Do-It-Yourself: Automate Security Process Management
Use what is at hand, and do not look for something else ...
Phileas Fogg
In today's world, security is one of the fundamental factors for business development. This does not require unnecessary words! The topic of reflection here can only be the amount of investments that a business is willing to invest in building and maintaining an effective security system that guarantees protection against possible incidents.
 This question does not have a simple solution - after all, to select the right business protection strategy, it is necessary to conduct a detailed analysis, clarify goals and choose the right approach to achieve them. As a rule, the best approach for medium and large companies will be the phased implementation of the security system: starting with protecting the most critical assets, gradually expanding the scope, including the lower priority ones. Big things start small, and to get a guarantee that the security system will develop in the right direction and reach the required level of maturity by a certain date, you need to pay special attention to the processes themselves, designed to protect the company. Such processes include incident management, risk management, continuity management, access control, change control, and many others. If the company pays enough attention to the correctness of the execution of such processes, then the project to build a security system is almost doomed to success.
This question does not have a simple solution - after all, to select the right business protection strategy, it is necessary to conduct a detailed analysis, clarify goals and choose the right approach to achieve them. As a rule, the best approach for medium and large companies will be the phased implementation of the security system: starting with protecting the most critical assets, gradually expanding the scope, including the lower priority ones. Big things start small, and to get a guarantee that the security system will develop in the right direction and reach the required level of maturity by a certain date, you need to pay special attention to the processes themselves, designed to protect the company. Such processes include incident management, risk management, continuity management, access control, change control, and many others. If the company pays enough attention to the correctness of the execution of such processes, then the project to build a security system is almost doomed to success.
')
To ensure the correct execution of these processes they need to be managed. Management consists of planning, monitoring, evaluating performance, adequate support and modifications, if such a need arises. In this activity, a very important point is the interaction of people, which consists in the collection, processing, analysis of information, as well as its exchange with process implementers and other interested parties. It occupies the largest part of the process management activities.
 For medium-sized (and especially large companies), even with the initially small area of security system implementation, this represents a considerable amount of work: meetings, interviews, recording the information received, analyzing data, developing strategies and corrective measures, developing plans, monitoring activities and managing tasks the implementation of security systems and processes. A large amount of work in this area always determines a large amount of information.
For medium-sized (and especially large companies), even with the initially small area of security system implementation, this represents a considerable amount of work: meetings, interviews, recording the information received, analyzing data, developing strategies and corrective measures, developing plans, monitoring activities and managing tasks the implementation of security systems and processes. A large amount of work in this area always determines a large amount of information.
Here the question arises: how to ensure effective work with a large amount of information?
Of course, responsible employees should be trained in effective analysis techniques, focusing on learning and using best practices in process management. Here, the following solution also seems obvious: automating the processes of collecting, analyzing and interacting, creating a common information field for all participants in the processes.
To implement the latter solution, it is necessary to use (and before that - create) a special information system that:
The information system itself is not a panacea! The main work (collection, analysis, decision-making) is done by a person, provided that he has the right tool, and his time is not taken by long searches for necessary data, by copying them from one application to another, etc.
A person equipped with a specialized system has access to a common information field, which contains all the necessary information and allows you to effectively interact with other employees. In such a context, Excel tablets and Word documents do not seem to be an acceptable option.
When choosing the necessary information system, it is always necessary to make the following decision: which system is best to choose in order to guarantee the achievement of the goals set? In this case, the goal is effective management of information security processes.
Usually there are such options:
In our market there are many companies with different goals and opportunities, but very often for large and medium-sized companies the most cost-effective approach is to build and fully utilize their own system and then increase its functionality.
In my company, I have chosen for many years successfully used MS SharePoint to build a security management system.
There were such obvious prerequisites for this:
• Web-based interface is easy and clear.
• This system is already familiar and actively used by all employees.
• Easy access control
• Availability of additional components for granular access control.
• Rich functionality:
• Ability to easily integrate the system being developed with existing business process management systems based on a single information platform
• Development flexibility:
• Minimum investment
Integration of security processes with business processes is a very important point. Such integration in the framework of one information system provides another additional and, of course, a very important advantage - a portal common for the whole enterprise to exchange important production information. The list of assets of the company, employees, departments, analyzed problems, as a rule, already exists in the system, therefore, it is not necessary to spend additional resources to add functionality for managing such information.

As a result, with minimal investment, a full-fledged Infopulse Corporate Security Management System tool was built to manage such processes:
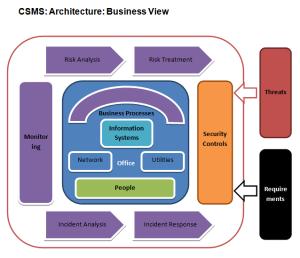
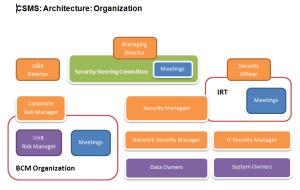
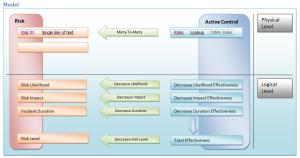
The system implements a single information field that covers the processes, systems and related data as part of enterprise security management, and also allows you to centrally document and monitor the current status of all important components of the security system.
The convenience of everyday work with a hand-built tool prompted in me a desire to share experience using the above reasoning. I hope they will be useful for my colleagues in the field of information security.
Phileas Fogg
In today's world, security is one of the fundamental factors for business development. This does not require unnecessary words! The topic of reflection here can only be the amount of investments that a business is willing to invest in building and maintaining an effective security system that guarantees protection against possible incidents.
 This question does not have a simple solution - after all, to select the right business protection strategy, it is necessary to conduct a detailed analysis, clarify goals and choose the right approach to achieve them. As a rule, the best approach for medium and large companies will be the phased implementation of the security system: starting with protecting the most critical assets, gradually expanding the scope, including the lower priority ones. Big things start small, and to get a guarantee that the security system will develop in the right direction and reach the required level of maturity by a certain date, you need to pay special attention to the processes themselves, designed to protect the company. Such processes include incident management, risk management, continuity management, access control, change control, and many others. If the company pays enough attention to the correctness of the execution of such processes, then the project to build a security system is almost doomed to success.
This question does not have a simple solution - after all, to select the right business protection strategy, it is necessary to conduct a detailed analysis, clarify goals and choose the right approach to achieve them. As a rule, the best approach for medium and large companies will be the phased implementation of the security system: starting with protecting the most critical assets, gradually expanding the scope, including the lower priority ones. Big things start small, and to get a guarantee that the security system will develop in the right direction and reach the required level of maturity by a certain date, you need to pay special attention to the processes themselves, designed to protect the company. Such processes include incident management, risk management, continuity management, access control, change control, and many others. If the company pays enough attention to the correctness of the execution of such processes, then the project to build a security system is almost doomed to success. ')
To ensure the correct execution of these processes they need to be managed. Management consists of planning, monitoring, evaluating performance, adequate support and modifications, if such a need arises. In this activity, a very important point is the interaction of people, which consists in the collection, processing, analysis of information, as well as its exchange with process implementers and other interested parties. It occupies the largest part of the process management activities.
 For medium-sized (and especially large companies), even with the initially small area of security system implementation, this represents a considerable amount of work: meetings, interviews, recording the information received, analyzing data, developing strategies and corrective measures, developing plans, monitoring activities and managing tasks the implementation of security systems and processes. A large amount of work in this area always determines a large amount of information.
For medium-sized (and especially large companies), even with the initially small area of security system implementation, this represents a considerable amount of work: meetings, interviews, recording the information received, analyzing data, developing strategies and corrective measures, developing plans, monitoring activities and managing tasks the implementation of security systems and processes. A large amount of work in this area always determines a large amount of information.Here the question arises: how to ensure effective work with a large amount of information?

Of course, responsible employees should be trained in effective analysis techniques, focusing on learning and using best practices in process management. Here, the following solution also seems obvious: automating the processes of collecting, analyzing and interacting, creating a common information field for all participants in the processes.
To implement the latter solution, it is necessary to use (and before that - create) a special information system that:
- provide information sharing with users of such a system
- automates work with information
The information system itself is not a panacea! The main work (collection, analysis, decision-making) is done by a person, provided that he has the right tool, and his time is not taken by long searches for necessary data, by copying them from one application to another, etc.

A person equipped with a specialized system has access to a common information field, which contains all the necessary information and allows you to effectively interact with other employees. In such a context, Excel tablets and Word documents do not seem to be an acceptable option.
When choosing the necessary information system, it is always necessary to make the following decision: which system is best to choose in order to guarantee the achievement of the goals set? In this case, the goal is effective management of information security processes.
Usually there are such options:
- Find and use an available free system
Such systems exist, but there are certain drawbacks: limited functionality, non-guaranteed reliability, execution errors, etc. In the future, there is also a need for programmers to help integrate with other information systems that are already implemented in the company. - Develop such a system from scratch yourself
For this, we need our own qualified architects, programmers, engineers, and specialists in the applied field - in information security. In this case, it is often beneficial to attract another company that has the necessary competencies and specializes in developing business applications. Of course, this requires additional investments. But such a choice can also be justified. - Use a system that is already in production
This is a well-known approach based on the principle of “use what is at hand and do not look for something else for yourself,” which does not require additional investments to acquire the system. A commonly used system is not fully loaded. So, there is an opportunity to increase the utilization of already paid resources. In the opposite case, when the system is loaded, it can be scaled to the required capacity, which is cheaper than purchasing new systems. This approach allows to achieve a higher level of integration with existing processes that are automated in this system, with less investment. - Buy a ready-made system
This approach solves the problem, but usually it is the most expensive solution. Ready for the introduction of the system of the class under discussion for a long time developed by foreign developers and have a rich variety of functionality. This means that the cost of such systems can not be small. For very large foreign companies that have been working with security processes for more than a decade, wide functionality is the main criterion, which is why they are the main customers of such systems. But companies in the Russian and Ukrainian market, which have just begun to implement their security system, as a rule, need only the most minimal set of necessary functions that will actually be used with benefit. In the CIS market, the high cost of such systems, which have excess functionality that will not be used by the buyer in the next 5 years, makes such serious investments questionable.
In our market there are many companies with different goals and opportunities, but very often for large and medium-sized companies the most cost-effective approach is to build and fully utilize their own system and then increase its functionality.
In my company, I have chosen for many years successfully used MS SharePoint to build a security management system.
There were such obvious prerequisites for this:
• Web-based interface is easy and clear.
• This system is already familiar and actively used by all employees.
• Easy access control
• Availability of additional components for granular access control.
• Rich functionality:
- full data search (FAST Search)
- business intelligence (Excel Services, PerformancePoint, Visio, Web Parts, Web Diagrams, Filter Framework)
- Office Client Integration (Business Connectivity Services)
• Ability to easily integrate the system being developed with existing business process management systems based on a single information platform
• Development flexibility:
- management system development can be done independently
- if necessary, with the involvement of programmers and subject experts in the field of information security and process optimization
• Minimum investment
Integration of security processes with business processes is a very important point. Such integration in the framework of one information system provides another additional and, of course, a very important advantage - a portal common for the whole enterprise to exchange important production information. The list of assets of the company, employees, departments, analyzed problems, as a rule, already exists in the system, therefore, it is not necessary to spend additional resources to add functionality for managing such information.

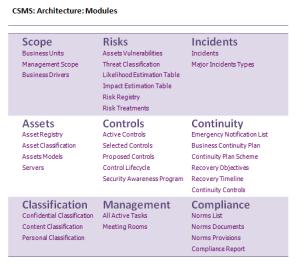
As a result, with minimal investment, a full-fledged Infopulse Corporate Security Management System tool was built to manage such processes:
- Accounting information assets
- Incident management
- Corporate risk management
- Business Continuity
- Management of personal data protection system
- Security Control Management
- Security Compliance
- Security Task Management
- Security Knowledge Management
- Security communication
The system implements a single information field that covers the processes, systems and related data as part of enterprise security management, and also allows you to centrally document and monitor the current status of all important components of the security system.
The convenience of everyday work with a hand-built tool prompted in me a desire to share experience using the above reasoning. I hope they will be useful for my colleagues in the field of information security.
Source: https://habr.com/ru/post/142422/
All Articles