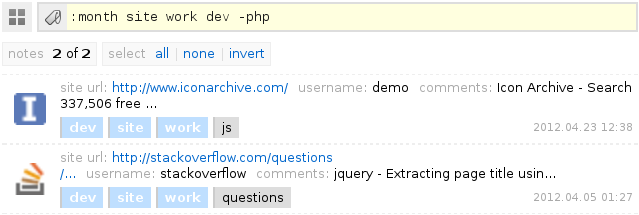
The resulting list displays all satisfying notes, where each line corresponds to one note with a brief indication of the field contents, the date of the last changes and a complete list of tags. When you click on a tag, you can add it to the search terms or remove it from the search, if it was already there. With the Ctrl key pressed simultaneously, you can add the selected tag with a minus sign to the search.
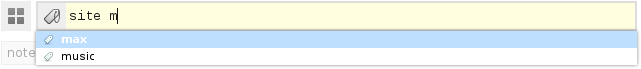
The search field supports intelligent auto-completion. Just start typing the name of the tag and immediately a list of possible options will be displayed, taking into account the tags already entered. Those. Only those tags that are found in pairs with those already indicated are displayed.
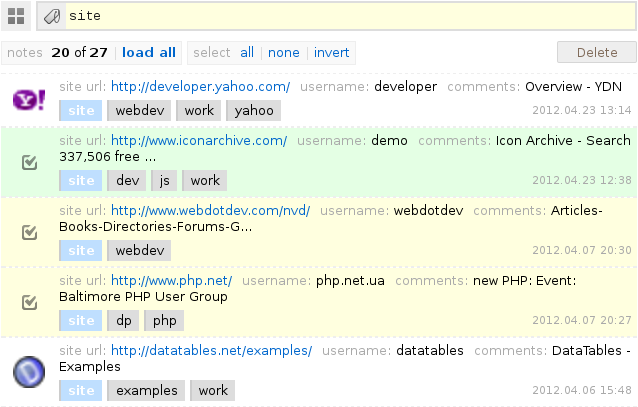
Tag search returns the first 20 notes. If you need to get a complete list, you can use the corresponding load all link. There are also links to highlight all notes, deselect and invert. To start working with a note, simply click on it with the mouse, after which the line will be marked with a check mark and highlighted in green, and the note will be opened in edit mode. It is also possible to tick one or more notes by clicking on the desired line with the Ctrl key pressed . Similar to working in file managers, selecting notes while holding down the Shift key works — it selects all the elements between two mouse clicks. You can perform general operations on selected checkmarks: delete or restore deleted ones. To switch to the deleted notes recovery mode, you can use the system tag : deleted . Also, the ability to go to the recovery is present in the tooltip that pops up immediately after deleting the selected notes.
If words that are not tags are found in the search bar, they will be used to further filter all the notes loaded in the list.
Development languages - PHP and Javascript. The second is significantly more, because the main work goes on the client side. The role of the server side is reduced to the registration / authorization and processing of AJAX requests to save / retrieve data and their search. For AES encryption on the client using a 256 bit key, the wonderful Stanford Javascript Crypto Library ( SJCL) library is used.
The client side is essentially a web application that runs without reloads, and consists of a set of js classes. The jQuery library and modules for it are actively used: jquery-autocomplete and SimpleModal . There is a system core, the main function of which comes down to storing and retrieving a password, as well as encrypting and decrypting data using this password. All other modules of the system (using the observer template) are notified when the password is received from the user, or when the storage time has expired. Depending on this, the decryption of the closed data takes place with further display, or cleaning / encryption and blocking.
All communication between the client and the server is performed by the data in the JSON format. When starting a web application, all reference data is already present on the page as JS arrays and objects. Further requests are performed using background AJAX requests.
For the server side, a micro-framework was developed with CNC support and absolutely minimal functionality. The “nothing superfluous” approach and maximum caching (general data — APC , user- JSON in gzipovannyh files on the RAMFS partition in RAM) made it possible to achieve quite impressive performance indicators. So, for example, the generation of a page of a closed user section takes 5-7ms on an old machine of the level Athlon 2800+.
Lighttpd is used as a web server. PHP-FPM as a FastCGI process manager.
Database - MySql . Access is done through its implementation of an approach similar to the MeekroDB library. The difference is in the use of PDO and the in-built validation of tables and fields. This library is allocated in a separate project . Using PDO in theory means being able to work with other databases (besides MySql), but this has not been tested.
To minimize calls to the server, all JS files are packed into one collective file all.js, and all CSS files are packed into all.css. When modifying any source file in debug mode, automatic reassembly occurs.
The system contains two shell scripts, init.sh and halt.sh, executed when the server is started and shut down, respectively:
The system is free and open to all. Moreover, it is distributed with open source, so that anyone can personally audit the code or, if necessary, install this system on their personal home or corporate server. Full source codes are in the public mercurial repository , and detailed installation instructions are available on the wiki .
Plans: add data import / export, detailed auditing, session management, settings and multilingualism.
Site address - http://fortnotes.com/
Or secure encrypted connection - https://fortnotes.com/
Project on ohloh.net .
Constructive comments and suggestions are welcome.
Pleasant and safe work :)
Update (2013.02.10):
Cleared code and documentation, editing minor bugs.
Added the ability to run using the Apache web server.
Added support for embedded PHP web server. This removes the mandatory dependency on Apache or Lighttpd.
Added support for sqlite databases. This allows you to quickly install the system without any external databases (such as Mysql).
Representative offices were created in various social networks: Google+ , Facebook , VKontakte .
Update (2013.03.30):
Another piece of minor revisions, optimizations, and updates to the source code documentation.
Activation and support of the SJCL entropy generation mechanism to improve the quality and reliability of random passwords generated.
Long-awaited backup recovery implementation. The user and password in the backup must match the login and password of the account where the recovery is performed. All old data will be deleted, and the data from the backup file will be imported.
When exporting, a more convenient name is offered, the opportunity to completely log out in the password request window has appeared.
A detailed step- by -step installation guide for the project has been added (windows system, Sqlite database, php built-in web server) and a detailed description of the architecture in English.
Update (2013.11.13):
There is a complete rework system. Emphasis on scalability, multi-platform support, ease of installation and operation. All are welcome.
Update (2018.06.05):
Docker test images of the current version are released with minor cosmetic changes and serious internal processing.
Details - github.com/fortnotes/legacy/tree/master/docker
I want to share a project that I recently completed. I hope someone will come in handy.
Everyone who has used the Internet for a long time has probably accumulated a large amount of various private data, such as usernames and passwords for websites, mailboxes, servers and databases. Someone less, someone more, but everyone has such data. You can store it on scraps of paper, stickers on the monitor, in a notebook on a bedside table, or in a file on the desktop. Many people realize that this is not very safe: someone can spy or tritely lose this precious data, but usually rarely anyone tries to do something about it.
The Internet has entered our lives very tightly and it would be nice to be able to streamline and secure your data. Even if you don’t keep millions in banks and don’t worry that someone steals a password from a bank account, it doesn’t mean that losing access to mail, wm-keeper or facebook will be pleasant. Personal correspondence, business contacts, photos, secret information of a different type - all this should not be available to anyone except the owner.
General system description
FortNotes is Fort Knox for user data. The technology behind this project is BlackBox , a black box or an encrypted container. All records created on this site are immediately encrypted directly in the browser using AES (a symmetric block encryption algorithm adopted as the encryption standard by the US government) and only after that are sent to the server already encrypted. This means that no one except the data owner has access to them. Neither the interception of Internet connection data, nor the study of an encrypted container by an overly curious site administrator, will allow access to the original data. Without a user password, this would just be a meaningless jumble of characters. The black box is decrypted in real information only when entering the FortNotes site and entering a password. Thus, users do not trust the storage of their secret data to anyone: the FortNotes server stores only encrypted black boxes and nothing more, no information in the clear. Further, the user's computer and browser does not even leave the login, which is registered in the system. Absolutely everything is encrypted before being sent to the server. When data is needed, a request is sent, a crypto-container is uploaded and decryption occurs. The process is automated and transparent: only a preliminary password is required.
Going deeper
check in
For registration in the system, only a login and password are required, which are converted into a sha256-hash before being sent to the server, which essentially makes the registration anonymous. Instead of user names and their passwords in the database are character sequences of the form "a9dc602f9d82bc6720b2b4bb016edcacf7da4b2b453a466b742da743f3cba15d". The server does not store any data that could identify users. For the same reason, the user's e-mail is not requested, so the recovery of the login and password is impossible. The high level of security imposes certain requirements: there are no backdoors, no “recovery of forgotten passwords”. This means that the loss of this password is equivalent to the loss of the entire database of secret user data. The modal registration window strongly emphasizes this:

')
Captcha is used to verify registration:

After successful registration there is a redirect to the user section. Each time you enter this closed section, a password is requested, which is necessary for all data encryption and decryption operations. The password is stored in RAM for a limited (adjustable) time, after which it is cleared and again requested from the user:

Before clearing the password (after its storage time has expired), all data that has not yet been saved is encrypted and temporarily stored in the browser without being sent to the server. After the user enters his password, this data will be restored, and the user will be able to continue working.
Two commands are available in the upper right corner of the screen:
- Lock allows you to immediately encrypt all open data, erase the password from the memory and lock the screen until a password is entered. It is important to remember that if at this moment any notes were edited and they were not saved, then with this lock, these changes will remain only in the browser and will not get to the server until the user explicitly stores the note.
- Exit performs a full logout with clearing the password from memory, deleting all user caches and sessions on the server, and then redirects to the project’s home page.
Create and edit notes
The main unit of information in the system is a note. Notes can be of different types. To create notes there are a dozen basic types, designed in the form of templates. With their help, in one click you can get a note like "mailbox", "site", "jabber account", "ssh / ftp server", etc. Types are not static, but more on that later. List of sample templates for notes:

Each note consists of a set of fields ( entry ), which are the final input fields of information, and a list of tags, separated by a space. For example, a skype note consists of three fields: skype name (skype account name), password (password), comments (optional comment field) and looks like this:

Fields, in turn, are also divided by type: simple single-line text, e-mail, URI (for addresses such as sites), password, multi-line text, html.
The division by types for the fields allows you to add various auxiliary operations: for example, for the password type field, the function of generating a random password of a given length becomes available;
As mentioned above, the fields in the notes are not static. In a Skype-type note, you can add a new field of any type at any time (for example, e-mail) and position it in the desired location, you can delete any existing field (restore deleted), move higher or lower, change type or just edit text field and title.
When you hover the mouse over any field, additional controls pop up:

The type of any field can be changed at any time using the appropriate item. The text of the header (if it was changed) and the data is saved.

We should also note the review of the history of changes in each field with the ability to roll back to previously saved values. Both field data and header are restored. When you select the appropriate item in the pop-up menu, a table appears with the ten most recent history values and a link to restore:

When changing the header or data of an existing note, the modified data is highlighted:

After making changes while saving a note, which fields are added visually and which are updated (plus a new field, a check mark is updated):

When editing a note, it is possible to perform a quick save using the Ctrl + Enter key combination.
In addition to saving, two special commands are available - duplicating the current note and creating a new note with the same current one, but with empty fields. It will be convenient when creating a series of similar notes.
Search and filtering
The search on the server side is carried out with the help of tags that are listed separated by spaces in the search string. Using a search tag with a minus sign in front of it displays a list of notes where such a tag is not found. In addition to custom tags created when adding notes, there is a set of system tags for getting a list of deleted notes, notes without tags, or filtering by last access time. Such tags are available in the search bar after entering the colon character " : ". The example below shows the search result for records for the last month, where the site , work and dev tags are found, but the php tag is not found:

The resulting list displays all satisfying notes, where each line corresponds to one note with a brief indication of the field contents, the date of the last changes and a complete list of tags. When you click on a tag, you can add it to the search terms or remove it from the search, if it was already there. With the Ctrl key pressed simultaneously, you can add the selected tag with a minus sign to the search.
The search field supports intelligent auto-completion. Just start typing the name of the tag and immediately a list of possible options will be displayed, taking into account the tags already entered. Those. Only those tags that are found in pairs with those already indicated are displayed.

Tag search returns the first 20 notes. If you need to get a complete list, you can use the corresponding load all link. There are also links to highlight all notes, deselect and invert. To start working with a note, simply click on it with the mouse, after which the line will be marked with a check mark and highlighted in green, and the note will be opened in edit mode. It is also possible to tick one or more notes by clicking on the desired line with the Ctrl key pressed . Similar to working in file managers, selecting notes while holding down the Shift key works — it selects all the elements between two mouse clicks. You can perform general operations on selected checkmarks: delete or restore deleted ones. To switch to the deleted notes recovery mode, you can use the system tag : deleted . Also, the ability to go to the recovery is present in the tooltip that pops up immediately after deleting the selected notes.
If words that are not tags are found in the search bar, they will be used to further filter all the notes loaded in the list.

Technical side
Development languages - PHP and Javascript. The second is significantly more, because the main work goes on the client side. The role of the server side is reduced to the registration / authorization and processing of AJAX requests to save / retrieve data and their search. For AES encryption on the client using a 256 bit key, the wonderful Stanford Javascript Crypto Library ( SJCL) library is used.
The client side is essentially a web application that runs without reloads, and consists of a set of js classes. The jQuery library and modules for it are actively used: jquery-autocomplete and SimpleModal . There is a system core, the main function of which comes down to storing and retrieving a password, as well as encrypting and decrypting data using this password. All other modules of the system (using the observer template) are notified when the password is received from the user, or when the storage time has expired. Depending on this, the decryption of the closed data takes place with further display, or cleaning / encryption and blocking.
All communication between the client and the server is performed by the data in the JSON format. When starting a web application, all reference data is already present on the page as JS arrays and objects. Further requests are performed using background AJAX requests.
For the server side, a micro-framework was developed with CNC support and absolutely minimal functionality. The “nothing superfluous” approach and maximum caching (general data — APC , user- JSON in gzipovannyh files on the RAMFS partition in RAM) made it possible to achieve quite impressive performance indicators. So, for example, the generation of a page of a closed user section takes 5-7ms on an old machine of the level Athlon 2800+.
Lighttpd is used as a web server. PHP-FPM as a FastCGI process manager.
Database - MySql . Access is done through its implementation of an approach similar to the MeekroDB library. The difference is in the use of PDO and the in-built validation of tables and fields. This library is allocated in a separate project . Using PDO in theory means being able to work with other databases (besides MySql), but this has not been tested.
To minimize calls to the server, all JS files are packed into one collective file all.js, and all CSS files are packed into all.css. When modifying any source file in debug mode, automatic reassembly occurs.
The system contains two shell scripts, init.sh and halt.sh, executed when the server is started and shut down, respectively:
- init.sh creates a directory for the cache (if necessary) and mounts it as RAMFS . If there is a backup of previously cached data, they are transferred to the cache. Additionally, it checks and creates (if necessary) sub cache directories responsible for different data. The required access rights are set. A database structure is generated for use in subsequent verification of table and field names. Check and create a log folder, its contents and installation rights. Preparation of collective files for JS and CSS files. Run php-fpm and lighttpd.
- halt.sh exits lighttpd and php-fpm. It backs up all cached data and disables the cache.
Finally
The system is free and open to all. Moreover, it is distributed with open source, so that anyone can personally audit the code or, if necessary, install this system on their personal home or corporate server. Full source codes are in the public mercurial repository , and detailed installation instructions are available on the wiki .
Plans: add data import / export, detailed auditing, session management, settings and multilingualism.
Site address - http://fortnotes.com/
Or secure encrypted connection - https://fortnotes.com/
Project on ohloh.net .
Constructive comments and suggestions are welcome.
Pleasant and safe work :)
Update (2013.02.10):
Cleared code and documentation, editing minor bugs.
Added the ability to run using the Apache web server.
Added support for embedded PHP web server. This removes the mandatory dependency on Apache or Lighttpd.
Added support for sqlite databases. This allows you to quickly install the system without any external databases (such as Mysql).
Representative offices were created in various social networks: Google+ , Facebook , VKontakte .
Update (2013.03.30):
Another piece of minor revisions, optimizations, and updates to the source code documentation.
Activation and support of the SJCL entropy generation mechanism to improve the quality and reliability of random passwords generated.
Long-awaited backup recovery implementation. The user and password in the backup must match the login and password of the account where the recovery is performed. All old data will be deleted, and the data from the backup file will be imported.
When exporting, a more convenient name is offered, the opportunity to completely log out in the password request window has appeared.
A detailed step- by -step installation guide for the project has been added (windows system, Sqlite database, php built-in web server) and a detailed description of the architecture in English.
Update (2013.11.13):
There is a complete rework system. Emphasis on scalability, multi-platform support, ease of installation and operation. All are welcome.
Update (2018.06.05):
Docker test images of the current version are released with minor cosmetic changes and serious internal processing.
Details - github.com/fortnotes/legacy/tree/master/docker
Source: https://habr.com/ru/post/142710/
All Articles