Sandbox wars - Part 3: ARP-Spoofing, the uselessness of filtering by MAC address and the danger of installing unsigned software

A little more than a year has passed since the publication of the previous articles ( 1 , 2 ), and only recently the circumstances were such that I had a reason to conduct a new attack.
This time there is no physical access to the network infrastructure. There is only a laptop with Internet access via Wi-Fi. The victim - a neighbor in the hostel - is connected to another access point (DIR-320) via Ethernet, but the password for connecting to the point is known to almost everyone, because its owner prefers to use MAC address filtering as a means of access control, adding and removing addresses from the database as needed. My MAC address is not on the allowed list.
')
Ok, we connect, we do several tests, and we see that MAC address filtering occurs only at the network level, that is, the access point does not refuse:
- send my frames to the ethernet segment and deliver the responses
- respond to ARP requests and receive ARP responses
The only thing that the access point refuses to do is to interact with a stranger at the network level, that is, it does not give me an IP address through DHCP, it cannot be pinged, and the Internet does not go through it either.
ARP-Spoofing
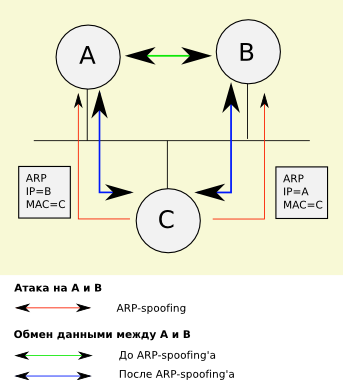
For those who do not know what is ARP and ARP-Spoofing - a small educational program. The network layer, which uses IP addresses, is used on top of the data link layer (it uses MAC addresses set by the manufacturers of the network card). When sending an IP packet, the computer must wrap it in an Ethernet frame, specifying the MAC address of the recipient (or gateway). To find out the MAC address of the recipient, the computer makes a broadcasting ARP request of the form “Computer with ip abcd, respond!”. The abcd computer responds with an ARP reply of the form “abcd is me, my MAC address is: 00: 11: 22: 33: 44: 55”. And the answer can be sent even if there was no request and it will be processed. All computers support the IP → MAC correspondence cache and at every opportunity (an ARP request / response is received) it is updated.
There is no authentication at the level of ARP, on which the ARP-spoofing attack is based. It is enough to introduce yourself (send an ARP response) to the victim as a router, and to the victim as a router in order to proxy their traffic through themselves.
But, since the access point does not let me go to the Internet, then the classic version of ARP spoofing - it’s not possible to get between the victim and the router. If so, you can get up not between the victim and the router, and instead of the router. We go to the market, buy a USB-WiFi adapter, connect the built-in adapter (by disabling the IP protocol on it) to the target network, and the second one to ours to have a channel to the Internet. We create a virtual machine with two adapters in VirtualBox, connect the first bridge with the target network, do the NAT on the second. We configure NAT inside the virtual machine-router, we run arpspoof on it in order to convince the victim’s computer that the router’s MAC address has changed to ours.
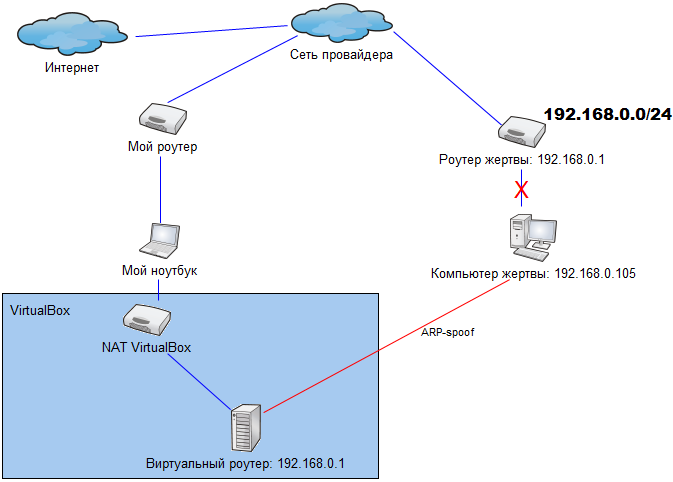
As a result, the victim will send packets not to the real router, but to ours, which will be able to route them to the Internet, by viewing and modifying. Virtually standard ARP spoofing scheme. With only one small drawback - it does not work. It works more precisely, but with such interruptions that the victim can not fail to notice problems with the network.
Looking at the traffic on the network, you can understand why. Yes, we notify every second the victim's router that the address 192.168.0.105 belongs to us, and the victim that the ip address 192.168.0.1 belongs to us. However, there is another ARP activity on the network. For example, a router periodically broadcasts to the network “192.168.0.109, where are you?”, And there is no such address on the network. The reasons for this activity are not very clear - it is possible that a port from an external ip is sent to this address on the router. But such sociability on the part of the router does not lead to anything good. The victim's computer sees this broadcast request, and, although the request is not related to it, it updates the MAC address of the router in its cache. The result is race condition, and the victim sends outgoing packets either to our address or to the address of this router.
What to do? Since the router is so worried about non-existent ip-addresses, you need to calm it down, for example, telling it that these addresses belong to us. So:
- Every two seconds, send an ARP request to all segment addresses to find out who is online.
- Every ten seconds for each IP address that we have not seen on the network for a long time, send an ARP reply to the router, stating that this address belongs to us
After adding such functionality in the form of a python script, parsing the output of tcpdump arp and sending out ARP requests and responses, communication failures became much less. When a computer connects to the network, it usually starts its activity with an ARP request for its IP and IP router, as a result of which we see that it appeared and cease to impersonate it. When the computer turns off, we see that it has disconnected and takes its place. As a result, the router now has no reason to send broadcast ARP requests and confuse the victim's computer.
Taking control of the car
Listening to http-traffic, or using sslstrip , in order to listen to the ssl-enabled traffic of the sites does not interest us now - firstly it’s old, secondly there’s nothing interesting in the traffic. I want to get full control over the target machine.
Backdoor
For maximum privileges, our backdoor program should run on behalf of LocalSystem. To do this, we write the Windows Service (in C # this is a couple of dozen lines, which the IDE also generates). For management we will use the Jabber protocol ( agsXMPP ). The service will connect to the Jabber server when it starts up and wait for commands. You can manage it with the help of any Jabber-client, sending commands via chat. As for the commands, for some reason, cmd.exe is considered to be a UI program from the Windows point of view, and system services cannot interact with the user. It was not possible to launch cmd.exe from the service. As a result, instead of the cmd shell commands, it was decided to transfer the bot code to C #, which it will interpret and return the result; a fairly universal “shell” is obtained.

Installer
The installer stores the executable file and the library service and at startup does the following:
- Save the service files to some secluded place in the% WINDOWS% directory
- Install service
- Make HTTP GET on http://google.com/success (why you need it - it will become clear later)
Installation
Now we need to somehow force the client to run our installer.
Look at the automatic updates, it may be possible to replace them. Using HTTP headers, we find out that Opera is on the machine as a browser, but, as it turned out, its updates go via https, so they are too tough for us. Updates from Microsoft go on plain-http, but there, for sure, every update file has a digital signature, which is checked before launching, after all, MS students are not working in MS.
Ok, with automatic updates, nothing can be done, it remains to hope for the user's inattention. Let's try to inject the installer into the first downloaded executable file.
To do this, we write a transparent proxy (in Twisted it is a little over a hundred lines), which in addition to its normal duties performs the following actions:
- If the request URL is equal to google.com/serviceinstaller , then as a response, we return the installer binary created earlier
- If the request URL is google.com/success , then report back to me about success and go into the usual honest proxy mode
- If the server response code is 200, the Content-Type belongs to the list ['application / octet-stream', 'application / x-msdownload', 'application / exe', 'application / x-exe', 'application / dos-exe' , 'vms / exe', 'application / x-winexe', 'application / msdos-windows', 'application / x-msdos-program', 'application / binary'], and the Content-Length does not exceed 20 megabytes, then :
- Download file
- Send a file with a POST request to the main machine (since there is Windows) for further analysis
- Send the response to the POST request to the client (by correcting the Content-Length and Content-MD5 headers respectively)
We start this proxy server on the virtual router and redirect all HTTP traffic to it using iptables.
Now we are writing a wrapper project in C #, the main program of which as a resource includes the executable file original.exe as a resource (for now we will create just an empty file with that name). We register in the manifest of a wrapper that it has to be started with the administrator's rights. The wrapper code is extremely simple:
- Download at google.com/serviceinstaller and run our service installer
- Save the built-in original.exe resource to a temporary file and run it.
After that we write an auxiliary web server, which for each received request performs the following actions:
- Save the data to the original.exe file
- If original.exe is an executable file and does not have a digital signature, then start rebuilding the wrapper project, and return the result of the compilation. Otherwise, return the original file without changes.
On this coding is over. Now we run all the components, and see how it should work:
- The user is going to download some game installer or something else (unsigned installers on the Internet are now missing, the same Notepad ++ , which is a very convenient and popular program)
- The proxy server receives an HTTP request, forwards it to the server, receives response headers from the server, sees by the headers that the downloaded file is a potential candidate for implementing our installer into it
- The proxy server downloads the file to the end and sends it to the injection server.
- The injection server verifies that it is a valid executable file (otherwise it could have been transmitted in application / octet-stream), verifies that the file is unsigned, so you can modify it without danger of exposure (the installer still does not check the checksums, even if on the site they are laid out)
- The injection server compiles the binary wrapper, embeds the original executable file in it and returns the result to the proxy server.
- The proxy gives the file to the client (the client will not suspect anything, since the source file was no more than 20 megabytes, which means that the previous three points delayed the start of the download for only a few seconds)
- The client runs the downloaded file, receives a UAC request (exactly the same as it would have been from the original file), accepts it
- Our installer is downloaded and launched, does its dirty work, reports success to us.
- The original installer starts.
Running all waiting. And, after a couple of days, we see in the logs of the injection server:
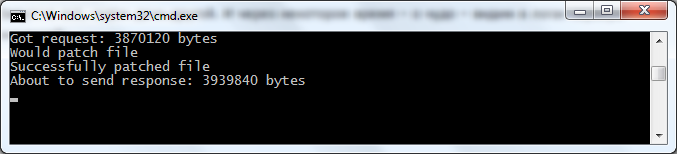
and in the proxy server logs:
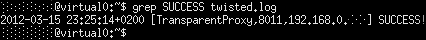
Now you can go to your neighbor and please him by showing tricks that we can do with his computer (restart, give scary sounds from the audio system, etc.).
findings
- Filtering by MAC address. Do not rely on it. It will not save from a cracker. From a student who wants to use the Internet at your expense, too, he will simply change the MAC address to any of the overheard.
- ARP-spoofing. You can protect against it even on a SOHO router. For example, for the popular Dlink DIR-300/320 device, you can enable the Guest Zone , which isolates clients from each other.
- MITM. Do not use unprotected means of communication (
for example, ICQ transmits a password in clear text, vk.com also seems to still do this. UPD : ICQ and vk already use SSL for authentication). If you need to download the installer, download it via https. If it is distributed only via http, then check the digital signature of the file after downloading. If there is no digital signature, then verify the checksums with those indicated on the site (preferably, watch the checksums on the site on another Internet channel). - Antivirus. Do not rely on it, the person will always be smarter than the program. I don’t know how another antivirus would act here, but Microsoft Security Essentials, which was installed on the victim’s computer, didn’t react to all the above described manipulations.
 Morality. I will repeat the advice from the first part : do not be a “bad guy,” maybe your neighbor is just looking for a victim.
Morality. I will repeat the advice from the first part : do not be a “bad guy,” maybe your neighbor is just looking for a victim.
______________________
The text was prepared in the Habr Editor from © SoftCoder.ru
Source: https://habr.com/ru/post/140440/
All Articles