Protection in a virtual environment: checklist of threats
Data protection in a virtual environment is a “brave new world”, meaning a major change in world view regarding the understanding of threats.
I work with the protection of personal data, my colleagues and I have a huge table of possible security threats with which you can check what is wrong on specific sites.
Likbez
Standard IT concepts (server, cable, network switch, and so on) from the area of physical objects are transferred to virtual ones. In the virtualization environment, they begin to be elements of the configuration of the program code of the virtual environment (hypervisor).
')
Changing the very form of threats. On the one hand, threats of the “real” world disappear in a virtual environment (for example, cable breaks, failure of a specific server board, etc.), but others arise (for example, incorrect software configuration of logical connections between objects of the virtual environment, the possibility of theft / destruction of virtual environments entirely due to the fact that virtual machines are files that can be copied to removable media or deleted).
In addition, there is the question of how to “stretch” the requirements of regulatory bodies (FSTEC) on the virtual environment, since the existing requirements describe the requirements for protection, assuming that cables, servers and network equipment are physical objects.
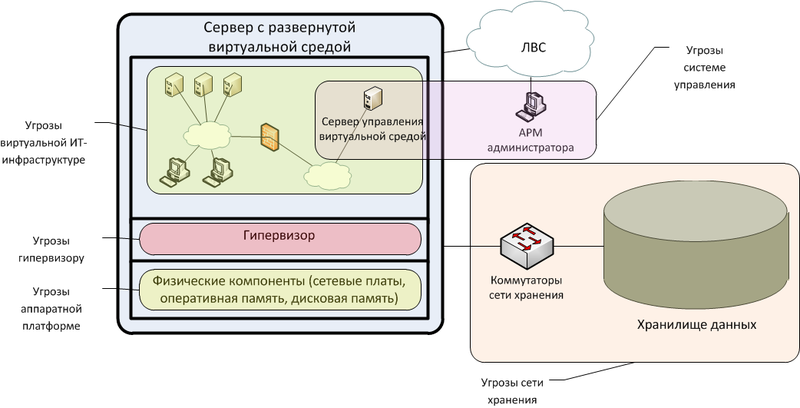
We structure security threats in a virtual environment in accordance with its architectural levels:
- The hardware platform on which the virtual environment is deployed;
- System software virtualization (hypervisor), performing the functions of managing hardware resources and resources of virtual machines;
- Virtual environment management system (server and client software components that allow you to control the settings of the hypervisor and virtual machines locally or remotely);
- Virtual machines that include system and application software;
- Storage area network (including switching equipment and storage system) with hosted virtual machine images and data (storage network can be implemented based on SAN, NAS, iSCSI).
When analyzing threats, it is important to take into account the specifics of processing personal data in a virtual environment:
- They are processed within the virtual machines. Within a single server, there can be many virtual servers, on each of which personal data of different categories can be processed, and the servers themselves can be included in different personal data information systems. In this case, the "image" of the server can be located in a separate data storage.
- Transferred between virtual machines within a virtual environment. Since a virtual machine is a file stored in the data storage, the transfer of personal data between virtual machines assumes that PDs come out of one data storage area, pass network switches, go to a server with a virtual environment deployed, and then return to the storage in reverse order. but for another virtual machine.
- Transmitted between the virtual environment and the external environment (both real and virtual). The peculiarity is that data related to different virtual servers or information systems can “come out” of the network interface of a single physical server and, accordingly, the question arises of integrating protection mechanisms of the virtual environment and external physical components.
Consider the threats of each level caused by intentional or unintentional actions of potential violators.
Threats to the hardware platform (common server platforms, blade baskets)
Violation of the hardware components of server hardware with installed components of the virtual environment
Potential intruder:
1) An employee who does not have access rights to premises with hosted virtual environment components;
2) Visitor;
3) Administrator.
What's happening:
1) Physical damage to the hardware components of the virtual environment;
2) Unauthorized removal or replacement of equipment components;
3) Unauthorized violation of the hardware components or adjacent supporting systems (power off, air conditioning systems, etc.);
4) Failures and failures in the operation of adjacent support systems (power supply, air conditioning, etc.).
Effects:
1) Violation of the availability of PD. Stopping virtual machines running on a hardware platform, as well as disrupting the operation of contiguous IT systems depending on their health;
2) Violation of the integrity of PD;
3) Destruction of PD, placed on damaged data carriers.
Technical measures:
1) The use of access control systems in rooms with placed hardware components of the virtual environment;
2) The use of protection from unauthorized access to the server racks (closing and sealing cabinets with server hardware);
3) Redundancy of components of supporting systems.
Organizational measures:
1) Regulating the procedures for access to premises with the hosted hardware components of the virtual environment;
2) Regulation of procedures for access to hardware components;
3) Regulating the procedures for regular maintenance of hardware components;
3) Regulating the procedures for recovering hardware components after failures and failures;
4) Regulation of procedures for the careful selection of staff for the post of administrator.
Unauthorized removal from the server hardware and theft of storage media
Potential intruder:
1) An employee who does not have the right of access to premises with placed hardware components of the virtual environment;
2) Visitor;
3) Administrator.
What's happening:
Unauthorized removal of media and their removal outside the organization.
Effects:
Loss and / or leakage of PD (if they are on stolen media).
Technical measures:
1) The use of access control systems in a room with hosted hardware components of the virtual environment;
2) The use of protection from unauthorized access to the server racks (closing and sealing cabinets with server hardware);
3) Use of backup and recovery systems on data carriers.
Organizational measures:
1) Regulating the procedures for access to premises with the hosted hardware components of the virtual environment;
2) Regulation of procedures for access to hardware components;
3) Regulating the procedures for regular maintenance of hardware components;
4) Regulating the procedures for recovering hardware components after failures and failures;
5) Regulating procedures for backing up and restoring data;
6) Regulation of procedures for the careful selection of staff for the post of administrator.
Network Switch Violation
Potential intruder:
1) An employee who does not have the right to access premises with hosted network equipment;
2) Visitor;
3) Administrator.
What's happening:
Connecting the network interfaces of the hardware platform to untrusted network segments and changing their network settings.
Effects:
1) The ability to conduct network attacks from untrusted network segments to virtual machines deployed on a hardware platform;
2) Violation of the ISPD, deployed in a virtual environment.
Technical measures:
Secure configuration of network equipment (mapping of switch ports to the MAC addresses of network cards).
Organizational measures:
1) Regulating the procedures for access to premises with hosted network equipment;
2) Regulation of procedures for the careful selection of staff for the post of administrators.
Threats to Virtualization System Software (Hypervisor)
Incorrect configuration of hypervisor and virtual machine parameters affecting security
Potential intruder:
Administrator of the virtual environment.
What's happening:
Unauthorized access (remote access from a real environment or access within a virtual environment) to virtual machine resources due to incorrect settings of the hypervisor.
Effects:
Examples of possible threats and their corresponding security settings for VMware vSphere 4.1 are described in the “Security Hardening Guide” communities.vmware.com/docs/DOC-15413
Technical measures:
1) Using security analysis tools and analyzing the compliance of the virtual environment settings with “best practices” and organization security policies;
2) Using tools to control the integrity of the settings of the hypervisor;
3) The use of specialized systems of protection from unauthorized access in a virtual environment for the differentiation of access rights of administrators of the virtual environment (IT and IB), recording actions of administrators of the virtual environment.
Organizational measures:
1) Regulation of work on the analysis of security and analysis of the compliance settings of the hypervisor to security policies;
2) Separation and regulation of the rights of virtual environment administrators and information security administrators in the operation of a virtual environment;
3) Regulate security incident investigation procedures in a virtual environment.
Incorrect configuration of hypervisor and virtual machine parameters affecting security
Potential intruder:
Administrator of the virtual environment.
What's happening:
Unauthorized access (remote access from a real environment or access within a virtual environment) to virtual machine resources due to incorrect settings of the hypervisor.
Effects:
Examples of possible threats and their corresponding security settings for VMware vSphere 4.1 are described in the “Security Hardening Guide” communities.vmware.com/docs/DOC-15413
Technical measures:
1) Using security analysis tools and analyzing the compliance of the virtual environment settings with “best practices” and organization security policies;
2) Using tools to control the integrity of the settings of the hypervisor;
3) The use of specialized systems of protection from unauthorized access in a virtual environment for the differentiation of access rights of administrators of the virtual environment (IT and IB), recording actions of administrators of the virtual environment.
Organizational measures:
1) Regulation of work on the analysis of security and analysis of the compliance settings of the hypervisor to security policies;
2) Separation and regulation of the rights of virtual environment administrators and information security administrators in the operation of a virtual environment;
3) Regulate security incident investigation procedures in a virtual environment.
Software Hypervisor Errors
Potential intruder:
1) Administrator of the virtual environment;
2) An employee who has legitimate access to a particular virtual machine (s)
What's happening:
Unauthorized access (within the virtual environment) to virtual machine resources due to software tabs (or errors) in the hypervisor software.
Effects:
Destruction / theft / corruption of PDs processed within a virtual machine to which unauthorized connection occurred.
Technical measures:
Confirmation of the correct operation of the hypervisor software and the absence of undeclared capabilities in it as part of its certification in the FSTEC of Russia.
Organizational measures:
Regulate the maintenance procedures of the hypervisor software in accordance with the technical specifications under which the hypervisor software was certified.
Substitution of hypervisor executables
Potential intruder:
Administrator of the virtual environment.
What's happening:
Unauthorized access (remote access from a real environment or access within a virtual environment) to virtual machine resources due to distortion of the hypervisor software.
Effects:
1) Unauthorized access to stored, processed and transferred between virtual machines PD;
2) Violation of the availability of ISPD, deployed in a virtual environment.
Technical measures:
1) Use of software integrity monitoring tools and hypervisor settings (during the boot process and during work).
2) Registration of actions of administrators of the virtual environment.
Organizational measures:
1) Regulating the procedures for monitoring the integrity of the hypervisor software;
2) Regulate security incident investigation procedures in a virtual environment.
Unauthorized remote access to hypervisor resources due to network attacks like "buffer overflow" on the open network ports of the server with the hypervisor in case of vulnerabilities in its software
Potential intruder:
1) An employee who has network access to a network segment to which a server with an installed hypervisor is connected;
2) An intruder acting from outside the organization’s network, who has remotely penetrated the network segment to which the server with the hypervisor is connected.
What's happening:
Perform buffer overflow attacks.
Effects:
Taking control of a server with a hypervisor installed with the authority of a hacked service.
Technical measures:
1) Timely installation of security updates for the hypervisor;
2) The separation of the productive network from the management network and the service network.
3) Using firewalls and intrusion prevention systems to filter network traffic and block network attacks.
Organizational measures:
1) Regulating the procedure for updating the software of the hypervisor;
2) Regulation of procedures for the operation of firewalls and intrusion prevention systems.
The depletion of server computing resources with a hypervisor due to denial of service attacks against virtual machines
Potential intruder:
An employee who has access to a network segment to which a server with a hypervisor is connected.
What's happening:
Perform denial of service attacks.
Effects:
Slowing down or stopping the server with the hypervisor due to depletion of computing resources.
Technical measures:
1) Setting the parameters of the hypervisor to limit and guarantee resources for virtual machines;
2) Monitoring server capacity utilization with a hypervisor.
Organizational measures:
1) Regulating procedures for the creation, configuration and maintenance of virtual machines;
2) Regulating server monitoring procedures with a hypervisor.
Accidental or deliberate distortion / destruction of virtual machine images
Potential intruder:
Virtual Environment Administrator
What's happening:
Erasing images, distorting images by regular means of the virtual environment
Effects:
1) Violation of the virtual machine and, as a result, accessibility of PDs processed on it;
2) Destruction / distortion of PD processed within a compromised virtual machine;
Technical measures:
Use backup and restore virtual machine images.
Organizational measures:
Regulate the procedure for backing up and restoring images of virtual machines.
Threats to the virtual environment management system
Obtaining unauthorized access to the virtual infrastructure management console (virtual environment administrator workstation)
Potential intruder:
1) An employee who does not have access to the management console;
2) Visitor.
What's happening:
1) Password selection;
2) Gaining access to the active administration console.
Effects:
1) Unauthorized changes to the settings of the virtual environment, leading to a decrease in the level of security of the virtual environment;
2) Theft of virtual machine disk images;
3) Unauthorized change of the virtual environment settings, leading to disruption of operation, destruction of the virtual environment and theft of PD processed in it.
Technical measures:
1) Specialized means of protection against unauthorized access to the virtual infrastructure console, installed on the workstations of administrators.
2) Tools that implement mechanisms for restricting access to virtual machine disk image files;
3) The use of access control systems in the room with the administrator workstation;
4) The use of multifactor authentication systems when accessing an administrative workplace.
Organizational measures:
1) Regulating the procedures for accessing a room with an administrative workstation;
2) Regulating the actions of administrators when working with the AWP administration;
3) Regulate account management procedures.
Obtaining unauthorized access to virtual machine settings
Potential intruder:
Virtual environment administrator who has access to the administration console but does not have the right to configure certain virtual machines
What's happening:
Use of standard tools of a virtual environment management system
Effects:
Unauthorized change of virtual environment settings leading to disruption of operation, destruction of virtual environment and theft of PDs processed in it.
Technical measures:
1) The use of specialized means of delimiting access to resources of the virtual environment;
2) Registration of actions of administrators of the virtual environment.
Organizational measures:
1) Regulating the procedures for administering the virtual environment and differentiating access rights for its administration;
2) Regulate security incident investigation procedures in a virtual environment.
Obtaining unauthorized remote access to the control system interface
Potential violator:
1) An employee who does not have the right of remote access to the control system;
2) An external attacker who gained access to the control segment.
What happens:
1) Connect to the management interface and password selection;
2) Connection to the control segment and interception of the current session (man-in-the-middle attack);
3) Penetration into the control segment from adjacent segments and implementation of actions similarly to item 1 and item 2
Effects:
1) Distortion of the security settings of the virtual environment, allowing further attacks on virtual machines;
2) Distortion of the security settings of the virtual environment, which can disrupt the functioning of the virtual environment.
Technical measures:
1) The use of specialized means of restricting access to resources of the virtual environment;
2) Isolation of a virtual environment management network into a separate network segment and its protection by means of firewall and intrusion prevention;
3) Using security analysis tools to control the security of the virtual environment and its settings to comply with internal security policies and “best practices”;
4) Using the means of monitoring the integrity of the settings and software management system.
Organizational measures:
1) Regulating the procedures for granting access to the virtual environment management system;
2) Regulation of work on the analysis of security and integrity control;
3) Regulating the administration of firewall and intrusion prevention tools.
Threats to the IT infrastructure implemented within the virtual environment
Deploying new poorly protected virtual machines
Potential intruder:
Administrator of the virtual environment.
What's happening:
Creating virtual machines using standard virtual platform tools.
Effects:
The emergence of threats of hacking poorly protected virtual machines with the subsequent compromise of the rest.
Technical measures:
Creation of new virtual machines based on ready protected images.
Organizational measures:
Regulation of the process of creating new virtual machines.
"Mixing" of information at various levels of confidentiality within a single hardware platform
Potential intruder:
Virtual Environment Administrator
What's happening:
Placement of virtual machines with different levels of privacy within a single hardware platform.
Effects:
Carrying out network attacks from the virtual machine domain with a low level of confidentiality against virtual machines with a higher level of confidentiality.
Technical measures:
1) Placement of virtual machines with different levels of confidentiality within various hardware platforms (a combination of server and network equipment); 2) The use of certified firewalling to differentiate access between hardware platforms containing virtual machines with different levels of privacy.
Organizational measures:
Regulate the design and deployment of virtual machines with different levels of privacy within a virtual environment.
Unauthorized network connection to the virtual machine
Potential intruder:
1) Virtual IT infrastructure administrator;
2) An employee who is a user of the virtual environment;
3) An external attacker who gained access to a network segment with hosted virtual machines.
What's happening:
1) Password selection for network connection using standard automated workstations (AWP) users;
2) Conducting network attacks against virtual machines using their vulnerabilities;
3) Remote penetration into a network segment with virtual machines and implementation of actions from item 1 and item 2.
Effects:
1) Violation of the virtual machine and, accordingly, violation of the integrity of PDs processed on it;
2) Destruction / distortion of PD processed within a compromised virtual machine;
3) PD leakage processed within the compromised virtual machine.
Technical measures:
1) Using firewalls and intrusion prevention to control network traffic between different network segments;
2) Using multi-factor user authentication tools;
3) Using security analysis tools for virtual machines;
4) Logging actions of virtual environment administrators and virtual machine users.
Organizational measures:
1) Regulate account management and password policy procedures;
2) Regulation of work on the analysis of the security of virtual machines;
3) Regulating firewall operation procedures, intrusion prevention tools and multifactor authentication tools;
4) Regulate security incident investigation procedures in a virtual environment.
Substitution and / or interception of data and RAM of virtual machines in the process of their migration by means of a virtual environment
Potential intruder:
An employee who has network access to a segment in which the migration procedures take place.
What's happening:
Interception of network traffic or penetration into a network session in which virtual machine is being migrated (implementation of a man-in-the-middle attack).
Effects:
1) Malfunction of the migrated virtual machine;
2) Theft of the virtual machine image and the leakage of data processed on it.
Technical measures:
1) Using a firewall to distinguish between a user network, a network of virtualization and storage tools, and a migration network;
2) The use of cryptographic protection of network traffic for the implementation of the migration procedure.
Organizational measures:
Regulation of procedures for the operation of firewalls and means of cryptographic protection of network traffic.
Network attacks between virtual machines
Potential intruder:
1) Virtual IT infrastructure administrator;
2) An employee who is a user of the virtual environment;
3) An external attacker who gained access to a network segment with hosted virtual machines.
What's happening:
1) Implementing “buffer overflow” attacks, SQL-injection, etc. using system and application vulnerabilities;
2) Remote penetration into the network segment with virtual machines and implementation of actions from p.1.
Effects:
1) Violation of the virtual machine and, accordingly, violation of the availability of PDs processed on it;
2) Destruction / distortion of PD processed within a compromised virtual machine;
3) PD leaks processed within a compromised virtual machine (privacy property).
Technical measures:
1) Using firewalls and intrusion prevention to control network traffic between different network segments;
2) The use of tools for analyzing the security of virtual machines.
Organizational measures:
1) Regulation of work on the analysis of the security of virtual machines;
2) Regulating firewall and intrusion prevention procedures.
Virus infection of virtual machines
Potential intruder:
All employees
What's happening:
Using infected removable media, receiving viruses via email, via the Internet.
Effects:
1) Violation of the virtual and, accordingly, violation of the availability of PDs processed on it;
2) Destruction / distortion of PD processed within a compromised virtual machine;
3) PD leakage processed within the compromised virtual machine.
Technical measures:
Using antivirus software in a virtual environment and at the organization’s network perimeter level (mail, Internet).
Organizational measures:
1) Regulating the procedures for working with removable media, e-mail, the Internet;
2) Regulating the maintenance of antivirus software.
Threats to the storage area network [1] with hosted virtual machine images
Theft of storage system partitions with virtual machine images and data
Potential intruder:
Storage Network Administrator.
What's happening:
Unauthorized copying of partitions of a storage system by standard means on removable storage devices.
Effects:
PD leaks processed within virtual machines.
Technical measures:
1) The use of access control to peripheral devices on AWP administrators;
2) Using logging tools for storage administrators.
Organizational measures:
1) Regulating the procedures for granting access to storage management;
2) Regulating the procedures for operating access control devices, access control devices for peripheral devices and monitoring tools.
Theft of storage network media
Potential intruder:
1) Storage Network Administrator;
2) Any employee who has received physical access to the storage network.
What's happening:
Physical theft of carriers.
Effects:
Violation of the virtual machines and destruction / leakage of PD stored on stolen media.
Technical measures:
1) Using access control mechanisms in rooms with storage network components located;
2) Use of backup and recovery systems on data carriers.
Organizational measures:
1) Regulation of access to premises with hosted storage network components;
2) Regulate data backup and restore procedures.
Physical destruction of storage network media
Potential intruder:
1) Storage Network Administrator;
2) Any employee who has received physical access to the storage network.
What's happening:
Physical destruction of carriers.
Effects:
Violation of the virtual machines and destruction of PD, placed on the destroyed media.
Technical measures:
1) The use of fault tolerance mechanisms in the construction of a storage network;
2) Using access control mechanisms in rooms with components of the storage network;
3) Use of backup and recovery systems on data carriers.
Organizational measures:
1) Regulation of access to premises with hosted storage network components;
2) Regulate data backup and restore procedures.
Obtaining unauthorized access to the storage network administrator workstation
Potential intruder:
Any employee who received local or remote access to the AWS of the storage area network administrator.
What's happening:
1) Destruction, distortion or unauthorized copying of sections of the storage system by regular means;
2) Disruption of the storage system components.
Effects:
1) Destruction, distortion or leakage of PD processed within virtual machines;
2) Violation of the availability of PDAs located in the storage area network.
Technical measures:
1) The use of protection against unauthorized access at the level of AWS storage network administrators;
2) Use backup and restore tools.
Organizational measures:
1) Regulation of access to the premises with the location of the AWP administrators;
2) Regulate backup and restore procedures.
Obtaining unauthorized access (remote) to the management interfaces of the storage network components
Potential intruder:
1) Any employee who has access to the network segment with the management interfaces of the storage network component;
2) An external attacker who gained access to the network segment with the components of the storage network.
What's happening:
1) Destruction, distortion or unauthorized copying of sections of the storage system by regular means;
2) Disruption of the storage system components.
Effects:
1) Destruction, distortion or leakage of PD processed within virtual machines;
2) Violation of the availability of PDAs located in the storage area network;
Technical measures:
1) The allocation of a special segment to provide access to the control interfaces of the components of the storage network;
2) Using firewalling to separate the storage network management segment from the rest of the network segments and use intrusion detection tools;
3) Using backup and recovery tools.
Organizational measures:
1) Regulating procedures for setting up and operating firewalling tools;
2) Regulate backup and restore procedures.
Obtaining unauthorized access from virtual machines, where PD processing is not allowed, to storage system partitions with hosted PD
Potential intruder:
An employee who is a user of the virtual environment, working with a virtual machine that is not intended for processing PD.
What's happening:
1) Unauthorized connection of storage system partitions (LUNs) containing PD to a hardware platform with virtual machines not authorized to process PD.
2) Carrying out at the network storage level attacks such as "spoofing" and "man in the middle."
Effects:
The leakage, distortion or destruction of PD in the framework of intercepted sessions.
Technical measures:
1) The organization of the protection of the storage network by standard certified [2] components of the storage system, in particular, the segmentation of the storage network (the formation of separate zones for storing information of different levels of confidentiality);
2) Placing information of different levels of confidentiality within individual storage networks.
Organizational measures:
Regulate the procedures for creating and administering the storage area network.
Notes:
[1] This implies that the storage network is based on a SAN.[2] At the moment there are no precedents for certification in the FSTEC of the storage network component that implements protection functions.
We use this table when developing specific threat models for personal data information systems deployed in a virtual environment and organizing protection measures. It is necessary to at least go over the checklist and check all the points: a “leak” even in one of them can mean a serious threat to the security of the system as a whole.
PS I see a lot of bookmarks added, but still I would like to understand how relevant such data is here and whether it is worth, for example, to consider the specific scenarios of each of the threats in future articles. Give feedback, please.
Source: https://habr.com/ru/post/140044/
All Articles