Overview of vulnerabilities in 2011: Opera on horseback, Adobe at risk
Where thin, there breaks. The Research Center Positive Research, together with the information security portal SecurityLab.ru, analyzed computer vulnerabilities for 2011. It turned out that serious security problems were observed in SCADA-systems, CMS, Adobe programs and in almost all browsers. Traditionally, a friendly family of Windows operating systems “distinguished”, where one of the vulnerabilities was exploited by the legendary Duqu virus.
How many vulnerabilities have been fixed?
In just a year, 4733 vulnerabilities were described. Software manufacturers were able to eliminate by January 1, only 58% of vulnerabilities, and another 7% issued instructions on how to fix them. Thus, more than a third of the vulnerabilities remained open to cybercriminals.
Adobe programs are being cracked
Zero-day vulnerabilities are a headache for developers. These gaps in the system are actively exploited by hackers even before the publication of the message about the vulnerability and the release of the patch.
It is interesting to note the increase in the number of such vulnerabilities in Adobe products - last year they were found seven, and by this parameter Adobe overtook another giant, Microsoft, which had 5 zero-day vulnerabilities. Recent examples include the Adobe Reader CVE-2011-2462 vulnerability, discovered at the end of 2011, used to crack ManTech, a contractor of the US Department of Defense.

')
Is Opera Browser Safest?
The most secure browser in terms of the number of vulnerabilities in 2011 was Opera. In all common applications of this type, except Opera, a very large number of high-risk vulnerabilities have been discovered that can be used to compromise the system. Last year, leading browsers also found 4 vulnerabilities of a critical degree of danger, which were used by attackers to conduct successful attacks on various companies. Most of them (three) were in Internet Explorer and one was found in Chrome 11.x.
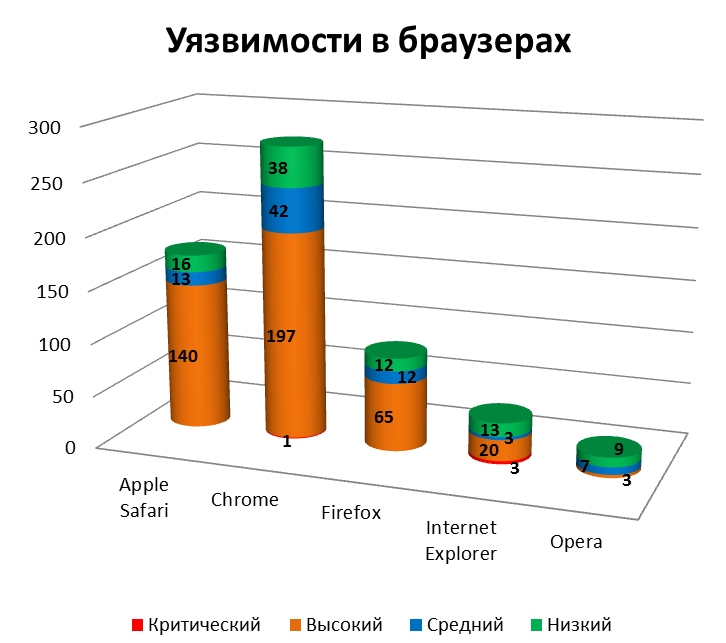
A general view of vulnerabilities in different versions of browsers is as follows:
Windows - almost 100 vulnerabilities per year
The popularity of Windows logically affects the number of vulnerabilities. Compared to other operating systems, the product from Microsoft found them the most. Windows holds the lead both in the overall standings (92 vulnerabilities) and individually - only this OS had 2 critical vulnerabilities published during the reporting period. On the other hand, the maximum number of high-risk vulnerabilities (33) was found in Mac OS, 22 were found in Windows, and only one in different versions of Linux.

All attention to SCADA-systems
In server software, vulnerabilities in SCADA systems are widespread: 37 security vulnerabilities have been described in 17 security notifications. The interest of researchers in the software of the automated process control systems is not accidental - in the last two years, viruses aimed at industrial automation applications have become common.
CMS and forums - a favorable environment for hackers
Content management systems provide the best conditions for unauthorized intrusions in a segment of web applications (18%). Hackers are constantly looking for vulnerabilities in CMS, and, as we see, find them in large numbers (204 vulnerabilities per year). Administrators of sites built on popular platforms need not only to monitor suspicious activity, but also to quickly install updates for CMS. We should not forget also about web forums, which are in second place in the number of vulnerabilities (7%).
Apple iTunes security is questionable
Last year's charts of the most vulnerable media players (among the most popular) were led by Apple iTunes (133 vulnerabilities). In the middle of the list is the widespread VLC Media Player (15 vulnerabilities), while Windows Media Player only published two vulnerabilities, which is about 70 times less than Apple iTunes.
77% of the “holes” in the system can be used remotely
If we consider all the vulnerabilities for 2011, the attacker could work remotely with 77% of the vulnerabilities in operation. For 15%, local area network was required, and for 8%, personal presence or insider information was required.
Every fourth vulnerability can compromise the system
About a quarter of the vulnerabilities (24%) allowed a hacker to compromise the system by executing an arbitrary code on the victim’s computer. Another 21% of the “holes” found were suitable for XSS attack, 15% could be used for denial of service, 13% for revealing important data, 12% for unauthorized data modification.
Vulnerabilities as a way to stop the plant and the nuclear program
In 2011, experts in full voice started talking about the coming of the era of cold cyberwar. Targets of hackers are industrial enterprises and military secrets. In the fall, it became aware of a Trojan virus called Duqu. It penetrates a Windows-based computer, exploiting the critical vulnerability CVE-2011-3402. The virus is then able to infiltrate an adjacent SCADA system of an enterprise in order to steal information about the IT infrastructure and establish control over industrial facilities. Some experts noted that fragments of the main Duqu module are very similar to the Stuxnet worm, which in 2010 put several Iranian uranium enrichment plants down.
Fake SSL Certificates - Revenge For Iran?
In the spring and summer of 2011, Iranian hackers consistently hacked the servers of Comodo and DigiNotar certification centers. The second case was particularly fruitful. Some of the stolen security certificates belonged to the CIA, Mossad and MI-6. In addition to international cyber intelligence, stolen “digital passports” were used for man-in-the-middle attacks (MitM). The hacker passed the “client” Internet traffic through his own proxy server, where the victim's browser met with a fake certificate and gave out the information in decrypted form. The users of Internet banking, postal online services and other services that use SSL certificates are at risk.
US digital signatures and military secrets
Having hacked RSA Security's server in mid-March 2011, unknown hackers compromised the reliability of RSA SecurID digital signatures. These keys were used by more than 40 million workers to gain access to closed networks. The attack began with an e-mail calling for employees of the RSA head company to open a fake Excel file with the intriguing name “Staffing Plan 2011.xls”. The infected table, when opened, installed Poison Ivy backdoor on the PC, exploiting the CVE-2011-0609 vulnerability in the Adobe Flash Player. Among the stolen information was information about the latest solutions for two-factor authentication. Later, using the stolen keys, they tried to hack the servers of the world's largest military-industrial complex enterprise, Lockheed Martin Corporation.
What happens because of non-compliance with the PCI DSS standard
In May 2011, Romanian hackers were caught hacking into the transaction processing systems of the trading terminals and intercepting customer payment card data for three years. The main blow fell on the company Subway. Penetration of a Subway LAN, according to The Wire, was carried out via wireless networks in restaurants, and the terminals themselves did not meet the Payment Card Industry Security Standard (PCI DSS). In addition, the specialists who provide remote technical support for the terminals not only did not install updates for the PCAnywhere remote administration application, but also chose the simplest combination of login and password (administrator, computer) in more than 200 systems.
UPD : OS vulnerabilities took into account only those that were present in the core of the OS and in its components / services, i.e. vulnerabilities in third-party software were not specifically considered
UPD2 : full review
How many vulnerabilities have been fixed?
In just a year, 4733 vulnerabilities were described. Software manufacturers were able to eliminate by January 1, only 58% of vulnerabilities, and another 7% issued instructions on how to fix them. Thus, more than a third of the vulnerabilities remained open to cybercriminals.
Adobe programs are being cracked
Zero-day vulnerabilities are a headache for developers. These gaps in the system are actively exploited by hackers even before the publication of the message about the vulnerability and the release of the patch.
It is interesting to note the increase in the number of such vulnerabilities in Adobe products - last year they were found seven, and by this parameter Adobe overtook another giant, Microsoft, which had 5 zero-day vulnerabilities. Recent examples include the Adobe Reader CVE-2011-2462 vulnerability, discovered at the end of 2011, used to crack ManTech, a contractor of the US Department of Defense.

')
Is Opera Browser Safest?
The most secure browser in terms of the number of vulnerabilities in 2011 was Opera. In all common applications of this type, except Opera, a very large number of high-risk vulnerabilities have been discovered that can be used to compromise the system. Last year, leading browsers also found 4 vulnerabilities of a critical degree of danger, which were used by attackers to conduct successful attacks on various companies. Most of them (three) were in Internet Explorer and one was found in Chrome 11.x.

A general view of vulnerabilities in different versions of browsers is as follows:
| Browser / danger level | Critical | Tall | Average | Low |
| Apple Safari 5.x | 0 | 140 | 13 | sixteen |
| Chrome 8.x | 0 | sixteen | four | 2 |
| Chrome 9.x | 0 | 43 | eight | 3 |
| Chrome 10.x | 0 | 23 | 3 | four |
| Chrome 11.x | 0 | 12 | five | 2 |
| Chrome 12.x | one | 26 | 9 | one |
| Chrome 13.x | 0 | 40 | 9 | 3 |
| Chrome 14.x | 0 | 17 | 2 | eight |
| Chrome 15.x | 0 | 20 | one | sixteen |
| Internet Explorer 6 | 3 | sixteen | 2 | eleven |
| Internet Explorer 7 | 3 | 15 | 2 | 12 |
| Internet Explorer 8 | 2 | 17 | 3 | eleven |
| Internet Explorer 9 | one | 14 | 2 | ten |
| Mozilla Firefox 3.5.x | 0 | 18 | 3 | 3 |
| Mozilla Firefox 3.6.x | 0 | 34 | 6 | four |
| Mozilla Firefox 5.0.x | 0 | 7 | one | one |
| Mozilla Firefox 6.0.x | 0 | 7 | one | one |
| Mozilla Firefox 7.0.x | 0 | five | one | 2 |
| Mozilla Firefox 8.0.x | 0 | four | one | 2 |
| Opera 10.x | 0 | one | one | four |
| Opera 11.x | 0 | 3 | 7 | eight |
| Opera Mobile for Android 11.x | 0 | 0 | 0 | one |
Windows - almost 100 vulnerabilities per year
The popularity of Windows logically affects the number of vulnerabilities. Compared to other operating systems, the product from Microsoft found them the most. Windows holds the lead both in the overall standings (92 vulnerabilities) and individually - only this OS had 2 critical vulnerabilities published during the reporting period. On the other hand, the maximum number of high-risk vulnerabilities (33) was found in Mac OS, 22 were found in Windows, and only one in different versions of Linux.

All attention to SCADA-systems
In server software, vulnerabilities in SCADA systems are widespread: 37 security vulnerabilities have been described in 17 security notifications. The interest of researchers in the software of the automated process control systems is not accidental - in the last two years, viruses aimed at industrial automation applications have become common.
CMS and forums - a favorable environment for hackers
Content management systems provide the best conditions for unauthorized intrusions in a segment of web applications (18%). Hackers are constantly looking for vulnerabilities in CMS, and, as we see, find them in large numbers (204 vulnerabilities per year). Administrators of sites built on popular platforms need not only to monitor suspicious activity, but also to quickly install updates for CMS. We should not forget also about web forums, which are in second place in the number of vulnerabilities (7%).
Apple iTunes security is questionable
Last year's charts of the most vulnerable media players (among the most popular) were led by Apple iTunes (133 vulnerabilities). In the middle of the list is the widespread VLC Media Player (15 vulnerabilities), while Windows Media Player only published two vulnerabilities, which is about 70 times less than Apple iTunes.
77% of the “holes” in the system can be used remotely
If we consider all the vulnerabilities for 2011, the attacker could work remotely with 77% of the vulnerabilities in operation. For 15%, local area network was required, and for 8%, personal presence or insider information was required.
Every fourth vulnerability can compromise the system
About a quarter of the vulnerabilities (24%) allowed a hacker to compromise the system by executing an arbitrary code on the victim’s computer. Another 21% of the “holes” found were suitable for XSS attack, 15% could be used for denial of service, 13% for revealing important data, 12% for unauthorized data modification.
Vulnerabilities as a way to stop the plant and the nuclear program
In 2011, experts in full voice started talking about the coming of the era of cold cyberwar. Targets of hackers are industrial enterprises and military secrets. In the fall, it became aware of a Trojan virus called Duqu. It penetrates a Windows-based computer, exploiting the critical vulnerability CVE-2011-3402. The virus is then able to infiltrate an adjacent SCADA system of an enterprise in order to steal information about the IT infrastructure and establish control over industrial facilities. Some experts noted that fragments of the main Duqu module are very similar to the Stuxnet worm, which in 2010 put several Iranian uranium enrichment plants down.
Fake SSL Certificates - Revenge For Iran?
In the spring and summer of 2011, Iranian hackers consistently hacked the servers of Comodo and DigiNotar certification centers. The second case was particularly fruitful. Some of the stolen security certificates belonged to the CIA, Mossad and MI-6. In addition to international cyber intelligence, stolen “digital passports” were used for man-in-the-middle attacks (MitM). The hacker passed the “client” Internet traffic through his own proxy server, where the victim's browser met with a fake certificate and gave out the information in decrypted form. The users of Internet banking, postal online services and other services that use SSL certificates are at risk.
US digital signatures and military secrets
Having hacked RSA Security's server in mid-March 2011, unknown hackers compromised the reliability of RSA SecurID digital signatures. These keys were used by more than 40 million workers to gain access to closed networks. The attack began with an e-mail calling for employees of the RSA head company to open a fake Excel file with the intriguing name “Staffing Plan 2011.xls”. The infected table, when opened, installed Poison Ivy backdoor on the PC, exploiting the CVE-2011-0609 vulnerability in the Adobe Flash Player. Among the stolen information was information about the latest solutions for two-factor authentication. Later, using the stolen keys, they tried to hack the servers of the world's largest military-industrial complex enterprise, Lockheed Martin Corporation.
What happens because of non-compliance with the PCI DSS standard
In May 2011, Romanian hackers were caught hacking into the transaction processing systems of the trading terminals and intercepting customer payment card data for three years. The main blow fell on the company Subway. Penetration of a Subway LAN, according to The Wire, was carried out via wireless networks in restaurants, and the terminals themselves did not meet the Payment Card Industry Security Standard (PCI DSS). In addition, the specialists who provide remote technical support for the terminals not only did not install updates for the PCAnywhere remote administration application, but also chose the simplest combination of login and password (administrator, computer) in more than 200 systems.
UPD : OS vulnerabilities took into account only those that were present in the core of the OS and in its components / services, i.e. vulnerabilities in third-party software were not specifically considered
UPD2 : full review
Source: https://habr.com/ru/post/140849/
All Articles