Injection of Excel Formulas in Google Docs
You all probably know about Google’s program to encourage information security researchers to provide information on weaknesses on Google’s web resources. We also managed to participate in this program. Here is a little story from me and Lesha Sintsov d00kie .
Once we really needed to do a small survey, and it was decided to use Google Docs as a platform for the questionnaire.
In Google Docs, there is an object such as Google Forms, and it is used, as the name implies, to create all sorts of forms, surveys and questionnaires.

')
After creating a form, as a rule, a link to it is published on the Internet or distributed to people who need to complete a survey.
This is how the form looks for the fill:

And so the form creator sees the answers to the questions:

It seems to me that any web searcher at the sight of the form instinctively inserts there ', ",> and other interesting characters :)
We also tried, however, as expected, everything was encoding and filtering.
Hmm ... and after all the entire user input is inserted into the Excel spreadsheet, why not try to inject some formula?
Formulas in Excel begin with the symbol "=".
OK, we try.

Failure. Sly Google inserts a space character in front of the "=" sign, which makes the formula look like simple text in a cell.
How to remove the gap? Very simple: use backspace :)
% 08 - Hex-code of the backspace key

Accordingly, in the form field we write:
% 08 = 1 + 2 + C3
And voila!

The formula is perfectly inserted into the table.
It only remained to come up with an interesting and practical vector for such a kind of injection. Then Google Functions came to help:
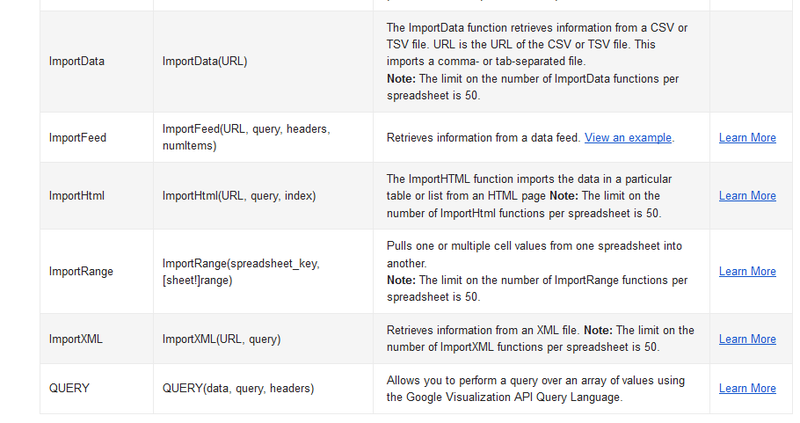
With the help of Google Functions, it became possible to perform queries for any domains, and insert the results of the query into the specified cell.
Thus, such an attack vector has developed:
1) In cell A1, we place critical user data (or they are already located there)
2) in the cell Z31337 insert the formula that will make a GET request to chipik_site.com/secret_data_in_base64_from_A1
3) Read webserver logs, get data from cells
...
4) Profit!
Having described the bug and the possible attack vector to the guys from the Google Security Team, we very soon received the following letter:

and a little later saw their names in the Google Hall of Fame :

And finally - a small Google Hack;)

Once we really needed to do a small survey, and it was decided to use Google Docs as a platform for the questionnaire.
In Google Docs, there is an object such as Google Forms, and it is used, as the name implies, to create all sorts of forms, surveys and questionnaires.

')
After creating a form, as a rule, a link to it is published on the Internet or distributed to people who need to complete a survey.
This is how the form looks for the fill:

And so the form creator sees the answers to the questions:

It seems to me that any web searcher at the sight of the form instinctively inserts there ', ",> and other interesting characters :)
We also tried, however, as expected, everything was encoding and filtering.
Hmm ... and after all the entire user input is inserted into the Excel spreadsheet, why not try to inject some formula?
Formulas in Excel begin with the symbol "=".
OK, we try.

Failure. Sly Google inserts a space character in front of the "=" sign, which makes the formula look like simple text in a cell.
How to remove the gap? Very simple: use backspace :)
% 08 - Hex-code of the backspace key

Accordingly, in the form field we write:
% 08 = 1 + 2 + C3
And voila!

The formula is perfectly inserted into the table.
It only remained to come up with an interesting and practical vector for such a kind of injection. Then Google Functions came to help:

With the help of Google Functions, it became possible to perform queries for any domains, and insert the results of the query into the specified cell.
Thus, such an attack vector has developed:
1) In cell A1, we place critical user data (or they are already located there)
2) in the cell Z31337 insert the formula that will make a GET request to chipik_site.com/secret_data_in_base64_from_A1
3) Read webserver logs, get data from cells
...
4) Profit!
Having described the bug and the possible attack vector to the guys from the Google Security Team, we very soon received the following letter:

and a little later saw their names in the Google Hall of Fame :

And finally - a small Google Hack;)

Source: https://habr.com/ru/post/140882/
All Articles