Pentest on steroids. Automating the process
With this topic, I spoke at CodeFest. And here I will retell in words what, how and why.

The report is rather superficial and requires almost no qualification in the field of information security. It was designed for the target audience (web developers, testers (not penetration), system administrators, etc.). It's pretty simple: several utilities, launched, waited, parse the report.
Video invitation to the conference:
')
Pentest ( penetration testing ) - assessment of the security of the end node or resource by means and methods of intruders © Wiki . Differences from hacking in that (hacking) the task to find any vulnerability for the required purposes, unleash and exploit. Here is a comprehensive analysis of the goal.
The goal is to automate the penetration testing of a network resource using a black box strategy, obtaining objective results without spending a cent on software.
We divide the test into 2 stages:
We will look for vulnerabilities, check out exploits that have come out, look for “weak” accounts, configuration errors, and just human negligence.

Armitage is a GUI to Metasploit Framework and Nmap. Visualizes targets, collects data, allows to simplify the process ofhacking pentest as a whole.
To imagine more clearly what is at stake, here is the screen:
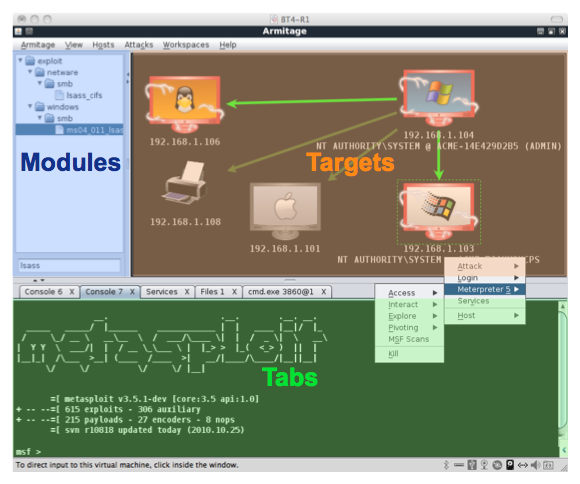
Modules (blue) - selection of exploits and post-exploits (they are applied already after the session has been established. For example, to get a dump of configs).
Targets (orange) - in fact, the goal. Depending on the status of the target, its icon changes. If you just added the necessary host and nothing is known about it, there will be just a “black” monitor or an equipment icon. If you managed to install the OS - the OS icon will appear. And the “last” state — an icon in a red frame with lightning — one of the exploits worked, it was possible to establish a shell session.
Tabs (green) - the current task activity console
Let's go to the process.
After the completion of the Hail Mary module, two results await us. Or the exploit (s) worked (s) and the session (s) was created (s)
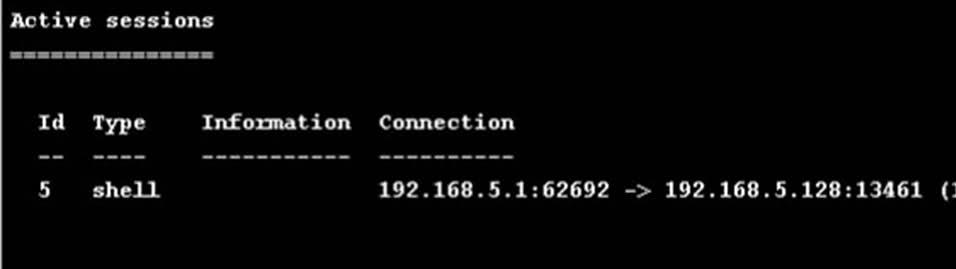
Or not

After checking the launched network services, a test for resistance to public- exploit can also check the default / common accounts. To do this, select the Login -> service class -> check all credentials -> Launch checkbox in the menu.
Armitage , Metasploit Framework is a part of Metasploit, which can be downloaded here . The moment: after installation, just 1 time start the console of the framework and close it (initialization of the initial data). After that, start Armitage and allow it to start the metasploit RPC server.
Moment. I told about Nikto and Skipfish in the article Review of free tools for pentest web-resources and not only v2
Nikto is a perl utility to search for gaps like undeleted files (/1.php / info.php), availability of database management scripts (phpmyadmin, phppgadmin, etc.), and simply vulnerable scripts. This is pretty tight for the latter, since the check is just sending the required HTTP request and looks at the response code (404/200), and not that the script is really susceptible to some kind of exploit already released.
PS In fact, it has not been updated for a long time, you need to look for a replacement (or modify it) ... For now, only paid analogs are still in the know.
Product Page - www.cirt.net/nikto2
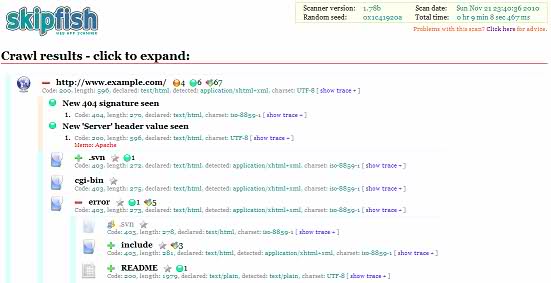
skipfish
Web Script Scanner for vulnerabilities from Google (now not only Michal Zalewski works on it). Looks for all that you can, how much you can (it was almost 5 days), eats traffic and as a result generates a report in html5. Consider, I’ve put a server to them a couple of times, causing a denial of service, overflowing / tmp (php created sessions with each request).
Source codes are downloaded here , and collected under win can be downloaded here (mentioned in this article).
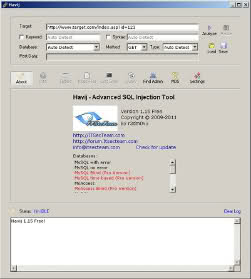 Havij - finds and unwinds SQL injections. In general, a piece must have, works clearly, quickly, bypasses some filters (although it was a case, one trivial WAF did not bypass, was tested on the CTF in this task). There are two versions - paid and free. Differ in functionality. And one of the most necessary features is the search for an injection in a parameter with a CNC, such as
Havij - finds and unwinds SQL injections. In general, a piece must have, works clearly, quickly, bypasses some filters (although it was a case, one trivial WAF did not bypass, was tested on the CTF in this task). There are two versions - paid and free. Differ in functionality. And one of the most necessary features is the search for an injection in a parameter with a CNC, such as
site.com/users/ sql_inj / topics
which is not in the free version. There is nothing more to tell, the program has a GUI, everything is extremely clear and convenient :)
You can download it here.
1337day.com / exploit-db.com
Mainly intended in situations where distributed scripts are found on the target resource. We go to the sites above and look for exploits for them, and in turn launch (a kind of Hail Mary from Armitage). It is worth considering the moment that plugins are more often vulnerable to scripts than scripts themselves.
Also, when analyzing the web, it can happen that there is a “neighboring” vulnerable application, and through it you can get access to the analyzer and merge the same database, infect it with a virus or perform a deface.
Tulsa nemerenno, it makes no sense to list the top-sec-list , but some “combines” can not be called. True, they already indirectly relate to our topic (remember about 0 cents for software?), But you can try to get the Shareware version.
MaxPatrol / XSpider
Domestic products from the company Positive Technologies , whose employees also write on Habrahabr. XSpider (7.8) is a stripped-down version of MaxPatrol. Practically has nothing in common with previous versions in the 7th branch (it’s strange that they didn’t change the major version, because there is every reason for that). A webinar about XSpider 7.8 (from Oleg Matykov, head of design solutions at Positive Technologies) can be found here ( pdf ).
In general, I would like to say a few words about the new XSpider. As a minus, I would have brought out the interface, it was too overloaded and ill-conceived (IMHO). But, of course, we need something different from the product, this scan includes almost the entire article above, excluding some points (for example, skipfish self-educates, and the more often you launch it, the more its dictionary), though this is compensated just head over with constant new product builds. He himself is crammed, perepichkan well, just with everything you can. Dictionaries for bruteforce also pleased. In general, I somehow recently managed to find a vulnerability on a resource (one of the most popular in runet), about which I heard only briefly and no other scanner found it. Shareware version with restrictions on the number of hosts can be obtained by contacting the PT sales department, and already try out on their resources.
Acuentix
Web scanner, easy to use for beginners, very intuitive interface. The full version can also be asked from the sales department, they are very responsive. Just keep in mind that later they just flood you with mail - “how do you like our product?”, “Do not want to buy?”, Etc.
Nessus (OpenVAS)
Nessus and its free analog OpenVAS. I would call their exploit machines :) Nessus home-version is free, and OpenVAS is free.

Of course, the hands, manual analysis has not been canceled. It directly depends on the hands and knowledge of the verifier, a little on luck, and also a little on the “energy hacking”, about which you will not find articles anywhere. But this is not the topic of our article (report).
Perfect case

This, of course, is a statistical code analysis. I usually do it in regular intervals (although I did it 2 times in my life, it is a painfully time-consuming process and not always possible), such as grep -nr “exec” ./ and analyzing the result obtained. Although there are scripts for this too, they are usually not applicable, as they are mostly outdated and intended for projects not on frameworks (the times when they wrote without them are over).
Probably, even more experience using utilities is higher (echoes from my history of the beginning of 2011)
1. Blackbox, the whole site is checked, such things as CSRF / XSS are found, but nothing like what could “tangle” the resource completely.
Armitage-> Host-> Login-> ftp-> check all credentials
And there is anonymous: anonymous , looking by mistake in / var / www
2. It seems that I killed 5 days then, leaving the PC only for sleep and food. CSRF / XSS / phpmyadmin , most likely installed by the package manager, since it was in lower case and written in Apache aliases (respectively, the administrator did not see this script in public html). PMA invulnerable (the version was vulnerable, but there were not those conditions). And nothing ... already upset :) Skipfish fell off (just the case with a DOS resource due to scanning). Resource raised, skipfish scans again and finds a brut ...
site / scripts / config.ini
Bingo! .ini file, which is given to the Apache as plain text with the configs to connect to the database! As it was learned later, it was used for some cron-script. Use in mistakenly supplied PMA.
PS As the media says, some of the tools above use Anonymous in their affairs .
I have it all. As a bonus presentation
And demo using Havij and Armitage (I advise to view) .
Anyone who mastered - I shake your hand :)
upd 05/25/2012: speech record added

The report is rather superficial and requires almost no qualification in the field of information security. It was designed for the target audience (web developers, testers (not penetration), system administrators, etc.). It's pretty simple: several utilities, launched, waited, parse the report.
Video invitation to the conference:
')
Pentest
Pentest ( penetration testing ) - assessment of the security of the end node or resource by means and methods of intruders © Wiki . Differences from hacking in that (hacking) the task to find any vulnerability for the required purposes, unleash and exploit. Here is a comprehensive analysis of the goal.
What are we doing?
The goal is to automate the penetration testing of a network resource using a black box strategy, obtaining objective results without spending a cent on software.
Testing stages
We divide the test into 2 stages:
- Testing network services
- Testing web applications (applications)
We will look for vulnerabilities, check out exploits that have come out, look for “weak” accounts, configuration errors, and just human negligence.
Let's go!

Part 1. Network services - Armitage (nmap + msf)
Armitage is a GUI to Metasploit Framework and Nmap. Visualizes targets, collects data, allows to simplify the process of

To imagine more clearly what is at stake, here is the screen:

Modules (blue) - selection of exploits and post-exploits (they are applied already after the session has been established. For example, to get a dump of configs).
Targets (orange) - in fact, the goal. Depending on the status of the target, its icon changes. If you just added the necessary host and nothing is known about it, there will be just a “black” monitor or an equipment icon. If you managed to install the OS - the OS icon will appear. And the “last” state — an icon in a red frame with lightning — one of the exploits worked, it was possible to establish a shell session.
Tabs (green) - the current task activity console
Let's go to the process.
- Add a host (Hosts -> Add Hosts)
- Click on it right, Scan . At this stage, not the above mentioned Nmap is started, but the port scanning module built into metasploit. But you can also use Nmap for this task.
- Attacks -> Find Attacks . At this step, a search is made for available exploits for the services found (a match occurs in open ports).
- Attacks -> Hail Mary . This is a module to launch exploits one at a time from the step above. Runs an exploit and waits for a reverse connection. Note that for this your IP must be “white”.
- We are waiting for the completion of the operation. The process goes like this
After the completion of the Hail Mary module, two results await us. Or the exploit (s) worked (s) and the session (s) was created (s)

Or not

After checking the launched network services, a test for resistance to public- exploit can also check the default / common accounts. To do this, select the Login -> service class -> check all credentials -> Launch checkbox in the menu.
Armitage , Metasploit Framework is a part of Metasploit, which can be downloaded here . The moment: after installation, just 1 time start the console of the framework and close it (initialization of the initial data). After that, start Armitage and allow it to start the metasploit RPC server.
Part 2. Web
- Nikto
- Skipfish
- Havij
- 1337day.com, exploit-db.com
Moment. I told about Nikto and Skipfish in the article Review of free tools for pentest web-resources and not only v2
Nikto is a perl utility to search for gaps like undeleted files (/1.php / info.php), availability of database management scripts (phpmyadmin, phppgadmin, etc.), and simply vulnerable scripts. This is pretty tight for the latter, since the check is just sending the required HTTP request and looks at the response code (404/200), and not that the script is really susceptible to some kind of exploit already released.
PS In fact, it has not been updated for a long time, you need to look for a replacement (or modify it) ... For now, only paid analogs are still in the know.

Product Page - www.cirt.net/nikto2
skipfish
Web Script Scanner for vulnerabilities from Google (now not only Michal Zalewski works on it). Looks for all that you can, how much you can (it was almost 5 days), eats traffic and as a result generates a report in html5. Consider, I’ve put a server to them a couple of times, causing a denial of service, overflowing / tmp (php created sessions with each request).
Source codes are downloaded here , and collected under win can be downloaded here (mentioned in this article).

 Havij - finds and unwinds SQL injections. In general, a piece must have, works clearly, quickly, bypasses some filters (although it was a case, one trivial WAF did not bypass, was tested on the CTF in this task). There are two versions - paid and free. Differ in functionality. And one of the most necessary features is the search for an injection in a parameter with a CNC, such as
Havij - finds and unwinds SQL injections. In general, a piece must have, works clearly, quickly, bypasses some filters (although it was a case, one trivial WAF did not bypass, was tested on the CTF in this task). There are two versions - paid and free. Differ in functionality. And one of the most necessary features is the search for an injection in a parameter with a CNC, such assite.com/users/ sql_inj / topics
which is not in the free version. There is nothing more to tell, the program has a GUI, everything is extremely clear and convenient :)
You can download it here.
1337day.com / exploit-db.com
Mainly intended in situations where distributed scripts are found on the target resource. We go to the sites above and look for exploits for them, and in turn launch (a kind of Hail Mary from Armitage). It is worth considering the moment that plugins are more often vulnerable to scripts than scripts themselves.
Also, when analyzing the web, it can happen that there is a “neighboring” vulnerable application, and through it you can get access to the analyzer and merge the same database, infect it with a virus or perform a deface.
What else?
Tulsa nemerenno, it makes no sense to list the top-sec-list , but some “combines” can not be called. True, they already indirectly relate to our topic (remember about 0 cents for software?), But you can try to get the Shareware version.
MaxPatrol / XSpider
Domestic products from the company Positive Technologies , whose employees also write on Habrahabr. XSpider (7.8) is a stripped-down version of MaxPatrol. Practically has nothing in common with previous versions in the 7th branch (it’s strange that they didn’t change the major version, because there is every reason for that). A webinar about XSpider 7.8 (from Oleg Matykov, head of design solutions at Positive Technologies) can be found here ( pdf ).
In general, I would like to say a few words about the new XSpider. As a minus, I would have brought out the interface, it was too overloaded and ill-conceived (IMHO). But, of course, we need something different from the product, this scan includes almost the entire article above, excluding some points (for example, skipfish self-educates, and the more often you launch it, the more its dictionary), though this is compensated just head over with constant new product builds. He himself is crammed, perepichkan well, just with everything you can. Dictionaries for bruteforce also pleased. In general, I somehow recently managed to find a vulnerability on a resource (one of the most popular in runet), about which I heard only briefly and no other scanner found it. Shareware version with restrictions on the number of hosts can be obtained by contacting the PT sales department, and already try out on their resources.
Acuentix
Web scanner, easy to use for beginners, very intuitive interface. The full version can also be asked from the sales department, they are very responsive. Just keep in mind that later they just flood you with mail - “how do you like our product?”, “Do not want to buy?”, Etc.
Nessus (OpenVAS)
Nessus and its free analog OpenVAS. I would call their exploit machines :) Nessus home-version is free, and OpenVAS is free.
And what else?

Of course, the hands, manual analysis has not been canceled. It directly depends on the hands and knowledge of the verifier, a little on luck, and also a little on the “energy hacking”, about which you will not find articles anywhere. But this is not the topic of our article (report).
Perfect case

This, of course, is a statistical code analysis. I usually do it in regular intervals (although I did it 2 times in my life, it is a painfully time-consuming process and not always possible), such as grep -nr “exec” ./ and analyzing the result obtained. Although there are scripts for this too, they are usually not applicable, as they are mostly outdated and intended for projects not on frameworks (the times when they wrote without them are over).
Examples
Probably, even more experience using utilities is higher (echoes from my history of the beginning of 2011)
1. Blackbox, the whole site is checked, such things as CSRF / XSS are found, but nothing like what could “tangle” the resource completely.
Armitage-> Host-> Login-> ftp-> check all credentials
And there is anonymous: anonymous , looking by mistake in / var / www
2. It seems that I killed 5 days then, leaving the PC only for sleep and food. CSRF / XSS / phpmyadmin , most likely installed by the package manager, since it was in lower case and written in Apache aliases (respectively, the administrator did not see this script in public html). PMA invulnerable (the version was vulnerable, but there were not those conditions). And nothing ... already upset :) Skipfish fell off (just the case with a DOS resource due to scanning). Resource raised, skipfish scans again and finds a brut ...
site / scripts / config.ini
Bingo! .ini file, which is given to the Apache as plain text with the configs to connect to the database! As it was learned later, it was used for some cron-script. Use in mistakenly supplied PMA.
PS As the media says, some of the tools above use Anonymous in their affairs .
I have it all. As a bonus presentation
And demo using Havij and Armitage (I advise to view) .
Anyone who mastered - I shake your hand :)
upd 05/25/2012: speech record added
Source: https://habr.com/ru/post/141803/
All Articles