Blackhole + CVE-2012-0507 = Carberp
This week, the famous Blackhole exploit kit has been updated to version 1.2.3, and a new exploit for Java has been introduced to the vulnerability CVE-2012-0507 ( Java / Exploit.CVE-2012-0507 ). The first to draw public attention to the relevance of this vulnerability was Microsoft, which published a message in its blog about an interesting way of executing Java code outside of the JRE (Java Runtime Environment) sandbox.
The first mention of a combat exploit for this vulnerability came from the company Immunity, which released a special module for its product Immunity CANVAS in early March 7/03/2012. This vulnerability was closed on February 15 as part of a critical update from Oracle. Just late yesterday, at the time of this publication, a public exploit appeared for the CVE-2012-0507 as part of the Metasploit Framework. Separately, it is worth noting its cross-platform and the possibility of operation on Windows, Linux, Solaris and OSX systems (Apple's security update appeared yesterday). The latter is particularly interesting in light of the increase in the number of malicious programs for it, spreading also through the exploitation of Java vulnerabilities. The exploit from Metasploit Framework looks very similar to the one that was found in the updated Blackhole and it seems that it was ripped mostly from there ...
Recently, I often wrote about exploits for Java and they are really the last year to be the most disruptive in mass distribution of malware incidents. The developers of exploit kits, such as Blackhole, use only the so-called 1-day vulnerabilities, i.e. already containing the official fix from the developers. Because the use of 0-day is too expensive for their purposes and does not pay for itself at all, but there are exceptions when 0-day hits public with PoC. The use of the zero-day vulnerability at the moment can most often be seen in targeted attacks. By the way, a rather entertaining post about the prices for 0-day and the resets' karma can be read here .
')
Let's return to our exploit, this week again the spread of Win32 / TrojanDownloader.Carberp through popular web resources was noticed, through the introduction of iFrame constructs for redirection to a resource with a set of exploits.
First we came across the resource lifenews.ru, which contained the following iFrame:

As can be seen from the embedded code, the attack was immediately CVE-2012-0507, and the domain name on which Blackhole was located is very similar to the name of the attacked web resource. The result of executing code in iFrame can even be seen visually on a modified original page.
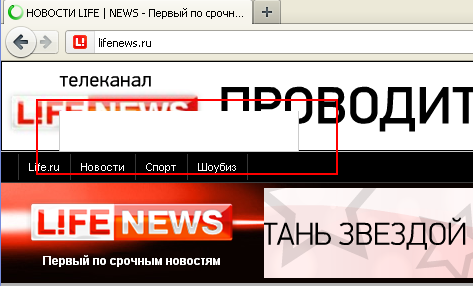
After that, the old, but not good, page of waiting is displayed and it is at this moment that the active stage of operation takes place.
A similar attack was seen on the web resource izvestia.ru and a modification from the Win32 / TrojanDownloader.Carberp family was also installed. In general, the first Java / Exploit.CVE-2012-0507 operating detections were seen closer to mid-March.
The full event log when you visit the modified page of the livenews.ru web resource looks like this:

In both cases, the infection occurred when visiting the URL of the form:
hxxp: //izvestia.ru/banners/index.php? p = 55
hxxp: //lifenews.ru/banners/index.php? p = 2
This suggests an idea of infection through the banner network used on both resources. The address at which the redirection occurred also looked the same in both cases.
By the way, the reader may have a logical question, but what about the recent press noise about the detention of a group of cybercriminals spreading Win32 / TrojanDownloader.Carberp and earning fraud in RBS systems. Everything was rightly arrested eight people who were different parts of the criminal network and were only one group that worked with Carberp. But after all, others remained at large and naturally a miracle did not happen and they didn’t roll their activities.
But let's still return to the exploit on the vulnerability CVE-2012-0507, it is he who represents the greatest interest of all this attack (Carberp was previously known to us modifications and only repacked to bypass detection). The vulnerability is hidden in the implementation of the class AtomicReferenceArray, in which there is an incorrect check for belonging to the type Object []. This vulnerability belongs to the so-called “Type Confusion Vulnerabilities” class, before such vulnerabilities were encountered at the bytecode verifier level, but now they are already closed and the conflict is directly in the Java API. All this allows you to perform a specially prepared applet or class outside the sandbox JRE.
The object structure in Java / Exploit.CVE-2012-0507 is as follows:

The init () method of the Ner class creates an object of type AtomicReferenceArray to execute code outside the sandbox.

In the next step, the doWork () method from the Hal class is executed; it is through this method that the class code is created, which later will be executed outside the sandbox.

The class code that should be executed outside the sandbox is encrypted with a simple permutable encryption algorithm and decrypted before execution, which eventually results in DownloadAndExec, which already outside the isolated environment downloads the Carberp Trojan in the% TEMP% \ vdsh89 directory \ gyu <file_number> and executes it.

To counteract the detection of antivirus products, the code encryption algorithm is constantly changing, which downloads the payload and obfuscation of string constants.
I think this year we will return again and again to the topic of exploiting vulnerabilities for the Java platform and this is not the last vulnerability for it.
study author: matrosov
The first mention of a combat exploit for this vulnerability came from the company Immunity, which released a special module for its product Immunity CANVAS in early March 7/03/2012. This vulnerability was closed on February 15 as part of a critical update from Oracle. Just late yesterday, at the time of this publication, a public exploit appeared for the CVE-2012-0507 as part of the Metasploit Framework. Separately, it is worth noting its cross-platform and the possibility of operation on Windows, Linux, Solaris and OSX systems (Apple's security update appeared yesterday). The latter is particularly interesting in light of the increase in the number of malicious programs for it, spreading also through the exploitation of Java vulnerabilities. The exploit from Metasploit Framework looks very similar to the one that was found in the updated Blackhole and it seems that it was ripped mostly from there ...
Recently, I often wrote about exploits for Java and they are really the last year to be the most disruptive in mass distribution of malware incidents. The developers of exploit kits, such as Blackhole, use only the so-called 1-day vulnerabilities, i.e. already containing the official fix from the developers. Because the use of 0-day is too expensive for their purposes and does not pay for itself at all, but there are exceptions when 0-day hits public with PoC. The use of the zero-day vulnerability at the moment can most often be seen in targeted attacks. By the way, a rather entertaining post about the prices for 0-day and the resets' karma can be read here .
')
Let's return to our exploit, this week again the spread of Win32 / TrojanDownloader.Carberp through popular web resources was noticed, through the introduction of iFrame constructs for redirection to a resource with a set of exploits.
First we came across the resource lifenews.ru, which contained the following iFrame:

As can be seen from the embedded code, the attack was immediately CVE-2012-0507, and the domain name on which Blackhole was located is very similar to the name of the attacked web resource. The result of executing code in iFrame can even be seen visually on a modified original page.

After that, the old, but not good, page of waiting is displayed and it is at this moment that the active stage of operation takes place.

A similar attack was seen on the web resource izvestia.ru and a modification from the Win32 / TrojanDownloader.Carberp family was also installed. In general, the first Java / Exploit.CVE-2012-0507 operating detections were seen closer to mid-March.
The full event log when you visit the modified page of the livenews.ru web resource looks like this:

In both cases, the infection occurred when visiting the URL of the form:
hxxp: //izvestia.ru/banners/index.php? p = 55
hxxp: //lifenews.ru/banners/index.php? p = 2
This suggests an idea of infection through the banner network used on both resources. The address at which the redirection occurred also looked the same in both cases.
By the way, the reader may have a logical question, but what about the recent press noise about the detention of a group of cybercriminals spreading Win32 / TrojanDownloader.Carberp and earning fraud in RBS systems. Everything was rightly arrested eight people who were different parts of the criminal network and were only one group that worked with Carberp. But after all, others remained at large and naturally a miracle did not happen and they didn’t roll their activities.
But let's still return to the exploit on the vulnerability CVE-2012-0507, it is he who represents the greatest interest of all this attack (Carberp was previously known to us modifications and only repacked to bypass detection). The vulnerability is hidden in the implementation of the class AtomicReferenceArray, in which there is an incorrect check for belonging to the type Object []. This vulnerability belongs to the so-called “Type Confusion Vulnerabilities” class, before such vulnerabilities were encountered at the bytecode verifier level, but now they are already closed and the conflict is directly in the Java API. All this allows you to perform a specially prepared applet or class outside the sandbox JRE.
The object structure in Java / Exploit.CVE-2012-0507 is as follows:

The init () method of the Ner class creates an object of type AtomicReferenceArray to execute code outside the sandbox.

In the next step, the doWork () method from the Hal class is executed; it is through this method that the class code is created, which later will be executed outside the sandbox.

The class code that should be executed outside the sandbox is encrypted with a simple permutable encryption algorithm and decrypted before execution, which eventually results in DownloadAndExec, which already outside the isolated environment downloads the Carberp Trojan in the% TEMP% \ vdsh89 directory \ gyu <file_number> and executes it.

To counteract the detection of antivirus products, the code encryption algorithm is constantly changing, which downloads the payload and obfuscation of string constants.
I think this year we will return again and again to the topic of exploiting vulnerabilities for the Java platform and this is not the last vulnerability for it.
study author: matrosov
Source: https://habr.com/ru/post/141365/
All Articles